* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download a client
Survey
Document related concepts
Network tap wikipedia , lookup
Computer network wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Deep packet inspection wikipedia , lookup
Remote Desktop Services wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Airborne Networking wikipedia , lookup
Internet protocol suite wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Distributed firewall wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Peer-to-peer wikipedia , lookup
Routing in delay-tolerant networking wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Service-oriented architecture implementation framework wikipedia , lookup
Transcript
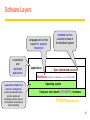
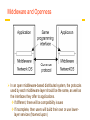
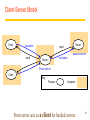
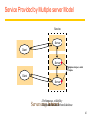
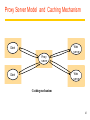
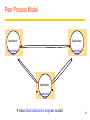
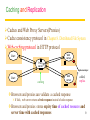
Revision Distributed Systems Introduction Distributed Systems A distributed system is: Distributed system is one in which components located at networked computers communicated and coordinate their actions only by passing message –G. Coulouris A collection of independent computers that appears to its users as a single coherent system. - S. Tanenbaum It leads to concurrency of components, lack of a global clock and independent failures of components - Characteristics of distributed systems Concurrency No Global clock Independent failures Why Distributed Systems? Main features Geographical distribution of autonomous computers Communication through cable/fiber/wireless/...connections A collection of independent computers that appears to its users as a single coherent system logically( called a single view system). Advantages interaction, co-operation, and sharing of resources Benefits reduced costs, improved availability and performance Scalability, resource sharing, fault tolerance. 3 Distributed Systems Data 0. - Distributed system ? Autonomous systems Computer network Distributed software Communication Network Data 0. - Important consequences Concurrency No global clock Independent failure 4 Distributed Systems- consequences Concurrency web pages / sharing resources No Global clock No single global notion of the correct time Independent failures slow network /unexpected termination each component of the system can fail independently Introduction of Distributed Systems Definitions of Distributed Systems A collection of independent computers that appears to its users as a single coherent system. A distributed system organized as middleware. Note that the middleware layer extends over multiple machines. 6 Importance of Distributed Computing Distributed (computer) systems are critical for functioning of many organizations Banks Transport Telecommunications Distributed Application A set of processes that are distributed across a network of machines and work together as an ensemble to solve a common problem 7 Typical examples The Internet global network of interconnected computers which communicate through IP protocols A vast interconnected collection of computer networks of many different types. An Intranets a separately administered network with a boundary that allows to enforce local security policies A portion of the Internet. Router/firewall exclusive File services/ Impeding Firewalls/The cost of installation Mobile and ubiquitous computing laptops, PDAs, mobile phones, printers, home devices, ... technological advance in device miniaturization and wireless networking. World-Wide Web system for publishing and accessing resources and services across the Internet HTML/URLs/HTTP/Dynamic Pages 8 Distributed Systems’ Challenges Challenges Heterogeneity Openness Security Scalability Failure handling Concurrency Transparency Due to: complexity size changing technologies society’s dependence Distributed Systems’ Challenges Heterogeneity Networks, hardware, OSs, P-languages…etc. Solution-Protocol, middleware. Openness Cumbersome & slow moving - follow standardization Security Hospital/E-commerce/banking Failure handling Software/hardware - proper policies Concurrency Sharing resource at the same time - operation should be synchronized Scalability / Transparency Heterogeneity varying software and hardware OSs, networks, computer hardware, program languages, implementations by different developers need for standards of protocols, middleware Heterogeneity and mobile code support virtual machine approach (cf, Java applets) 11 Openness independence of vendors publishable key interfaces CORBA(Common Object Request Broker Architecture) publishable communication mechanisms Java RMI(Remote Method Invocation) 12 Security confidentiality (protect against disclosure) cf, medical records integrity (protect against alteration and interference) cf, financial data Need encryption and knowledge of identity 1. Denial of Service attacks->Distributed DoS 2. Security of mobile code 13 Scalability Design of scalable distributed systems Controlling the cost of physical resource Controlling the performance loss Preventing software resource running out Avoiding performance bottleneck Examples of scalability