3rd Edition: Chapter 4
... Router Architecture Overview Two key router functions: run routing algorithms/protocol (RIP, OSPF, BGP) forwarding datagrams from incoming to outgoing link ...
... Router Architecture Overview Two key router functions: run routing algorithms/protocol (RIP, OSPF, BGP) forwarding datagrams from incoming to outgoing link ...
Troubleshooting
... ▫ Logical networking models separate network functionality into modular layers. ▫ Each layer of the OSI or TCP/IP model has specific functions and protocols. ...
... ▫ Logical networking models separate network functionality into modular layers. ▫ Each layer of the OSI or TCP/IP model has specific functions and protocols. ...
network
... 4.2 virtual circuit and datagram networks 4.3 what’s inside a router 4.4 IP: Internet Protocol datagram format IPv4 addressing ...
... 4.2 virtual circuit and datagram networks 4.3 what’s inside a router 4.4 IP: Internet Protocol datagram format IPv4 addressing ...
EUR_STELLAZ Wall Radiator Thermostat Valve Control Quick Start Firmware Version : 0.4
... Remote controls send signals to static controllers to trigger scenes or other actions 7. Remote controls control other actuators. There are two different role a controller can have. There is always one single primary controller that is managing the network and including/excluding devices. The contro ...
... Remote controls send signals to static controllers to trigger scenes or other actions 7. Remote controls control other actuators. There are two different role a controller can have. There is always one single primary controller that is managing the network and including/excluding devices. The contro ...
Y-Comm: A new architecture for heterogeneous networking
... – Proactive Policies allow us to maximize the use of available channels provided you know the amount of time a channel will be available. – That time is known as: • Time before vertical handover (TBVH) • Can significantly reduce packet loss during all vertical handovers ...
... – Proactive Policies allow us to maximize the use of available channels provided you know the amount of time a channel will be available. – That time is known as: • Time before vertical handover (TBVH) • Can significantly reduce packet loss during all vertical handovers ...
Network+ Guide to Networks 5th Edition
... corresponding layer in the second node • The communication process starts at layer 7 (application) and initiated by a user or device to start data exchange, the application layer separates data into PDU. Then, PDU progress down through OSI model layers (6,5,4,3,2,1) and header is added to the data u ...
... corresponding layer in the second node • The communication process starts at layer 7 (application) and initiated by a user or device to start data exchange, the application layer separates data into PDU. Then, PDU progress down through OSI model layers (6,5,4,3,2,1) and header is added to the data u ...
Lecture 6 - Aerobic Suspended Growth
... Physical layer: provides electrical, functional, and procedural means to activate, maintain, and deactivate physical links that transparently pass the bit stream for communication; only recognizes individual bits (not characters nor frames) and provides bit synchronization; peer-to-peer. Data link l ...
... Physical layer: provides electrical, functional, and procedural means to activate, maintain, and deactivate physical links that transparently pass the bit stream for communication; only recognizes individual bits (not characters nor frames) and provides bit synchronization; peer-to-peer. Data link l ...
ID Layer for Internet of Things Based on Name
... ganized in hierarchical manner, which allows a tree-based ID routing, i.e., the data frames are transferred, according to ID carried in their headers, by established trees in both upload and download directions. The IDs are created and managed taking into account the location of each IoT object. Nam ...
... ganized in hierarchical manner, which allows a tree-based ID routing, i.e., the data frames are transferred, according to ID carried in their headers, by established trees in both upload and download directions. The IDs are created and managed taking into account the location of each IoT object. Nam ...
Development of a Smart Home Control System Based on
... industry grade standard, small size, easy to install and are stable and reliable. It can be applicable to security alarm, wireless automatic meter reading, home and industrial automation, remote control, wireless data transmission and other systems [6]. 3.3. Relay Module The relay is an electrical c ...
... industry grade standard, small size, easy to install and are stable and reliable. It can be applicable to security alarm, wireless automatic meter reading, home and industrial automation, remote control, wireless data transmission and other systems [6]. 3.3. Relay Module The relay is an electrical c ...
Lecture #14 - Wayne State University
... EFCI (Explicit Forward Congestion Indication) bit in data cells: set to 1 in congested switch to indicate congestion to destination host. when RM arrives at destination, if most recently received data cell has EFCI=1, sender sets CI bit in returned RM cell ...
... EFCI (Explicit Forward Congestion Indication) bit in data cells: set to 1 in congested switch to indicate congestion to destination host. when RM arrives at destination, if most recently received data cell has EFCI=1, sender sets CI bit in returned RM cell ...
Network Layer - e-learning website
... Internal router :: a level 1 router. Backbone router :: a level 2 router. Area border router (ABR) :: a backbone router that attaches to more than one area. AS border router :: (an interdomain router), namely, a router that attaches to routers from other ASs across AS boundaries. ...
... Internal router :: a level 1 router. Backbone router :: a level 2 router. Area border router (ABR) :: a backbone router that attaches to more than one area. AS border router :: (an interdomain router), namely, a router that attaches to routers from other ASs across AS boundaries. ...
