3 What is MMS? - ECO Documentation Database
... circuit switched data (CSD) bearers. MMS has been standardized by 3GPP [1, 2] and the standards have been published by ETSI. WAP is an industry standard produced by the WAP-forum, which has been integrated into the Open Mobile Alliance (OMA, http://www.openmobilealliance.org/). The work of the WAP ...
... circuit switched data (CSD) bearers. MMS has been standardized by 3GPP [1, 2] and the standards have been published by ETSI. WAP is an industry standard produced by the WAP-forum, which has been integrated into the Open Mobile Alliance (OMA, http://www.openmobilealliance.org/). The work of the WAP ...
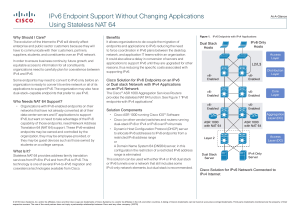
IPv6 Endpoint Support Without Changing Applications Using Stateless NAT 64
... With this solution an organization that wants to run IPv6 on a site or campus can still provide access to and from the IPv4 Internet. One important restriction of this solution is that it requires each host in the IPv6 network that needs to communicate with the IPv4 Internet to have a routable IPv4 ...
... With this solution an organization that wants to run IPv6 on a site or campus can still provide access to and from the IPv4 Internet. One important restriction of this solution is that it requires each host in the IPv6 network that needs to communicate with the IPv4 Internet to have a routable IPv4 ...
show route
... --- 172.26.25.1 ping statistics --25 packets transmitted, 25 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.014/1.875/2.073/0.285 ms user@router> traceroute 192.168.100.25 routing-instance new-instance traceroute to 192.168.100.25 (192.168.100.25), 30 hops max, 40 byte packets 1 ...
... --- 172.26.25.1 ping statistics --25 packets transmitted, 25 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.014/1.875/2.073/0.285 ms user@router> traceroute 192.168.100.25 routing-instance new-instance traceroute to 192.168.100.25 (192.168.100.25), 30 hops max, 40 byte packets 1 ...
About the Presentations
... • Common rules for packet filtering: – Drop all inbound connections except connection requests for configured servers – Eliminate packets bound for all ports that should not be available to the Internet – Filter out any ICMP redirect or echo (ping) messages – Drop all packets that use the IP header ...
... • Common rules for packet filtering: – Drop all inbound connections except connection requests for configured servers – Eliminate packets bound for all ports that should not be available to the Internet – Filter out any ICMP redirect or echo (ping) messages – Drop all packets that use the IP header ...
ROVANIEMI UNIVERSITY OF APPLIED SCIENCES SCHOOL OF TECHNOLOGY
... purposes indicating how to make maximum profits from telecommunication service. As a result, the competition is one of important aspects for the companies’ development. Reducing input cost and increasing quality of services are considered as the best solutions at the moment. In currently economic si ...
... purposes indicating how to make maximum profits from telecommunication service. As a result, the competition is one of important aspects for the companies’ development. Reducing input cost and increasing quality of services are considered as the best solutions at the moment. In currently economic si ...
Module 2 - OoCities
... a. Easy to understand and modify because the C-Language is a high level language. b. C-Language is allowing UNIX to be Portable. Q10: UUCP stands for ______________________________. (Answer: Unix to Unix Copy Program). ...
... a. Easy to understand and modify because the C-Language is a high level language. b. C-Language is allowing UNIX to be Portable. Q10: UUCP stands for ______________________________. (Answer: Unix to Unix Copy Program). ...
15-744: Computer Networking
... • End-to-end state • May provide reliability, flow and congestion control ...
... • End-to-end state • May provide reliability, flow and congestion control ...
Powerpoint
... NOT used for carrying Internet prefixes or customer prefixes design goal is to minimise number of prefixes in IGP to aid scalability and rapid convergence ...
... NOT used for carrying Internet prefixes or customer prefixes design goal is to minimise number of prefixes in IGP to aid scalability and rapid convergence ...
Layer 3 - Ohio Supercomputer Center
... Ensures that your “right of way” is not sold to other party who wishes to place cables Records and drawings of cable paths should be professionally done and provided to municipality IRUs cover above issues and annual maintenance ...
... Ensures that your “right of way” is not sold to other party who wishes to place cables Records and drawings of cable paths should be professionally done and provided to municipality IRUs cover above issues and annual maintenance ...
LP-N24 - LanPro
... herein are the trademarks or registered trademarks of their respective holders. Copyright of the whole product as integration, including its accessories and software, belongs to LanPro Inc. Without the permission of LanPro Inc., any individual or party is not allowed to copy, plagiarize, imitate or ...
... herein are the trademarks or registered trademarks of their respective holders. Copyright of the whole product as integration, including its accessories and software, belongs to LanPro Inc. Without the permission of LanPro Inc., any individual or party is not allowed to copy, plagiarize, imitate or ...
Instability of BGP ASPP
... prevent ASPP cycle. If there is no practical way, try to find all the AS that form the cycle. (John said maybe they could negotiate and find some solution:-) ...
... prevent ASPP cycle. If there is no practical way, try to find all the AS that form the cycle. (John said maybe they could negotiate and find some solution:-) ...
