presentation PPT
... from multiple sources Difficult to reconcile sources Permanent need for IT support Delays in business processes ...
... from multiple sources Difficult to reconcile sources Permanent need for IT support Delays in business processes ...
Chapter 5 Business Intelligence: Data Warehousing, Data
... – Flat, two-dimensional tables with multiple access queries – Examines relations between multiple tables – Flexible, quick, and extendable with data independence ...
... – Flat, two-dimensional tables with multiple access queries – Examines relations between multiple tables – Flexible, quick, and extendable with data independence ...
Vector Data Model
... Designed for use with the 1990 U.S. Census Block-level maps – Points, lines & areas explicitly addressed – Census blocks can be retrieved directly by block number ...
... Designed for use with the 1990 U.S. Census Block-level maps – Points, lines & areas explicitly addressed – Census blocks can be retrieved directly by block number ...
Be my host: What to ask about free services that may be hosting your
... may be hosting your data The increasing use of third-party file-hosting services raises at least three questions worth considering BY RICHARD MARTINEZ, SAMUEL WALLING Traditionally, privacy and cybersecurity efforts have focused on how companies can protect their IT assets from intrusion. Literally ...
... may be hosting your data The increasing use of third-party file-hosting services raises at least three questions worth considering BY RICHARD MARTINEZ, SAMUEL WALLING Traditionally, privacy and cybersecurity efforts have focused on how companies can protect their IT assets from intrusion. Literally ...
Problems with the Traditional File Environment
... to reconstruct it. Now the organization is spending dollars and time to establish and maintain separate sets of data on the same entities because of program-data dependence. Lack of Flexibility: The Sales and Marketing manager needs information about his company’s new production schedule. However, ...
... to reconstruct it. Now the organization is spending dollars and time to establish and maintain separate sets of data on the same entities because of program-data dependence. Lack of Flexibility: The Sales and Marketing manager needs information about his company’s new production schedule. However, ...
Week 9 Question
... Linear regression determines the straight line that best fits the data. It doesn’t make the fit good. An exponential regression determines the exponential expression that best fits the data. It can have a poorer or a better fit than the linear fit for a given case. A complex regression may have a nu ...
... Linear regression determines the straight line that best fits the data. It doesn’t make the fit good. An exponential regression determines the exponential expression that best fits the data. It can have a poorer or a better fit than the linear fit for a given case. A complex regression may have a nu ...
Controlled medical vocabulary server
... healthcare terms so they can be interpreted and used correctly by the computer system. ...
... healthcare terms so they can be interpreted and used correctly by the computer system. ...
Hitachi Data Systems Upstream Oil and Gas Overview
... must resolve a business problem, which typically fulfills a step in a business process and fits within a defined workflow. Solutions range from simple to complex, involving collaboration of one or more ISVs, one or more IT infrastructure vendors, and the end-user’s business unit. Dealing with big da ...
... must resolve a business problem, which typically fulfills a step in a business process and fits within a defined workflow. Solutions range from simple to complex, involving collaboration of one or more ISVs, one or more IT infrastructure vendors, and the end-user’s business unit. Dealing with big da ...
Case Study – tcACCESS Operating System: OS/390 DB2 – IMS DL/I
... A very important log file is being maintained on that server. The log keeps track on error conditions and is also being used to control the accesses and the performance. These processes are being used by several hundred of the more than 3000 mainframe users. The Gateway-Server is a web-service that ...
... A very important log file is being maintained on that server. The log keeps track on error conditions and is also being used to control the accesses and the performance. These processes are being used by several hundred of the more than 3000 mainframe users. The Gateway-Server is a web-service that ...
D Data Mining: Payoffs and Pitfalls
... technology investments, and the dramatic drop in the cost/performance ratio of computer systems. Another reason is the rise of data warehousing. In the past, it was often necessary to gather the data, cleanse it, and merge it. Now, in many cases, the data are already sitting in a data warehouse read ...
... technology investments, and the dramatic drop in the cost/performance ratio of computer systems. Another reason is the rise of data warehousing. In the past, it was often necessary to gather the data, cleanse it, and merge it. Now, in many cases, the data are already sitting in a data warehouse read ...
Statistical Information System for Local Level Planning By Local
... software has been developed for storing the data. The system developed for this has the following features : The data collected during any survey period can be incorporated in the system. The data once stored can be updated as and when required – updating in the sense of revising the data if nec ...
... software has been developed for storing the data. The system developed for this has the following features : The data collected during any survey period can be incorporated in the system. The data once stored can be updated as and when required – updating in the sense of revising the data if nec ...
here - Temple Fox MIS
... – Customers receive incentives (average cost: $160) when account is opened – Giving new incentives to everyone who might leave is very expensive (as well as wasteful) – Bringing back a customer after they leave is both difficult and costly ...
... – Customers receive incentives (average cost: $160) when account is opened – Giving new incentives to everyone who might leave is very expensive (as well as wasteful) – Bringing back a customer after they leave is both difficult and costly ...
Presentation - Directorate of Valuation
... · Capture of export data in a standardized format on a daily basis from all customs stations. · Consolidation and analysis electronically by DOV to identify potential cases of valuation fraud · Export Valuation Tool and Decision Support System. · Check abuse of export incentive schemes based on expo ...
... · Capture of export data in a standardized format on a daily basis from all customs stations. · Consolidation and analysis electronically by DOV to identify potential cases of valuation fraud · Export Valuation Tool and Decision Support System. · Check abuse of export incentive schemes based on expo ...
