Intel ISG Caesars Entertainment Case Study
... Intel technologies’ features and benefits depend on system configuration and may require enabled hardware, software or service activation. Performance varies depending on system configuration. No computer system can be absolutely secure. Check with your system manufacturer or retailer or learn m ...
... Intel technologies’ features and benefits depend on system configuration and may require enabled hardware, software or service activation. Performance varies depending on system configuration. No computer system can be absolutely secure. Check with your system manufacturer or retailer or learn m ...
p1 p2 p3 pn
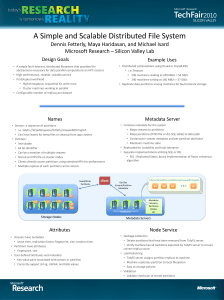
... • Distributed computations using Dryad or DryadLINQ • i.e. Terasort • 240 machines reading at 240 MB/s = 56 GB/s • 240 machines writing at 160 MB/s = 37 GB/s • Replicate data partitions among machines for fault tolerant storage ...
... • Distributed computations using Dryad or DryadLINQ • i.e. Terasort • 240 machines reading at 240 MB/s = 56 GB/s • 240 machines writing at 160 MB/s = 37 GB/s • Replicate data partitions among machines for fault tolerant storage ...
Work with Tables and Database Records
... • You can easily sort by one or more fields to achieve the order that you want. Access can sort text, numbers, or dates in ascending or descending order. • When you are using multiple fields, determine in which order you want them to be sorted. The primary sort field is called the outermost field . ...
... • You can easily sort by one or more fields to achieve the order that you want. Access can sort text, numbers, or dates in ascending or descending order. • When you are using multiple fields, determine in which order you want them to be sorted. The primary sort field is called the outermost field . ...
Automatic Social Media Data Extraction
... proposals in analyzing web documents and extracting the relevant information in structured formats [1]. These proposals are most commonly referred to as wrappers or as information extractors [4-12]. With studies done on the contemporary IE systems, the common categories of approaches used in data ex ...
... proposals in analyzing web documents and extracting the relevant information in structured formats [1]. These proposals are most commonly referred to as wrappers or as information extractors [4-12]. With studies done on the contemporary IE systems, the common categories of approaches used in data ex ...
Considerations in the Submission of Exposure Data in an SDTM-Compliant Format
... regarding the level of active drug. The sponsor suggested that merging ARMCD from DM would address this problem, but the EX dataset should not be dependent upon data from another dataset. EX is intended to provide a more granular representation of the treatments within the Elements of an Arm, and th ...
... regarding the level of active drug. The sponsor suggested that merging ARMCD from DM would address this problem, but the EX dataset should not be dependent upon data from another dataset. EX is intended to provide a more granular representation of the treatments within the Elements of an Arm, and th ...
Question Bank
... Transaction typically includes a unique transaction identity number (trans_ID), and a list of the items making up the transaction. .Define Spatial Databases. Spatial databases contain spatial-related information. Such databases include geographic (map) databases, VLSI chip design databases, and medi ...
... Transaction typically includes a unique transaction identity number (trans_ID), and a list of the items making up the transaction. .Define Spatial Databases. Spatial databases contain spatial-related information. Such databases include geographic (map) databases, VLSI chip design databases, and medi ...
Document
... – Maximal language for which reasoning (including query answering) is known to be worst case logspace (same as DB) – Captures (most of) expressive power of ER/UML schemas • Features include limited form of existential restrictions, subClass, equivalentClass, disjointness, range and domain, symmetric ...
... – Maximal language for which reasoning (including query answering) is known to be worst case logspace (same as DB) – Captures (most of) expressive power of ER/UML schemas • Features include limited form of existential restrictions, subClass, equivalentClass, disjointness, range and domain, symmetric ...
SQL Access for Cincom® SUPRA® PDM
... information that you can use to meet both immediate objectives and long-term business goals. ...
... information that you can use to meet both immediate objectives and long-term business goals. ...
Data Warehouse Development
... massive effort that must be planned and executed according to established methods There are many facets to the project lifecycle, and no single person can be an expert in each area ...
... massive effort that must be planned and executed according to established methods There are many facets to the project lifecycle, and no single person can be an expert in each area ...
Designing Distributed Data Warehouses and OLAP Systems
... This motivates us to take a closer look into the systems dynamics, not just the static data structures. Furthermore, as dialogue objects over a data warehouse lead to views over a view, it may be questioned, whether it makes sense to take a holistic approach to data warehouse design or whether it mi ...
... This motivates us to take a closer look into the systems dynamics, not just the static data structures. Furthermore, as dialogue objects over a data warehouse lead to views over a view, it may be questioned, whether it makes sense to take a holistic approach to data warehouse design or whether it mi ...
Computer Forensics
... Methods Of Detecting/Recovering Data (cont) • Steganalysis Methods – Detection cont... – Disk analysis utilities can search the hard drive for hidden tracks/sectors/data – RAM slack is the space from the end of the file to the end of the containing sector. Before a sector is written to disk, it is ...
... Methods Of Detecting/Recovering Data (cont) • Steganalysis Methods – Detection cont... – Disk analysis utilities can search the hard drive for hidden tracks/sectors/data – RAM slack is the space from the end of the file to the end of the containing sector. Before a sector is written to disk, it is ...
Apigee Gateway Specifications, Jul
... Systems Management Server (SMS) for centralized deployment Systems Management Server (SMS) for centralized deployment Simple Network Monitoring Protocol support with MIB ...
