Getting Started with PROC LOGISTIC
... 'event of interest' will occur as a linear function of one (or more) continuous and/or dichotomous independent variables, this technique is implemented in the SAS® System in PROC LOGISTIC. This paper gives an overview of how some common forms of logistic regression models can be implemented using PR ...
... 'event of interest' will occur as a linear function of one (or more) continuous and/or dichotomous independent variables, this technique is implemented in the SAS® System in PROC LOGISTIC. This paper gives an overview of how some common forms of logistic regression models can be implemented using PR ...
Web Data Mining Techniques and Implementation for Handling Big
... Web data mining technology is opening avenues on not just gathering data but it is also raising a lot of concerns related to data security. There is loads of personal information available on the internet and web data mining had helped to keep the idea of the need to secure that information at the f ...
... Web data mining technology is opening avenues on not just gathering data but it is also raising a lot of concerns related to data security. There is loads of personal information available on the internet and web data mining had helped to keep the idea of the need to secure that information at the f ...
p2p
... are zero-cost object lookups. – Theorem [3]: In a given graph G, the static placement problem is NP-complete, even if all the queries in the workload in G are object queries. • Proof of this theorem is based on a reduction from the vertexcover problem. ...
... are zero-cost object lookups. – Theorem [3]: In a given graph G, the static placement problem is NP-complete, even if all the queries in the workload in G are object queries. • Proof of this theorem is based on a reduction from the vertexcover problem. ...
ppt
... Compute distance from all points to all kcenters Assign each point to the nearest k-center Compute the average of all points assigned to all specific k-centers Replace the k-centers with the new averages ...
... Compute distance from all points to all kcenters Assign each point to the nearest k-center Compute the average of all points assigned to all specific k-centers Replace the k-centers with the new averages ...
Full text
... that vary smoothly over wide rangesof periods. However, both methods yield discontinuitiesin pzu where bands overlap at periods of 3 and 30 sec. These discontinuities will be discussed later, and it will be shown that they are not caused by systematic errors in data processing. The standardanalysis ...
... that vary smoothly over wide rangesof periods. However, both methods yield discontinuitiesin pzu where bands overlap at periods of 3 and 30 sec. These discontinuities will be discussed later, and it will be shown that they are not caused by systematic errors in data processing. The standardanalysis ...
Presentation
... • Versions 1.* and 2.* were developed by an informal network of individuals from the social science community and official statistics – Funding was through grants ...
... • Versions 1.* and 2.* were developed by an informal network of individuals from the social science community and official statistics – Funding was through grants ...
ppt - hkust cse
... Y3=s0: Same attitude toward C-Gov and C-Bus People who are touch on corruption are equally tough toward C-Gov and C-Bus. People who are relaxed about corruption are more relaxed toward C-Bus than C-GOv ...
... Y3=s0: Same attitude toward C-Gov and C-Bus People who are touch on corruption are equally tough toward C-Gov and C-Bus. People who are relaxed about corruption are more relaxed toward C-Bus than C-GOv ...
Slide 1
... • Policy-based management provides the ability to define policies that apply to servers, databases, and other objects in your data environment. • Well-defined policies can help administrators to control and manage change proactively within the data services environment. ...
... • Policy-based management provides the ability to define policies that apply to servers, databases, and other objects in your data environment. • Well-defined policies can help administrators to control and manage change proactively within the data services environment. ...
PowerPoint Template
... Venn diagrams have found a new business opportunity and we have defined the target ...
... Venn diagrams have found a new business opportunity and we have defined the target ...
Churn Analysis Case Study
... customer will churn away before the company can fully recoup its acquisition costs. It is clear that spending money holding on to existing customers is more efficient than acquiring new customers. Consequently, churn management has emerged as a crucial competitive weapon, and a foundation for an en ...
... customer will churn away before the company can fully recoup its acquisition costs. It is clear that spending money holding on to existing customers is more efficient than acquiring new customers. Consequently, churn management has emerged as a crucial competitive weapon, and a foundation for an en ...
