Configuring Network Settings for Your LifeSize PhoneTM
... power. Inspect connections to any system cables and ensure there are no obstructions or loose cables at either end. Ensure you have plugged in the network cable correctly to the PoE adapter or port. Although it is possible to plug in the LAN end to the phone, the phone will not work. Correct the con ...
... power. Inspect connections to any system cables and ensure there are no obstructions or loose cables at either end. Ensure you have plugged in the network cable correctly to the PoE adapter or port. Although it is possible to plug in the LAN end to the phone, the phone will not work. Correct the con ...
Application Layer - Teknik Elektro UGM
... P2P network allow computers to act as both clients and servers during the same communication. Each of them is called ‘peer’ because they can perform both tasks. Each user is in charge of his own access policies Disadvantage: ...
... P2P network allow computers to act as both clients and servers during the same communication. Each of them is called ‘peer’ because they can perform both tasks. Each user is in charge of his own access policies Disadvantage: ...
SSL and IPSec
... – Association between peers for security services • Identified uniquely by dest address, security protocol (AH or ESP), unique 32-bit number (security parameter index, or SPI) ...
... – Association between peers for security services • Identified uniquely by dest address, security protocol (AH or ESP), unique 32-bit number (security parameter index, or SPI) ...
Communication - Computer Science Division
... Divide times in epochs Client broadcasts epoch when reboots Upon hearing a new epoch servers kills the orphans Disadvantage: doesn’t solve problem when network partitioned ...
... Divide times in epochs Client broadcasts epoch when reboots Upon hearing a new epoch servers kills the orphans Disadvantage: doesn’t solve problem when network partitioned ...
Basic Networking
... Client/Server Networks • Server: central computer used to facilitate communication and resource sharing between other computers on the network (called clients) • Client/server network: uses a server to enable clients to share data, data storage space, and devices • To function as a server, a comput ...
... Client/Server Networks • Server: central computer used to facilitate communication and resource sharing between other computers on the network (called clients) • Client/server network: uses a server to enable clients to share data, data storage space, and devices • To function as a server, a comput ...
Document
... Datagram Model • Packets contain a destination address; each router uses it to forward each packet, possibly on different paths ISP’s equipment ...
... Datagram Model • Packets contain a destination address; each router uses it to forward each packet, possibly on different paths ISP’s equipment ...
Top-Down Network Design
... network/subnet field and which part is the host field – The network/subnet portion of the mask is all 1s in binary. – The host portion of the mask is all 0s in binary. – Convert the binary expression back to dotted-decimal notation for entering into configurations. ...
... network/subnet field and which part is the host field – The network/subnet portion of the mask is all 1s in binary. – The host portion of the mask is all 0s in binary. – Convert the binary expression back to dotted-decimal notation for entering into configurations. ...
Business Class DSL Routers
... PPP (RFC 1661, RFC 2364) • PPP over Ethernet (RFC2516) • Data compression of up to 4:1 (STAC™ LZS) (RFC 1974) • Van Jacobson header compression (RFC 1144) • Spoofing and filtering (IP-RIP, IPX-RIP, SAP, Watchdog, serialization) • Automatic IP and DNS assignment (RFC 1877) IP Address Translation • Ne ...
... PPP (RFC 1661, RFC 2364) • PPP over Ethernet (RFC2516) • Data compression of up to 4:1 (STAC™ LZS) (RFC 1974) • Van Jacobson header compression (RFC 1144) • Spoofing and filtering (IP-RIP, IPX-RIP, SAP, Watchdog, serialization) • Automatic IP and DNS assignment (RFC 1877) IP Address Translation • Ne ...
presentation.
... • Highly versatile Internet connectivity solution for non-Internet enabled devices. • Seamless interface with RS232, Ethernet, switches, sensors and relays. • Uses IEEE assigned MAC addresses. • Network configurable. • RS485 up-gradable. ...
... • Highly versatile Internet connectivity solution for non-Internet enabled devices. • Seamless interface with RS232, Ethernet, switches, sensors and relays. • Uses IEEE assigned MAC addresses. • Network configurable. • RS485 up-gradable. ...
ppt - CSE Home
... Client broadcasts need for an IP address. DHCP servers on the network respond. Client chooses a server and sends the MAC (Media Access Control) address of its network card. ...
... Client broadcasts need for an IP address. DHCP servers on the network respond. Client chooses a server and sends the MAC (Media Access Control) address of its network card. ...
009_namingaddressing
... An Ethernet network uses two hardware addresses which identify the source and destination of each frame sent by the Ethernet. The destination address (all 1's) may also identify a broadcast packet (to be sent to all connected computers). The hardware address is also known as the Medium Access Contro ...
... An Ethernet network uses two hardware addresses which identify the source and destination of each frame sent by the Ethernet. The destination address (all 1's) may also identify a broadcast packet (to be sent to all connected computers). The hardware address is also known as the Medium Access Contro ...
Part I: Introduction - University of Pittsburgh
... CSMA, CSMA/CD, CSMA/CA CSMA – sense carrier before sending CD – detect collision while sending and cancel it CA – avoid collision by getting permission first Ethernet and Wi-Fi? ...
... CSMA, CSMA/CD, CSMA/CA CSMA – sense carrier before sending CD – detect collision while sending and cancel it CA – avoid collision by getting permission first Ethernet and Wi-Fi? ...
Basic Configuration of WAP4410N
... should be reachable. Usually their VLAN is left untagged - '1' to assume the Native VLAN of the switch. 5. Under Setup -> LAN, disable the DHCP server (assuming DHCP Is already running on this subnet) 6. Go to Setup -> Advanced Routing and ensure that Inter-VLAN routing is enabled. This is important ...
