Inferring Subnets in Router-Level Topology Collection Studies
... sidecar [19] detects changes in traversed paths by enabling record route option of probe packets. The third task is to resolve anonymous routers. This is required because not all routers respond to traceroute probes all the time [23]. A router may ignore responding with ICMP error messages due to it ...
... sidecar [19] detects changes in traversed paths by enabling record route option of probe packets. The third task is to resolve anonymous routers. This is required because not all routers respond to traceroute probes all the time [23]. A router may ignore responding with ICMP error messages due to it ...
Inferring Subnets in Router-level Topology Collection Studies
... sidecar [19] detects changes in traversed paths by enabling record route option of probe packets. ...
... sidecar [19] detects changes in traversed paths by enabling record route option of probe packets. ...
HLP: A Next Generation Inter
... • They claim the growth of the Internet routing table is a cause for alarm, but do not attempt to make the routing table smaller. • They focus on lower “churn” and more “isolation” without addressing whether these factors actually generate a significant amount of traffic. • The implication is that t ...
... • They claim the growth of the Internet routing table is a cause for alarm, but do not attempt to make the routing table smaller. • They focus on lower “churn” and more “isolation” without addressing whether these factors actually generate a significant amount of traffic. • The implication is that t ...
Routing Theory Part 2
... Network Discovery with Split Horizon - First Round of Updates RTB’s routing update sent out serial 0 to RTA Includes the network 10.1.3.0/24 which RTA can reach via 10.1.2.2. Split horizon: Does not include the 10.1.2.0/24 network. Split horizon blocks the 10.1.2.0/24 update from being sent to R ...
... Network Discovery with Split Horizon - First Round of Updates RTB’s routing update sent out serial 0 to RTA Includes the network 10.1.3.0/24 which RTA can reach via 10.1.2.2. Split horizon: Does not include the 10.1.2.0/24 network. Split horizon blocks the 10.1.2.0/24 update from being sent to R ...
ppt
... http://www.coursesmart.com/0136066992/?a=1773944 www.pearson-books.com/student (for additional discounts and offers) ...
... http://www.coursesmart.com/0136066992/?a=1773944 www.pearson-books.com/student (for additional discounts and offers) ...
Firewall Labs
... If rule table indicates that stateful table must be checked: check to see if there is already a connection in stateful table Stateful filters can also remember outgoing UDP segments Firewall. 50 ...
... If rule table indicates that stateful table must be checked: check to see if there is already a connection in stateful table Stateful filters can also remember outgoing UDP segments Firewall. 50 ...
Ayodele Damola
... The use of peer-to-peer (P2P) applications is growing dramatically, particularly for sharing content such as video, audio, and software. The traffic generated by these applications represents a large proportion of Internet traffic. For the broadband access network providers P2P traffic presents seve ...
... The use of peer-to-peer (P2P) applications is growing dramatically, particularly for sharing content such as video, audio, and software. The traffic generated by these applications represents a large proportion of Internet traffic. For the broadband access network providers P2P traffic presents seve ...
Basic Features of i-mode - San Jose State University
... • i-mode was developed by DoCoMo ( which means “anywhere” in Japanese) as a subsidiary of NTT (The Japan’s largest telecommunication service provider Nippon Telegraph and Telephone Corp.) in 1992. • i-mode (The “i” stands for information) is a wireless technology and service mark. • The i-mode servi ...
... • i-mode was developed by DoCoMo ( which means “anywhere” in Japanese) as a subsidiary of NTT (The Japan’s largest telecommunication service provider Nippon Telegraph and Telephone Corp.) in 1992. • i-mode (The “i” stands for information) is a wireless technology and service mark. • The i-mode servi ...
Apuntes seguridad Redes Avanzadas 0708
... way similar to a receiver requesting native multicast traffic from a local DR. Relays receive the multicast traffic natively from the sources, and encapsulate it into unicast datagrams to be forwarded to gateways through tunnels. This allows any potential receiver in the Internet to create a dynamic ...
