* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download 03-WAS Common Threats - Professional Data Management
Address space layout randomization wikipedia , lookup
Cryptanalysis wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Distributed firewall wikipedia , lookup
Cyberattack wikipedia , lookup
Security-focused operating system wikipedia , lookup
Unix security wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Wireless security wikipedia , lookup
Certificate authority wikipedia , lookup
Security and safety features new to Windows Vista wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Web of trust wikipedia , lookup
Quantum key distribution wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Computer security wikipedia , lookup
Diffie–Hellman key exchange wikipedia , lookup
Mobile security wikipedia , lookup
Social engineering (security) wikipedia , lookup
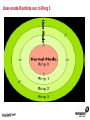
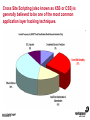
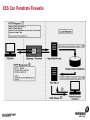
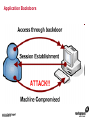
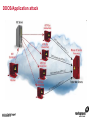
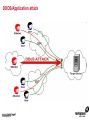
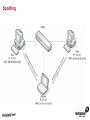
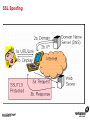
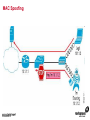
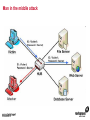
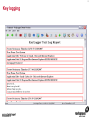
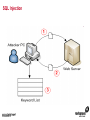
1 Module 3: Common Threats 2 Overview • • • • • • • • Root Kits and Boot Kits Cross Site Scripting Hidden Object (Services, Files and Users) Web Application Backdoors (C99.php, etc) Vulnerability Scan DDOS / Application Attack Spoofing DNS, SSL, MAC, etc Man in the middle attack 3 Overview - Continued • • • • • • Phishing Key Logging SQL Injection Mail form exploits Defacing Social Engineering 4 Root Kits and Boot Kits Rootkits • A root kit is software that enables continued privileged access to a computer • The term rootkit is a concatenation of the "root" user account in Unix operating systems • And "kit", which refers to the software components that implement the tool How to Detect Rootkits • Signature-Based Detection • Detection-By Comparison • Heuristic-Based Detection • Integrity-Based Detection How to protect from Rootkits • Install a good anti-malware solution on the computer, and always keep it activated and updated. • Install a personal firewall that will protect against unauthorized access to your computer. • Always ensure that the applications installed on computer are kept up-to-date, and make sure to install any security patches supplied by manufacturers. However, the task of protecting against rootkits is not to be taken lightly, and cannot be limited to a series of generic protection measures. User-mode Rootkits run in Ring 3 Bootkits • A kernel-mode rootkit variant called a bootkit • It is used predominantly to attack full disk encryption systems • A bootkit replaces the legitimate boot loader with one controlled by an attacker typically the mal ware loader persists through the transition to protected mode when the kernel has loaded 12 Cross Site Scripting Cross-site scripting (XSS) • Cross-site scripting (XSS) is a type of computer security vulnerability typically found in web applications • It enables malicious attackers to inject client-side script into web pages viewed by other users • Their impact may range from a petty nuisance to a significant security risk Exploit scenarios Cross-site scripting Non-persistent: • Alice often visits a particular website, which is hosted by Bob. Bob's website allows Alice to log in with a username/password pair and stores sensitive data, such as billing information. • Mallory observes that Bob's website contains a reflected XSS vulnerability. • Mallory crafts a URL to exploit the vulnerability, and sends Alice an email, enticing her to click on a link for the URL under false pretenses. This URL will point to Bob's website, but will contain Mallory's malicious code, which the website will reflect. Exploit scenarios Cross-site scripting • Alice visits the URL provided by Mallory while logged into Bob's website. • The malicious script embedded in the URL executes in Alice's browser, as if it came directly from Bob's server (this is the actual XSS vulnerability). • The script can be used to send Alice's session cookie to Mallory. Mallory can then use the session cookie to steal sensitive information available to Alice (authentication credentials, billing info, etc.) without Alice's knowledge. Exploit scenarios Cross-site scripting Persistent attack: • Mallory posts a message with malicious payload to a social network. • When Bob reads the message, Mallory's XSS steals Bob's cookie. • Mallory can now hijack Bob's session and impersonate Bob. Cross Site Scripting (also known as XSS or CSS) is generally believed to be one of the most common application layer hacking techniques. Cross-site scripting attacks XSS Can Penetrate Firewalls How to protect Cross-site scripting attacks • Encode output based on input parameters. • Filter input parameters for