PowerPoint version
... far as outside word is concerned: no need to be allocated range of addresses from ISP: - just one IP address is used for all devices can change addresses of devices in local network without notifying outside world can change ISP without changing addresses of devices in local network devices ...
... far as outside word is concerned: no need to be allocated range of addresses from ISP: - just one IP address is used for all devices can change addresses of devices in local network without notifying outside world can change ISP without changing addresses of devices in local network devices ...
There are many ways to describe and analyze data communications
... of routers located throughout the world and maintained by governments, private enterprise, non-profit organizations, and other entities. Routers work by taking data in the form of e-mail, web browser requests, and file transfers and delivering these data items to their appropriate destinations. More ...
... of routers located throughout the world and maintained by governments, private enterprise, non-profit organizations, and other entities. Routers work by taking data in the form of e-mail, web browser requests, and file transfers and delivering these data items to their appropriate destinations. More ...
Cisco Catalyst 3524-PWR Desktop Switch with Inline
... priority, and ensure that a network can immediately recover from network convergence or power failures, will help ready LANs for advanced Internet applications. The Catalyst 3524-PWR XL is the industry’s first shipping desktop LAN switch with advanced features for converged networks, such as advance ...
... priority, and ensure that a network can immediately recover from network convergence or power failures, will help ready LANs for advanced Internet applications. The Catalyst 3524-PWR XL is the industry’s first shipping desktop LAN switch with advanced features for converged networks, such as advance ...
Classful IP Addresses
... – Private networks are IP networks that are not part of the public Internet – IP addresses need to be unique only within the same private network • Systems on different private networks can re-use addresses – When packets cross between private network and public Internet, IP addresses in header must ...
... – Private networks are IP networks that are not part of the public Internet – IP addresses need to be unique only within the same private network • Systems on different private networks can re-use addresses – When packets cross between private network and public Internet, IP addresses in header must ...
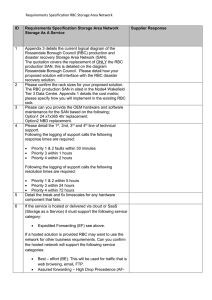
Appendix 2. Requirements Specification RBC Storage Area Network
... commands in order to deal with any priority 1 issues where the Telephony is down. This support will include the continuous monitoring of all network communications infrastructure including SIPS, carrier circuits, Internet provision, ISDN’s, switches, routers, firewalls, VPN’s, virtual cloud etc. The ...
... commands in order to deal with any priority 1 issues where the Telephony is down. This support will include the continuous monitoring of all network communications infrastructure including SIPS, carrier circuits, Internet provision, ISDN’s, switches, routers, firewalls, VPN’s, virtual cloud etc. The ...
XORs in the Air: Practical Wireless Network Coding
... ◦ COPE does not work well with hidden terminals. Without hidden terminals, TCP’s throughput increases by an average of 38% ◦ Network Coding is useful for throughput improvement, but COPE introduces coding as a practical tool that can be integrated with forwarding, routing and reliable delivery. ...
... ◦ COPE does not work well with hidden terminals. Without hidden terminals, TCP’s throughput increases by an average of 38% ◦ Network Coding is useful for throughput improvement, but COPE introduces coding as a practical tool that can be integrated with forwarding, routing and reliable delivery. ...
PPT - Suraj @ LUMS
... Router receives an IP datagram with network portion N and destination D If N is directly connected Transmit on that network Else If host specific entry for D exists Use next hop in that entry Else If route entry for N exists Use next hop in that entry Else If default route for next hop exists ...
... Router receives an IP datagram with network portion N and destination D If N is directly connected Transmit on that network Else If host specific entry for D exists Use next hop in that entry Else If route entry for N exists Use next hop in that entry Else If default route for next hop exists ...
Document
... • The OSPF is similar to RIP however, it allows the admin the ability to assign a cost or metric to each route. • The metric can be based on a type of service (ie . Min delay, max throughput, etc..) • For OSPF, a router will have multiple routing tables – one for each TOS • Unlike RIP, sharing or up ...
