154 kb - Mahopac Central School District
... Key Idea 1: Engineering design is an iterative process involving modeling & finding the best solution within given constraints, which are used to develop technological solutions to problems within given constraints. T1.1 Describe objects, imaginary or real, that might be modeled or made differently ...
... Key Idea 1: Engineering design is an iterative process involving modeling & finding the best solution within given constraints, which are used to develop technological solutions to problems within given constraints. T1.1 Describe objects, imaginary or real, that might be modeled or made differently ...
CIS 5357 - FSU Computer Science
... Semantic Security • The game – Adversary is given a public key and can generate any number of ciphertexts (polynomial time bound and probabilistically) – Adversary generates two equal – length messages m0 and m1 and transmits them to a challenge oracle along with the public key – The challenge orac ...
... Semantic Security • The game – Adversary is given a public key and can generate any number of ciphertexts (polynomial time bound and probabilistically) – Adversary generates two equal – length messages m0 and m1 and transmits them to a challenge oracle along with the public key – The challenge orac ...
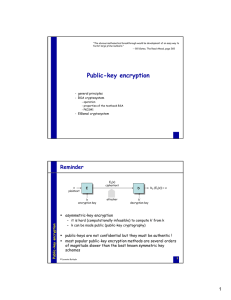
Public-key encryption
... – if yes, then n may be prime and we need to test it further with other bases – if n passes the test for many bases, then we accept it as a prime – this is a Monte Carlo algorithm • the algorithm always gives an answer • the answer may be wrong with some probability ε ...
... – if yes, then n may be prime and we need to test it further with other bases – if n passes the test for many bases, then we accept it as a prime – this is a Monte Carlo algorithm • the algorithm always gives an answer • the answer may be wrong with some probability ε ...
Chapter 1 Security Problems in Computing
... Choose a multiplier w and a modulus n, where n > S1 + … + SM and w is relprime to n. Note: Usually n is a prime, which is relprime to any number < n. Example: w = 19 and n = 303. ...
... Choose a multiplier w and a modulus n, where n > S1 + … + SM and w is relprime to n. Note: Usually n is a prime, which is relprime to any number < n. Example: w = 19 and n = 303. ...
CN 2015 5 - SNGCE DIGITAL LIBRARY
... Transpositional cipher is also not a very secure approach. The attacker can find the plaintext by trial and error utilizing ...
... Transpositional cipher is also not a very secure approach. The attacker can find the plaintext by trial and error utilizing ...
CADD LEGACY PCA Model 6300
... ENTER key to change the Demand Dose Lockout. NOTE: if no Demand Dose was programmed, this screen will NOT be displayed. 13. Enter the “Max Doses Per Hour”. The range available will be displayed at the bottom of this programming screen. Use the up/down arrow key to scroll to the desired number and pr ...
... ENTER key to change the Demand Dose Lockout. NOTE: if no Demand Dose was programmed, this screen will NOT be displayed. 13. Enter the “Max Doses Per Hour”. The range available will be displayed at the bottom of this programming screen. Use the up/down arrow key to scroll to the desired number and pr ...
PPT - Purdue Computer Science
... – key transport: one party creates, and securely transfers it to the other(s). – key agreement: key establishment technique in which a shared secret is derived by two (or more) parties ...
... – key transport: one party creates, and securely transfers it to the other(s). – key agreement: key establishment technique in which a shared secret is derived by two (or more) parties ...
Devireddy
... If the attacker knows plaintext of one encrypted message, he can change the plaintext to the new message by calculating CRC-32 and doing bit flips on the original encrypted message. If the attacker sends the new packet to the access point, it will be accepted. ...
... If the attacker knows plaintext of one encrypted message, he can change the plaintext to the new message by calculating CRC-32 and doing bit flips on the original encrypted message. If the attacker sends the new packet to the access point, it will be accepted. ...
MT311-14
... be granted or denied different types of access independently. For example, a file can be a resource, and the read action can be differentiated from the write action. So, you can easily grant read-only access to a particular file. You can do the same with objects, allowing you to create security poli ...
... be granted or denied different types of access independently. For example, a file can be a resource, and the read action can be differentiated from the write action. So, you can easily grant read-only access to a particular file. You can do the same with objects, allowing you to create security poli ...
Packaging Information: Data Compression and
... Decryption keys are used to decode ciphertext and recover the original plaintext Decryption keys are sometimes discovered by brute force methods employing computers to search large potential key spaces ...
... Decryption keys are used to decode ciphertext and recover the original plaintext Decryption keys are sometimes discovered by brute force methods employing computers to search large potential key spaces ...
Section2.3
... alphabet is obtained by writing the letters of the resulting array column by column (starting with column 1) below the plaintext alphabet. ...
... alphabet is obtained by writing the letters of the resulting array column by column (starting with column 1) below the plaintext alphabet. ...
Enhancement of Security through a Cryptographic Algorithm
... Pulkit Singhal, 2Narendra Kumar Verma, 3Aurobinda Laha, 4Prof. Pranam Paul and 5Prof. A K Bhattacharjee ...
