Course Objectives: Upon Completion Of This Course
... Course Length: 5 Days Course Content: In this course, you will learn about the key components and procedures needed to install, configure, and manage the Cisco Nexus 7000, 5000, and 2000 Series switches and MDS Series switches in the network and SAN environment. Our enhanced Cisco labs include extra ...
... Course Length: 5 Days Course Content: In this course, you will learn about the key components and procedures needed to install, configure, and manage the Cisco Nexus 7000, 5000, and 2000 Series switches and MDS Series switches in the network and SAN environment. Our enhanced Cisco labs include extra ...
VDSL Transmission up to 15 Mbps
... ETHERNET SWITCH WITH VLAN SECURITY SWM-8/24VD are Ethernet switches allowing 8 or 24 users to link up to the Ethernet network by a telephonic pair. Each port could be individually configured either activated forbidden. The class of ac-cess is defined in rate (4/1 (asymmetric) and 5/10/15 Mbps (Full ...
... ETHERNET SWITCH WITH VLAN SECURITY SWM-8/24VD are Ethernet switches allowing 8 or 24 users to link up to the Ethernet network by a telephonic pair. Each port could be individually configured either activated forbidden. The class of ac-cess is defined in rate (4/1 (asymmetric) and 5/10/15 Mbps (Full ...
tom
... – If Internet a pure hierarchical structure (tree): k = O(n) – If Internet no hierarchy at all (worst case, clique): k = O(n2) – Internet has moderate hierarchical structure [TGJ+02] For reasonably large n, (e.g., 100), k = O(nlogn) (extensive linear regression tests on both synthetic and real topol ...
... – If Internet a pure hierarchical structure (tree): k = O(n) – If Internet no hierarchy at all (worst case, clique): k = O(n2) – Internet has moderate hierarchical structure [TGJ+02] For reasonably large n, (e.g., 100), k = O(nlogn) (extensive linear regression tests on both synthetic and real topol ...
VLANs Virtual LANs
... Dynamic VLANs • Dynamic VLANs assume that the network administrator builds a database of all MAC addresses, then assigns those addresses to logical VLANs. • Once built, the workstations can be plugged into any port on any switch at any time and it will find its way to the proper VLAN ...
... Dynamic VLANs • Dynamic VLANs assume that the network administrator builds a database of all MAC addresses, then assigns those addresses to logical VLANs. • Once built, the workstations can be plugged into any port on any switch at any time and it will find its way to the proper VLAN ...
Implementing L2 at the Data Center Access Layer
... L2 broadcast domains can span across multiple access elements (a single physical switch or Virtual Chassis acting as a single logical switch) to implement multi-node server cluster technologies that require L2 connectivity among the nodes participating in these clusters. Some examples of these techn ...
... L2 broadcast domains can span across multiple access elements (a single physical switch or Virtual Chassis acting as a single logical switch) to implement multi-node server cluster technologies that require L2 connectivity among the nodes participating in these clusters. Some examples of these techn ...
bigiron 4000, 8000, 15000
... BigIron systems equipped with JetCore modules provide an ideal choice for Internet data centers because of the 10/100, Gigabit and 10 Gigabit Ethernet port density, superior serviceability, high availability, security and advanced Layer 2/3 feature sets. With wire-speed, granular rate limiting, serv ...
... BigIron systems equipped with JetCore modules provide an ideal choice for Internet data centers because of the 10/100, Gigabit and 10 Gigabit Ethernet port density, superior serviceability, high availability, security and advanced Layer 2/3 feature sets. With wire-speed, granular rate limiting, serv ...
UCI Lecture 1
... – Supports most Cisco devices (Cisco IP phones and wireless access points). – Uses a Cisco proprietary method of determining if an attached device requires power. Power is delivered only to devices that require power. ...
... – Supports most Cisco devices (Cisco IP phones and wireless access points). – Uses a Cisco proprietary method of determining if an attached device requires power. Power is delivered only to devices that require power. ...