... Systems Management Server (SMS) for centralized deployment Systems Management Server (SMS) for centralized deployment Simple Network Monitoring Protocol support with MIB ...
Distributed Databases
... Failure of communication links: The system must be able to deal with failure of one or more of the communication links that connect the sites. An extreme case of this problem is that network partitioning may occur. This breaks up the sites into two or more partitions, where the sites within each par ...
... Failure of communication links: The system must be able to deal with failure of one or more of the communication links that connect the sites. An extreme case of this problem is that network partitioning may occur. This breaks up the sites into two or more partitions, where the sites within each par ...
Section 0: Introduction
... Positive relationship P(Country(Actor) = U.S.| gender(Actor)=W, ActsIn(“hate”,Actor), RunTime(“hate”)=short) ...
... Positive relationship P(Country(Actor) = U.S.| gender(Actor)=W, ActsIn(“hate”,Actor), RunTime(“hate”)=short) ...
Explaining 50+ terms you should know So you think you
... in Data Set 2) or alias values (CA vs California), you also need some way to recognise that Janet Smith (maiden name) and Jane Johnson (married name) are actually the same person. The picture gets even more complicated when you want to start matching offline records to online data, like the digital ...
... in Data Set 2) or alias values (CA vs California), you also need some way to recognise that Janet Smith (maiden name) and Jane Johnson (married name) are actually the same person. The picture gets even more complicated when you want to start matching offline records to online data, like the digital ...
4 rel model
... • Can we merge Courses and Teach since each professor teaches at most one course? • Do we need a separate relation to store evaluations? • How can we handle pre-requisites that are “or”s, e.g., you can take CS 4604 if you have taken either CS 2604 or CS 2606? • How do we generalize this schema to ha ...
... • Can we merge Courses and Teach since each professor teaches at most one course? • Do we need a separate relation to store evaluations? • How can we handle pre-requisites that are “or”s, e.g., you can take CS 4604 if you have taken either CS 2604 or CS 2606? • How do we generalize this schema to ha ...
SQLMagic
... more effective use of technical resources, SQLMagic is designed to deliver speed, accuracy and efficiency at every turn. With SQLMagic, users can quickly create, alter or drop SQL objects, such as tables, views and indexes. And with SQLMagic’s powerful set of wizards, complex tasks like splitting pa ...
... more effective use of technical resources, SQLMagic is designed to deliver speed, accuracy and efficiency at every turn. With SQLMagic, users can quickly create, alter or drop SQL objects, such as tables, views and indexes. And with SQLMagic’s powerful set of wizards, complex tasks like splitting pa ...
WT Orientation
... together to create interactive and animated web sites[1] by using a combination of a static markup language (such as HTML), a client-side scripting language (such as JavaScript), a presentation definition language (such as CSS), and the Document Object Model.[2] ...
... together to create interactive and animated web sites[1] by using a combination of a static markup language (such as HTML), a client-side scripting language (such as JavaScript), a presentation definition language (such as CSS), and the Document Object Model.[2] ...
3D Optical Data Storage Technology
... Great for archiving. Several forms of optical media are write-once read-many, which means that when data is written to them, they cannot be reused. This is excellent for archiving because data is preserved permanently with no possibility of being overwritten. Transportability. Optical media are wide ...
... Great for archiving. Several forms of optical media are write-once read-many, which means that when data is written to them, they cannot be reused. This is excellent for archiving because data is preserved permanently with no possibility of being overwritten. Transportability. Optical media are wide ...
Distributing near-real time data
... • Large multidimensional arrays from forecast models • Coordinate systems to access data by region and time • Need for near-real time data • Read-only or read-mostly access to existing data • Security often a minor issue: data is usually freely available and shared, but data systems must – Protect d ...
... • Large multidimensional arrays from forecast models • Coordinate systems to access data by region and time • Need for near-real time data • Read-only or read-mostly access to existing data • Security often a minor issue: data is usually freely available and shared, but data systems must – Protect d ...
Presentation (PowerPoint File)
... Manages the processing of data through a series of specified operations Loads input, processing and output modules dynamically as needed at execution time Allows for the addition of newly developed modules without the need to rebuild the engine Interprets a mining plan script that provides the detai ...
... Manages the processing of data through a series of specified operations Loads input, processing and output modules dynamically as needed at execution time Allows for the addition of newly developed modules without the need to rebuild the engine Interprets a mining plan script that provides the detai ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... or gain the data of the entire London city. Lastly, the architectural structure is sub divided into many entities or parts so that the data is totally secured but as per the demand of the client in order to retrieval of data it undergoes various steps which increases the access time. ...
... or gain the data of the entire London city. Lastly, the architectural structure is sub divided into many entities or parts so that the data is totally secured but as per the demand of the client in order to retrieval of data it undergoes various steps which increases the access time. ...
Query and Analysis of Data on Electric Consumption
... reason below. HBase is between NoSQL and RDBMS. It retrieves data only by row key and the range of row key, and does not support coarse index. But the relational databases usually inquire data by their properties. HBase only supports transactions with a command line, but there is a lot of linking in ...
... reason below. HBase is between NoSQL and RDBMS. It retrieves data only by row key and the range of row key, and does not support coarse index. But the relational databases usually inquire data by their properties. HBase only supports transactions with a command line, but there is a lot of linking in ...