limitations Concept Example Centralized services A single server for all users Centralized data A single on-line telephone book Centralized algorithms Doing routing based on complete information 14 Scalability Techniques (1) The difference between letting: No. of servers or clients a) a server or b) a client check forms as they are being filled Thin Thick(=fat) Thick(=fat) Thin 15 Scalability Characteristics of decentralized algorithms: No machine has complete information about the system state. Machines make decisions based only on local information. Failure of one machine does not ruin the algorithm. There is no implicit assumption that a global clock exists. Failure handling Ability to continue computation in the presence of failures. Detecting failures Masking failures(= hiding failure) Tolerate failures Recovery from failures Redundancy 17 Concurrency Processes execute simultaneously and share resources. synchronization inter-process communication(IPC) 18 Transparency Concealment of the separated nature of system from user/programmer =>Network transparency Access transparency + Location Transparency cf .log on, email, …. on network Transparencies=> By ANSA Reference Manual & ISO Reference Model for Open Distributed Processing (RM-ODP) 19 Transparencies(1) G. Coulouris •Access transparency: enables local and remote resources to be accessed using identical operations. •Location transparency: enables resources to be accessed without knowledge of their physical or network location (for example, which building or IP address). •Concurrency transparency: enables several processes to operate concurrently using shared resources without interference between them. •Replication transparency: enables multiple instances of resources to be used to increase reliability and performance without knowledge of the replicas by users or application programmers. Transparencies(2) G. Coulouris •Failure transparency: enables the concealment of faults, allowing users and application programs to complete their tasks despite the failure of hardware or software components. •Mobility transparency: allows the movement of resources and clients within a system without affecting the operation of users or programs. •Performance transparency: allows the system to be reconfigured to improve performance as loads vary. •Scaling transparency: allows the system and applications to expand in scale without change to the system structure or the application algorithms. Distributed Systems : System Models 22 Application Layering (1) Recall previously mentioned layers of architectural style The user-interface level The processing level The data level Application Layering (2) The simplified organization of an Internet search engine into three different layers. Multitiered Architectures (1) The simplest organization is to have only two types of machines: A client machine containing only the programs implementing (part of) the userinterface level A server machine containing the rest, the programs implementing the processing and data level Multitiered Architectures (2) Alternative client-server organizations (a)–(e). Client-Sever System ctd Client-Server Application DS. Client : Process that request a service Server : Process that provides a service Client blocks until server responds Client is invoked by end users when they require a service Server waits for incoming requests Server can have many clients making concurrent requests Server is a program with special system privileges 27 Client-Sever System – Applying Database system ctd “Gartner Group” - 2-tier Database system’s architecture user interface = presentation, application = logic, database = data Client system Server system X-Window Telnet World Wide Web(html, java–CGI http server) Network File(DB) systems Distributed databases 28 Client-Sever System ctd Gartner Group’ Configuration(2-tier, 3-tier Architectures) Client system Server system Distributed data : Distributed databases Remote data : Network File systems Distributed transaction : World Wide Web(html, java – CGI http server) Remote presentation : Telnet Distributed presentation : X-Window 29 Software Layers language and run-time support for program Interactions conventional and distributed applications applications extended services available to those of the distributed system Open (distributed) services Middleware( CORBA, Java RMI, Web service, DCOM, RD-ODP) responsible for basic local Operating system resource management (memory allocation/protection, process creation and scheduling, local inter-process communication and peripheral devices handling) Computer and network (TCP.UDP/IP). hardware Platform(green part) 30 Software layers ctd Service layers Higher-level access services at lower layers Services can be located on different computers Process types: server process client process peer processes(client process + server process) Ex. remote conferences 31 Important layers Platform lowest-level hardware+software( OS + Communication) common programming interface different implementations of operating system facilities for co-ordination & communication Middleware programming support for distributed computing 32 Software Concepts DOS (Distributed Operating Systems) NOS (Network Operating