Sirrix AG
... and insider threats. Targeted malware attacks and data leakages are the most visible examples of these increasing threats. Thus, time has come for a more comprehensive approach to endpoint security. Today, IT infrastructures are shared, distributed, and heterogeneous. They extend into cloud computin ...
... and insider threats. Targeted malware attacks and data leakages are the most visible examples of these increasing threats. Thus, time has come for a more comprehensive approach to endpoint security. Today, IT infrastructures are shared, distributed, and heterogeneous. They extend into cloud computin ...
Backup-Restore Instructions
... A much more subtle source of data loss is through data corruption which is usually caused by power failures and/or machines crashing, being turned off, or rebooted while the data tables are still open. Often the data corruption can go on for a long period of time after the initial corruption before ...
... A much more subtle source of data loss is through data corruption which is usually caused by power failures and/or machines crashing, being turned off, or rebooted while the data tables are still open. Often the data corruption can go on for a long period of time after the initial corruption before ...
Chapter 4: Database Management
... Database Design and Use • Data Mining (On-Line Analytical Processing) – Drill down from summary data to detailed data – Data Warehouses/Data Marts • Integrates many large databases into one repository ...
... Database Design and Use • Data Mining (On-Line Analytical Processing) – Drill down from summary data to detailed data – Data Warehouses/Data Marts • Integrates many large databases into one repository ...
380E_SP16_Week9
... • A discipline to help a variety of discipline with their information problems • By defining and developing technical and socio-technical solutions • That take the information life cycle of data and related objects into account ...
... • A discipline to help a variety of discipline with their information problems • By defining and developing technical and socio-technical solutions • That take the information life cycle of data and related objects into account ...
transparencies
... full access right to another physician or limited access right to a researcher. A physician may query the medical information system to find patient data. The patient or another physician may grant him the access. Researchers may access to blanked images if authorized by a physician who has access r ...
... full access right to another physician or limited access right to a researcher. A physician may query the medical information system to find patient data. The patient or another physician may grant him the access. Researchers may access to blanked images if authorized by a physician who has access r ...
Normalisation
... it is in the second normal form and there are no nonkey columns dependant on other non-key columns that could not act as the primary key. ...
... it is in the second normal form and there are no nonkey columns dependant on other non-key columns that could not act as the primary key. ...
SEER-Medicare
... The linkage of these two data sources results in a unique population-based source of information that can be used for an array of epidemiological and health services research. For example, investigators using this combined dataset have conducted studies on patterns of care for persons with cancer be ...
... The linkage of these two data sources results in a unique population-based source of information that can be used for an array of epidemiological and health services research. For example, investigators using this combined dataset have conducted studies on patterns of care for persons with cancer be ...
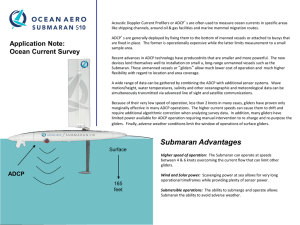
Submaran Ap Notes - Oceanology International North America
... prohibitive. To meet the market needs and relieve users from these capital and overhead costs, the industry has begun to move toward offering operational services. Ocean Aero believes that this operational service model is poised for rapid growth and is developing its own Robot as a Service (RaaS) m ...
... prohibitive. To meet the market needs and relieve users from these capital and overhead costs, the industry has begun to move toward offering operational services. Ocean Aero believes that this operational service model is poised for rapid growth and is developing its own Robot as a Service (RaaS) m ...
7910 Demonstrate knowledge of computer data types and
... ASCII refers to American Standard Code for Information Interchange, a 7-bit encoding standard enabling 128 characters (alphabetic, numeric, and special characters) to be represented inside a computer. A barcode is an optical, machine-readable, representation of data; the data usually describes somet ...
... ASCII refers to American Standard Code for Information Interchange, a 7-bit encoding standard enabling 128 characters (alphabetic, numeric, and special characters) to be represented inside a computer. A barcode is an optical, machine-readable, representation of data; the data usually describes somet ...
THE ANTARCTIC BIODIVERSITY INFORMATION FACILITY
... encompass the complexity of the potential impacts of these changes. Having an optimal access to data also allows addressing complex scientific questions on the biodiversity of Antarctica and its connectivity with the rest of the world. Our responsibility as scientists The Antarctic Treaty recognizes ...
... encompass the complexity of the potential impacts of these changes. Having an optimal access to data also allows addressing complex scientific questions on the biodiversity of Antarctica and its connectivity with the rest of the world. Our responsibility as scientists The Antarctic Treaty recognizes ...
7910 Demonstrate knowledge of computer data types and
... ASCII refers to American Standard Code for Information Interchange, a 7-bit encoding standard enabling 128 characters (alphabetic, numeric, and special characters) to be represented inside a computer. A barcode is an optical, machine-readable, representation of data; the data usually describes somet ...
... ASCII refers to American Standard Code for Information Interchange, a 7-bit encoding standard enabling 128 characters (alphabetic, numeric, and special characters) to be represented inside a computer. A barcode is an optical, machine-readable, representation of data; the data usually describes somet ...
Data center

A data center is a facility used to house computer systems and associated components, such as telecommunications and storage systems. It generally includes redundant or backup power supplies, redundant data communications connections, environmental controls (e.g., air conditioning, fire suppression) and various security devices. Large data centers are industrial scale operations using as much electricity as a small town.