special characters. • Filter output based on input parameters for special characters. How to protect Cross-site scripting attacks • RULE #0-Never Insert Untrusted Data Except in Allowed Locations • RULE #1 - HTML Escape Before Inserting Untrusted Data into HTML Element Content • RULE #2 - Attribute Escape Before Inserting Untrusted Data into HTML Common Attributes How to protect Cross-site scripting attacks • RULE #3 - JavaScript Escape Before Inserting Untrusted Data into HTML JavaScript Data Values • RULE #4 - CSS Escape Before Inserting Untrusted Data into HTML Style Property Values • RULE #5 - URL Escape Before Inserting Untrusted Data into HTML URL Parameter Values How to protect Cross-site scripting attacks • RULE #6 - Use an HTML Policy engine to validate or clean user-driven HTML in an outbound way • RULE #7 - Prevent DOM-based XSS 25 Phishing 26 Phishing • In the field of computer security, phishing is the criminally fraudulent process of attempting to acquire sensitive information such as usernames, passwords and credit card details by masquerading as a trustworthy entity in an electronic communication. • Phishing is typically carried out by e-mail or instant messaging. 27 Phishing e-mail- Example An example of a phishing e-mail, disguised as an official e-mail from a (fictional) bank. The sender is attempting to trick the recipient into revealing confidential information by "confirming" it at the phisher's website. Note the misspelling of the words received and discrepancy. Such mistakes are common in most phishing emails. Also note that although the URL of the bank's webpage appears to be legitimate, it actually links to the phisher's webpage. Phishing techniques • Recent phishing attempts • Link manipulation • Filter evasion • Website forgery • Phone phishing • Other techniques Network-Based Phishing Protection • Vulnerability Filters • Pattern-Matching Signatures • Behavior-Based Protection Techniques • Content Inspection Phishing Protection Comprehensive Phishing Protection Against: • Initial Web Site Compromises • Mass Phishing E-mails • Click through on Misleading URLs • Displays of Phish Web Sites • Submissions of Personal Information 31 Hidden Object (Services, Files and Users) 32 Common Senarios Scenario #1 Your application relies on a powerful framework like ColdFusion or ASP.Net. XSS flaws are found in these framework components you rely on. An update is released to fix these flaws but you don’t update your libraries. Until you do, attackers can easily find and exploit these flaws in your app. Scenario #2 The app server admin console is automatically installed and not removed. Default accounts aren’t changed. Attacker discovers the standard admin pages are on your server, logs in with default passwords, and takes over. 33 Common Senarios Scenario #3 Directory listing is not disabled on your server. Attacker discovers she can simply list directories to find any file. Attacker finds and downloads all your compiled Java classes, which she reverses to get all your custom code. She then finds a serious access control flaw in your application. Scenario #4 App server configuration allows stack traces to be returned to users, potentially exposing underlying flaws. Attackers love the extra information error messages provide. 34 How to Protect The primary recommendations are to establish all of the following: A repeatable hardening process that makes it fast and easy to deploy another environment that is properly locked down. Development, QA, and production environments should all be configured identically. This process should be automated to minimize the effort required to setup a new secure environment. A process for keeping abreast of and deploying all new software updates and patches in a timely manner to each deployed environment. This needs to include all code libraries as well, which are frequently overlooked. A strong application architecture that provides good separation and security between components. Consider running scans and doing audits periodically to help detect future misconfigurations or missing patches. 35 Web Application Backdoors (C99.php, etc) Application Backdoors Common threats to Web Application 38 Common Senarios Buffer overflow attacks These kind of attacks involves sending overly long input streams to the attacked server, causing the server to overflow parts of the memory and either crash the system or execute the attackers arbitrary code as if it was part of the servers code. The attackers code can inject a backdoor code as well as set the return address of a function within the server code to point to the backdoor. When the function returns, the backdoor is successfully installed. 40 Common Senarios Remote Administration / Troubleshooting Administrators and sometimes developers directly connect to the application for troubleshooting but after finishing the job they might either forget to stop the related service or while fixing an instant problem in the application they may introduce insecure code; in both the cases attackers get an easy way to inject a backdoor which they later on use for information theft. 