... Pulkit Singhal, 2Narendra Kumar Verma, 3Aurobinda Laha, 4Prof. Pranam Paul and 5Prof. A K Bhattacharjee ...
Slides on Security
... • Encryption can be used to secure messages sent over a network. • Encryption can also be used to secure data stored on a computer. • Think of a data file as a very slow message. ...
... • Encryption can be used to secure messages sent over a network. • Encryption can also be used to secure data stored on a computer. • Think of a data file as a very slow message. ...
Chapter 8: Network Security
... exploits vulnerabilities in end-systems. Worms, pieces of self-replicating code that spread over networks, have been known for several decades and continue to cause problems, as do their relatives, viruses, which are spread by the transmission of “infected” files. Infected machines can then be arran ...
... exploits vulnerabilities in end-systems. Worms, pieces of self-replicating code that spread over networks, have been known for several decades and continue to cause problems, as do their relatives, viruses, which are spread by the transmission of “infected” files. Infected machines can then be arran ...
Public Key Encryption and Digital Signatures
... – Public Key encryption • does not require communication of a key • security depends on the difficulty of factoring very large numbers (hundreds of digits) ...
... – Public Key encryption • does not require communication of a key • security depends on the difficulty of factoring very large numbers (hundreds of digits) ...
compatible-development-of
... at Pearl Harbor surprised by Japanese attack, despite U.S. breaking of Japanese codes. U.S. enters World War II April 1943 - Admiral Yamamoto, architect of Pearl Harbor attack, is assassinated by U.S. forces who know his itinerary from decoded messages. This shows that the lives of cryptographers ar ...
... at Pearl Harbor surprised by Japanese attack, despite U.S. breaking of Japanese codes. U.S. enters World War II April 1943 - Admiral Yamamoto, architect of Pearl Harbor attack, is assassinated by U.S. forces who know his itinerary from decoded messages. This shows that the lives of cryptographers ar ...
Cryptanalysis of the Lorenz cipher

Cryptanalysis of the Lorenz cipher was the process that enabled the British to read high-level German army messages during World War II. The British Government Code and Cypher School (GC&CS) at Bletchley Park decrypted many communications between the Oberkommando der Wehrmacht (OKW, German High Command) in Berlin and their army commands throughout occupied Europe, some of which were signed ""Adolf Hitler, Führer"". These were intercepted non-Morse radio transmissions that had been enciphered by the Lorenz SZ teletypewriter rotor stream cipher attachments. Decrypts of this traffic became an important source of ""Ultra"" intelligence which contributed significantly to Allied victory.For its high-level secret messages, the German armed services enciphered each character using various online Geheimschreiber (secret writer) stream cipher machines at both ends of a telegraph link using the 5-bit International Telegraphy Alphabet No. 2 (ITA2). These machines were the Lorenz SZ (SZ for Schluesselzusatzgeraet, meaning ""cipher attachment machine"") for the army, the Siemens and Halske T52 for the air force and the Siemens T43, which was little used and never broken by the Allies.Bletchley Park decrypts of messages enciphered with the Enigma machines revealed that the Germans called one of their wireless teleprinter transmission systems ""Sägefisch"" (sawfish), which led British cryptographers to refer to encrypted German teleprinter traffic as ""Fish"". ""Tunny"" was the name given to the first non-Morse link, and it was subsequently used for the Lorenz SZ machines and the traffic enciphered by them. The cryptanalysts did not see one of these machines until after the end of the war in Europe.As with the entirely separate cryptanalysis of the Enigma, it was German operational shortcomings that allowed the initial diagnosis of the system, and a way into decryption. Unlike Enigma, no physical machine reached allied hands until the very end of the war in Europe, long after wholesale decryption had been established. Initially, operator errors produced a number of pairs of transmissions sent with the same keys, giving a ""depth"", which often allowed manual decryption to be achieved. One long depth also allowed the complete logical structure of the machine to be worked out, a quite remarkable cryptanalytical feat on which the subsequent wholesale decrypting of Tunny messages relied.When depths became less frequent, decryption was achieved by a combination of manual and automated methods. The first machine to automate part of the decrypting process was called ""Heath Robinson"" and it was followed by several other ""Robinsons"". These were, however, slow and unreliable, and were supplemented by the much faster and more flexible ""Colossus"", the world's first electronic, programmable digital computer, ten of which were in use by the end of the war, by which time some 90% of Tunny messages were being decrypted at Bletchley Park. Albert W. Small, an American cryptographer from the US Signal Corps who was seconded to Bletchley Park and worked on Tunny, said in his December 1944 report back to Arlington Hall that:Daily solutions of Fish messages at GC&CS reflect a background of British mathematical genius, superb engineering ability, and solid common sense. Each of these has been a necessary factor. Each could have been overemphasised or underemphasised to the detriment of the solutions; a remarkable fact is that the fusion of the elements has been apparently in perfect proportion. The result is an outstanding contribution to cryptanalytic science.