What do I do?
... In this model Wholesaler records where the call originated from “Previous Hop” and Bills the retailer back. This could be recorded at the Gateway or Network Proxy. © 2001, Cisco Systems, Inc. All rights reserved. ...
... In this model Wholesaler records where the call originated from “Previous Hop” and Bills the retailer back. This could be recorded at the Gateway or Network Proxy. © 2001, Cisco Systems, Inc. All rights reserved. ...
Eligible Services List 2012 - Universal Service Administrative
... To be eligible for support, telecommunications services must be provided by a telecommunications carrier, that is, a company that offers telecommunications services on a common carriage basis. A telecommunications service is “the offering of telecommunications for a fee directly to the public, or to ...
... To be eligible for support, telecommunications services must be provided by a telecommunications carrier, that is, a company that offers telecommunications services on a common carriage basis. A telecommunications service is “the offering of telecommunications for a fee directly to the public, or to ...
Brief - Electronic Privacy Information Center
... This case involves the intentional interception of electronic communications sent over home Wi-Fi networks. The intercepted data includes personal information and communications – passwords, e-mails, financial records, and other documents – that individuals consider extremely private. The fact that ...
... This case involves the intentional interception of electronic communications sent over home Wi-Fi networks. The intercepted data includes personal information and communications – passwords, e-mails, financial records, and other documents – that individuals consider extremely private. The fact that ...
Acceptable use Policy
... spam, bot nets, and other methods of intrusion. Addressing inappropriate content or transmissions – Cibola Wireless reserves the right to refuse to transmit or post, and to remove or block, any information or materials, in whole or in part, that it, in its sole discretion, deems to be in violation o ...
... spam, bot nets, and other methods of intrusion. Addressing inappropriate content or transmissions – Cibola Wireless reserves the right to refuse to transmit or post, and to remove or block, any information or materials, in whole or in part, that it, in its sole discretion, deems to be in violation o ...
Deployment of IPSec Virtual Private Network Solutions
... Network infrastructure & cost reduction Network Security Threats ...
... Network infrastructure & cost reduction Network Security Threats ...
Network
... The Basic Communication Link Dial-up telephone line, A circuit is temporarily established between caller and callee ...
... The Basic Communication Link Dial-up telephone line, A circuit is temporarily established between caller and callee ...
Using Spamhaus BGPf in a production environment
... approximately 3,000 clients, mostly Desktop and Mobile systems as well as operating nearly 2,000 servers which are being used to host various online services and online portals. ...
... approximately 3,000 clients, mostly Desktop and Mobile systems as well as operating nearly 2,000 servers which are being used to host various online services and online portals. ...
In NGN - APNOMS
... from different service providers) to build distinctive service offerings to customers; 3. Providing the management capabilities which enable organizations offering NGN services to offer users the ability to personalize user services and to create new services from NGN capabilities (potentially from ...
... from different service providers) to build distinctive service offerings to customers; 3. Providing the management capabilities which enable organizations offering NGN services to offer users the ability to personalize user services and to create new services from NGN capabilities (potentially from ...
Read more - Broadband Internet Technical Advisory Group
... BITAG Publishes Report on VoIP Impairment, Failure, and Restrictions Denver, CO (May 29, 2014): The Broadband Internet Technical Advisory Group (BITAG) is pleased to announce the publication of its technical report on VoIP impairment, failure, and restrictions. The executive summary and recommendati ...
... BITAG Publishes Report on VoIP Impairment, Failure, and Restrictions Denver, CO (May 29, 2014): The Broadband Internet Technical Advisory Group (BITAG) is pleased to announce the publication of its technical report on VoIP impairment, failure, and restrictions. The executive summary and recommendati ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... As the sub product of electronic mail services, spam became a serious issue in penetrating into any mail system and this types of penetration is mainly used by hackers for stealing confidential data without the knowledge of the user. Generally few hackers use worm which is standalone malware compute ...
... As the sub product of electronic mail services, spam became a serious issue in penetrating into any mail system and this types of penetration is mainly used by hackers for stealing confidential data without the knowledge of the user. Generally few hackers use worm which is standalone malware compute ...
Information-centric networking – Ready for the real world?
... research community and have been taken up by several research activities that are addressing the topic from different angles. Numerous research problems remain open, some of which (such as naming content) may find different (optimal) solutions in different deployments while others are more fundament ...
... research community and have been taken up by several research activities that are addressing the topic from different angles. Numerous research problems remain open, some of which (such as naming content) may find different (optimal) solutions in different deployments while others are more fundament ...
Juniper Networks Presentation Template-EMEA
... • First generation of pure VoIP carriers are gone • Price of 1 min of voice has fallen through the floor VoIP with other services is the way to go • Value-add: Unified messaging, voice accessible content, video telephony • Additional non-voice: Broadcast video, surveillance, etc. VPNs and other bu ...
... • First generation of pure VoIP carriers are gone • Price of 1 min of voice has fallen through the floor VoIP with other services is the way to go • Value-add: Unified messaging, voice accessible content, video telephony • Additional non-voice: Broadcast video, surveillance, etc. VPNs and other bu ...