CONNECTRIX VDX-6740B
... The Connectrix® VDX-6740B Top-of-Rack (ToR) switch redefines IP storage connectivity as the first Ethernet fabric switch purpose-built for IP storage. Designed for storage workloads it offers the network availability, deterministic performance and agility required for today’s business-critical appli ...
... The Connectrix® VDX-6740B Top-of-Rack (ToR) switch redefines IP storage connectivity as the first Ethernet fabric switch purpose-built for IP storage. Designed for storage workloads it offers the network availability, deterministic performance and agility required for today’s business-critical appli ...
Mobile Number Portability in India
... M3UA link between Patna MSS1 and STP Delhi is created. Links are UP and testing are in progress. M3UA link creation between Patna MSS and STP Meerut is in progress. LRN for Idea Bihar is 2100. For non STP circles Idea have jotted down the scenarios which require MNP check and which do not require MN ...
... M3UA link between Patna MSS1 and STP Delhi is created. Links are UP and testing are in progress. M3UA link creation between Patna MSS and STP Meerut is in progress. LRN for Idea Bihar is 2100. For non STP circles Idea have jotted down the scenarios which require MNP check and which do not require MN ...
Managed Switch Quick Start Guide
... supplies are not being used, then a jumper can be used between these terminals to prevent a fault (indicated by solid red LED). Also connect the 0 V common (#3 or #4 on Rail and #2°2 on MICE) and optionally, the fault contact (normally-closed for indication of alarm such as lost power supply, redund ...
... supplies are not being used, then a jumper can be used between these terminals to prevent a fault (indicated by solid red LED). Also connect the 0 V common (#3 or #4 on Rail and #2°2 on MICE) and optionally, the fault contact (normally-closed for indication of alarm such as lost power supply, redund ...
Multipath Protocol for Delay-Sensitive Traffic
... setting, we discuss the feasibility of using multiple paths and the changes required to the network architecture for these cases separately. Using multiple routes in the intradomain setting is easier since all the traffic originates and terminates within a single autonomous system. Inside the networ ...
... setting, we discuss the feasibility of using multiple paths and the changes required to the network architecture for these cases separately. Using multiple routes in the intradomain setting is easier since all the traffic originates and terminates within a single autonomous system. Inside the networ ...
Slide 1
... ● Telnet Server - Allows users to configure the switch using CLI over an Ethernet connection ● Web-based Interface - Web pages accessed with a standard browser for switch configuration and diagnostics. ● Remote Monitoring (RMON) - A standard network management protocol that allows monitoring and pro ...
... ● Telnet Server - Allows users to configure the switch using CLI over an Ethernet connection ● Web-based Interface - Web pages accessed with a standard browser for switch configuration and diagnostics. ● Remote Monitoring (RMON) - A standard network management protocol that allows monitoring and pro ...
Huawei S1700 Switch Data Sheet
... The S1700 series enterprise switches (S1700s) are next-generation, energy-saving Ethernet access switches. The S1700 uses high-performance hardware, which offers a wide array of features to help customers build secure, reliable, high-performance networks. The S1700 is easy to install and maintain, a ...
... The S1700 series enterprise switches (S1700s) are next-generation, energy-saving Ethernet access switches. The S1700 uses high-performance hardware, which offers a wide array of features to help customers build secure, reliable, high-performance networks. The S1700 is easy to install and maintain, a ...
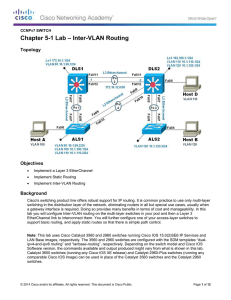
Lab 5-1 Inter-VLAN Routing
... At this point, basic intervlan routing can be demonstrated using an attached host. Host D is attached to DLS2 via interface Fa0/6. On DLS2, assign interface Fa0/6 to VLAN 110 and configure the host with the address 10.1.110.50/24 and default gateway of 10.1.110.1. Once you have done that, try and pi ...
... At this point, basic intervlan routing can be demonstrated using an attached host. Host D is attached to DLS2 via interface Fa0/6. On DLS2, assign interface Fa0/6 to VLAN 110 and configure the host with the address 10.1.110.50/24 and default gateway of 10.1.110.1. Once you have done that, try and pi ...
Scalable and Deterministic Overlay Network Diagnosis
... it hard to figure out what went wrong and even harder to assign responsibility. ̶ ̶ “Looking Over the Fence at Networks: A Neighbor's View of Networking Research”, by Committees on Research Horizons in Networking, National ...