41 How to Protect • Develop documented secure practices for remote administration of server or for troubleshooting the application. • Ideally, development and production environment should be kept separate with no access to production for any programming changes. • Training of developers on secure coding in order to avoid attacks like buffer overflow and XSS. • Test all applications and any modification to application for security risks before rolling into production environment. • Routinely Audit for user accounts, configuration files and system files for the changes if any and ensure such changes have been authorized. • Purge all the logs after fixing a problem in the application. 42 Vulnerability Scan Vulnerability scan • A vulnerability scanner is a computer program designed to assess computers, computer systems, networks or applications for weaknesses • Functionality varies between different types of vulnerability scanners • They share a common, core purpose of enumerating the vulnerabilities present in one or more targets Types of Vulnerability Scanners • Port scanner • Network enumerator • Network vulnerability scanner • Web application security scanner 47 DDOS / Application Attack DDOS/Application attack • A denial-of-service attack (DoS attack) or distributed denial-of-service attack (DDoS attack) • It is an attempt to make a computer resource unavailable to its intended users Symptoms of denial-of-service attacks • Unusually slow network performance (opening files or accessing web sites) • Unavailability of a particular web site • Inability to access any web site • Dramatic increase in the number of spam emails received—(this type of DoS attack is considered an e-mail bomb) Modes of Dos attacks • It can include the consumption of resources such as the bandwidth, disk space • It can include the destruction or alteration of configuration information • It can includes destruction or alteration of Network components DDOS/Application attack DDOS/Application attack Measures for Network Admins • Measure I: Prevention of IP Spoofing • Measure 2: Use of Packet Filters for Network agents • Measure 3: Packet filtering • Measure 4: Automatic Attack recognition Measures for Network agents • Measure 5: Establishment of a contingency plan. • Measure 6: Secure Configuration of the Servers • Measure 7: Restrictive Granting of Rights and Recording • Measure 8: Use of Open Source Products Measures for Content Providers • Measure 1: Selection of suitable and IT safety-conscious server operators • Measure 2: Prevention of active Content: • Measure 3: Daily checking of files for viruses and attack programs 60 Spoofing DNS, SSL, MAC, etc Spoofing • In the context of network security, a spoofing attack is a situation in which one person or program successfully masquerades as another by falsifying data and thereby gaining an illegitimate advantage. • Spoofing is the creation of TCP/IP packets using somebody else's IP address. Routers use the "destination IP" address in order to forward packets through the Internet, but ignore the "source IP" address. That address is only used by the destination machine when it responds back to the source. Spoofing An Example of Spoofing • Spoofing has two main uses. The first use is an untraceable denial-ofservice attack. By intimately understanding the internal workings of TCP/IP, a hacker can abuse the software used in Internet communication and bring a network to its knees. • Flooding a network with packets that have a fake return address not only will slow the flooded network, but will also affect the computer that owns the forged return address. This is like sending out a thousand pieces of insulting mail to your boss while using the return address of your annoying neighbor (not recommended). DNS Spoofing • DNS spoofing works by forcing a DNS "client" to generate a request to a "server", then spoofing the response from the "server". • Most DNS servers support "recursive" queries. You can therefore send a request to any DNS server asking for it to resolve a name-to-address. • DNS servers will "cache" information for a certain amount of time. If an intruder can successfully spoof a response for "www.microsoft.com", any legitimate users of that DNS server will then be redirected to the intruder's site. DNS Spoofing SSL Spoofing 73 MAC Spoofing MAC Spoofing • MAC Spoofing is a technique of changing an assigned Media Access Control (MAC) address of a networked device to a different one • MAC spoofing is the activity of altering the MAC address of a network card. • A user may wish to legitimately spoof the MAC Address of a previous hardware device in order to reacquire connectivity after hardware failure. MAC Spoofing MAC spoofing may be done with the following programs: • Technitium Mac Address Changer (Windows) • SMAC (Windows) • iproute2 • ifconfig MAC Spoofing 77 Man in the middle attack Man in the middle attack In cryptography, the man-in-the-middle attack (often abbreviated MITM), bucket-brigade attack, or sometimes Janus attack, is a form of active eavesdropping in which: • The attacker makes independent connections with the victims • Relays messages between them, making them believe that they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker Man in the middle attack • A man-in-the-middle attack can succeed only when the attacker can impersonate each endpoint to the satisfaction of the other—it is an attack on mutual authentication 80 Example of an attack • Suppose Alice wishes to communicate with Bob. Meanwhile, Mallory wishes to intercept the conversation to eavesdrop and possibly deliver a false message to Bob . 