Temporal Relational Calculus
... attributes by appropriately modifying or relaxing the requirements on the structure of relation schemas (see the entry Point-stamped Temporal Models). An interesting observation is that a variant of TRC, in which temporal variables range over intervals and that utilizes Allen’s interval relations as ...
... attributes by appropriately modifying or relaxing the requirements on the structure of relation schemas (see the entry Point-stamped Temporal Models). An interesting observation is that a variant of TRC, in which temporal variables range over intervals and that utilizes Allen’s interval relations as ...
Change Detection in Multivariate Datastreams: Likelihood
... Even though this problem is of utmost relevance in datastream mining, no theoretical or experimental study investigate how the data dimension d impacts on the change detectability. In Section 3, we consider change-detection problems in Rd and investigate how d affects the detectability of a change w ...
... Even though this problem is of utmost relevance in datastream mining, no theoretical or experimental study investigate how the data dimension d impacts on the change detectability. In Section 3, we consider change-detection problems in Rd and investigate how d affects the detectability of a change w ...
Identifying and Overcoming Common Data Mining Mistakes
... Using a categorical variable with too many levels often results in performance problems. This is a common reason why model processing slows to a crawl or even stops in some cases. This has nothing to do with the software and everything to do with the way in which categorical variables must be estima ...
... Using a categorical variable with too many levels often results in performance problems. This is a common reason why model processing slows to a crawl or even stops in some cases. This has nothing to do with the software and everything to do with the way in which categorical variables must be estima ...
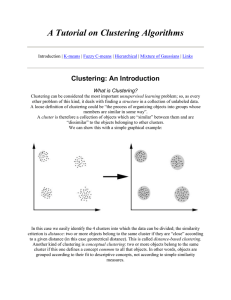
A Tutorial on Clustering Algorithms
... idea is to define k centroids, one for each cluster. These centroids shoud be placed in a cunning way because of different location causes different result. So, the better choice is to place them as much as possible far away from each other. The next step is to take each point belonging to a given d ...
... idea is to define k centroids, one for each cluster. These centroids shoud be placed in a cunning way because of different location causes different result. So, the better choice is to place them as much as possible far away from each other. The next step is to take each point belonging to a given d ...
The promise of graph databases in public health is web-scale discovery.
... the graphic below is where the richness lies. Entities can also have attributes, such as keys to identify them, but verb-style relationships in this sense describe the entities in a richer way than simple identifiers or other labels do. And those relationships can be mined in ways most conventional ...
... the graphic below is where the richness lies. Entities can also have attributes, such as keys to identify them, but verb-style relationships in this sense describe the entities in a richer way than simple identifiers or other labels do. And those relationships can be mined in ways most conventional ...
Part 2: Decision Support Systems
... A DSS is an interactive, flexible, and adaptable CBIS, specially developed for supporting the solution of a non-structured management problem for improved decision making. It utilizes data, it provides easy user interface, and it allows for the decision maker’s own insights ...
... A DSS is an interactive, flexible, and adaptable CBIS, specially developed for supporting the solution of a non-structured management problem for improved decision making. It utilizes data, it provides easy user interface, and it allows for the decision maker’s own insights ...
A Web Usage Mining Framework for Business Intelligence
... This paper introduces the basic ideas of Recommender system and importance of web usage mining in business intelligence. Recommender systems have emerged as powerful tools for helping customers find items of interest. The research work existing in this paper makes several contributions to the framew ...
... This paper introduces the basic ideas of Recommender system and importance of web usage mining in business intelligence. Recommender systems have emerged as powerful tools for helping customers find items of interest. The research work existing in this paper makes several contributions to the framew ...
R measurement and QCD study in the full BEPCII energy region
... integrated luminosity had: detection efficiency for Nhad ...
... integrated luminosity had: detection efficiency for Nhad ...