... it hard to figure out what went wrong and even harder to assign responsibility. ̶ ̶ “Looking Over the Fence at Networks: A Neighbor's View of Networking Research”, by Committees on Research Horizons in Networking, National ...
pptx - UCL Computer Science
... • Higher cost – More complicated devices that cost more money • Delay in forwarding frames – Bridge/switch must receive and parse the frame – … and perform a look-up to decide where to forward – Introduces store-and-forward delay • Can ameliorate using cut-through switching – Start forwarding after ...
... • Higher cost – More complicated devices that cost more money • Delay in forwarding frames – Bridge/switch must receive and parse the frame – … and perform a look-up to decide where to forward – Introduces store-and-forward delay • Can ameliorate using cut-through switching – Start forwarding after ...
COMP 535 Multicasting Simon Foucher (260 223 197) McGill
... group. There are 2 types of multicast communication which yield different optimizations: source specific (data sent only by a single vertex), and group specific (all vertices can communicate with one another). The multicast optimization problem is called the ‘Steiner tree Problem in Networks’ (SPN). ...
... group. There are 2 types of multicast communication which yield different optimizations: source specific (data sent only by a single vertex), and group specific (all vertices can communicate with one another). The multicast optimization problem is called the ‘Steiner tree Problem in Networks’ (SPN). ...
Residential Ethernet Overview
... Existing Wiring & Wireless • Phone (old and Cat 5), Coax (CATV), Powerline, Wireless • HomePNA & Ethernet , MoCA, HomePlug, WiFi & UWB ...
... Existing Wiring & Wireless • Phone (old and Cat 5), Coax (CATV), Powerline, Wireless • HomePNA & Ethernet , MoCA, HomePlug, WiFi & UWB ...
24-Port 10/100/1000Mbps with 4 Shared SFP 802.3at
... stacking, 384 Gigabit PoE ports can be managed by a stacking group and additional ports and functionality can be added as needed. The 2 built-in stacking ports providing 5Gbps bandwidth and up to 20Gbps Bi-directional speed. It can handle extremely large amounts of data in a secure topology linking ...
... stacking, 384 Gigabit PoE ports can be managed by a stacking group and additional ports and functionality can be added as needed. The 2 built-in stacking ports providing 5Gbps bandwidth and up to 20Gbps Bi-directional speed. It can handle extremely large amounts of data in a secure topology linking ...
C80216m-08/880 Project Title
... Each SS/MS has an X.509 certificate that is bound to the MAC address. The addition of a secondary certificate or use of an internal algorithm to (randomly) generate a key pair to protect MS ID privacy during network entry. This secondary key pair would then be used to hash the MS MAC address. Then t ...
... Each SS/MS has an X.509 certificate that is bound to the MAC address. The addition of a secondary certificate or use of an internal algorithm to (randomly) generate a key pair to protect MS ID privacy during network entry. This secondary key pair would then be used to hash the MS MAC address. Then t ...
TN-Lecture9
... then can determine how to connect the call to its final destination. • The same process is followed using a Setup Message to any adjacent Switches and Circuits connecting those Switches. • The entire call may require several connections between several switches. ...
... then can determine how to connect the call to its final destination. • The same process is followed using a Setup Message to any adjacent Switches and Circuits connecting those Switches. • The entire call may require several connections between several switches. ...
PDF
... Cisco Services Available with Cisco IOS Software and the IP Base image, the Cisco Catalyst Blade Switch 3120 products offer a complete set of intelligent services to deliver security, quality of service (QoS), and high availability in the server farm access environment. The IP Base feature set inclu ...
... Cisco Services Available with Cisco IOS Software and the IP Base image, the Cisco Catalyst Blade Switch 3120 products offer a complete set of intelligent services to deliver security, quality of service (QoS), and high availability in the server farm access environment. The IP Base feature set inclu ...
Routing Protocols Overview - Home
... • Interior Gateway Routing Protocol (IGRP) is a proprietary protocol developed by Cisco. A distance vector routing protocol Bandwidth, load, delay and reliability are used to create a composite metric. Updates are broadcast every 90 seconds, by ...
... • Interior Gateway Routing Protocol (IGRP) is a proprietary protocol developed by Cisco. A distance vector routing protocol Bandwidth, load, delay and reliability are used to create a composite metric. Updates are broadcast every 90 seconds, by ...
CG5a-NJ
... •Choose a pair of objects, which results in the first path in the tree. •Choose a third object and establish the linear equations to let the object branch off the path. •Choose a pair of leaves in the tree constructed so far and compute the point a newly chosen object is inserted at. 1. If the new p ...
... •Choose a pair of objects, which results in the first path in the tree. •Choose a third object and establish the linear equations to let the object branch off the path. •Choose a pair of leaves in the tree constructed so far and compute the point a newly chosen object is inserted at. 1. If the new p ...
