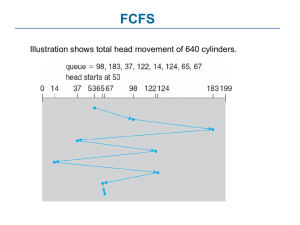
Big Data for Advanced Threat Protection
... sauce that makes it different/better than other solutions in the market. However, such obscure treatment of this all-important topic can also hide the fact that a solution is seriously deficient in its actual capabilities – perhaps that it’s focused primarily on the movement and management of data, ...
... sauce that makes it different/better than other solutions in the market. However, such obscure treatment of this all-important topic can also hide the fact that a solution is seriously deficient in its actual capabilities – perhaps that it’s focused primarily on the movement and management of data, ...
Slide 1
... 1. Create the UML model elements using the UML modeling tool. This is a painstaking task for any moderately complex real-world application. The application object model is essentially specified twice: as a UML Class model and as a UML Data model. The Class model corresponds to the objects in the app ...
... 1. Create the UML model elements using the UML modeling tool. This is a painstaking task for any moderately complex real-world application. The application object model is essentially specified twice: as a UML Class model and as a UML Data model. The Class model corresponds to the objects in the app ...
Link to April 21st slides
... Low cost is the defining characteristic of tertiary storage. Generally, tertiary storage is built using removable media Common examples of removable media are floppy disks and CD-ROMs; other ...
... Low cost is the defining characteristic of tertiary storage. Generally, tertiary storage is built using removable media Common examples of removable media are floppy disks and CD-ROMs; other ...
Data Science in the Department of Computer Science and
... analytics, scalable data--driven pattern discovery, and fundamental algorithmic and statistical concepts ...
... analytics, scalable data--driven pattern discovery, and fundamental algorithmic and statistical concepts ...
All – Will have created a basic database structure and
... edit field content; search criteria, including relational operators ‘greater than’, less than’, ‘equals’ and ‘contains’, report 2.9.2 Database: column and row; field and record; set up a database, primary key, enter and edit field content; data types, including text, date/time and number; number for ...
... edit field content; search criteria, including relational operators ‘greater than’, less than’, ‘equals’ and ‘contains’, report 2.9.2 Database: column and row; field and record; set up a database, primary key, enter and edit field content; data types, including text, date/time and number; number for ...
Slide 1
... edit field content; search criteria, including relational operators ‘greater than’, less than’, ‘equals’ and ‘contains’, report 2.9.2 Database: column and row; field and record; set up a database, primary key, enter and edit field content; data types, including text, date/time and number; number for ...
... edit field content; search criteria, including relational operators ‘greater than’, less than’, ‘equals’ and ‘contains’, report 2.9.2 Database: column and row; field and record; set up a database, primary key, enter and edit field content; data types, including text, date/time and number; number for ...
Oracle: From Client Server to the Grid and beyond Oracle Corporation Graham Wood
... Reliability: Version 4 October 1984 y Larger Installed Base (well, it had one) y Architectural Improvements ...
... Reliability: Version 4 October 1984 y Larger Installed Base (well, it had one) y Architectural Improvements ...
Requirement Extraction for Open Data Platform Project: CANFAR
... Study will be based on a set of User Stories, i.e. how the researcher describes the steps to solve each part of the problem addressed. In practice, the selection of the use stories shall be representative reflecting both of the research challenge and complexity, and of the possible solutions offered ...
... Study will be based on a set of User Stories, i.e. how the researcher describes the steps to solve each part of the problem addressed. In practice, the selection of the use stories shall be representative reflecting both of the research challenge and complexity, and of the possible solutions offered ...
notes on methodology
... Final consumption expenditure of households is calculated from regular surveys of the Croatian Bureau of Statistics on turnover data for retail trade and for hotels and restaurants. Expenditure on other services, which are not covered by regular surveys of the Croatian Bureau of Statistics, was extr ...