Network Routing Algorithms
... (a nonadaptive routing algorithm) Mark the source node as permanent. Designate the source node as the working node. Set the tentative distance to all other nodes to infinity. While some nodes are not marked permanent Compute the tentative distance from the source to all nodes adjacent to the working ...
... (a nonadaptive routing algorithm) Mark the source node as permanent. Designate the source node as the working node. Set the tentative distance to all other nodes to infinity. While some nodes are not marked permanent Compute the tentative distance from the source to all nodes adjacent to the working ...
Network Routing Algorithms
... (a nonadaptive routing algorithm) Mark the source node as permanent. Designate the source node as the working node. Set the tentative distance to all other nodes to infinity. While some nodes are not marked permanent Compute the tentative distance from the source to all nodes adjacent to the working ...
... (a nonadaptive routing algorithm) Mark the source node as permanent. Designate the source node as the working node. Set the tentative distance to all other nodes to infinity. While some nodes are not marked permanent Compute the tentative distance from the source to all nodes adjacent to the working ...
ConneXium - Schneider Electric
... Unmanaged Switch ● An unmanaged switch is a low cost device that connects multiple Ethernet devices to a single network segment ● Unmanaged switch – Capabilities ● Plug and Play device operation, no configuration required ● Store and Forward – stores and checks all received data before forwarding ● ...
... Unmanaged Switch ● An unmanaged switch is a low cost device that connects multiple Ethernet devices to a single network segment ● Unmanaged switch – Capabilities ● Plug and Play device operation, no configuration required ● Store and Forward – stores and checks all received data before forwarding ● ...
Serial and Asynchronous High-Speed WAN Interface Cards for
... protocol transport, console server, and dial access server. Customers can mix and match HWICs to tailor cost-effective solutions for common networking problems such as remote network management, external dial modem access, low-density WAN aggregation, legacy protocol transport and high port density ...
... protocol transport, console server, and dial access server. Customers can mix and match HWICs to tailor cost-effective solutions for common networking problems such as remote network management, external dial modem access, low-density WAN aggregation, legacy protocol transport and high port density ...
SMLT and RSMLT Deployment Guide V1.1
... difficult challenge is to ensure traffic is balanced across the network links. Several years after STP was widely deployed, some vendors implemented proprietary extensions to the STP protocol to achieve faster convergence; an example of this is the FastStart feature on the Nortel switching products. ...
... difficult challenge is to ensure traffic is balanced across the network links. Several years after STP was widely deployed, some vendors implemented proprietary extensions to the STP protocol to achieve faster convergence; an example of this is the FastStart feature on the Nortel switching products. ...
CCNA 3 Revision Notes
... guarantees that each path is loop free. DUAL inserts lowest cost paths into the routing table. These primary routes are known as successor routes. A copy of the successor routes is also placed in the topology table. 7. What is the difference between a “feasible successor” route and a :successor” rou ...
... guarantees that each path is loop free. DUAL inserts lowest cost paths into the routing table. These primary routes are known as successor routes. A copy of the successor routes is also placed in the topology table. 7. What is the difference between a “feasible successor” route and a :successor” rou ...
Student Workbook
... 4. What is a Network Operating System, and how does it differ from an Operating System used in a mainframe or stand-alone PC? ...
... 4. What is a Network Operating System, and how does it differ from an Operating System used in a mainframe or stand-alone PC? ...
PDF
... 802.11b wireless LANs. Today, the Cisco Aironet 350 Series represents that same market leadership. Now in general availability, the Cisco Aironet 350 Series provides superior functionality and better pricing than the legacy Cisco Aironet 4800 line of products and is an ideal replacement product line ...
... 802.11b wireless LANs. Today, the Cisco Aironet 350 Series represents that same market leadership. Now in general availability, the Cisco Aironet 350 Series provides superior functionality and better pricing than the legacy Cisco Aironet 4800 line of products and is an ideal replacement product line ...
Carrier
... Management, security and scalability reasons. Layer3 between VLANs 4094 available VLANs not enough for an SP! Transparency problem within the SP backbone network! A failure in the customer’s domain still affects the spanning-tree of the provider’s core (transport) network ...