... way similar to a receiver requesting native multicast traffic from a local DR. Relays receive the multicast traffic natively from the sources, and encapsulate it into unicast datagrams to be forwarded to gateways through tunnels. This allows any potential receiver in the Internet to create a dynamic ...
RAD Katalog 2016
... manufacturing companies often cited as one of the world’s premier generators of hi-tech innovation. A unique business philosophy distinguishes the RAD Group, which has no holding company but is strategically guided by its founders. Each company in the RAD Group operates autonomously under a common s ...
... manufacturing companies often cited as one of the world’s premier generators of hi-tech innovation. A unique business philosophy distinguishes the RAD Group, which has no holding company but is strategically guided by its founders. Each company in the RAD Group operates autonomously under a common s ...
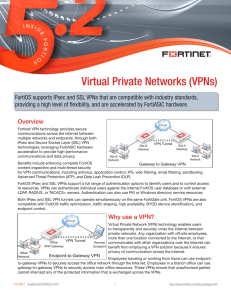
Virtual Private Networks (VPNs)
... immediately available to carry traffic and seamlessly maintain service. • Compatibility with most third-party IPsec VPN gateway and client solutions: FortiOS IPsec VPN is compatible with the VPN capabilities of Microsoft Windows (L2TP-IPsec), Cisco routers (GRE over IPsec), and iOS and Android mobil ...
... immediately available to carry traffic and seamlessly maintain service. • Compatibility with most third-party IPsec VPN gateway and client solutions: FortiOS IPsec VPN is compatible with the VPN capabilities of Microsoft Windows (L2TP-IPsec), Cisco routers (GRE over IPsec), and iOS and Android mobil ...
government of india - Department of Telecommunications
... actual start/provision of service by the licensee or any mutual obligations between the licensee and any other service provider/BSNL/MTNL/VSNL/Departments of the Central or State Government/local or statutory bodies. (ii) The Telecom Authority has decided to waive the Licence Fee for a period upto 3 ...
... actual start/provision of service by the licensee or any mutual obligations between the licensee and any other service provider/BSNL/MTNL/VSNL/Departments of the Central or State Government/local or statutory bodies. (ii) The Telecom Authority has decided to waive the Licence Fee for a period upto 3 ...
Intelligent WAN and WAN Design Summary (CVD) – October
... This guide provides a high level overview of several wide-area network (WAN) technologies, followed by a discussion of the usage of each technology at the WAN-aggregation site and remote sites. This guide should be used as a roadmap on how to use the companion Intelligent WAN (IWAN) and WAN deployme ...
... This guide provides a high level overview of several wide-area network (WAN) technologies, followed by a discussion of the usage of each technology at the WAN-aggregation site and remote sites. This guide should be used as a roadmap on how to use the companion Intelligent WAN (IWAN) and WAN deployme ...
Multicast Basic Concept
... • Unicast: point to point communication • Broadcast: packets are sent to all – IP supports broadcasting, but the use of broadcasts is strictly limited. – Protocols require broadcasts only when there is no alternative – Routers limit broadcasts to the local network or subnet, preventing broadcasts fo ...
... • Unicast: point to point communication • Broadcast: packets are sent to all – IP supports broadcasting, but the use of broadcasts is strictly limited. – Protocols require broadcasts only when there is no alternative – Routers limit broadcasts to the local network or subnet, preventing broadcasts fo ...
思科运营商网络研讨会: 苏远超 思科中国电信运营商事业部 高级顾问工程师 2011.10.27
... Provisioning and activation for transport and packet networks including IP RAN Backhaul Diagnosis and repair of packet networks Point and click provisioning of RAN backhaul connections Service Catalog & Dashboard Order to Service ...
... Provisioning and activation for transport and packet networks including IP RAN Backhaul Diagnosis and repair of packet networks Point and click provisioning of RAN backhaul connections Service Catalog & Dashboard Order to Service ...
