H3C S5820X Series 10-Gigabit Switches
... technology, which can work in 1/10 gbps mode depending on user requirements. As capacity is needed, users can upgrade to 10 gigabit Ethernet throughput to increase performance and protect their network infrastructure investment. Integrated Network Services with support for embedded applications, S58 ...
... technology, which can work in 1/10 gbps mode depending on user requirements. As capacity is needed, users can upgrade to 10 gigabit Ethernet throughput to increase performance and protect their network infrastructure investment. Integrated Network Services with support for embedded applications, S58 ...
Slides
... 802.1aq Shortest Path Bridging is being standardized by the IEEE as an evolution of the various spanning tree protocols. 802.1aq allows for true shortest path routing, multiple equal cost paths, much larger layer 2 topologies, faster convergence, vastly improved use of the mesh topology, single poin ...
... 802.1aq Shortest Path Bridging is being standardized by the IEEE as an evolution of the various spanning tree protocols. 802.1aq allows for true shortest path routing, multiple equal cost paths, much larger layer 2 topologies, faster convergence, vastly improved use of the mesh topology, single poin ...
GSM7324 Product Training - Layer 3+ Managed Switch -
... • As simple as listening for the default route from the network ...
... • As simple as listening for the default route from the network ...
PPT - mrazian.com
... walkthrough: send datagram from A to B via R focus on addressing – at IP (datagram) and MAC layer (frame) assume A knows B’s IP address assume A knows IP address of first hop router, R (how?) assume A knows R’s MAC address (how?) ...
... walkthrough: send datagram from A to B via R focus on addressing – at IP (datagram) and MAC layer (frame) assume A knows B’s IP address assume A knows IP address of first hop router, R (how?) assume A knows R’s MAC address (how?) ...
semestr 3 - final
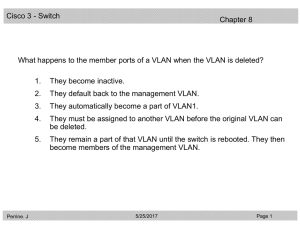
... VLANs can not be deleted until all ports have been removed from the VLAN assignment. VLANs can only be deleted by the user that created them. VLAN 1 can not be deleted until another VLAN has been assigned its duties. *** VLAN1 is the management VLAN by default and can not be deleted. The command was ...
... VLANs can not be deleted until all ports have been removed from the VLAN assignment. VLANs can only be deleted by the user that created them. VLAN 1 can not be deleted until another VLAN has been assigned its duties. *** VLAN1 is the management VLAN by default and can not be deleted. The command was ...
pptx - Brown Computer Science
... so packet can reach every LAN. First the root must be selected. By ID, it is elected. Least cost paths from root are traced. In the tree, these paths are placed. A mesh is made by folks like me, then bridges find a spanning tree. Radia Perlman ...
... so packet can reach every LAN. First the root must be selected. By ID, it is elected. Least cost paths from root are traced. In the tree, these paths are placed. A mesh is made by folks like me, then bridges find a spanning tree. Radia Perlman ...
VLAN und MPLS, Firewall und NAT, Wiederholung
... single broadcast domain: all layer-2 broadcast traffic (ARP, DHCP, unknown location of destination MAC address) must cross entire LAN security/privacy, efficiency issues Link Layer 5-3 ...
... single broadcast domain: all layer-2 broadcast traffic (ARP, DHCP, unknown location of destination MAC address) must cross entire LAN security/privacy, efficiency issues Link Layer 5-3 ...
20088-2 CCNA3 3.1-08 Questions VLAN
... If the destination port is unknown, a bridge will flood the frame to all ports in the broadcast domain, except for the source port. ...
... If the destination port is unknown, a bridge will flood the frame to all ports in the broadcast domain, except for the source port. ...
The California Institute for Telecommunications and
... – Fixed templates for each switch/router model – Templates are extended depending on configuration needed ...
... – Fixed templates for each switch/router model – Templates are extended depending on configuration needed ...
10/100/1000 and Gig-E Testing SmartClass™ Ethernet
... SmartClass Ethernet offers a unique, economical combination of feature-specific functionality, while providing an easy-touse, cost-effective Ethernet solution for physical layer cable testing, layer 2 and layer 3 traffic generation, and full RFC-2544 testing. Rugged, battery-operated, and applicatio ...
... SmartClass Ethernet offers a unique, economical combination of feature-specific functionality, while providing an easy-touse, cost-effective Ethernet solution for physical layer cable testing, layer 2 and layer 3 traffic generation, and full RFC-2544 testing. Rugged, battery-operated, and applicatio ...
Installing Template Theme Files
... is for IT Staff only to configure the network. A separate VLAN provides additional security for your network. Users will not be able to access the configuration for network devices Cisco Confidential ...
... is for IT Staff only to configure the network. A separate VLAN provides additional security for your network. Users will not be able to access the configuration for network devices Cisco Confidential ...
5780 Part-1 Spring 2001 - University of North Texas
... that interconnects and manages the telecommunications wiring between itself and any number of IDFs (Intermediate Distribution Frames). Unlike an IDF, which connects internal lines to the MDF, the MDF connects private or public lines coming into a building with the internal network. For example, an e ...