1. Alice sends a message to Bob, which is intercepted by Mallory: Alice "Hi Bob, it's Alice. Give me your key"--> Mallory Bob 2. Mallory relays this message to Bob; Bob cannot tell it is not really from Alice: Alice Mallory "Hi Bob, it's Alice. Give me your key"--> Bob 3. Bob responds with his encryption key: Alice Mallory <--[Bob's_key] Bob 4. Mallory replaces Bob's key with her own, and relays this to Alice, claiming that it is Bob's key: Alice <--[Mallory's_key] Mallory Bob Example of an attack 5. Alice encrypts a message with what she believes to be Bob's key, thinking that only Bob can read it: Alice "Meet me at the bus stop!"[encrypted with Mallory's key]--> Mallory Bob 6. However, because it was actually encrypted with Mallory's key, Mallory can decrypt it, read it, modify it (if desired), re-encrypt with Bob's key, and forward it to Bob: Alice Mallory "Meet me in the windowless van at 22nd Ave!"[encrypted with Bob's key]--> Bob 7. Bob thinks that this message is a secure communication from Alice Man in the middle attack Tips to protect oneself from a MITM attack-End users • Look for the "green glow" in the address bar: Man-in-the-middle and phishing attacks in the wild today can be combated through Extended Validation (EV) SSL Certificates and to notice when there is an absence of green • EV SSL Certificates definitively confirm the identity of the organization that owns the Web site. Online criminals do not have access to EV SSL Certificates for the sites they're counterfeiting and therefore cannot spoof the green glow that shows that an authenticated Web site is secure. Tips to protect oneself from a MITM attack-End users • Download the latest version of high security Web browsers such as Internet Explorer 7 or higher, FireFox 3 or higher, Google Chrome, Safari or Opera. • Take advantage of authentication credentials such as tokens and other forms of two factor authentication for sensitive accounts. • Treat e-mails from unknown senders with a high degree of skepticism, and don't click links to access secure sites (type in the Web address into the browser). 90 Key Logging 91 Key logging • Keystroke logging (often called key logging) is the action of tracking (or logging) the keys struck on a keyboard • Typically in a covert manner so that the person using the keyboard is unaware that their actions are being monitored • There are numerous key logging methods, ranging from hardware and software-based approaches to electromagnetic and acoustic analysis 92 A log file from a software-based key logger. 93 Key logging Key logging • Software-based key loggers -Remote access software key loggers • Hardware-based key loggers -Wireless keyboard sniffers -Keyboard overlays Key logging • Acoustic key loggers -Electromagnetic emissions • Other -Optical surveillance How to protect from Key logging • Enable your firewalls. This is especially important if you are hooked up to a DSL/Broadband connection. • Install anti-spyware and anti-virus software. Key logger spyware often invades your PC system via viruses, Trojans and other malware. • Obtain and use an automated form-filler, particularly if you often enter personal or financial information at any website. How to protect from Key logging • Consider using an on screen keyboard. You would enter your information into this keyboard using your mouse rather than typing it in • Get an alternative keyboard layout. Most of the key logger software available is based on the traditional QWERTY layout • Use a one time password (OTP). An OTP is key logger proof, because once it is used, it is automatically invalidated. 