... • The OSPF is similar to RIP however, it allows the admin the ability to assign a cost or metric to each route. • The metric can be based on a type of service (ie . Min delay, max throughput, etc..) • For OSPF, a router will have multiple routing tables – one for each TOS • Unlike RIP, sharing or up ...
What is the Grid?
... • Technical inability to provision individual (per-flow) QoS – “normal“ Internet users • unlimited number of flows come and go at any time • heterogeneous traffic mix – Grid users • number of members in a “virtual team“ may be limited • clear distinction between bulk data transfer and SOAP messages ...
... • Technical inability to provision individual (per-flow) QoS – “normal“ Internet users • unlimited number of flows come and go at any time • heterogeneous traffic mix – Grid users • number of members in a “virtual team“ may be limited • clear distinction between bulk data transfer and SOAP messages ...
ITC2015 Advanced Network Tap application for
... – network tap latency in TAP mode, will not depend on the network load on the Inline Tap. – The Inline Tap latency depends on the port speed, packet length and a general static latency of a few microseconds. – The network tap latency in case the Inline Tap is running in BYPASS mode, is close to zero ...
... – network tap latency in TAP mode, will not depend on the network load on the Inline Tap. – The Inline Tap latency depends on the port speed, packet length and a general static latency of a few microseconds. – The network tap latency in case the Inline Tap is running in BYPASS mode, is close to zero ...
The Petabit Routing Company - Home Page
... Telecommunications Magazine June 2001 Telecommunications Magazine Selects Hyperchip for Technological Prowess, Impressive Management Team and Financial Stability ...
... Telecommunications Magazine June 2001 Telecommunications Magazine Selects Hyperchip for Technological Prowess, Impressive Management Team and Financial Stability ...
Automation of Batch Vacuum Pans At D.R.B.C Sugar Factory
... window size of the sender to 0 - Choking Maintain TCP end-to-end semantics Packet loss due to error bits is propagated to sender Freeze TCP True end-to-end scheme and does not require the involvement of any intermediaries (such as base stations) for flow control Changes in TCP code are restricted to ...
... window size of the sender to 0 - Choking Maintain TCP end-to-end semantics Packet loss due to error bits is propagated to sender Freeze TCP True end-to-end scheme and does not require the involvement of any intermediaries (such as base stations) for flow control Changes in TCP code are restricted to ...
gdfgdfgfggdf - personal.kent.edu
... demodulates signals for transmission and reception via cable wiring Cable modems operate at the Physical and Data Link layer of the OSI Model, and therefore do not manipulate higher-layer protocols such as IP or IPX To provide Internet access through its network, the cable company must upgrade its e ...
... demodulates signals for transmission and reception via cable wiring Cable modems operate at the Physical and Data Link layer of the OSI Model, and therefore do not manipulate higher-layer protocols such as IP or IPX To provide Internet access through its network, the cable company must upgrade its e ...
Introduction to networking, protocol layers, TCP/IP protocol suite
... first packet length = 620 = 20 new IP header + 600 old data, offset 0 second packet length = 620 = 20 new IP header + 600 old data, offset 600 third packet length = 220 = 20 new IP header + 200 old data, offset 1200 the new fragments have the same unique frag id as the original why? ...
... first packet length = 620 = 20 new IP header + 600 old data, offset 0 second packet length = 620 = 20 new IP header + 600 old data, offset 600 third packet length = 220 = 20 new IP header + 200 old data, offset 1200 the new fragments have the same unique frag id as the original why? ...
Optical Access Networks
... to reflections at the ends. The solution is to use Time Division Duplex (TDD) or different wavelengths, (1.3 and 1.55 µm, for example), which may be called Wavelength Division Duplex (WDD).. The cost of this solution grows linearly with the number of ONUs, and the operator must deploy and maintain a ...
... to reflections at the ends. The solution is to use Time Division Duplex (TDD) or different wavelengths, (1.3 and 1.55 µm, for example), which may be called Wavelength Division Duplex (WDD).. The cost of this solution grows linearly with the number of ONUs, and the operator must deploy and maintain a ...
Configuring the switch port.
... One of the first things to consider is whether or not there will be VLANs (virtual local area networks). While switches may break up collision domains, they do not break up broadcast domains. VLANs, on the other hand, will. VLANs take a single network environment and create smaller network segments ...