... that interconnects and manages the telecommunications wiring between itself and any number of IDFs (Intermediate Distribution Frames). Unlike an IDF, which connects internal lines to the MDF, the MDF connects private or public lines coming into a building with the internal network. For example, an e ...
Layer 2 Network Design
... physical location or connections to the network. All workstations and servers used by a particular workgroup share the same VLAN, regardless of the physical connection or location. ...
... physical location or connections to the network. All workstations and servers used by a particular workgroup share the same VLAN, regardless of the physical connection or location. ...
100-101 (ICND1) - Galaxy Computer Education
... exam includes topics on the Operation of IP Data Networks; LAN Switching Technologies; IP Addressing (IPv4 & IPv6); IP Routing Technologies; IP Services (DHCP, NAT, ACLs); Network ...
... exam includes topics on the Operation of IP Data Networks; LAN Switching Technologies; IP Addressing (IPv4 & IPv6); IP Routing Technologies; IP Services (DHCP, NAT, ACLs); Network ...
Sybex CCNA 640-802 Chapter 1: Internetworking Instructor
... LAN traffic congestion: •Too many hosts in a broadcast domain •Broadcast storms •Multicasting •Low bandwidth •Adding hubs for connectivity to the network •A bunch of ARP or IPX traffic (IPX is a Novell protocol that is like IP, but really, really chatty. Typically not used in today’s networks.) ...
... LAN traffic congestion: •Too many hosts in a broadcast domain •Broadcast storms •Multicasting •Low bandwidth •Adding hubs for connectivity to the network •A bunch of ARP or IPX traffic (IPX is a Novell protocol that is like IP, but really, really chatty. Typically not used in today’s networks.) ...
Layer and Subnetting1
... • Network interface of hosts. • Build-in physical address. • Layer 2 device. ...
... • Network interface of hosts. • Build-in physical address. • Layer 2 device. ...
Software-Defined Networks: Incremental Deployment with
... from or is directed to SDNc ports can be defined exclusively at the SDN switches. – Effectively limit added complexity ...
... from or is directed to SDNc ports can be defined exclusively at the SDN switches. – Effectively limit added complexity ...
S5700-EI Series Gigabit Enterprise Switches
... • The S5700-EI provides multiple security measures to defend against Denial of Service (DoS) attacks, and attacks against networks or users. DoS attack types include SYN Flood attacks, Land attacks, Smurf attacks, and ICMP Flood attacks. Attacks to networks refer to STP BPDU/root attacks. Attacks t ...
... • The S5700-EI provides multiple security measures to defend against Denial of Service (DoS) attacks, and attacks against networks or users. DoS attack types include SYN Flood attacks, Land attacks, Smurf attacks, and ICMP Flood attacks. Attacks to networks refer to STP BPDU/root attacks. Attacks t ...
SMC1255TX / SMC1255TX/LP www.smc.com
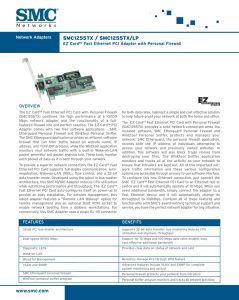
... Adapter comes with two free software applications – SMC Etherguard Personal Firewall and WinEtool Personal Sniffer. The SMC Etherguard application provides an efficient software firewall that can filter traffic based on website name, IP address, and TCP/UDP protocol, while the WinEtool application m ...
... Adapter comes with two free software applications – SMC Etherguard Personal Firewall and WinEtool Personal Sniffer. The SMC Etherguard application provides an efficient software firewall that can filter traffic based on website name, IP address, and TCP/UDP protocol, while the WinEtool application m ...
Measuring Next-Generation Networks: HOPI
... • As you glue together different technologies (L2+L1+MPLS+…) if there is a problem, finding that problem will be harder; • If you don’t use SONET at L1, indications from network are potentially fewer (or different); GFP operations and monitoring functions? ...
... • As you glue together different technologies (L2+L1+MPLS+…) if there is a problem, finding that problem will be harder; • If you don’t use SONET at L1, indications from network are potentially fewer (or different); GFP operations and monitoring functions? ...
Chp. 4, Part I - comp
... • An ARP request message is data-link broadcasted on the LAN with the target IP address. • Every IP host picks up a copy of the message and examine the target IP address. – If matching its IP address, send an ARP reply message back to the sender with its MAC address. – Else, drop the message. ...
... • An ARP request message is data-link broadcasted on the LAN with the target IP address. • Every IP host picks up a copy of the message and examine the target IP address. – If matching its IP address, send an ARP reply message back to the sender with its MAC address. – Else, drop the message. ...
LAN Overview
... incorporates logic to function as multiport bridge new installations typically include layer 2 switches with bridge functionality rather than bridges ...
... incorporates logic to function as multiport bridge new installations typically include layer 2 switches with bridge functionality rather than bridges ...
ConnectX®-3 EN
... Clustered databases, web infrastructure, and high frequency trading are just a few applications that will achieve significant throughput and latency improvements resulting in faster access, real-time response and more users per server. ConnectX-3 EN improves network performance by increasing availab ...
... Clustered databases, web infrastructure, and high frequency trading are just a few applications that will achieve significant throughput and latency improvements resulting in faster access, real-time response and more users per server. ConnectX-3 EN improves network performance by increasing availab ...