Systems) Middleware System Description Main Goal DOS Tightly-coupled operating system for multiprocessors and homogeneous multicomputers Hide and manage hardware resources NOS Loosely-coupled operating system for heterogeneous Offer local services to multicomputers (LAN and WAN) remote clients Middleware Additional layer atop of NOS implementing generalpurpose services Provide distribution transparency Network Operating System OSes can be different (Windows or Linux) Typical services: rlogin, rcp Fairly primitive way to share files Distributed Operating Systems But no longer have shared memory Provide message passing Can try to provide distributed shared memory But tough to get acceptable performance Distributed System as Middleware Middleware Definitions and Examples of Middleware 37 Middleware provides... ctd Support for distributed processes/objects: suitable for applications programming communication via the following mechanisms; remote method invocation (Java RMI), or remote procedure call (Sun RPC) Services infrastructure for application programs naming, security, transactions, event notification, ... Commercial products: CORBA, DCOM,… 38 Middleware and Openness 1.23 In an open middleware-based distributed system, the protocols used by each middleware layer should be the same, as well as the interfaces they offer to applications. If different, there will be compatibility issues If incomplete, then users will build their own or use lowerlayer services (frowned upon) Main types of Architecture models * Client-server architecture and Peer-to-peer architecture Client-server model first and most commonly used Multiple server model to improve performance and reliability e.g. search engines (more than 1000’s of computers) Proxy server model to reduce load on network, to provide access through firewall Peer process model when faster interactive response needed 40 Client-Server Model Client invocation Server result Backed server result invocation Server Front server Client Key: Process: Computer: Front server acts as a client for backed servers 41 Service Provided by Multiple server Model Service Server Client Server Replicated object, called Replica Client Server - Performance, reliability Servers -may interact Replicated and distributed database 42 Proxy Server Model and Caching Mechanism Web s erv er Client Prox y s erv er Web s erv er Client Caching mechanism 43 Peer Process Model Application Application Coordination code Coordination code Application Coordination code when faster interactive response needed 44 Horizontal Distribution Distribute servers across nodes E.g., Web server for load balancing Distribute clients in peer-to-peer systems. Client-server and mobility Mobile code downloaded from server, runs on locally e.g. web applets Mobile agent (code + data) travels from computer to another collects information, returning to origin => Beware! Security risks 46 Web applets Client requests results, applet code is downloaded; Client Applet code Web server Client interacts with applet; Client Applet Web server 47 Thin & Fat Clients Thin client = Network computer Typically no local storage has only presentation function(= user interface) Fat Client = Desktop PC, Workstation has both presentation function and logic function (=application) Motivation for Thin Clients Hidden costs of System administration and supports Networks computers move toward centralized system Admin. , but local processing at client Java(mobile code) an enabling technology E.g. PDA 48 Design Requirements for Distributed Architectures Judging how good the architecture is... 1)Performance how fast will it respond? 2)Quality of Service(QoS) are video frames and sound synchronized? 3)Dependability does it work correctly? 49 1) Performance Responsiveness fast interactive response delayed by remote requests use of caching, replication Throughput dependent on speed of server and data transfer Load balancing use of applets, multiple servers 50 Caching and Replication Caches and Web Proxy Servers(Proxies) Cache consistency protocol in Chapter 8. Distributed File System Web-caching protocol in HTTP protocol Web server Client Proxy server Replicated object Client caching Web server called, replica Browsers and proxies can validate a cached response If fails, web server returns a fresh response instead of stale response Browsers and proxies stores expiry time of cached resource and server time with cached responses 51 2) Quality of Service (QoS) Non-functional properties experienced by users: Deadline properties hard deadlines (must be met within T time units) soft deadlines (`there is a 90% chance that the video frame will be delivered within T time units, ex, 10 units -90% 9units) multimedia traffic, video/sound synchronization depend on availability of sufficient resources Adaptability ability to adapt to changing system configuration 52 3) Dependability Correctness Ensuring correctness of distributed and concurrent programs e.g. use of verification Fault-tolerance ability to tolerate/recover from faults e.g. use of redundancy Security ability to withstand malicious attack e.g. use of encryption, etc 53 Fundamental Models for Distributed Systems Sharing some fundamental properties processes that communicate