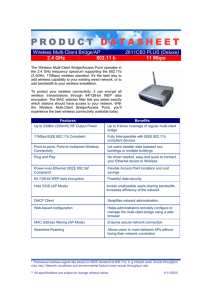
Wireless Multi-Client Bridge/AP 2611CB3 PLUS (Deluxe) 2.4 GHz
... the 2.4 GHz frequency spectrum supporting the 802.11b (2.4GHz, 11Mbps) wireless standard. It's the best way to add wireless capability to your existing wired network, or to add bandwidth to your wireless installation. To protect your wireless connectivity, it can encrypt all wireless transmissions t ...
... the 2.4 GHz frequency spectrum supporting the 802.11b (2.4GHz, 11Mbps) wireless standard. It's the best way to add wireless capability to your existing wired network, or to add bandwidth to your wireless installation. To protect your wireless connectivity, it can encrypt all wireless transmissions t ...
CSE 461 - University of Washington
... • Bonus Question: How do you determine who gets to be the new active monitor? • Node with the highest MAC address wins. ...
... • Bonus Question: How do you determine who gets to be the new active monitor? • Node with the highest MAC address wins. ...
ZTE ZXR10 5900E Series MPLS Easy
... ZXR10 5900E fully support MPLS L2/L3 VPN technology, providing an economical reliable VPN solution for Enterprise campus or branch office leased line service. ...
... ZXR10 5900E fully support MPLS L2/L3 VPN technology, providing an economical reliable VPN solution for Enterprise campus or branch office leased line service. ...
AMS 2003 - The Laboratory for Advanced Systems Research
... • Companies can retain administrative control • Server eventually becomes a bottleneck • Static topology • Suboptimal position of server with respect to ...
... • Companies can retain administrative control • Server eventually becomes a bottleneck • Static topology • Suboptimal position of server with respect to ...
Spanning Tree Protocol (STP)
... In Figure , bridge A has priority 8192 and is the root for the VLAN. Bridge B has priority 16384 and is the backup root bridge for the same VLAN. Bridges A and B, connected by a Gigabit Ethernet link, make up a core of the network. Bridge C is an access switch and has PortFast configured on the por ...
... In Figure , bridge A has priority 8192 and is the root for the VLAN. Bridge B has priority 16384 and is the backup root bridge for the same VLAN. Bridges A and B, connected by a Gigabit Ethernet link, make up a core of the network. Bridge C is an access switch and has PortFast configured on the por ...
EDS-405A/408A Series
... Features and Benefits • DHCP Option 82 for IP address assignment with different policies • Support EtherNet/IP, Modbus/TCP and PROFINET* protocols for device management and monitoring • EtherNet/IP EDS (Electronic Data Sheet) file, custom AOI (Add-On Instructions) and FactoryTalk® View faceplate ...
... Features and Benefits • DHCP Option 82 for IP address assignment with different policies • Support EtherNet/IP, Modbus/TCP and PROFINET* protocols for device management and monitoring • EtherNet/IP EDS (Electronic Data Sheet) file, custom AOI (Add-On Instructions) and FactoryTalk® View faceplate ...
Reverse Hashing for High-speed Network Monitoring: Algorithms
... • Switches down, e.g., unbootable IOS problems ...
... • Switches down, e.g., unbootable IOS problems ...
Virtual LANs - NET 331 and net 221
... Is a router, but a faster and more sophisticated. •The switching fabric in a three-layer switch allows faster table lookup and forwarding. •We can use the terms router and three-layer switch ...
... Is a router, but a faster and more sophisticated. •The switching fabric in a three-layer switch allows faster table lookup and forwarding. •We can use the terms router and three-layer switch ...
Control plane
... • What algorithm does the protocol run? –Spanning-tree construction, distance vector, linkstate routing, path-vector routing, source routing, end-to-end signaling ...
... • What algorithm does the protocol run? –Spanning-tree construction, distance vector, linkstate routing, path-vector routing, source routing, end-to-end signaling ...
