A+ Guide to Managing and Maintaining Your PC, 7e
... A+ Guide to Managing and Maintaining Your PC, 7e ...
... A+ Guide to Managing and Maintaining Your PC, 7e ...
Lecture 21
... Reads the IP address from the message Transmits an ARP request – “Who does this belong to” The IP address owner replies “Me” by returning its MAC address The sender assigns the received MAC to the destination field in the frame header… …and send the frame on its way ...
... Reads the IP address from the message Transmits an ARP request – “Who does this belong to” The IP address owner replies “Me” by returning its MAC address The sender assigns the received MAC to the destination field in the frame header… …and send the frame on its way ...
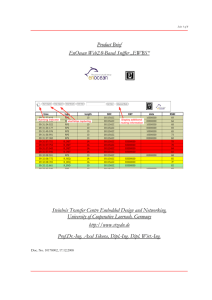
IPmux-4L_Product
... • Incumbents migrating services from TDM leased lines to Ethernet links (LAN inter-connect, IPVPN, Fast Internet service) Benefits • Customer does not need to replace HW ...
... • Incumbents migrating services from TDM leased lines to Ethernet links (LAN inter-connect, IPVPN, Fast Internet service) Benefits • Customer does not need to replace HW ...
module_1.0
... – Computers and their users are customers of the network utility The network must accommodate the needs of customers – As computer usage increases so does the requirements of the network utility ...
... – Computers and their users are customers of the network utility The network must accommodate the needs of customers – As computer usage increases so does the requirements of the network utility ...
Contactual Technical Requirements 6.5.1 - Packet8
... customer computer to permit the download and running of the Collaborate program. Some anti-virus programs or operating system security features may incorrectly identify the program downloaded to the customer's computer by the Collaborate feature as a security threat. ...
... customer computer to permit the download and running of the Collaborate program. Some anti-virus programs or operating system security features may incorrectly identify the program downloaded to the customer's computer by the Collaborate feature as a security threat. ...
Layer 2
... http://playground.sun.com/pub/ipng/html/ipng-main.html IPv6 work including mobility support •"The 3G IP Multimedia Subsystem" by Gonzalo Camarillo and Miguel A. Garcia Martin (available in google books) ...
... http://playground.sun.com/pub/ipng/html/ipng-main.html IPv6 work including mobility support •"The 3G IP Multimedia Subsystem" by Gonzalo Camarillo and Miguel A. Garcia Martin (available in google books) ...
21-06-0472-00-0000-Handover_Use_Case_More_IEs
... – The Bus is doing the handover and “sees” a variety of WLAN and WiMAX networks as well as universal GPRS – it needs to decide which one(s) to connect to ...
... – The Bus is doing the handover and “sees” a variety of WLAN and WiMAX networks as well as universal GPRS – it needs to decide which one(s) to connect to ...
Title Subtitle - School of Computing and Engineering
... Between Layer 2 and Layer 3 Headers (other technologies use different approaches) ...
... Between Layer 2 and Layer 3 Headers (other technologies use different approaches) ...
The Internet Motion Sensor: A Distributed Blackhole
... location are important components of sensor coverage. The second issue is service emulation. If the sensors do not directly involve live hosts then there is a question of what services to emulate and at what level to emulate them. This is a difficult problem given the immense number services on the ...
... location are important components of sensor coverage. The second issue is service emulation. If the sensors do not directly involve live hosts then there is a question of what services to emulate and at what level to emulate them. This is a difficult problem given the immense number services on the ...
Cisco 1 - Network Specialist Program
... 5. To minimize what types of packets show up in our simulation, we will again create a filter. Use what you learned previously in this lab to configure Packet Tracer to show only ICMP packets (refer back if you need to). 6. Use what you learned in the previous task to create a simple test message in ...
... 5. To minimize what types of packets show up in our simulation, we will again create a filter. Use what you learned previously in this lab to configure Packet Tracer to show only ICMP packets (refer back if you need to). 6. Use what you learned in the previous task to create a simple test message in ...
network-troubleshooting & system management
... start network interfaces, mount directories, and monitor your system. Most of these scripts are run from subdirectories of /etc/rc.d. The program that starts most of these services up when you boot and stops them when you shut down is the /etc/rc.d/rc script. The following sections describe run-leve ...
... start network interfaces, mount directories, and monitor your system. Most of these scripts are run from subdirectories of /etc/rc.d. The program that starts most of these services up when you boot and stops them when you shut down is the /etc/rc.d/rc script. The following sections describe run-leve ...
Blue Socket, Mike Brockney
... – Same problem as proprietary IPsec clients for guest access Client software is required to run 802.1x , involving the need to upgrade all client devices – Only some Windows versions provide support; not on other devices (PDA’s, Apple MACs, Scanners, etc., etc.) – No visitor, non-802.1x guest user ...
... – Same problem as proprietary IPsec clients for guest access Client software is required to run 802.1x , involving the need to upgrade all client devices – Only some Windows versions provide support; not on other devices (PDA’s, Apple MACs, Scanners, etc., etc.) – No visitor, non-802.1x guest user ...
Power Point Slides for Chap. 5
... – How are IP packets processed at router? • 1. Pkt. arrives at router • 2. Destination address is looked up – For distant network? Forwarded to next router on interface given on table. – Local host? Sent directly to destination – Network not on table? Sent to default router with more extensive table ...
... – How are IP packets processed at router? • 1. Pkt. arrives at router • 2. Destination address is looked up – For distant network? Forwarded to next router on interface given on table. – Local host? Sent directly to destination – Network not on table? Sent to default router with more extensive table ...