... Final consumption expenditure of households is calculated from regular surveys of the Croatian Bureau of Statistics on turnover data for retail trade and for hotels and restaurants. Expenditure on other services, which are not covered by regular surveys of the Croatian Bureau of Statistics, was extr ...
Presentation
... In 2013 a WMO Hydrological Observing System (WHOS) was proposed by the CHy Advisory Working Group as the means to provide the most comprehensive hydrological component in fulfillment of the WIGOS objective of “an integrated, comprehensive, and coordinated system which is comprised of the present WMO ...
... In 2013 a WMO Hydrological Observing System (WHOS) was proposed by the CHy Advisory Working Group as the means to provide the most comprehensive hydrological component in fulfillment of the WIGOS objective of “an integrated, comprehensive, and coordinated system which is comprised of the present WMO ...
Using R with databases
... Data within R and data stored in relational databases both have a defined type or structure. It is important to understand the various data types and how to map values properly. R has a very limited set of base data types including: characters, numeric (integers and doubleprecision floating point va ...
... Data within R and data stored in relational databases both have a defined type or structure. It is important to understand the various data types and how to map values properly. R has a very limited set of base data types including: characters, numeric (integers and doubleprecision floating point va ...
ppt
... • Handling multiple dimension rows that preserve history – 1st approach: Mapping table contains surrogate key for most current dimension row – 2nd approach: Mapping table lists all surrogate keys that were ever used for each natural key • Add additional columns to mapping table: – Begin_date, End_da ...
... • Handling multiple dimension rows that preserve history – 1st approach: Mapping table contains surrogate key for most current dimension row – 2nd approach: Mapping table lists all surrogate keys that were ever used for each natural key • Add additional columns to mapping table: – Begin_date, End_da ...
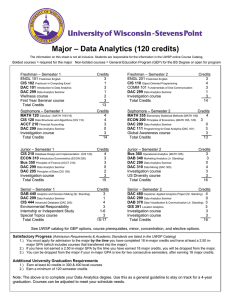
Major – Data Analytics (120 credits)
... See UWSP catalog for GEP options, course prerequisites, minor, concentration, and elective options. Satisfactory Progress (Admission Requirements & Academic Standards are listed in the UWSP Catalog) 1.) You must apply for admission to the major by the time you have completed 18 in-major credits and ...
... See UWSP catalog for GEP options, course prerequisites, minor, concentration, and elective options. Satisfactory Progress (Admission Requirements & Academic Standards are listed in the UWSP Catalog) 1.) You must apply for admission to the major by the time you have completed 18 in-major credits and ...
Data transfer, storage and analysis for data mart enlargement
... Fact and dimensional data are arranged in one of the following models: Star schema – In this model, the data are stored in one table, even at the cost of redundant records - "unnormalized". Another important feature of this model is a way to create a hierarchy of dimensions. They are formed only by ...
... Fact and dimensional data are arranged in one of the following models: Star schema – In this model, the data are stored in one table, even at the cost of redundant records - "unnormalized". Another important feature of this model is a way to create a hierarchy of dimensions. They are formed only by ...
Table - Wiley
... In a table containing customers, the Social Security Number field could be the primary key No two individuals have the same Social Security Number A field in a table that uniquely identifies a record in another table In a table containing Payments information, a single field would be used to keep tr ...
... In a table containing customers, the Social Security Number field could be the primary key No two individuals have the same Social Security Number A field in a table that uniquely identifies a record in another table In a table containing Payments information, a single field would be used to keep tr ...
Information Technology Module for Managers Structured Query
... SQL is a client/server language. Personal computer programs use SQL to communicate over a local area network with database servers that store shared data. Many new applications are using this client/server architecture, which minimizes network traffic and allows both PCs and servers to do what they ...
... SQL is a client/server language. Personal computer programs use SQL to communicate over a local area network with database servers that store shared data. Many new applications are using this client/server architecture, which minimizes network traffic and allows both PCs and servers to do what they ...