Basic Configuration of WAP4410N
... Enable. Now go to Wireless -> Security and setup an appropriately secure configuration for the secure network. Once that is complete select the Guest Network and setup its security as well. Under Wireless -> VLAN and QoS ensure that VLAN is enabled, that the default VLAN is 1 and that the VLAN for y ...
... Enable. Now go to Wireless -> Security and setup an appropriately secure configuration for the secure network. Once that is complete select the Guest Network and setup its security as well. Under Wireless -> VLAN and QoS ensure that VLAN is enabled, that the default VLAN is 1 and that the VLAN for y ...
Router/Switch Security
... A trunk allows you to extend the VLANs across an entire network. A trunk does not belong to a specific VLAN, rather it is a conduit for VLANs between switches and routers. ...
... A trunk allows you to extend the VLANs across an entire network. A trunk does not belong to a specific VLAN, rather it is a conduit for VLANs between switches and routers. ...
PPP
... is responsible for generating routes between points Ensuring that looping does not take place Storing alternative routes, in the event of failure ...
... is responsible for generating routes between points Ensuring that looping does not take place Storing alternative routes, in the event of failure ...
PPT
... What do the BPDUs do? With the help of the BPDUs, bridges can: • Elect a single bridge as the root bridge. • Calculate the distance of the shortest path to the root bridge • Each LAN can determine a designated bridge, which is the bridge closest to the root. The designated bridge will forward packe ...
... What do the BPDUs do? With the help of the BPDUs, bridges can: • Elect a single bridge as the root bridge. • Calculate the distance of the shortest path to the root bridge • Each LAN can determine a designated bridge, which is the bridge closest to the root. The designated bridge will forward packe ...
Network Designs
... interfaces? Make sure you have enough. Extra interfaces are even better. Will the servers have both interfaces active in each VLAN, or just one? Some server high-availability solutions require the switches to be configured a certain way, while others require different configurations. Work this out i ...
... interfaces? Make sure you have enough. Extra interfaces are even better. Will the servers have both interfaces active in each VLAN, or just one? Some server high-availability solutions require the switches to be configured a certain way, while others require different configurations. Work this out i ...
ppt - NOISE
... • Flooding can lead to forwarding loops and broadcast storms – E.g., if the network contains a cycle of switches – Either accidentally, or by design for higher reliability ...
... • Flooding can lead to forwarding loops and broadcast storms – E.g., if the network contains a cycle of switches – Either accidentally, or by design for higher reliability ...
WDM Multicasting via Optical Burst / Label Switching
... neither Global Topology Nor MC Info • Basic idea - local multicast forwarding cache • A branching MI switch sends a “purge” message to all but one downstream switch • Each purged switch then floods a “grow” request to its neighbors – direct grow : only neighbors already on the forest can reply to th ...
... neither Global Topology Nor MC Info • Basic idea - local multicast forwarding cache • A branching MI switch sends a “purge” message to all but one downstream switch • Each purged switch then floods a “grow” request to its neighbors – direct grow : only neighbors already on the forest can reply to th ...
COMS 4995-1 Networking Laboratory
... Elect a single bridge as the root bridge. Calculate the distance of the shortest path to the root bridge Each LAN can determine a designated bridge, which is the bridge closest to the root. The designated bridge will forward packets towards the root bridge. Each bridge can determine a root p ...
... Elect a single bridge as the root bridge. Calculate the distance of the shortest path to the root bridge Each LAN can determine a designated bridge, which is the bridge closest to the root. The designated bridge will forward packets towards the root bridge. Each bridge can determine a root p ...
Chapter 15 Local Area Network Overview
... • Switch has multiple parallel data paths —Can handle multiple frames at a time ...
... • Switch has multiple parallel data paths —Can handle multiple frames at a time ...
What are the collision domains?
... – The switch starts frame transmission after it reads the first 64 bytes, which includes the frame header, and switching begins before the entire data field and checksum are read. – Runts were detected and discarded. A late collision is when a collision happens after the first 64 bytes of the frame ...
