Introduction - Bapatla Engineering College
... A client-server application typically consists of three layers: 1.User-Interface level: +Consists of the programs that allow end users to interact with application. 2.Processing level: +Implements the application logic (core functionality) +Typically implemented at the server side 3.Data level +Main ...
... A client-server application typically consists of three layers: 1.User-Interface level: +Consists of the programs that allow end users to interact with application. 2.Processing level: +Implements the application logic (core functionality) +Typically implemented at the server side 3.Data level +Main ...
Chapter 4
... government. “Com” stands for commercial, so many businesses have .com as their domain name. Top-level domains are registered by Internet Assigned Numbers Authority (IANA); http://www.iana.org/. In order for network traffic to travel across routers all over the world, the domain name needs to be regi ...
... government. “Com” stands for commercial, so many businesses have .com as their domain name. Top-level domains are registered by Internet Assigned Numbers Authority (IANA); http://www.iana.org/. In order for network traffic to travel across routers all over the world, the domain name needs to be regi ...
TL-WR542G 54M Wireless Router
... sensitive data secure transmission. The TL-WR542G 54Mbps Wireless Router complies with the IEEE 802.11g and IEEE 802.11b standards so that the data transmission rate is up to 54Mbps. It adopts 2x to 3x eXtended Range™ WLAN transmission technology so that the transmission distance is 2-3 times of tra ...
... sensitive data secure transmission. The TL-WR542G 54Mbps Wireless Router complies with the IEEE 802.11g and IEEE 802.11b standards so that the data transmission rate is up to 54Mbps. It adopts 2x to 3x eXtended Range™ WLAN transmission technology so that the transmission distance is 2-3 times of tra ...
PowerPoint - DePaul University
... Given that an ISP announces netblocks 64.5.0.0/20, 64.5.16.0/20, 192.0.2.0/25 and 192.0.2.192/26 and 192.0.2.128/26: ...
... Given that an ISP announces netblocks 64.5.0.0/20, 64.5.16.0/20, 192.0.2.0/25 and 192.0.2.192/26 and 192.0.2.128/26: ...
Reference Manual for the Model RP614 Web Safe Router
... Federal Communications Commission (FCC) Compliance Notice: Radio Frequency Notice This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interfer ...
... Federal Communications Commission (FCC) Compliance Notice: Radio Frequency Notice This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interfer ...
turbo 7 wireless gateway with voice (3g10wvt)
... Local (LAN) access (username: admin, password: admin) Remote (WAN) access (username: support, password: support) User access (username: user, password: user) LAN IP address: 10.0.0.138 Remote WAN access: disabled NAT and firewall: enabled Dynamic Host Configuration Protocol (DHCP) server on LAN inte ...
... Local (LAN) access (username: admin, password: admin) Remote (WAN) access (username: support, password: support) User access (username: user, password: user) LAN IP address: 10.0.0.138 Remote WAN access: disabled NAT and firewall: enabled Dynamic Host Configuration Protocol (DHCP) server on LAN inte ...
DRCP - Telcordia
... as border router is concerned. It uses two parallel cache system , routing and paging, for location update. Handoff is initiated by the mobile host Proposes a 2-layer method for binding protocol. Uses Mobile IP for global mobility. For macro-mobility it assigns the mobile node an address ass ...
... as border router is concerned. It uses two parallel cache system , routing and paging, for location update. Handoff is initiated by the mobile host Proposes a 2-layer method for binding protocol. Uses Mobile IP for global mobility. For macro-mobility it assigns the mobile node an address ass ...
Good Control/Good Proxy Server Installation
... Users of mobile devices in the field often need to access internal resources directly via the GP server, bypassing the BlackBerry Network Operations Center (NOC, not shown). This configuration is called Direct Connect. Reasons for enabling Direct Connect include increased performance (by decreased n ...
... Users of mobile devices in the field often need to access internal resources directly via the GP server, bypassing the BlackBerry Network Operations Center (NOC, not shown). This configuration is called Direct Connect. Reasons for enabling Direct Connect include increased performance (by decreased n ...
The Network Layer
... Real-time traffic and mobile users are also becoming more common – IPv4 cannot support various QoS requirements ...
... Real-time traffic and mobile users are also becoming more common – IPv4 cannot support various QoS requirements ...
Defense
... • Fast reconnection: Do quick re-authentication by passing only session keys. The session can be resumed without having to perform PEAP Phase 1 or 2. • Seamless transition: uses the connection re-establishment mechanism provided by the TLS handshake protocol. Nirmala 12/18/03 ...
... • Fast reconnection: Do quick re-authentication by passing only session keys. The session can be resumed without having to perform PEAP Phase 1 or 2. • Seamless transition: uses the connection re-establishment mechanism provided by the TLS handshake protocol. Nirmala 12/18/03 ...
Serial over Ethernet Device Server User`s Manual
... devices. It provides a convenient and economical solution not only to protect your current hardware investment, but also to ensure future network expandability. With Serial over Ethernet Server, users can centralize serial devices and distribute the management hosts at the same time. Serial over Eth ...
... devices. It provides a convenient and economical solution not only to protect your current hardware investment, but also to ensure future network expandability. With Serial over Ethernet Server, users can centralize serial devices and distribute the management hosts at the same time. Serial over Eth ...
