Data Foresensics
... Repair file system, partition table, master boot record Hard disk recovery – one time recovery Recovering deleted files Often data is not removed, only the references to them in the file table ...
... Repair file system, partition table, master boot record Hard disk recovery – one time recovery Recovering deleted files Often data is not removed, only the references to them in the file table ...
Resume - RIT - People - Rochester Institute of Technology
... (PHP CodeIgniter, JavaScript, JQuery, Ajax, MySQL, WordPress, Apache, HTML, CSS, XML, Bootstrap, HighCharts.js, GIT, SVN, cPanel) Designed, developed and maintained the projects in PHP (CodeIgniter, WordPress framework) with MySQL back-end. Implemented JavaScript, jQuery and AJAX as per the projec ...
... (PHP CodeIgniter, JavaScript, JQuery, Ajax, MySQL, WordPress, Apache, HTML, CSS, XML, Bootstrap, HighCharts.js, GIT, SVN, cPanel) Designed, developed and maintained the projects in PHP (CodeIgniter, WordPress framework) with MySQL back-end. Implemented JavaScript, jQuery and AJAX as per the projec ...
NDLE 2016
... Computational Thinking and Data literacy Languages, literacy and communication Come to a conclusion of what country you are in by looking at a flowchart that asks questions as inputs on things like currency, landmarks, travel times to get there etc. Mathematics and numeracy Look at an algorithm to ...
... Computational Thinking and Data literacy Languages, literacy and communication Come to a conclusion of what country you are in by looking at a flowchart that asks questions as inputs on things like currency, landmarks, travel times to get there etc. Mathematics and numeracy Look at an algorithm to ...
Anomaly Detection vi..
... online applications which have computation or memory limitations. Compared with the well-known power method for PCA and other popular anomaly detection algorithms, our experimental results verify the feasibility of our proposed method in terms of both accuracy and efficiency. ...
... online applications which have computation or memory limitations. Compared with the well-known power method for PCA and other popular anomaly detection algorithms, our experimental results verify the feasibility of our proposed method in terms of both accuracy and efficiency. ...
Probability Distributions
... (You may use either the method of moments, or maximum likelihood, whichever you prefer) Plot a figure that shows the histogram and pdf of these distributions. b) For the month you are working with rank the data (from smallest to largest) and prepare a Q-Q plot (see preliminary data analysis powerpoi ...
... (You may use either the method of moments, or maximum likelihood, whichever you prefer) Plot a figure that shows the histogram and pdf of these distributions. b) For the month you are working with rank the data (from smallest to largest) and prepare a Q-Q plot (see preliminary data analysis powerpoi ...
Intro to Information Systems
... Lack of data integration Data dependence – files, storage devices, and software are dependent on each other Lack of data integrity or standardization ...
... Lack of data integration Data dependence – files, storage devices, and software are dependent on each other Lack of data integrity or standardization ...
Geometric Range Search on Encrypted Spatial Data Abstract
... privacy leakage to the third party. Searchable encryption is a technique to perform meaningful queries on encrypted data without revealing privacy. However, geometric range search on spatial data has not been fully investigated nor supported by existing searchable encryption schemes. In this paper, ...
... privacy leakage to the third party. Searchable encryption is a technique to perform meaningful queries on encrypted data without revealing privacy. However, geometric range search on spatial data has not been fully investigated nor supported by existing searchable encryption schemes. In this paper, ...
Chapter 10
... – New systems development and integration – Systems maintenance – Systems back-up and contingency planning – Electronic commerce – Control over computer operations ...
... – New systems development and integration – Systems maintenance – Systems back-up and contingency planning – Electronic commerce – Control over computer operations ...
Customer Marketing via Biometrics - I
... Complete Customer Internet Data hosting and reporting portal specifically designed for the restaurant industry. Using BIOMETRICS to record all repeat visitors Providing a central database that will store all customer records, across locations Internet to view transactions & customer data Providing a ...
... Complete Customer Internet Data hosting and reporting portal specifically designed for the restaurant industry. Using BIOMETRICS to record all repeat visitors Providing a central database that will store all customer records, across locations Internet to view transactions & customer data Providing a ...
Quantitative Literacy
... Analysis (IDA): Working with Sociology Department to Address the Quantitative Literacy Gap.” Teaching Sociology, 34: 23-38 • National Center for Educational Statistics. “National Assessment of Adult Literacy.” • Steen, Lynn. 1997. Why Numbers Count: Quantitative Literacy for Tomorrow’s America. New ...
... Analysis (IDA): Working with Sociology Department to Address the Quantitative Literacy Gap.” Teaching Sociology, 34: 23-38 • National Center for Educational Statistics. “National Assessment of Adult Literacy.” • Steen, Lynn. 1997. Why Numbers Count: Quantitative Literacy for Tomorrow’s America. New ...
BI Accelarator (BIA)
... • Redundant data store of a BI InfoCube on the BI accelerator server. • To improve the performance of BI queries when data is read from an InfoCube • Data of a BI InfoCube is made available as a BI accelerator index in a compressed but not aggregated form. • Consists of several, possibly split index ...
... • Redundant data store of a BI InfoCube on the BI accelerator server. • To improve the performance of BI queries when data is read from an InfoCube • Data of a BI InfoCube is made available as a BI accelerator index in a compressed but not aggregated form. • Consists of several, possibly split index ...
Product information: Interactive Analyzer
... Traditional methods of data quality assurance depend on the manual definition of filter criteria; therefore, they new or unexpected error patterns often slip through these filters. Interactive Analyzer provides a ‚hypothesis-free‘, autonomous method for detecting inconsistencies and data errors. ...
