Network Protocols
... A proxy ARP is a response by a node for another node that cannot respond at the time the request is made (e.g. the node is a mobiel node and not on its host net at the time, its home agent will respond in its stead). ...
... A proxy ARP is a response by a node for another node that cannot respond at the time the request is made (e.g. the node is a mobiel node and not on its host net at the time, its home agent will respond in its stead). ...
When you make a call… - Tufts Computer Science
... “This paper presents a design principle that helps guide placement of functions among the modules of a distributed computer system. The principle, called the end-to-end argument, suggests that functions placed at low levels of a system may be redundant or of little value when compared with the cost ...
... “This paper presents a design principle that helps guide placement of functions among the modules of a distributed computer system. The principle, called the end-to-end argument, suggests that functions placed at low levels of a system may be redundant or of little value when compared with the cost ...
Power Management for 4G Mobile Broadband Wireless
... offer the ease and convenience of internet applications like Email and Web browsing on the go is widespread. • Inevitably user expectations also rise in terms of higher data rates, instant internet connectivity and a much larger variety of applications to play with. • Mobile broadband technologies s ...
... offer the ease and convenience of internet applications like Email and Web browsing on the go is widespread. • Inevitably user expectations also rise in terms of higher data rates, instant internet connectivity and a much larger variety of applications to play with. • Mobile broadband technologies s ...
module_50
... Internetworking refers to a collection of interconnected networks that function as a singe network. Internetwork is abbreviated as internet. However, Internet refers to the world’s largest internetwork. Network layer performs: – Provides services to Layer 4 (Transport) including fragmentation and re ...
... Internetworking refers to a collection of interconnected networks that function as a singe network. Internetwork is abbreviated as internet. However, Internet refers to the world’s largest internetwork. Network layer performs: – Provides services to Layer 4 (Transport) including fragmentation and re ...
Network Layers
... Access methods such as CSMA/CD (carrier sensed multiple access with collision detection) ...
... Access methods such as CSMA/CD (carrier sensed multiple access with collision detection) ...
Overview of High Speed Network Technologies
... There are different types of switching techniques. The two most known switching techniques are: Circuit Switching does keep the resources reserved through the whole communication path before transmitting the information. Packet Switching does not keep the resources reserved through the whole communi ...
... There are different types of switching techniques. The two most known switching techniques are: Circuit Switching does keep the resources reserved through the whole communication path before transmitting the information. Packet Switching does not keep the resources reserved through the whole communi ...
Juniper Networks M-series : Product Overview
... that are designed to accelerate, extend, and optimize your highperformance networks. Our services allow you to maximize operational efficiency while reducing costs and minimizing risk, achieving a faster time to value for your network. Juniper Networks ensures operational excellence by optimizing th ...
... that are designed to accelerate, extend, and optimize your highperformance networks. Our services allow you to maximize operational efficiency while reducing costs and minimizing risk, achieving a faster time to value for your network. Juniper Networks ensures operational excellence by optimizing th ...
SC PE
... TUN/TAP device are delivered to a user-space program that attaches itself to the device. • A user-space program may pass packets into a TUN/TAP device. TUN/TAP device delivers (or "injects") these packets to the operating system network stack thus emulating their reception from an external source. ...
... TUN/TAP device are delivered to a user-space program that attaches itself to the device. • A user-space program may pass packets into a TUN/TAP device. TUN/TAP device delivers (or "injects") these packets to the operating system network stack thus emulating their reception from an external source. ...
ISDN over IP
... Please install the PC programming software AGFEO TK-Suite. Launch the program AGFEO TK-Suite Set. For the purpose of data backup please download the complete telephone system program and, if applicable, any TK-Suite Bill call history information and save these to disc or flash drive. Update the Tele ...
... Please install the PC programming software AGFEO TK-Suite. Launch the program AGFEO TK-Suite Set. For the purpose of data backup please download the complete telephone system program and, if applicable, any TK-Suite Bill call history information and save these to disc or flash drive. Update the Tele ...
chapter 10 - University of Windsor
... Protocol layering principle is violated. (TCP/UDP now must not change the port number without a corresponding change in NAT in the IP layer.) The Internet was designed for peer-to-peer functions. (Napster music exchange based onpeer-to-peer functions. ) NATs assumption: Machines within the use ...
... Protocol layering principle is violated. (TCP/UDP now must not change the port number without a corresponding change in NAT in the IP layer.) The Internet was designed for peer-to-peer functions. (Napster music exchange based onpeer-to-peer functions. ) NATs assumption: Machines within the use ...
Mobile IP: Introduction
... – Hawaii nodes are IP routers Assume intra-domain routing protocol is operating in the access network, allowing each node to have routes to other nodes The routing information is used to exchange explicit signaling messages, and forward packets between old and new access points during handoff ...