Configuring Q-in-Q VLAN Tunnels
... The 802.1Q tunneling expands VLAN space by using a VLAN-in-VLAN hierarchy and tagging the tagged packets. A port configured to support 802.1Q tunneling is called a tunnel port. When you configure tunneling, you assign a tunnel port to a VLAN that is dedicated to tunneling. Each customer requires a s ...
... The 802.1Q tunneling expands VLAN space by using a VLAN-in-VLAN hierarchy and tagging the tagged packets. A port configured to support 802.1Q tunneling is called a tunnel port. When you configure tunneling, you assign a tunnel port to a VLAN that is dedicated to tunneling. Each customer requires a s ...
Chapter 6 - UniMAP Portal
... Assume n busy stations, and each may transmit with probability p in each contention time slot Once the contention period is over (a station successfully occupies the channel), it takes X seconds for a frame to be transmitted It takes tprop before the next contention period starts. (a) ...
... Assume n busy stations, and each may transmit with probability p in each contention time slot Once the contention period is over (a station successfully occupies the channel), it takes X seconds for a frame to be transmitted It takes tprop before the next contention period starts. (a) ...
Switching Concepts and LAN Design
... allows only one station to transmit at a time. Multimedia applications with higher bandwidth demand such as video and the Internet, coupled with the broadcast nature of Ethernet, can create network congestion. Normal latency as the frames travel across the layers Extending the distances and increasi ...
... allows only one station to transmit at a time. Multimedia applications with higher bandwidth demand such as video and the Internet, coupled with the broadcast nature of Ethernet, can create network congestion. Normal latency as the frames travel across the layers Extending the distances and increasi ...
IEEE C80216m-08/880r3 Project Title
... When transmitting RNG-RSP, BS can further ensure confidentiality in either one of two ways. One, would be for BS to transmit the hashed MAC address in RNG-RSP message. It is then up to the SS/MS to verify the hashed MAC address upon receiving the RNG-RSP. The other method would be for the BS to not ...
... When transmitting RNG-RSP, BS can further ensure confidentiality in either one of two ways. One, would be for BS to transmit the hashed MAC address in RNG-RSP message. It is then up to the SS/MS to verify the hashed MAC address upon receiving the RNG-RSP. The other method would be for the BS to not ...
Cisco ME 6500 Series Ethernet Switch
... DHCP Snooping, DHCP Option 82, and Dynamic ARP Inspection help in identifying user’s MAC and IP address and port number, hence preventing attacks from malicious users. Malicious attacks can jeopardize the functionality of the network by compromising the switch CPU, MAC table, etc. Features such as P ...
... DHCP Snooping, DHCP Option 82, and Dynamic ARP Inspection help in identifying user’s MAC and IP address and port number, hence preventing attacks from malicious users. Malicious attacks can jeopardize the functionality of the network by compromising the switch CPU, MAC table, etc. Features such as P ...
Part I: Introduction - Computer Science and Engineering
... Ethernet Switch • Link-layer device: takes an active role – Store, forward Ethernet frames – Examine incoming frame’s MAC address, selectively forward frame to one-or-more outgoing links when frame is to be forwarded on segment, uses CSMA/CD to access segment ...
... Ethernet Switch • Link-layer device: takes an active role – Store, forward Ethernet frames – Examine incoming frame’s MAC address, selectively forward frame to one-or-more outgoing links when frame is to be forwarded on segment, uses CSMA/CD to access segment ...
D-Link DXS-3600 Series Sales Guide
... – DCBX allows auto exchange of Ethernet Parameters and Discovery Function between switches and end points – Goals of DCBX: Discovery of DCB capability in a peer ...
... – DCBX allows auto exchange of Ethernet Parameters and Discovery Function between switches and end points – Goals of DCBX: Discovery of DCB capability in a peer ...
Spanning Tree Protocol
The Spanning Tree Protocol (STP) is an older network protocol that ensures a loop-free topology for any bridged Ethernet local area network. The basic function of STP is to prevent bridge loops and the broadcast radiation that results from them. Spanning tree also allows a network design to include spare (redundant) links to provide automatic backup paths if an active link fails, without the danger of bridge loops, or the need for manual enabling/disabling of these backup links.Spanning Tree Protocol (STP) was originally standardized as IEEE 802.1D, in 802.1d-1998, but much of the functionality (spanning tree, rapid spanning tree, multiple spanning tree) previously specified in 802.1D, 801.1s, 802.1w has been incorporated into IEEE 802.1Q-2014 which includes shortest path bridging, the IEEE sanctioned replacement for these spanning tree functions.As the name suggests, it creates a spanning tree within a network of connected layer-2 bridges (typically Ethernet switches), and disables those links that are not part of the spanning tree, leaving a single active path between any two network nodes. STP is based on an algorithm that was invented by Radia Perlman while she was working for Digital Equipment Corporation.