with one another by sending msgs Essential ingredients of System model what are the main entities in the systems ? how do they interact ? what are characteristics that affect their individual and collective behavior ? Purpose of system model to make explicit relevant assumptions at system modeling to generate the concerning possible or impossible assumptions 54 3 Fundamental Models ctd Discussions of fundamental models Interaction Model Failure Model Security Model (skipped in this review) 55 Interaction Model Distributed systems have many processes, complex interactions among them transmission of message between processes(local, remote) Interacting processing communication performance impossible to maintain global time( each system has its local time) Performance of communication channel Latency(message, network, system) bandwidth Jitter 56 Interaction Model ctd Computer clocks and timing events clock drift rate(Global time needed) clock synchronization Two variants of the interaction model Synchronous DS has on; process is executing in a known lower/ upper bounded time message is received within a known bounded time known local clock’s drift rate Asynchronous DS has no bounds on; process execution speed message transmission delay clock drift rate -so, not suitable for multimedia service 57 Failure Model In DS, processes and channels may failure 3 failures : Omission, Arbitrary, timing failures Omission failures process omission failures Correct, fail-stop, timeouts communication failures send/receive omission failures process p process send m q Receive Communication channel Outgoing message buffer Incoming message buffer 58 Failure Model ctd Omission and arbitrary failures Class of failure Fail-stop Affects Process Crash Process Omission Channel Send-omission Process Receive-omission Process Arbitrary (Byzantine) Process or channel Description Process halts and remains halted. Other processes may detect this state. Process halts and remains halted. Other processes may not be able to detect this state. A message inserted in an outgoing message buffer never arrives at the other end’s incoming message buffer. A process completes as end, but the message is not put in its outgoing message buffer. A message is put in a process’s incoming message buffer, but that process does not receive it. Process/channel exhibits arbitrary behaviour: it may send/transmit arbitrary messages( with wrong values) at arbitrary times, commit omissions; a process may stop or take an incorrect step. 59 Failure Model ctd Arbitrary failures(=Byzantine failure, Data failure) Process/channel exhibits arbitrary behaviour(delivering corrupted, nonexisted message ) Timing Failures Class of Failure Clock Affects Process Description Performance Process Process exceeds the bounds on the interval Performance Channel Process’s local clock exceeds the bounds on its rate of drift from real time. between two steps. A message’s transmission takes longer than the stated bound. The others; Masking failures Checksum failure Failure of reliability of one-to-one communication Threats of validity and integrity 60 Networking and Interworking in DS Inter-Process Communication Operating System Support Dr. Sunny Jeong. [email protected] With Thanks to Prof. G. Coulouris, Prof. A.S. Tanenbaum and Prof. S.C Joo 61 Network issues in DSs Performance Latency Data transfer rate Message transfer rate time = latency + a massage length/ data transfer rate Total system bandwidth of network Throughput in the end systems total volume of traffic can be transferred across network in a time Scalability No designable to cope with size and load about network growing Reliability recoverable from communication failures 62 Network issues in DSs ctd Security protecting network and computers, ex) firewall between intranet and internet Mobility portability of computer and handled digital devices using wireless network location and identification are depicted with each other no designable to cope with size and load about network growing QoS(Quality of Service) guarantee for requirements of computer and network to meet deadline, bandwidth, bounded latency Multicasting One-to-many communication 63 Network principles Mode of transmission Switching schemes Protocol suites Routing Congestion control 64 Mode of transmission Packets messages divided into packets( on Transport Layer) packets queued in buffers before sent onto link QoS not guaranteed Data streaming links guarantee QoS (rate of delivery) for multimedia traffic need higher bandwidth 65 Switching schemes Broadcasts (Ethernet, wireless) send messages to all nodes nodes listen for own messages (carrier sensing) Circuit switching (phone networks) Packet switching (TCP/IP) store-and-forward unpredictable delays Frame/cell relay (ATM) bandwidth & latency guaranteed (virtual path) small, fixed size packets (padded if necessary) 53bytes= header 5 + body 48 avoids error checking at nodes (use reliable links) 66 Protocols ( ISO Open System Interconnection view) (Trivial File Transfer Protocol) Internet Control(Group) Message Protocol (Reverse Address Resolution Protocol) 67 OSI protocol summary Layer Application Description Protocols that are designed to meet the communication requirements of