* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Chp. 4, Part I - comp
Asynchronous Transfer Mode wikipedia , lookup
Wireless security wikipedia , lookup
Distributed firewall wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Internet protocol suite wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Network tap wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Point-to-Point Protocol over Ethernet wikipedia , lookup
Computer network wikipedia , lookup
Airborne Networking wikipedia , lookup
Virtual LAN wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
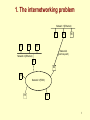
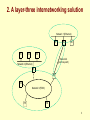
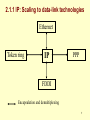
Chapter 4: Internetworking (Introduction) Dr. Rocky K. C. Chang 16 March 2004 1 1. The internetworking problem • Problem: How to interconnect heterogeneous networks effectively? • Three problems with interconnection at the data-link layer: – Do not scale to the number of data-link technologies. – Do not scale to the number of hosts (or networks). – Do not have a common addressing space. 2 1. The internetworking problem Network 1 (Ethernet) H7 H2 H1 S3 H8 H3 Network 4 (point-to-point) Network 2 (Ethernet) S1 S2 H4 Network 3 (FDDI) H5 H6 3 1.1 Scaling to data-link technologies • Conversion between frame structures. • Scalability problem as the number of data-link technologies supported increases, e.g., Ethernet PPP Token ring FDDI Frame conversion 4 1.2 Scaling to the network size • A switched LAN is a “flat” network---A single broadcast frame reaches every LAN. – VLAN can relieve this problem at the expense of managing VLAN membership. • Spanning tree protocol does not scale well to the network size. – Take a longer time for the protocol to converge. – Take a longer time to respond to network state changes. 5 1.3 Uncommon MAC address space • The number of bits used in a MAC address may differ. – 48-bit IEEE MAC addresses – IBM recommends another locally administered MAC addresses (overriding the burned-in MAC addresses). • Each address in a data-link technology must be universally unique, but its uniqueness is not guaranteed when several networks are bridged. 6 2. A layer-three internetworking solution • Use IP, XNS, IPX, etc on top of the networks. • Replace LAN switches with layer-three switches, more commonly known as routers. • Add IP software to each end host (with the whole protocol suite software). • Assign an IP address to each network interface. 7 2. A layer-three internetworking solution Network 1 (Ethernet) H7 H2 H1 R3 H8 H3 Network 4 (point-to-point) Network 2 (Ethernet) R1 R2 H4 Network 3 (FDDI) H5 H6 8 2.1.1 IP: Scaling to data-link technologies Ethernet Token ring IP PPP FDDI Encapsulation and demultiplexing 9 2.1.2 IP: Scaling to the network size • IP network uses hierarchy to achieve scalability. • There are at least three levels: – A single IP host (csultra6.comp.polyu.edu.hk) – A IP subnet (four subnets in comp.polyu.edu.hk) – An autonomous system (polyu.edu.hk) 10 2.1.3 IP: Uncommon MAC Address space • Create a logical (unicast) address space to identify network interfaces. • Classes A-C for unicast and a class D for 7 24 multicast: (a) (b) (c) 0 1 1 Network 0 1 Host 14 16 Network Host 0 21 8 Network Host 28 (d) 1 1 1 0 11 2.2 IP software at end hosts • The IP software mainly consists of modules for – – – – Application layer, such as DNS Transport layer: TCP, UDP Routing layer: IP, ICMP, and others. Data-link layer: MAC-IP-addresses binding Host names DNS ARP IP addresses MAC addresess RARP 12 2.2.1 An example www.sun.com 140.20.1.1 m1.sun.com 140.20.1.2 • A HTTP client is running in m1.sun.com to connect to a HTTP server at www.sun.com. • The DNS client at the m1.sun.com first obtains the IP address of www.sun.com. • The application data (HTTP+TCP) will then be encapsulated by an IP datagram with 13 2.2.1 An example – IP source address = 140.20.1.2 – IP destination address = 140.20.1.1 • Now m1.sun.com needs to run ARP to obtain the MAC address of www.sun.com’s network interface to the LAN. • The IP datagram is then encapsulated in an Ethernet frame with – MAC source address = that of m1.sun.com – MAC destination address = that of www.sun.com 14 2.2.2 IP software at routers • The software at routers is mainly used for routing and datagram forwarding. • Each router is running at least a “routing protocol” to construct a routing (or forwarding) table. – Each entry in a routing table consists of IP destination address and the next-hop’s IP address. • Upon receiving a datagram, a router forwards it based on a set of forwarding rules and the routing table. 15 2.3 Encapsulation and address binding • To transmit IP datagrams over any data-link network, two requirements are needed: – A standard way to encapsulate IP datagrams – Address resolution between IP addresses and MAC addresses • Standard RFCs for specifying datagram encapsulations and possibly address resolutions, e.g., Ethernet (RFC 894), IEEE 802 (RFC 1042), etc. • A shared medium uses an Address Resolution Protocol (ARP) for address binding. 16 2.3.1 Data encapsulation • You have seen – – – – IP over DIX Ethernet (slide 19 in Chapter 2, part I) IP over IEEE 802.3 (slide 22 in Chapter 2, part II) IP over PPP (slide 22 in Chapter 2, part I) IP over ATM via AAL 5 (slide 15 in Chapter 3, part III) Send out to the network interface 17 2.3.2 Address resolution protocol • An ARP request message is data-link broadcasted on the LAN with the target IP address. • Every IP host picks up a copy of the message and examine the target IP address. – If matching its IP address, send an ARP reply message back to the sender with its MAC address. – Else, drop the message. • To reduce broadcast traffic, each host uses an ARP cache to remember the recent binding. 18 2.3.2 Address resolution protocol 0 8 16 Hardware type = 1 HLen = 48 PLen = 32 31 ProtocolType = 0x0800 Operation SourceHardwareAddr (bytes 0 – 3) SourceHardwareAddr (bytes 4 – 5) SourceProtocolAddr (bytes 0 – 1) SourceProtocolAddr (bytes 2 – 3) TargetHardwareAddr (bytes 0 – 1) TargetHardwareAddr (bytes 2 – 5) TargetProtocolAddr (bytes 0 – 3) 19 2.4 An internetworking example • On each “hop or link,” both data encapsulation and address resolution occur. H1 H8 TCP R1 IP IP ETH R2 ETH R3 IP FDDI FDDI IP PPP PPP TCP IP ETH ETH 20