... Traditional methods of data quality assurance depend on the manual definition of filter criteria; therefore, they new or unexpected error patterns often slip through these filters. Interactive Analyzer provides a ‚hypothesis-free‘, autonomous method for detecting inconsistencies and data errors. ...
Measuring Information Architecture
... • Try to build a model of what is going on – Follow leads – Compare to previous situations ...
... • Try to build a model of what is going on – Follow leads – Compare to previous situations ...
Presentation - Directorate of Valuation
... · A comprehensive Database on Exports focusing on Valuation. · Capture of export data in a standardized format on a daily basis from all customs stations. · Consolidation and analysis electronically by DOV to identify potential cases of valuation fraud · Export Valuation Tool and Decision Support Sy ...
... · A comprehensive Database on Exports focusing on Valuation. · Capture of export data in a standardized format on a daily basis from all customs stations. · Consolidation and analysis electronically by DOV to identify potential cases of valuation fraud · Export Valuation Tool and Decision Support Sy ...
Drive pervasive business performance
... All rights reserved. Microsoft, Windows, Windows Vista and other product names are or may be registered trademarks and/or trademarks in the U.S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date o ...
... All rights reserved. Microsoft, Windows, Windows Vista and other product names are or may be registered trademarks and/or trademarks in the U.S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date o ...
Kennesaw, GA – Senior Environmental Database Analyst
... Collaborate with project teams and database manager to define specific project needs/requirements. ...
... Collaborate with project teams and database manager to define specific project needs/requirements. ...
A Database Management System (DBMS) for Monogenean
... fields. A well-designed database system is one of the most important tools for supporting biological data which includes a variety of different data types. However, in the life sciences field, some researchers are still using flat files and spreadsheets instead of an appropriate database management ...
... fields. A well-designed database system is one of the most important tools for supporting biological data which includes a variety of different data types. However, in the life sciences field, some researchers are still using flat files and spreadsheets instead of an appropriate database management ...
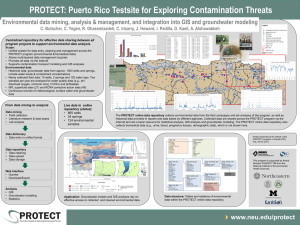
Environmental data mining, analysis & management, and integration
... Internet and are a basic resource for statistical analysis, GIS analysis and groundwater modeling. The PROTECT online data repository also collects biomedical data (e.g., urine, blood, pregnancy tissues, demographic data), which is not shown here. ...
... Internet and are a basic resource for statistical analysis, GIS analysis and groundwater modeling. The PROTECT online data repository also collects biomedical data (e.g., urine, blood, pregnancy tissues, demographic data), which is not shown here. ...
Architectural Constraints on Current Bioinformatics Integration
... Correlate transcription of interacting proteins. ...
... Correlate transcription of interacting proteins. ...
DATA WAREHOUSE IMPLEMENTATION
... Web based access through portals for Operational and Intraday reporting ...
... Web based access through portals for Operational and Intraday reporting ...
ppt - WMO
... • In many countries, data remains relatively inaccessible in hard copy format • Inappropriate data management – need sound systems, software, interoperability • Data should be exchanged internationally – but often isn’t. • Training needs: observations; analysis and interpretation; communications ...
... • In many countries, data remains relatively inaccessible in hard copy format • Inappropriate data management – need sound systems, software, interoperability • Data should be exchanged internationally – but often isn’t. • Training needs: observations; analysis and interpretation; communications ...
M.E.T.U. STATISTICS FALL 2011-2012 Dr. Ozlem Ilk STAT 462
... Dr. Ozlem Ilk STAT 462- Case Studies For each of the following datasets, read the data descriptions, decide on what type of data it is, the complexities that arise (missing data, correlation structure, the response and covariate types ...), the possible questions of interests, and appropriate approa ...
... Dr. Ozlem Ilk STAT 462- Case Studies For each of the following datasets, read the data descriptions, decide on what type of data it is, the complexities that arise (missing data, correlation structure, the response and covariate types ...), the possible questions of interests, and appropriate approa ...
From user demand to indicator – the example of labour market flow
... • Interaction terms where necessary • Bootstrap standard errors or use derived weights ...
... • Interaction terms where necessary • Bootstrap standard errors or use derived weights ...
Powerpoints
... additional analysis with more complex tools. ** Cannot use continuous data as an input Decision Tree – Used to predict outcomes based on past data, both discrete and continuous. Clustering – Used to segment the dataset. Use of a predictable outcome is not required. Makes it useful to detect anom ...
... additional analysis with more complex tools. ** Cannot use continuous data as an input Decision Tree – Used to predict outcomes based on past data, both discrete and continuous. Clustering – Used to segment the dataset. Use of a predictable outcome is not required. Makes it useful to detect anom ...
Data analysis

Analysis of data is a process of inspecting, cleaning, transforming, and modeling data with the goal of discovering useful information, suggesting conclusions, and supporting decision-making. Data analysis has multiple facets and approaches, encompassing diverse techniques under a variety of names, in different business, science, and social science domains.Data mining is a particular data analysis technique that focuses on modeling and knowledge discovery for predictive rather than purely descriptive purposes. Business intelligence covers data analysis that relies heavily on aggregation, focusing on business information. In statistical applications, some people divide data analysis into descriptive statistics, exploratory data analysis (EDA), and confirmatory data analysis (CDA). EDA focuses on discovering new features in the data and CDA on confirming or falsifying existing hypotheses. Predictive analytics focuses on application of statistical models for predictive forecasting or classification, while text analytics applies statistical, linguistic, and structural techniques to extract and classify information from textual sources, a species of unstructured data. All are varieties of data analysis.Data integration is a precursor to data analysis, and data analysis is closely linked to data visualization and data dissemination. The term data analysis is sometimes used as a synonym for data modeling.