... One of the first things to consider is whether or not there will be VLANs (virtual local area networks). While switches may break up collision domains, they do not break up broadcast domains. VLANs, on the other hand, will. VLANs take a single network environment and create smaller network segments ...
No Slide Title
... • SMTP administers the transmission of e-mail over computer networks. It does not provide support for transmission of data other than plain text. Terminal emulation (Telnet): • Telnet provides the capability to remotely access another computer. It enables a user to log in to an Internet host and exe ...
... • SMTP administers the transmission of e-mail over computer networks. It does not provide support for transmission of data other than plain text. Terminal emulation (Telnet): • Telnet provides the capability to remotely access another computer. It enables a user to log in to an Internet host and exe ...
Virtual Private Network
... whole packet and adds a new IP packet that contains the encrypted packet. The new IP packet only identifies the destination’s encryption agent. When the IPSec packet arrives at the encryption agent, the new encrypted packet is stripped and the original packet continues to its destination. In Trans ...
... whole packet and adds a new IP packet that contains the encrypted packet. The new IP packet only identifies the destination’s encryption agent. When the IPSec packet arrives at the encryption agent, the new encrypted packet is stripped and the original packet continues to its destination. In Trans ...
CAT2000 GSM Evolution Towards UMTS
... GPRS expect to be able to offer higher data rates without building too many new sites. EDGE follows GPRS and allow a quick and cheap rollout of fast mobile service. GSM->GPRS->EDGE->UMTS: ...
... GPRS expect to be able to offer higher data rates without building too many new sites. EDGE follows GPRS and allow a quick and cheap rollout of fast mobile service. GSM->GPRS->EDGE->UMTS: ...
EECS 700: Network Security
... • Decrease TTL, recompute the checksum • If TTL = 0; drop the packet and send an error message to source ...
... • Decrease TTL, recompute the checksum • If TTL = 0; drop the packet and send an error message to source ...
Network Address Translation
... network to communicate over the internet. NAT recalculates checksums to account for changes in IP addresses and port numbers. When NAT is used, all traffic from the private network appears (to outside parties) to originate from the private network’s gateway. The classic NAT model translates an inter ...
... network to communicate over the internet. NAT recalculates checksums to account for changes in IP addresses and port numbers. When NAT is used, all traffic from the private network appears (to outside parties) to originate from the private network’s gateway. The classic NAT model translates an inter ...
Skype Network - National Taiwan University
... S. A. Baset and H. Schulzrinne, “An Analysis of the Skype Peer-to-Peer Internet Telephone Protocol, ” Dept. of CS, Columbia University, Sep. 15, 2004. Stephanos Androutsellis-Theotokis and Diomidis Spinellis,“A Survey of Peer-to-Peer Content Distribution Technologies,” Athens University of Economics ...
... S. A. Baset and H. Schulzrinne, “An Analysis of the Skype Peer-to-Peer Internet Telephone Protocol, ” Dept. of CS, Columbia University, Sep. 15, 2004. Stephanos Androutsellis-Theotokis and Diomidis Spinellis,“A Survey of Peer-to-Peer Content Distribution Technologies,” Athens University of Economics ...
IP: Routing and Subnetting
... Router receives an IP datagram with network portion N and destination D If N is directly connected Transmit on that network Else If host specific entry for D exists Use next hop in that entry Else If route entry for N exists Use next hop in that entry Else If default route for next hop exists ...
... Router receives an IP datagram with network portion N and destination D If N is directly connected Transmit on that network Else If host specific entry for D exists Use next hop in that entry Else If route entry for N exists Use next hop in that entry Else If default route for next hop exists ...
network-layer-addressing
... far as outside word is concerned: no need to be allocated range of addresses from ISP: - just one IP address is used for all devices can change addresses of devices in local network without notifying outside world can change ISP without changing addresses of devices in local network devices ...
... far as outside word is concerned: no need to be allocated range of addresses from ISP: - just one IP address is used for all devices can change addresses of devices in local network without notifying outside world can change ISP without changing addresses of devices in local network devices ...