Identifying and Overcoming Common Data Mining Mistakes
... one nontrivial level. If only one dominant level appears, the variable is highly likely to be useless in any model since a large portion of the observations cannot be differentiated with respect to this variable. However, in the case of modeling rare events, it is still possible that an infrequently ...
... one nontrivial level. If only one dominant level appears, the variable is highly likely to be useless in any model since a large portion of the observations cannot be differentiated with respect to this variable. However, in the case of modeling rare events, it is still possible that an infrequently ...
The Role of Database Management Systems for Investigative Data
... In considering a few of the presently most widely used commercial systems, we will classify them by the type of model they implement (hierarchical, network or relational) and by the type of physical access method they use. Access methods are primarily of two types: physically linked DBMS and inverte ...
... In considering a few of the presently most widely used commercial systems, we will classify them by the type of model they implement (hierarchical, network or relational) and by the type of physical access method they use. Access methods are primarily of two types: physically linked DBMS and inverte ...
PDF - Wiley Online Library
... 2002) of cleaned and quality-controlled global magnetometer data, as well as the available IMF, solar wind, HPI, F10.7, and Dst data to produce an archive of AMIE runs at 1-min resolution [Ridley and Kihn, 2004]. The reasoning behind using these inputs for the period is that the data availability ac ...
... 2002) of cleaned and quality-controlled global magnetometer data, as well as the available IMF, solar wind, HPI, F10.7, and Dst data to produce an archive of AMIE runs at 1-min resolution [Ridley and Kihn, 2004]. The reasoning behind using these inputs for the period is that the data availability ac ...
Understanding Data Locality in Virtual SAN: VMware, Inc.
... and/or consume an inordinate amount of network resources. As a result, there is a considerable performance impact on a VM, for a while after vMotion is completed. Load balancing the compute resources (CPU and memory) in a cluster should not mean that one needs to also do expensive data moves. vSpher ...
... and/or consume an inordinate amount of network resources. As a result, there is a considerable performance impact on a VM, for a while after vMotion is completed. Load balancing the compute resources (CPU and memory) in a cluster should not mean that one needs to also do expensive data moves. vSpher ...
Lightning_SanFran_1-5_Shah_Azure
... Cloudly makes moving data in and out of clouds or data centers easy We address a problem that’s usually manual, labor intensive and time consuming ...
... Cloudly makes moving data in and out of clouds or data centers easy We address a problem that’s usually manual, labor intensive and time consuming ...
Yield Analysis and Product Quality
... Neither fabrication nor testing process is perfect hence non-zero DPM is a fact of life. DPM minimization is an important goal of quality-conscious companies. For commercial VLSI chips a DL greater than 500 dpm is considered unacceptable. ...
... Neither fabrication nor testing process is perfect hence non-zero DPM is a fact of life. DPM minimization is an important goal of quality-conscious companies. For commercial VLSI chips a DL greater than 500 dpm is considered unacceptable. ...
Data analysis

Analysis of data is a process of inspecting, cleaning, transforming, and modeling data with the goal of discovering useful information, suggesting conclusions, and supporting decision-making. Data analysis has multiple facets and approaches, encompassing diverse techniques under a variety of names, in different business, science, and social science domains.Data mining is a particular data analysis technique that focuses on modeling and knowledge discovery for predictive rather than purely descriptive purposes. Business intelligence covers data analysis that relies heavily on aggregation, focusing on business information. In statistical applications, some people divide data analysis into descriptive statistics, exploratory data analysis (EDA), and confirmatory data analysis (CDA). EDA focuses on discovering new features in the data and CDA on confirming or falsifying existing hypotheses. Predictive analytics focuses on application of statistical models for predictive forecasting or classification, while text analytics applies statistical, linguistic, and structural techniques to extract and classify information from textual sources, a species of unstructured data. All are varieties of data analysis.Data integration is a precursor to data analysis, and data analysis is closely linked to data visualization and data dissemination. The term data analysis is sometimes used as a synonym for data modeling.