Communications Market Act
... 9) public authority network means a communications network built for the needs of public order and security, rescue activities or civil defence, whose subscriber connections can be made available not only to public authorities but also to other user groups essential to the discharging of the duties ...
... 9) public authority network means a communications network built for the needs of public order and security, rescue activities or civil defence, whose subscriber connections can be made available not only to public authorities but also to other user groups essential to the discharging of the duties ...
Using Your Gateway WGR
... Using access point/router settings and features . . . . . . . . . . . . . . . . . . . . . . . . . . . 60 Restoring the access point/router’s default settings . . . . . . . . . . . . . . . . . . . . . 60 Upgrading the firmware . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . ...
... Using access point/router settings and features . . . . . . . . . . . . . . . . . . . . . . . . . . . 60 Restoring the access point/router’s default settings . . . . . . . . . . . . . . . . . . . . . 60 Upgrading the firmware . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . ...
Virtual Private Networks (VPN`s)
... remote-access VPN. The concentrators are offered in models suitable for everything from small businesses with up to 100 remote-access users to large organizations with up to 10,000 simultaneous remote users. ...
... remote-access VPN. The concentrators are offered in models suitable for everything from small businesses with up to 100 remote-access users to large organizations with up to 10,000 simultaneous remote users. ...
STANAG 5066 Update - HFIA, High Frequency Industry Association
... to what extent should token-relay be supported? the previous draft and implementations support one token-relay topology only, i.e., only on token relayer is allowed in the network; BUT USN has recently developed and tested a robust token-relay approach for sparse topologies where more than one ...
... to what extent should token-relay be supported? the previous draft and implementations support one token-relay topology only, i.e., only on token relayer is allowed in the network; BUT USN has recently developed and tested a robust token-relay approach for sparse topologies where more than one ...
SSM-Ping: A Ping Utility for Source Specific Multicast
... receivers in a multicast group. These trees are dynamically created and maintained by the routers, yet there is no feedback information built into the process. That is, if a tree cannot be built because there is no path to the source, the receiver will never know. Reachability ensures that sources c ...
... receivers in a multicast group. These trees are dynamically created and maintained by the routers, yet there is no feedback information built into the process. That is, if a tree cannot be built because there is no path to the source, the receiver will never know. Reachability ensures that sources c ...
Do Internet Incumbents Choose Low Interconnection Quality?
... connection quality with AOL Time Warner’s customers in the USA. However, it is likely that AOL Time Warner’s income from American customers also depends on the interconnection quality with European Internet users that are connected to the regional ISPs. Typically, the revenue from the installed bas ...
... connection quality with AOL Time Warner’s customers in the USA. However, it is likely that AOL Time Warner’s income from American customers also depends on the interconnection quality with European Internet users that are connected to the regional ISPs. Typically, the revenue from the installed bas ...
2 Huawei LTE PTT Broadband Trunking Solution
... is also developed from the analog technology to the digital technology and from only having voice services to having voice and data services. The 1G trunking communications network is an analog system that uses FDMA and provides only voice services. The 2G trunking communications network is a digita ...
... is also developed from the analog technology to the digital technology and from only having voice services to having voice and data services. The 1G trunking communications network is an analog system that uses FDMA and provides only voice services. The 2G trunking communications network is a digita ...
On peer-to-peer (P2P) content delivery
... bandwidth. The streaming application may also adapt the delivery media according to the resource available in the system and to the client. For example, for client at the end of a slow Internet link or for P2P network with insufficient total network bandwidth, a low bit rate version of the video can ...
... bandwidth. The streaming application may also adapt the delivery media according to the resource available in the system and to the client. For example, for client at the end of a slow Internet link or for P2P network with insufficient total network bandwidth, a low bit rate version of the video can ...
Leonard Kleinrock`s Keynote speech at
... UCLA puts out Press Release 8/29 BBN sends first switch (IMP) to UCLA ...
... UCLA puts out Press Release 8/29 BBN sends first switch (IMP) to UCLA ...