* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download ATM services spport in WT
Wireless security wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
TV Everywhere wikipedia , lookup
Net neutrality law wikipedia , lookup
Computer network wikipedia , lookup
Distributed firewall wikipedia , lookup
Network tap wikipedia , lookup
Airborne Networking wikipedia , lookup
Policies promoting wireless broadband in the United States wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Point-to-Point Protocol over Ethernet wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
National Broadband Plan (United States) wikipedia , lookup
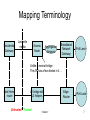
DAD in N:1 VLANs Reminding the issue – following Broadband Forum liaison to IETF#76 Christophe ALTER Broadband Forum Ambassador France Telecom Orange Multipoint-to-point access architecture Ethernet bridging in the Access Node Multiple subscribers are connected to a given VLAN (VLAN per service - no VLAN per Customer) All subscribers have layer 2 connectivity with the Broadband Network Gateway (BNG) No layer 2 connectivity between subscribers X N Subscribers 2 1 VLAN Access/Aggregation Nodes DSLAM / OLT BNG IP Edge Router IP Backbone Multipoint-to-point access architecture A popular Ethernet architecture in broadband service provider networks – Call it split-horizon, E-Tree, N:1 VLAN or multipoint-to-point – Found in xDSL and FTTx deployments (Broadband Forum), Enterprise networks (Metro Ethernet Forum) and Cable deployments 3 Chosen mainly for scalability – Typically 10 000s subscribers per VLAN – Avoids overloading every subscriber with every other subscriber broadcasts – Provides privacy between subscribers Issue to be resolved Deriving LLAs from MACs doesn’t prevent LLA duplicates – Because there might be duplicate MAC addresses in (untrusted) subscribers’ domains – Although MAC uniqueness in the service provider’s (trusted) domain is somehow ensured (typically through MAC Address Translation by the Access Node, c.f. Broadband Forum WT145) DAD is needed to prevent / resolve duplicate link local addresses - helping hosts that use DAD – But subscribers don’t have layer 2 connectivity to each other – Although they are connected to the BNG through a single VLAN 4 Some helper function is needed in the IP Edge Router to allow DAD to work in split horizon environments – This is what SAVI is kindly requested to define. Issue to be resolved DAD-NS: Hey, I’d like to use LLA1 ; anyone already using it ? DAD-NA: is already in use, please choose another X N Subscribers 5 1 VLAN Access/Aggregation Nodes DSLAM / OLT ? BNG IP Edge Router IP Backbone Backup / Archives The following slides were presented to IETF#76 by Dave Allan, Broadband Forum WG Chair Mapping Terminology Residential Gateway Last mile media Access Node Aggregation Network Broadband Network Gateway IPv6 Land Unlike a normal bridge The AN has a few diodes in it… Host/Home router L2 bridge with L3 helpers Untrusted Trusted <footer> Edge Router IPv6 Land 7 Background (From BBF 2009.877.01) • In order to enable IPv6 connectivity, every host must first of all create a link-local address (of the range FE80::/64) in order to allow communication on a single link. • The procedure for creating link-local addresses is defined in RFC 4862 [1]. When an IPv6 interface becomes active it will first concatenate it’s Interface ID with the link-local prefix FF08::/64. • The Interface ID for<footer> an Ethernet interface 8 Current state of the art in Uniqueness (From BBF 2009.877.01) • To protect against cases where the Interface ID would not be unique, IPv6 nodes test their address on the IPv6 link using Duplicate Address Detection (DAD). This test is performed to ensure uniqueness of the link-local address on the link. In case the Interface ID is derived from the MAC address, then link-local addresses should always be unique. • The above procedures work well in a trusted environment. Contrary to a trusted 9 <footer> network deployment, a broadband access Complication (From BBF 2009.877.01) • Even if the customer equipment was benign and altruistic w.r.t. network behaviour, direct layer 2 user-touser communication is controlled in a broadband access network by means of split-horizon forwarding, per TR101. • As a result, link-local connectivity only exists between the host and the BNG/edge router. There is no way for the individual hosts to know whether they are using duplicate link-local addresses as direct observation of neighbours traffic is precluded. – Editorial comment: This is not unique to BBF TR101, numerous link layers exhibit this behaviour (e.g. HFC or PON), and this can be virtualized at the networking level (e.g. MEF ETREE service definition, 802.1ad (2005) Asymmetric VID, 802.1ah/.1aq also support this model) <footer> 10 Consequences (From BBF 2009.877.01) • When deploying a plain IPv6 router that is not subscriber-aware, different hosts / RGs using the same link-local address would force the router to overwrite the corresponding entry in the Neighbor Cache. This can lead to a Theft of Service attack. <footer> 11 What is Needed (From BBF 2009.877.01) • When numerous hosts share an Ethernet broadcast domain, the BNG/edge router needs to support a mechanism that ensures duplicate link-local addresses can be handled correctly without necessarily depending on cooperative action by the hosts – it is explicitly required to do something to make this happen <footer> 12