98 SQL Injection SQL Injection • SQL injection is a code injection technique that exploits a security vulnerability occurring in the database layer of an application • The vulnerability is present when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and thereby unexpectedly executed SQL Injection Preventing SQL injection • Parameterized statements • Enforcement at the database level • Enforcement at the coding level 103 Mail form exploits Common Senarios • A would be spammer (the email variety, not a search engine spammer) googles for an email contact form. • If they find a ‘contact us’ page that is vulnerable they manipulate the form fields to add/change email headers. • They accomplish in much the same way a hacker would perform SQL injection or website search results injection. Common Senarios • By entering hexadecimal characters in the form field they are able to add carriage returns and spaces • So the following string entered in a form field such as “Your Email”: “[email protected]%0ACc:[email protected]%0ABcc:victim 2@victimsdomain • It will result in a carbon copy of the email being sent to [email protected] and a blind carbon copy being sent to [email protected] and [email protected] 106 How to Protect • Email exploit detection software analyzes emails for exploits – i.e., it scans for methods used to exploit the OS, email client or Internet Explorer – that can permit execution of code or a program on the user’s system. It does not check whether the program is malicious or not. It simply assumes there is a security risk if an email is using an exploit in order to run a program or piece of code. • In this manner, an email exploit engine works like an intrusion detection system (IDS) for email. The email exploit engine might cause more false positives, but it adds a new layer of security that is not available in a normal antivirus package, simply because it uses a totally different way of securing email. 107 Defacing 108 Common Senarios • A website defacement is an attack on a website that changes the visual appearance of the site. These are typically the work of system crackers, who break into a web server and replace the hosted website with one of their own. • A message is often left on the webpage stating his or her pseudonym and the output from "uname -a" and the "id" command along with "shout outs" to his or her friends. Sometimes, the Defacer makes fun of the system administrator for failing to maintain server security. Most times, the defacement is harmless, however, it can sometimes be used as a distraction to cover up more sinister actions such as uploading malware. • A high-profile website defacement was carried out on the website of the company SCO Group following its assertion that Linux contained stolen code. The title of the page was changed from "Red Hat v. SCO" to "SCO vs World," with various satirical content following. 109 How to Protect • Increase website security.Website security begins with managing the physical security of all servers. At the very least, web servers, application servers, communications servers, and communications equipment should be secured in a locked room accessible by those that have a need to access these devices. • Incorporate web server security.Securing the server in a locked room secures the hardware.But, what about securing the software and the data? After all, an attacker can still gain access through the connections and exploit vulnerable operating systems and web applications. Ensure the security updates and patches available for the operating systems and application software are current. Encrypt data and data streams accessing the server. If your company performs its own web application development, improve the web application security by adopting secure practices. 110 How to Protect • Install a web application firewall. You probably incorporate a firewall for the communications devices. A network firewall limits access to devices through various communications channels and analyzes incoming data with defined communications policies. Likewise, a web applications firewall analyzes incoming application data to determine if the data is legitimate or an attack on the system. • Tighten web application security. Many attackers exploit security vulnerabilities found in application and web application programs. If your company performs its own application and web application development, incorporate practices that do more to secure the code and eliminate holes that can be exploited. • Schedule regular security testing. How do you know if your systems are at risk? Well, you can wait until you are attacked and exploited, or you can take a proactive approach and develop security-testing policy and conduct security testing at regular intervals. 114 Social Engineering Social engineering Protect from Social engineering Security Awareness Is a Vital Defense • Two-Factor Authentication: Authentication for high-risk network services such as modem pools and VPNs should use two-factor authentication rather than fixed passwords. • Physical Security: The organization should have effective physical security controls such as visitor logs, escort requirements, and background checks. Example Common Scenarios Passive • You wave your FOB key near the detector or unlock a building door • You go in Attacker catches the door before it finishes closing and follows • You don't challenge or report attacker and keep going Example Common Scenarios Active • "Please, hold the door, I have my hands full! Thanks!“ • Someone calls your number from the door and asks to be "buzzed in" by saying "Please let me in, I forgot my key home and it's a 45 minute drive" and if necessary "I work/live on floor X, my name is _____, don't you remember me?" 119