specific applications, often defining the interface to a service. Protocols at this level transmit data in a network representation that is independent of the representations used in individual computers, which may differ. Encryption is also performed in this layer, if required. At this level reliability and adaptation are performed, such as detection of failures and automatic recovery. Examples HTTP, FTP , SMTP, CORBA IIOP Secure Sockets (SSL),CORBA Data Rep. Transport This is the lowest level at which messages (rather than packets) are handled. Messages are addressed to communication ports attached to processes, Protocols in this layer may be connection-oriented, or connectionless. TCP, UDP Network Transfers data packets between computers in a specific network. In a WAN or an internetwork this involves the generation of a route passing through routers. In a single LAN, no routing is required. Responsible for transmission of packets between nodes that are directly connected by a physical link. In a WAN transmission is between pairs of routers or between routers and hosts. In a LAN it is between any pair of hosts. The circuits and hardware that drive the network. It transmits sequences of binary data by analogue signalling, using amplitude or frequency modulation of electrical signals (on cable circuits), light signals (on fibre optic circuits) or other electromagnetic signals (on radio and microwave circuits). IP, ATM virtual circuits Presentation Session Data link Physical Ethernet MAC, ATM cell transfer, PPP Ethernet base- band signalling, ISDN 68 Internetwork protocol Intenetwork layer(=Virtual network layer) internet packet destination (by datagram protocol) Network interfaces layer Internetwork packets suitable packets underlying layer Message Underlying network layer Layers Application Internetwork protocols Transport Internetwork Internetwork packets Network interface Network-specific packets Underlying network protocols Underlying network 69 Port & Addressing Port network-independent message transport service between networks ports software-definable destination points for communications Addressing delivering messages to destination with transport addresses Transport address Network address + port number 70 Packet delivery In network layer datagram packet delivery(IP in Ethernet, most wired and wireless LAN technologies) virtual circuit packet delivery(ATM) In transport layer connection-oriented transmission(TCP) Reliable communication with static routing table(ISO, X.25) Ex) remote login(Telnet), FTP, HTTP(big-sized file), stream data connectionless transmission(UDP) Unreliable communication with pre-defined routing table Ex) rcp, rwho, RPC, HTTP(small-sized file), FTP(non-error bulk file) 71 Routing Necessary in non-broadcast networks (cf Internet) : Hop by Hop Distance-vector algorithm for each node stores table of state & cost information of links, cost infinity for faulty links determines route taken by packet (the next hop) periodically updates the table and sends to neighbors may converge slowly [Bellman-Ford] RIP-1(Router Information Protocol) for Internet Local router table changes use default routes, plus multicast and authentication better convergence( routes better route to an existing destination) 72 Congestion control When load on network exceeds 80% of its capacity packet queues long, links blocked Solutions(in datagram-based network layers) packet dropping reliable of delivery at higher levels reduce rate of transmission nodes send choke packets (Ethernet) special message requesting a reduction in transmission rate transmission control (TCP) transmit congestion information to each node QoS guarantees (ATM) 73 Transport level protocols UDP (basic, used for some IP functions) uses IP address+port number no guarantee of delivery, optional checksum messages up to 64KB Connectionless transmission( Unreliable and Asynchrnous communication with pre-defined routing table) Datagram service Ex) rcp, rwho, RPC, HTTP(small sized), FTP(non-error bulk file) TCP (more sophisticated, most IP functions) data stream abstraction, reliable delivery of all data messages divided into segments, sequence numbers sliding window, acknowledgement+retransmission buffering (with timeout for interactive applications) checksum (if no match segment dropped) Connection-oriented transmission( Reliable and Synchronous communication with static routing table(ISO, X.25)) Stream service Ex) remote login(Telnet), FTP, HTTP(bulk file), stream data 74 IP(TCP/IP) Addressing IP Address(IPv4) 75 IP(TCP/IP) Addressing ctd IP Structure(Universal)(IPv4 : 4bytes: 32bits) 7 Class A: 0 24 Network ID Host ID 14 Class B: 1 0 16 Network ID Host ID 21 Class C: 1 1 0 8 Network ID Host ID 28 Class D (multicast): 1 1 1 0 Multicast address 27 Class E (reserved): 1 1 1 1 0 unused IP Packet layout header IP addres s of s ource IP addres s of des tination up to 64 kiloby tes data 76 IP(TCP/IP) Addressing ctd octet 1 octet 2 Network ID Class A: 1 to 127 Class C: Range of addresses Host ID 0 to 255 0 to 255 1.0.0.0 to 127.255.255.255 0 to 255 0 to 255 128.0.0.0 to 191.255.255.255 0 to 255 Host ID 1 to 254 0 to 255 Network ID Class B: octet 4 octet 3 Host ID 128 to 191 0 to 255 192 to 223 Network ID 0 to 