Mobile IPv6 and Firewalls: Problem Statement
... Most firewalls available for IPv6 networks do not support Mobile IPv6. Since most networks in the current business environment deploy firewalls, this may prevent future large-scale deployment of the Mobile IPv6 protocol. ...
... Most firewalls available for IPv6 networks do not support Mobile IPv6. Since most networks in the current business environment deploy firewalls, this may prevent future large-scale deployment of the Mobile IPv6 protocol. ...
IP: Datagram and Addressing
... LIVE counter decrements by the number of seconds the datagram waited for service inside the router. ...
... LIVE counter decrements by the number of seconds the datagram waited for service inside the router. ...
Datasheet - EnOcean Alliance
... a unique timestamp for every telegram in the ring buffer. The ring buffer is also implemented on this controller as a temporary storage for up to 256 telegrams. The web server software can gain access to these telegrams via an exposed API, which allows for retrieval of specific telegrams as well as ...
... a unique timestamp for every telegram in the ring buffer. The ring buffer is also implemented on this controller as a temporary storage for up to 256 telegrams. The web server software can gain access to these telegrams via an exposed API, which allows for retrieval of specific telegrams as well as ...
tech brief - Arrow ECS
... transparently takes over by assuming the IP and MAC address “identity” of the failed switch. At Layer 2, its approach to redundancy is similar to spanning tree, except that its recovery rate ranges from two to six seconds. So how does ESRP compare to VRRP? VRRP was designed to support older shared-L ...
... transparently takes over by assuming the IP and MAC address “identity” of the failed switch. At Layer 2, its approach to redundancy is similar to spanning tree, except that its recovery rate ranges from two to six seconds. So how does ESRP compare to VRRP? VRRP was designed to support older shared-L ...
Managing Routing Disruptions in Internet Service Provider Networks
... and delay during routing-protocol convergence). These service disruptions are a significant problem for applications such as voice over IP (VoIP), video games, and commercial transactions. For example, a recent study of VoIP performance found that most service disruptions occur during routing change ...
... and delay during routing-protocol convergence). These service disruptions are a significant problem for applications such as voice over IP (VoIP), video games, and commercial transactions. For example, a recent study of VoIP performance found that most service disruptions occur during routing change ...
MPLS
... to address the problems faced by present-day networks—speed, scalability, quality-of-service (QoS) management, and traffic engineering Applying QoS on a flow-by-flow basis is not practical due to the huge numbers of IP traffic flows in carrier-sized networks. most of the routing protocols depl ...
... to address the problems faced by present-day networks—speed, scalability, quality-of-service (QoS) management, and traffic engineering Applying QoS on a flow-by-flow basis is not practical due to the huge numbers of IP traffic flows in carrier-sized networks. most of the routing protocols depl ...
Lab I: Internet services. Telnet (SSH), E
... of the connection. Applications work with protocols to send and receive data across the Internet. A web browser displays Hypertext Markup Language (HTML) as a web page. File Transfer Protocol (FTP) is used to download files and programs from the Internet. Web browsers also use proprietary plug-in ap ...
... of the connection. Applications work with protocols to send and receive data across the Internet. A web browser displays Hypertext Markup Language (HTML) as a web page. File Transfer Protocol (FTP) is used to download files and programs from the Internet. Web browsers also use proprietary plug-in ap ...
elc200day5
... • Protocols are pieces of software that run on every node or computer and allow every pair of computers to communicate directly without having to know much about each other, except for the IP address • Protocols govern communication between peer processes on different systems • Differing client brow ...
... • Protocols are pieces of software that run on every node or computer and allow every pair of computers to communicate directly without having to know much about each other, except for the IP address • Protocols govern communication between peer processes on different systems • Differing client brow ...
$doc.title
... • April 25, 1997: “The day the Internet died” – AS7007 (Florida Internet Exchange) de-‐aggregated the BGP route table and re-‐adverDsed all prefixes as if it originated paths to them • In effect, AS7007 ...
... • April 25, 1997: “The day the Internet died” – AS7007 (Florida Internet Exchange) de-‐aggregated the BGP route table and re-‐adverDsed all prefixes as if it originated paths to them • In effect, AS7007 ...
Virtual Private Networking: An Overview
... Because of the lack of privacy, frame-relay ultimately has proved unacceptable to many companies needing wide-area connectivity. Network security experts are quick to warn against trusting the infrastructure your frame-relay circuits cross, as they can become vulnerable to redirection, and more comm ...
... Because of the lack of privacy, frame-relay ultimately has proved unacceptable to many companies needing wide-area connectivity. Network security experts are quick to warn against trusting the infrastructure your frame-relay circuits cross, as they can become vulnerable to redirection, and more comm ...
PowerPoint slides - University of Calgary
... unique address (Internet Protocol/IP Address). •Internet service providers purchase a number of addresses for their computers and for the computers of their subscribers. •When you turn on your computer and modem an IP address is assigned to your computer from your ISP: - Dynamic addressing ...
... unique address (Internet Protocol/IP Address). •Internet service providers purchase a number of addresses for their computers and for the computers of their subscribers. •When you turn on your computer and modem an IP address is assigned to your computer from your ISP: - Dynamic addressing ...
Securing TCP/IP
... reliability of guaranteed datagram delivery. It merely makes a best effort to deliver a packet from one process to another. It is up to higher level software to provide reliability, if desired. The major advantage to UDP is the extremely low overhead involved in connectionless communications. UDP da ...
... reliability of guaranteed datagram delivery. It merely makes a best effort to deliver a packet from one process to another. It is up to higher level software to provide reliability, if desired. The major advantage to UDP is the extremely low overhead involved in connectionless communications. UDP da ...