* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download IntroductiontoInform.. - Home (www.dginter.net)
Survey
Document related concepts
Deep packet inspection wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Zero-configuration networking wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Computer network wikipedia , lookup
Airborne Networking wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Network tap wikipedia , lookup
Cellular network wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Internet protocol suite wikipedia , lookup
Transcript
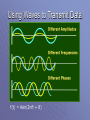
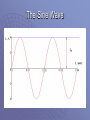
Introduction to Information Networking How to get the bits from here to there. Or If I was going there I wouldn’t start from here. What is a Network? Devices and media used to transfer information from place to place in real-time. Examples: • Phone System • Cable TV System • Internet Today these all converge. Basic Network Components Hosts: Communicators. Devices that send and receive data. Devices: used to interconnect hosts. • Hubs, switches routers…… Media: used to interconnect devices. • Ethernet, Fiber, Token Ring, Coaxial, Space (WiFi) Shared Peripherals: Assets connected to a host (printer, cd-tower, web camera) Network Roles Client: user of data Server: provider of data or service Client/Server: provider and consumer of data. • In the real world, all servers are also clients. As an example, web servers use Domain Name Servers to look up Internet Addresses. Source Channel and Destination Source: needs to send a message. Destination: where the message should go. Channel: how to get there from here. Example 1 Fred needs to Wilma to pick up bread on the way home. Fred sends e-mail to Wilma. Source=Fred; Destination=Wilma Channel: • Ethernet TCP/IP from Computer to Home Router • Home Router to ISP via cable/dsl/.. • Home ISP to Wilma’s employer’s ISP via Cloud (magic). • Employer’s Router to Wilma’s Computer via Ethernet Example 2 Betty needs to Barney to pick up bread on the way home. Betty sends ext message to Barney. Source=Betty; Destination=Barney Channel: • SMS Cellular Connection from Betty’s Cell to nearest available Cell Tower • Betty’s Cell Tower to Cell Tower near Barney via Public Switched Telephone Network (PSTN) aka Plain Old Telephone System (POTS). • Barney Cell Tower to Barney’s cell using SMS. Protocols Rules for Communication. Human Example: Phone Call • Caller Dials Number • PSTN finds receiver and creates connection. • Receiver Phone Rings. Receiver Picks Up • Caller Identifies themselves. • Both talk using the same language. Hopefully they both listen for silence before speaking. Protocols are Everywhere Encoding: preparing the message for transfer. Format: Agreeing on what is where. Size: Setting a limit on how much can be sent at once. Timing: when (access), how much (flow control), timeouts (max wait). Protocol Matching All Protocols must match for communication to occur. • Ethernet is a protocol to physically transfer data. Physical protocols must match for all connecting devices. • TCP/IP is a set of protocols to send data over a physical network. Communication Protocols must match at ends. Network Stacks Communication across networks is difficult and needs to be chunked into smaller manageable pieces. OSI has a seven layer protocol that defines the “ideal” network. TCP/IP is the real-world winner of the network protocols has a four layer protocol. OSI Model Layer Name What it does. Application Defines the rules. Presentation Data type, Encryption Session Open, close communication Transport End-to-end reliability, slices/dices/reassembles Network Routing. How to get there …. Data Link Node-to-node, error ID. Physical Spits Bits. Rules for spitting bits Mnemoic: All People Seem To Need Data Processing. There are worse! TCP/IP Stack Layer Name What it Does Application Transport Internet Network Interface Defines service rules, encryption, encapsulation End-to-end reliability, chunking, sequencing Routing Frames data for transmission and transmits. Is equal to the Network Interface Card. Data Transmission Copper Wire • Phone System • Ethernet Fiber Optic • Long Haul • Cable Distribution Airwaves • Radio/TV • WiFi • Bluetooth Data Transmission Terms Attenuation: Loss of signal over distance Noise: random unwanted signals. • Electric motors, fluorescent lights, crosstalk Signal Spread: high frequency attenuates more than low. Copper Wire Coaxial Cable. • Advantages • Highly immune to RFI • High SNR • Disadvantages • Cost, size, Installation, Access Twisted Pair • More twists less noise • Can be shielded but is expensive (manufacturing and installing) Optical Fiber Transmits Photons. Core is low attenuation. Cladding is high attenuation. Boundary is reflective. Single (60-100km) and MultiMode (2km) That’s about 36-62 miles versus 1.2 miles Disadvantage: $$$$$ Wireless Unguided Transmission. Higher Frequencies do not bend Wireless can reflect off different surfaces. i.e. Microwave reflects off stone and steel but passes through wood or sheet rock. Prone to interference (other devices) Common Bands: 0.9, 2.5, 5.0, & 5.8 GHZ Using Waves to Transmit Data f(t) = Asin(2πft + θ) The Sine Wave Amplitude Modulation Frequency Modulation Transmitting Digital Data using Analog Signalling PSK, a finite number of phases are used. FSK, a finite number of frequencies are used. ASK, a finite number of amplitudes are used. QAM, a finite number of at least two phases, and at least two amplitudes are used.