255 192.0.0.0 to 223.255.255.255 Multicast address Class D (multicast): 224 to 239 0 to 255 0 to 255 1 to 254 224.0.0.0 to 239.255.255.255 Class E (reserved): 240 to 255 0 to 255 0 to 255 1 to 254 128.0.0.0 to 247.255.255.255 • • • • Address Address Address Address 194.0.0.0 198.0.0.0 200.0.0.0 202.0.0.0 to to to to 195.255.255.255.are 199.255.255.255.are 201.255.255.255.are 195.203.255.255.are in in in in Europe N. America Central & South America Asia and Pacific 77 IPv4-> IPv6 IPv6 Address • Large Address space - 128 bit addresses –Every toaster can have its own IP address • Aggregation-based address hierarchy –Efficient backbone routing • Efficient and Extensible IP datagram –No fragmentation by routers –64 bits field alignment –Simpler basic header • Auto-configuration • Security • IP Renumbering part of the protocol 78 IPv4-> IPv6 3FFE:0B00:0C18:0001:0290:27FF:FE17:FC0F TLA NLA(s) 16 bits 32 bits SLA 16 bits Interface ID 64 bits TLA – top level aggregator Primary providers NLA: Next Level Aggregator Can have multiple NLA as sub-NLA SLA: Site Level Aggregator Your site (16 bits) Addresses are allocated from your provider If you change provider, your prefix changes But renumbering (of hosts, routers and sites) has been included in the IPv6 protocol 79 IPv4-> IPv6 IPv6 Header layout(16bytes : 128bits) Version (4 bits) Priority (4 bits) Flow label (24 bits) Payload length (16 bits) Next header (8 bits) Hop limit (8 bits) Source address (128 bits) Destination address (128 bits) IPv6’s main advances(Adapted by IETF in 1994) address space(2128 = 3×1038 IPs), routing speed up Real-time and other special services Future evolution Multicating & anycasting security 80 MobileIP At home normal, when elsewhere mobile host: notifies HA(Home Agent) before leaving informs FA(Foreign Agent), who allocates temporary care-of IP address & tells HA Packets for mobile host(MH): first packet routed to HA, encapsulated in MobileIP packet and sent to FA (tunnelling) FA unpacks MobileIP packet and sends to mobile host sender notified of the care-of address for future communications which can be direct via FA Problems efficiency low, need to notify HA 81 MobileIP routing Sender 4.Subsequent IP packets tunnelled to FA Mobile host (MH) 3.Address of FA returned to sender 1.First IP packet addressed to MH Internet Foreign agent(FA) Home Agent HA 2.First IP packet tunnelled to FA 82 Asynchronous Transfer Mode(ATM) Asynchronous Transfer Mode(ATM) Multimedia data(voice and video), distributed system services Packet switching network based on Cell-relay(a method of packet routing) Avoiding flow-control and error checking at the intermediate nodes Small and fixed length unit of data transmitted(53bytes= header 5 + body 48) reduction of buffer size, complexity, queuing delay at intermediate nodes B-ISDN(CCITT I.150 standard) Optical fiber transmission medium(155 - 622 megabits/sec) ATM protocol layers 83 Asynchronous Transfer Mode(ATM)- ctd ATM protocol Layer Mess age Lay ers A pplic ation Higher-lay er protoc ols A TM adaption layer A TM cells A TM layer A TM virtual channels Phy sical ATM cell layout Header: 5 by tes Virtual path id Virtual channel id Flags Data 53 byt es 84 Operating System Support Functionality of the Operating System (OS) resource management (CPU, memory, …) Processes and Threads Similarities V.S. differences multi-threaded servers and clients Implementation of... communication primitives Invocations 85 Operating System Support Resource sharing CPU (single/multiprocessor machines) concurrent processes/threads communication/synchronization primitives process scheduling memory (static/dynamic allocation to programs) memory manager file storage and devices file manager, printer driver, etc OS kernel implements CPU and memory sharing abstracts hardware Monolithic VS Microkernel 86 Distributed System layers Applications, services Middleware OS: kernel, libraries & servers OS1 Processes, threads, communication, ... OS2 Processes, threads, communication, ... Computer & network hardware Computer & network hardware Node 1 Platform Node 2 87 Core OS functionality Process manager Communication manager Thread manager Memory manager Supervisor 88 Core OS components Process manager creation and operations on processes (= address space+threads) Threads manager threads creation, synchronization, scheduling Communication manager communication between threads (sockets, semaphores) in different processes(concurrency) on different computers(parallel) Memory manager physical (RAM) and virtual (disk) memory Supervisor hardware abstraction (dispatching of interrupts, exceptions, system call traps) control of memory managements and hardware cache 89 Why middleware again... 90 Why middleware again... 91 Why middleware again... Network OS ex) UNIX, Windows NT network transparent access for remote files (NFS) no task/process scheduling across different nodes services rlogin, telnet, ftp, WWW 92 Why middleware again...ctd 93 Why middleware again...ctd Distributed OS (Mach..) transparent process scheduling across nodes load balancing none in use: cost of switching OS too high, load balancing not always easy to achieve 94 Why middleware again... ctd : NOS : NOS : DOS Distributed Operating System Services 95