... should be reachable. Usually their VLAN is left untagged - '1' to assume the Native VLAN of the switch. 5. Under Setup -> LAN, disable the DHCP server (assuming DHCP Is already running on this subnet) 6. Go to Setup -> Advanced Routing and ensure that Inter-VLAN routing is enabled. This is important ...
How to Configure Alerts on SolarWinds IP Address Manager 4.3
... A typical network comprises multiple network devices, servers, and user devices, which all need an IP address to function. With the number of devices increasing from tens to hundreds to thousands, administrators need to adopt a more proactive approach to monitoring and fixing network issues. Alertin ...
... A typical network comprises multiple network devices, servers, and user devices, which all need an IP address to function. With the number of devices increasing from tens to hundreds to thousands, administrators need to adopt a more proactive approach to monitoring and fixing network issues. Alertin ...
IP Addressing Notes - Mr. Dixon`s Weebly
... b. No two computers can share the same IP address. c. Telephone number analogy. If I dial a number, I connect with just one person. d. All devices, whether computer, laptop or cell phone require an IP address to go onto the Internet. 2. What does an IP address look like? a. Examples: 192.168.1.1 or ...
... b. No two computers can share the same IP address. c. Telephone number analogy. If I dial a number, I connect with just one person. d. All devices, whether computer, laptop or cell phone require an IP address to go onto the Internet. 2. What does an IP address look like? a. Examples: 192.168.1.1 or ...
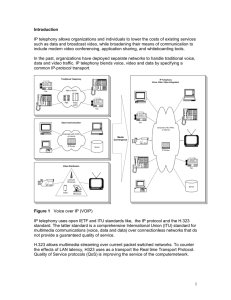
Introduction
... Figure 1 Voice over IP (VOIP) IP telephony uses open IETF and ITU standards like, the IP protocol and the H.323 standard. The latter standard is a comprehensive International Union (ITU) standard for multimedia communications (voice, data and data) over connectionless networks that do not provide a ...
... Figure 1 Voice over IP (VOIP) IP telephony uses open IETF and ITU standards like, the IP protocol and the H.323 standard. The latter standard is a comprehensive International Union (ITU) standard for multimedia communications (voice, data and data) over connectionless networks that do not provide a ...
Final Lecture: Course Overview
... • Allocated to Internet Service Providers and large institutions ...
... • Allocated to Internet Service Providers and large institutions ...
4th Edition: Chapter 1
... underlying channel may flip bits in packet checksum to detect bit errors the question: how to recover from errors: ...
... underlying channel may flip bits in packet checksum to detect bit errors the question: how to recover from errors: ...
R7200 SDSL Routers
... address on the Internet. Port Translation allows mail, Web, PPTP, and other servers on the LAN to be accessible from the Internet. (RFC 1631) • MultiNAT: Sophisticated NAT (RFC 1631) extension that provides security of a NAT "wall" to hide LAN IP addresses on LAN while providing flexible use of all ...
... address on the Internet. Port Translation allows mail, Web, PPTP, and other servers on the LAN to be accessible from the Internet. (RFC 1631) • MultiNAT: Sophisticated NAT (RFC 1631) extension that provides security of a NAT "wall" to hide LAN IP addresses on LAN while providing flexible use of all ...
ppt
... Hyper Text Transfer Protocol (HTTP) (continued) • HTTP 1.1 − Allows for embedded documents in the HTML file − “Persistent connections”: The client browser opens a (single) connection with the server for the html file. Then, embedded documents are requested within this same TCP connection − Pipeline ...
... Hyper Text Transfer Protocol (HTTP) (continued) • HTTP 1.1 − Allows for embedded documents in the HTML file − “Persistent connections”: The client browser opens a (single) connection with the server for the html file. Then, embedded documents are requested within this same TCP connection − Pipeline ...
NAME: Computer Science 461 Midterm Exam March 30, 2009
... For this question, there is a single client communicating with a single server using TCP. The client sends a very small amount of data using the send() function, and the server receives the data with a recv() call. Each of the following scenarios shows a different order in which the socket calls are ...
... For this question, there is a single client communicating with a single server using TCP. The client sends a very small amount of data using the send() function, and the server receives the data with a recv() call. Each of the following scenarios shows a different order in which the socket calls are ...
Chapter 1 - BRAC University Courses
... • Every device that connects to a network needs an IP address. • Network administrators assign static IP addresses to routers, servers, and other network devices whose locations (physical and logical) are not likely to change. • User computers in an organization often change locations, physically an ...
... • Every device that connects to a network needs an IP address. • Network administrators assign static IP addresses to routers, servers, and other network devices whose locations (physical and logical) are not likely to change. • User computers in an organization often change locations, physically an ...
Chapter 1
... • Every device that connects to a network needs an IP address. • Network administrators assign static IP addresses to routers, servers, and other network devices whose locations (physical and logical) are not likely to change. • User computers in an organization often change locations, physically an ...
... • Every device that connects to a network needs an IP address. • Network administrators assign static IP addresses to routers, servers, and other network devices whose locations (physical and logical) are not likely to change. • User computers in an organization often change locations, physically an ...
Programming Project - Department of Electrical Engineering
... keyword PING, the message sequence number, and the message timestamp. After sending each packet, the client will wait up to one second to receive a reply. If one second goes by without a reply from the server, then the client will assume that its packet or the server’s reply packet has been lost in ...
... keyword PING, the message sequence number, and the message timestamp. After sending each packet, the client will wait up to one second to receive a reply. If one second goes by without a reply from the server, then the client will assume that its packet or the server’s reply packet has been lost in ...