... – Hawaii nodes are IP routers Assume intra-domain routing protocol is operating in the access network, allowing each node to have routes to other nodes The routing information is used to exchange explicit signaling messages, and forward packets between old and new access points during handoff ...
Gnutella Network - University of Chicago
... o Reliability. External attacks should not cause significant data or performance loss. o Anonymity. Anonymity is valued as a means to protect privacy of people seeking or providing information that may not be popular. Gnutella nodes, called servents by developers, perform tasks normally associated w ...
... o Reliability. External attacks should not cause significant data or performance loss. o Anonymity. Anonymity is valued as a means to protect privacy of people seeking or providing information that may not be popular. Gnutella nodes, called servents by developers, perform tasks normally associated w ...
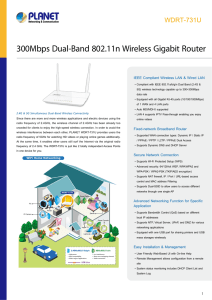
300Mbps Dual-Band 802.11n Wireless Gigabit Router
... The WDRT-731U supports NAT function allowing multiple users to access Internet via a single legal IP. It also provides Virtual Server for the specific LAN PC to act as an application server and offer certain service to the clients on the Internet. In addition, the powerful firewall protects your Int ...
... The WDRT-731U supports NAT function allowing multiple users to access Internet via a single legal IP. It also provides Virtual Server for the specific LAN PC to act as an application server and offer certain service to the clients on the Internet. In addition, the powerful firewall protects your Int ...
Network+ Guide to Networks 6th Edition
... • Abbreviations for multiple fields with zero values • 00FF can be abbreviated FF • 0000 can be abbreviated 0 ...
... • Abbreviations for multiple fields with zero values • 00FF can be abbreviated FF • 0000 can be abbreviated 0 ...
Computer Networks
... Computers can “manipulate” information Networks create “access” to information ...
... Computers can “manipulate” information Networks create “access” to information ...
Australia - Broadband Market - Insights, Statistics and Forecasts Brochure
... 1.3.1 Australian Bureau of Statistics (ABS) Survey – update December 2013 1.3.2 Statistical information by technology 1.3.3 Broadband speeds 1.3.4 Broadband traffic 1.4 ISP market overview 1.4.1 The market going into 2014 1.4.2 Data limiting 1.4.3 ISP market statistics 1.4.4 ISPs contracting but som ...
... 1.3.1 Australian Bureau of Statistics (ABS) Survey – update December 2013 1.3.2 Statistical information by technology 1.3.3 Broadband speeds 1.3.4 Broadband traffic 1.4 ISP market overview 1.4.1 The market going into 2014 1.4.2 Data limiting 1.4.3 ISP market statistics 1.4.4 ISPs contracting but som ...
University of Tehran
... » efforts to add QoS and multicast signaling capabilities to IP » introduction of hardware switching techniques in IP routers » improved congestion control mechanisms for data in ATM » extending ATM multicast to support manyto-many Univ. of Tehran ...
... » efforts to add QoS and multicast signaling capabilities to IP » introduction of hardware switching techniques in IP routers » improved congestion control mechanisms for data in ATM » extending ATM multicast to support manyto-many Univ. of Tehran ...
CEN 4500C Computer Networks Fundamentals
... have source port number x and destination port number y. What are the source and destination port numbers for the segments sent from B to A? (2 points) Source port number y and destination port number x. R4. Describe why an application developer might choose to run an application over UDP rather tha ...
... have source port number x and destination port number y. What are the source and destination port numbers for the segments sent from B to A? (2 points) Source port number y and destination port number x. R4. Describe why an application developer might choose to run an application over UDP rather tha ...
module_71
... Performance If processing speed cannot keep up with network traffic, some packets will not be examined This can make IDSs useless during DoS attacks ...
... Performance If processing speed cannot keep up with network traffic, some packets will not be examined This can make IDSs useless during DoS attacks ...
HEAnet`s UCLP Contact
... • Ethernet Relay Service (ERS) is a point-to-point VLANbased EVC. It is presented to the user as an 802.1q trunk which filters customer Layer 2 control protocols and uses the different customer VLAN IDs to direct customer traffic to different destinations. ERS is a non-transparent service, which mea ...
... • Ethernet Relay Service (ERS) is a point-to-point VLANbased EVC. It is presented to the user as an 802.1q trunk which filters customer Layer 2 control protocols and uses the different customer VLAN IDs to direct customer traffic to different destinations. ERS is a non-transparent service, which mea ...
PowerPoint
... How IP Addresses Are Assigned •Because of IP addresses the Internet is not an anonymous network! •Internet service providers purchase a number of addresses for their computers and for the computers of their subscribers. •When you turn on your computer and modem an IP address is assigned to your com ...
... How IP Addresses Are Assigned •Because of IP addresses the Internet is not an anonymous network! •Internet service providers purchase a number of addresses for their computers and for the computers of their subscribers. •When you turn on your computer and modem an IP address is assigned to your com ...