RT-WiFi: Real-Time High Speed Communication Protocol for
... will be blocked by a nondeterministic of time because of carrier sense, and further delayed by random backoff mechanism. To address this problem, we adopts TDMA mechanism and a centralized channel and time management to access the channels according to strict timing. Fig. 4b presents the channel acc ...
... will be blocked by a nondeterministic of time because of carrier sense, and further delayed by random backoff mechanism. To address this problem, we adopts TDMA mechanism and a centralized channel and time management to access the channels according to strict timing. Fig. 4b presents the channel acc ...
Supporting ZDOs with the XBee API
... The ZigBee Device Profile is a management and discovery service layer supported on all ZigBee devices. Like all other profiles, the ZigBee Device Profile defines a set of clusters that can be used to perform a variety of advanced network management and device discovery operations. Since the ZigBee D ...
... The ZigBee Device Profile is a management and discovery service layer supported on all ZigBee devices. Like all other profiles, the ZigBee Device Profile defines a set of clusters that can be used to perform a variety of advanced network management and device discovery operations. Since the ZigBee D ...
Cloud-Managed and Unified Wired and Wireless Networking Launch
... What are the key features of this integration? IMC EAD posture-checks devices for compliance to grant access to the network with selectable MDM-vendor-dependent criteria. The entire list of criteria is not represented. • MDM endpoint registration and MDM policy compliance • Password-enabled and auto ...
... What are the key features of this integration? IMC EAD posture-checks devices for compliance to grant access to the network with selectable MDM-vendor-dependent criteria. The entire list of criteria is not represented. • MDM endpoint registration and MDM policy compliance • Password-enabled and auto ...
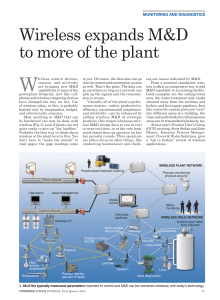
Wireless Expands M D to More of the Plant
... into the control and automation system as well. That’s the point. The data can go anywhere as long as a network can pick up the signals and the transmission is secure. Virtually all of the plant’s performance metrics—safety, productivity, efficiency, environmental compliance, and reliability—can be ...
... into the control and automation system as well. That’s the point. The data can go anywhere as long as a network can pick up the signals and the transmission is secure. Virtually all of the plant’s performance metrics—safety, productivity, efficiency, environmental compliance, and reliability—can be ...
No Slide Title
... • Protection/Restoration in physical layer has shorter fault switching time (~50ms) but worse network utilization. • Protection/Restoration in IP layer or application layer may take from several seconds to several minutes but has higher network utilization. • Protection/Restoration in one layer cann ...
... • Protection/Restoration in physical layer has shorter fault switching time (~50ms) but worse network utilization. • Protection/Restoration in IP layer or application layer may take from several seconds to several minutes but has higher network utilization. • Protection/Restoration in one layer cann ...
Lecture 2
... repeaters used to connect up to multiple segments repeater repeats bits it hears on one interface to its other interfaces: physical layer device only! has become a legacy technology ...
... repeaters used to connect up to multiple segments repeater repeats bits it hears on one interface to its other interfaces: physical layer device only! has become a legacy technology ...
Evaluating Design Approaches For Smart Building Systems
... building system, allowing it to control and monitor the physical environment. Frequently WSN operate in isolation but towards their collaboration in the IoT technology, interconnectivity between two or more networks is a challenging task. This is mainly due to the fact that different protocols, syst ...
... building system, allowing it to control and monitor the physical environment. Frequently WSN operate in isolation but towards their collaboration in the IoT technology, interconnectivity between two or more networks is a challenging task. This is mainly due to the fact that different protocols, syst ...
Document
... Organizations using VPNs must have clear security rules supported by top management When access goes beyond traditional office facilities ...
... Organizations using VPNs must have clear security rules supported by top management When access goes beyond traditional office facilities ...
Data Networking Fundamentals
... messages from one mail server to another over the Internet. Telnet - a terminal emulation protocol used to log on to remote hosts to issue configuration instructions. ...
... messages from one mail server to another over the Internet. Telnet - a terminal emulation protocol used to log on to remote hosts to issue configuration instructions. ...
00205r1P802-15_TG3-MAC-Proposal-for-High-Rate
... – Average response time for small packets is under 5 mS for current 1 Mbps system, projected to be less at higher data rate Submission ...
... – Average response time for small packets is under 5 mS for current 1 Mbps system, projected to be less at higher data rate Submission ...
Slides
... Low energy consumption (especially for asynchronous bidirectional communications) Suitable for switches/actuators controlled by ...
... Low energy consumption (especially for asynchronous bidirectional communications) Suitable for switches/actuators controlled by ...
Advances in Natural and Applied Sciences
... and get better the act of the system(V. Srivastava,2005). Mostly, the adaptive modulation ability of the PHY layer and the multi-rate data-encoding characteristic of solid disk request are joint to achieve a better end-user QoS (Physical Layer Aspects,2001). The cross-layer optimizer is split into t ...
... and get better the act of the system(V. Srivastava,2005). Mostly, the adaptive modulation ability of the PHY layer and the multi-rate data-encoding characteristic of solid disk request are joint to achieve a better end-user QoS (Physical Layer Aspects,2001). The cross-layer optimizer is split into t ...