r08-QoS - Computer Engineering
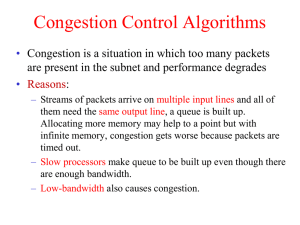
... • A congested DS node tries to protect packets with a lower drop precedence value from being lost by preferably discarding packets with a higher drop ...
... • A congested DS node tries to protect packets with a lower drop precedence value from being lost by preferably discarding packets with a higher drop ...
best-effort service!
... – Guaranteed Service for hard real-time (“Real-Time applications”) – Controlled Load for soft real-time (“tolerant” applications) ...
... – Guaranteed Service for hard real-time (“Real-Time applications”) – Controlled Load for soft real-time (“tolerant” applications) ...
MPLS-TP - Dspcsp.com
... Characteristics of transport networks 1. High availability 1. Fault Management OAM 2. Automatic Protection Switching 2. Efficient utilization, SLA support, and QoS mechanisms 1. high determinism 2. Connection Oriented behavior 3. Performance Management OAM 3. Management plane (optionally control pla ...
... Characteristics of transport networks 1. High availability 1. Fault Management OAM 2. Automatic Protection Switching 2. Efficient utilization, SLA support, and QoS mechanisms 1. high determinism 2. Connection Oriented behavior 3. Performance Management OAM 3. Management plane (optionally control pla ...
WAN topology
... – The elements for network operation within one campus (building) – Designed to provide high availability, scalability, and flexibility – Includes a campus backbone, a server farm, building access and building distribution modules and a network management module ...
... – The elements for network operation within one campus (building) – Designed to provide high availability, scalability, and flexibility – Includes a campus backbone, a server farm, building access and building distribution modules and a network management module ...
interface-based forwarding
... • MH send path setup message to BS. • BS adds a forwarding entry for the MH, and forwards path setup message to next hop. • Router 1 performs similar processing and forwards the message to Router 0. (domain root router in this example) • Router 0 adds an entry for the mobile host, and since it is th ...
... • MH send path setup message to BS. • BS adds a forwarding entry for the MH, and forwards path setup message to next hop. • Router 1 performs similar processing and forwards the message to Router 0. (domain root router in this example) • Router 0 adds an entry for the mobile host, and since it is th ...
Chapter 5
... This protocol is used for making the reservations. When making a reservation, a receiver can specify one or more sources that it wants to receive from. It can also specify whether these choices are fixed /variable. The routers use this information to optimize bandwidth planning. RSVP allows mult ...
... This protocol is used for making the reservations. When making a reservation, a receiver can specify one or more sources that it wants to receive from. It can also specify whether these choices are fixed /variable. The routers use this information to optimize bandwidth planning. RSVP allows mult ...
TNC-2001
... Support of QoS – cont. • regulatory infrastructure (DEN ?) • administrative mechanisms for access regulation of network resources based on categories such as users, hosts, applications, accounts, etc. ...
... Support of QoS – cont. • regulatory infrastructure (DEN ?) • administrative mechanisms for access regulation of network resources based on categories such as users, hosts, applications, accounts, etc. ...
Create a standard ACL that will deny traffic from 192
... Access-list 147 deny tcp 172.16.0.0 0.0.255.255 any eq23 Access-list 147 permit any any First answer All traffic to network 172.16.0.0 will be denied. Assuming the ACL in the graphic is correctly applied to an interface, Graphic has 1 command Access-list 120 deny tcp host 192.168.15.4 any eq 21 Firs ...
... Access-list 147 deny tcp 172.16.0.0 0.0.255.255 any eq23 Access-list 147 permit any any First answer All traffic to network 172.16.0.0 will be denied. Assuming the ACL in the graphic is correctly applied to an interface, Graphic has 1 command Access-list 120 deny tcp host 192.168.15.4 any eq 21 Firs ...
A method for IP multicast performance monitoring
... * Requirements for IP multicast performance monitoring (draft-bipi-mboned-ip-multicast-pmrequirement-02) MBONED WG ...
... * Requirements for IP multicast performance monitoring (draft-bipi-mboned-ip-multicast-pmrequirement-02) MBONED WG ...
IP : Internet Protocol
... and reassembly packet • TTL : Time to Live, maximum number of routers through with the datagrams may pass (hop count) – decrease at each router to prevent forever looping – normally set to 30 – if TTL == 0 discard and send ICMP TTL exceeded to source IP ...
... and reassembly packet • TTL : Time to Live, maximum number of routers through with the datagrams may pass (hop count) – decrease at each router to prevent forever looping – normally set to 30 – if TTL == 0 discard and send ICMP TTL exceeded to source IP ...
Introduction to networking
... A sign points toward a destination and indicates the distance to the destination. Further down the highway, another sign points toward the destination, but now the distance is shorter. As long as the distance is shorter, the traffic is on the best path. ...
... A sign points toward a destination and indicates the distance to the destination. Further down the highway, another sign points toward the destination, but now the distance is shorter. As long as the distance is shorter, the traffic is on the best path. ...
Key Terms
... Offers the benefits of supporting multiple protocols – Limits unnecessary network traffic between routers ...
... Offers the benefits of supporting multiple protocols – Limits unnecessary network traffic between routers ...
Programming the IBM Power3 SP
... – enable grid and network researchers to test and evaluate new protocols with actual traffic demands of applications rather than modulated demands • Multiclass service inference – enable network clients to assess a system's multi-class mechanisms and parameters using only passive, external observati ...
... – enable grid and network researchers to test and evaluate new protocols with actual traffic demands of applications rather than modulated demands • Multiclass service inference – enable network clients to assess a system's multi-class mechanisms and parameters using only passive, external observati ...
eRouter-200TM
... communication, saves on capital and operational expenses, and delivers the industry’s best price/performance solution for small and medium businesses (SMB) and branch offices. The eRouter-200 allows full or fractional T1 access, supporting up to 24 DS0s. AutoCAP™ functionality allows service provide ...
... communication, saves on capital and operational expenses, and delivers the industry’s best price/performance solution for small and medium businesses (SMB) and branch offices. The eRouter-200 allows full or fractional T1 access, supporting up to 24 DS0s. AutoCAP™ functionality allows service provide ...
8- Routing
... interior gateway protocol (each AS selects its own) exterior gateway protocol (Internet-wide standard) ...
... interior gateway protocol (each AS selects its own) exterior gateway protocol (Internet-wide standard) ...
ppt
... – Sum of all 16-bit words in the IP packet header – If any bits of the header are corrupted in transit – … the checksum won’t match at receiving host – Receiving host discards corrupted packets • Sending host will retransmit the packet, if needed ...
... – Sum of all 16-bit words in the IP packet header – If any bits of the header are corrupted in transit – … the checksum won’t match at receiving host – Receiving host discards corrupted packets • Sending host will retransmit the packet, if needed ...
Chapter 11 ATM
... — Used by two end users without network intervention to establish and release user to user VCC ...
... — Used by two end users without network intervention to establish and release user to user VCC ...
routing
... N denotes set of nodes in the graph l (i, j) denotes non-negative cost (weight) for edge (i, j) s denotes this node M denotes the set of nodes incorporated so far C(n) denotes cost of the path from s to node n ...
... N denotes set of nodes in the graph l (i, j) denotes non-negative cost (weight) for edge (i, j) s denotes this node M denotes the set of nodes incorporated so far C(n) denotes cost of the path from s to node n ...