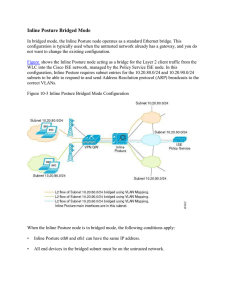
15360608-Inline Posture Bridged Mode
... they provide the rules for the profiles to follow. Access control lists (ACLs) prevent unwanted traffic from entering the network by filtering source and destination IP addresses, transport protocols, and other variables, using the RADIUS protocol. After you create DACLs as named permission objects, ...
... they provide the rules for the profiles to follow. Access control lists (ACLs) prevent unwanted traffic from entering the network by filtering source and destination IP addresses, transport protocols, and other variables, using the RADIUS protocol. After you create DACLs as named permission objects, ...
NETGEAR Wireless Router Setup Manual
... Federal Communications Commission (FCC) Compliance Notice: Radio Frequency Notice This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interfer ...
... Federal Communications Commission (FCC) Compliance Notice: Radio Frequency Notice This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interfer ...
LevelOne
... Chapter 2 explains printer server’s hardware installation and configuration. It is strongly recommended for you to read. The following chapters introduce: Chapter 3. Windows Peer-to-Peer Network Chapter 4. Windows 2000 Based Network Chapter 5. NetWare Network Chapter 6. UNIX System Network You may s ...
... Chapter 2 explains printer server’s hardware installation and configuration. It is strongly recommended for you to read. The following chapters introduce: Chapter 3. Windows Peer-to-Peer Network Chapter 4. Windows 2000 Based Network Chapter 5. NetWare Network Chapter 6. UNIX System Network You may s ...
DSL-G624T Wireless ADSL Router User Guide
... Any computer that uses the Router must be able to connect to it through the Ethernet port on the Router. The easiest method of installation is via the Ethernet connection and therefore requires that your computer be equipped with an Ethernet port as well. Most notebook computers are now sold with an ...
... Any computer that uses the Router must be able to connect to it through the Ethernet port on the Router. The easiest method of installation is via the Ethernet connection and therefore requires that your computer be equipped with an Ethernet port as well. Most notebook computers are now sold with an ...
IPv6 at Monash University
... Test service using hex IPv6 address, or a test DNS name Check via logs and/or network packet capture – Up to this point, changes are invisible to users • Add AAAA record to DNS for service name • Test service via DNS name • Check via logs and/or network packet capture – Beware of users who have IPv6 ...
... Test service using hex IPv6 address, or a test DNS name Check via logs and/or network packet capture – Up to this point, changes are invisible to users • Add AAAA record to DNS for service name • Test service via DNS name • Check via logs and/or network packet capture – Beware of users who have IPv6 ...
VESR90x Serial Server
... 10/100 Mbps Ethernet with Auto Selection LAN and WAN Communications TCP Client or Server, or UDP operation - configurable Virtual COM port and Paired Mode capabilities Firmware Upload for future revisions/upgrades Software Support - Windows 2000/2003 Server/XP/Vista Configuration of Ethernet and ser ...
... 10/100 Mbps Ethernet with Auto Selection LAN and WAN Communications TCP Client or Server, or UDP operation - configurable Virtual COM port and Paired Mode capabilities Firmware Upload for future revisions/upgrades Software Support - Windows 2000/2003 Server/XP/Vista Configuration of Ethernet and ser ...
PDF
... Cisco offers a wide range of services to help accelerate your success in deploying and optimizing Cisco Nexus 5000 Series Switches in your data center. Cisco’s innovative services are delivered through a unique combination of people, processes, tools, and partners and are focused on helping you incr ...
... Cisco offers a wide range of services to help accelerate your success in deploying and optimizing Cisco Nexus 5000 Series Switches in your data center. Cisco’s innovative services are delivered through a unique combination of people, processes, tools, and partners and are focused on helping you incr ...
Access your control systems via the Internet
... Remote Access & Control Features full SSL 128 bit encryption ...
... Remote Access & Control Features full SSL 128 bit encryption ...
TD-W8961NB 300Mbps Wireless N ADSL2+ Modem Router - TP-Link
... The TD-W8961NB connects to an Ethernet LAN or computers via standard Ethernet ports. The ADSL connection is made using ordinary telephone line with standard connectors. Multiple workstations can be networked and connected to the Internet using a single Wide Area Network (WAN) interface and single gl ...
... The TD-W8961NB connects to an Ethernet LAN or computers via standard Ethernet ports. The ADSL connection is made using ordinary telephone line with standard connectors. Multiple workstations can be networked and connected to the Internet using a single Wide Area Network (WAN) interface and single gl ...
Figure 20 - Zoonsuite
... Status Page Definitions ................................................................................................................ 33 Profiles Page Definitions .............................................................................................................. 36 DECT Page Definition ...
... Status Page Definitions ................................................................................................................ 33 Profiles Page Definitions .............................................................................................................. 36 DECT Page Definition ...
Employing a secure Virtual Private Network (VPN)
... Seapower,” 17 October 2007, available from www.navy.mil/maritime, (accessed 05 January 2009). ...
... Seapower,” 17 October 2007, available from www.navy.mil/maritime, (accessed 05 January 2009). ...