Syllabus MCA 2nd Sem
... 3NF& BCNF). Lossless join & Dependency preserving decomposition. Multivalued dependencies, join dependencies (4NF & 5NF), Denormalization. Unit IV – Transactions, Concurrency Control, Recovery Techniques Basic concept; ACID properties; transaction state; implementation of atomicity and durability; c ...
... 3NF& BCNF). Lossless join & Dependency preserving decomposition. Multivalued dependencies, join dependencies (4NF & 5NF), Denormalization. Unit IV – Transactions, Concurrency Control, Recovery Techniques Basic concept; ACID properties; transaction state; implementation of atomicity and durability; c ...
PPT File
... It is very important to distinguish between the database schema and database state. Let’s see if we can explain the differences. Initially we do not have a database. Once we define a new database, we specify its database schema only to the DBMS. Now we have a database but no data, the database at it ...
... It is very important to distinguish between the database schema and database state. Let’s see if we can explain the differences. Initially we do not have a database. Once we define a new database, we specify its database schema only to the DBMS. Now we have a database but no data, the database at it ...
Data Warehousing
... analyst) to make better and faster decisions. It provides architecture and tools for business executives to systematically organize, understand and use their data to make strategic decisions. Data Warehouse is a database used for reporting and analysis. It refers to the database that is maintained s ...
... analyst) to make better and faster decisions. It provides architecture and tools for business executives to systematically organize, understand and use their data to make strategic decisions. Data Warehouse is a database used for reporting and analysis. It refers to the database that is maintained s ...
Provable data privacy
... combination of privileges and views can limit a user’s access to precisely the data that the user needs. Silberschatz et al. [13] present the following banking example. Consider a clerk who needs to know the names of all customers who have a loan at each branch. This clerk is not authorized to see i ...
... combination of privileges and views can limit a user’s access to precisely the data that the user needs. Silberschatz et al. [13] present the following banking example. Consider a clerk who needs to know the names of all customers who have a loan at each branch. This clerk is not authorized to see i ...
06- CHAPTER (1)
... oriented systems provide the concept of complex objects to enable modeling of real-world entities. A complex object contains an arbitrary number of fields, each storing atomic data values or references to other objects (of arbitrary types). A complex object exactly models the user perception of some ...
... oriented systems provide the concept of complex objects to enable modeling of real-world entities. A complex object contains an arbitrary number of fields, each storing atomic data values or references to other objects (of arbitrary types). A complex object exactly models the user perception of some ...
BIM - BOUWonderWIJS.net
... General-purpose markup language capable of describing many different kinds of data XML provides a text-based format to describe and apply a tree-based structure to information XML can be used effectively to transfer various data via the Internet aecXML is a new framework for using the XML standard f ...
... General-purpose markup language capable of describing many different kinds of data XML provides a text-based format to describe and apply a tree-based structure to information XML can be used effectively to transfer various data via the Internet aecXML is a new framework for using the XML standard f ...
Ground Penetrating Radar- Data Acquisition, Processing
... The program will enable the participant to derive maximum information from GPR data and help them design the right GPR investigation program for a particular project requirement. It will also enable them to choose the right combination of antennas for varied geological conditions and resolution requ ...
... The program will enable the participant to derive maximum information from GPR data and help them design the right GPR investigation program for a particular project requirement. It will also enable them to choose the right combination of antennas for varied geological conditions and resolution requ ...
ICSA 411 Data Communication & Networking
... Each type of application (file transfer, remote access) requires different software on this layer ...
... Each type of application (file transfer, remote access) requires different software on this layer ...
How to address top problems in test data management
... compromising test data privacy in the testing process. Data masking goes by various names, including data obfuscation, de-identification, depersonalisation, scrubbing, scrambling or cleansing. By any name, it allows you to hide, remove or randomize sensitive information. However, there is a catch. W ...
... compromising test data privacy in the testing process. Data masking goes by various names, including data obfuscation, de-identification, depersonalisation, scrubbing, scrambling or cleansing. By any name, it allows you to hide, remove or randomize sensitive information. However, there is a catch. W ...