... – The switch starts frame transmission after it reads the first 64 bytes, which includes the frame header, and switching begins before the entire data field and checksum are read. – Runts were detected and discarded. A late collision is when a collision happens after the first 64 bytes of the frame ...
Exploration_LAN_Switching_Chapter5
... Loops and duplicate frames can have severe consequences on a network. The Spanning Tree Protocol (STP) was developed to address these issues. STP ensures that there is only one logical path between all destinations on the network by intentionally blocking redundant paths that could cause a loop. ...
... Loops and duplicate frames can have severe consequences on a network. The Spanning Tree Protocol (STP) was developed to address these issues. STP ensures that there is only one logical path between all destinations on the network by intentionally blocking redundant paths that could cause a loop. ...
Q and A for Ch. 17
... A: Yes. Gramma, let’s pretend you are sitting around with other old bitties sharing the latest gossip. Suppose you tell the person to your left some juicy gossip about who sat in a different pew in church on Sunday. (Oh my!) Then, that person tells the person on her left, who tells the person on her ...
... A: Yes. Gramma, let’s pretend you are sitting around with other old bitties sharing the latest gossip. Suppose you tell the person to your left some juicy gossip about who sat in a different pew in church on Sunday. (Oh my!) Then, that person tells the person on her left, who tells the person on her ...
eSmartES™ ES8100 Series
... and CLI interfaces, SNMPv3 management, 802.1p QoS Prioritization, Tagbased VLANs, IGMPv3 Snooping and IGMPL2 multicast management, port security, Link OAM (EFM, 802.3ah), and network redundancy options, including STP, RSTP, and MSTP for fault recovery. From six to eight 10/100Mb ports can be ordered ...
... and CLI interfaces, SNMPv3 management, 802.1p QoS Prioritization, Tagbased VLANs, IGMPv3 Snooping and IGMPL2 multicast management, port security, Link OAM (EFM, 802.3ah), and network redundancy options, including STP, RSTP, and MSTP for fault recovery. From six to eight 10/100Mb ports can be ordered ...
CiscoS4C - YSU Computer Science & Information Systems
... • Does CRC before looking up destination tables and forwarding the frame ...
... • Does CRC before looking up destination tables and forwarding the frame ...
[2016-NEW!] 200-120 New Questions and Answers -
... Broadcasts only use network layer addressing. A broadcast frame is never forwarded by a switch. A broadcast address will never be the source address of a frame. Broadcast addresses use an incorrect format for the switching table. Broadcast frames are never sent to switches. ...
... Broadcasts only use network layer addressing. A broadcast frame is never forwarded by a switch. A broadcast address will never be the source address of a frame. Broadcast addresses use an incorrect format for the switching table. Broadcast frames are never sent to switches. ...
Spanning Tree Protocol
The Spanning Tree Protocol (STP) is an older network protocol that ensures a loop-free topology for any bridged Ethernet local area network. The basic function of STP is to prevent bridge loops and the broadcast radiation that results from them. Spanning tree also allows a network design to include spare (redundant) links to provide automatic backup paths if an active link fails, without the danger of bridge loops, or the need for manual enabling/disabling of these backup links.Spanning Tree Protocol (STP) was originally standardized as IEEE 802.1D, in 802.1d-1998, but much of the functionality (spanning tree, rapid spanning tree, multiple spanning tree) previously specified in 802.1D, 801.1s, 802.1w has been incorporated into IEEE 802.1Q-2014 which includes shortest path bridging, the IEEE sanctioned replacement for these spanning tree functions.As the name suggests, it creates a spanning tree within a network of connected layer-2 bridges (typically Ethernet switches), and disables those links that are not part of the spanning tree, leaving a single active path between any two network nodes. STP is based on an algorithm that was invented by Radia Perlman while she was working for Digital Equipment Corporation.























![[2016-NEW!] 200-120 New Questions and Answers -](http://s1.studyres.com/store/data/000108812_1-bba6a7d69201d6f7aa4d0f7684ac7604-300x300.png)