... Management, security and scalability reasons. Layer3 between VLANs 4094 available VLANs not enough for an SP! Transparency problem within the SP backbone network! A failure in the customer’s domain still affects the spanning-tree of the provider’s core (transport) network ...
PowerPoint Sunusu
... • “open”: publicly available • uses link state algorithm – LS packet dissemination – topology map at each node – route computation using Dijkstra’s algorithm ...
... • “open”: publicly available • uses link state algorithm – LS packet dissemination – topology map at each node – route computation using Dijkstra’s algorithm ...
Routing Protocols - University of Alaska
... – LS packet dissemination – Topology map at each node – Route computation using Dijkstra’s algorithm ...
... – LS packet dissemination – Topology map at each node – Route computation using Dijkstra’s algorithm ...
Link-state routing protocols
... 5. Each router uses the database to construct a complete map of the topology and computes the best path to each destination network. The SPF algorithm is used to construct the map of the topology and to determine the best path to each network. (Road map) All routers will have a common map or tre ...
... 5. Each router uses the database to construct a complete map of the topology and computes the best path to each destination network. The SPF algorithm is used to construct the map of the topology and to determine the best path to each network. (Road map) All routers will have a common map or tre ...
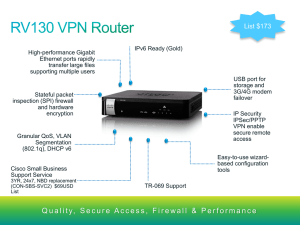
Cisco RV130/RV130W Product Overview
... • Lower Price Points • Bottom Line – improved versions at lower cost ...
... • Lower Price Points • Bottom Line – improved versions at lower cost ...
IP_2
... Static or dynamic? Static: • routes change slowly over time Dynamic: • routes change more quickly – periodic update – in response to link cost changes ...
... Static or dynamic? Static: • routes change slowly over time Dynamic: • routes change more quickly – periodic update – in response to link cost changes ...
Cisco Unified Fabric with Automation: Acronyms and Abbreviations
... both virtual and physical machines anywhere in a data center, the Cisco Unified Fabric needs the capability to track and detect end-hosts. Tracking end-host movement mainly involves discovering the end-host and propagating the end-host reachability information to the other switches (leaf switches) i ...
... both virtual and physical machines anywhere in a data center, the Cisco Unified Fabric needs the capability to track and detect end-hosts. Tracking end-host movement mainly involves discovering the end-host and propagating the end-host reachability information to the other switches (leaf switches) i ...
Chapter 12 Exterior Routing Protocols and Multicasting
... Forwarding Multicast Packets • If multicast address not recognised, discard • If router attaches to a network containing a member of group, transmit copy to that network • Consult spanning tree for this source-destination pair and forward to other routers if required ...
... Forwarding Multicast Packets • If multicast address not recognised, discard • If router attaches to a network containing a member of group, transmit copy to that network • Consult spanning tree for this source-destination pair and forward to other routers if required ...
Spanning Tree Protocol
The Spanning Tree Protocol (STP) is an older network protocol that ensures a loop-free topology for any bridged Ethernet local area network. The basic function of STP is to prevent bridge loops and the broadcast radiation that results from them. Spanning tree also allows a network design to include spare (redundant) links to provide automatic backup paths if an active link fails, without the danger of bridge loops, or the need for manual enabling/disabling of these backup links.Spanning Tree Protocol (STP) was originally standardized as IEEE 802.1D, in 802.1d-1998, but much of the functionality (spanning tree, rapid spanning tree, multiple spanning tree) previously specified in 802.1D, 801.1s, 802.1w has been incorporated into IEEE 802.1Q-2014 which includes shortest path bridging, the IEEE sanctioned replacement for these spanning tree functions.As the name suggests, it creates a spanning tree within a network of connected layer-2 bridges (typically Ethernet switches), and disables those links that are not part of the spanning tree, leaving a single active path between any two network nodes. STP is based on an algorithm that was invented by Radia Perlman while she was working for Digital Equipment Corporation.