* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Sigurnost bezicnih racunalnih mreza
Point-to-Point Protocol over Ethernet wikipedia , lookup
Net neutrality law wikipedia , lookup
Airborne Networking wikipedia , lookup
Computer security wikipedia , lookup
TCP congestion control wikipedia , lookup
Wireless security wikipedia , lookup
Computer network wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
Network tap wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Internet protocol suite wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Packet switching wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
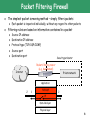
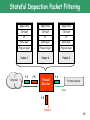
Kriptografija i mrežna sigurnost Network Firewalls Mario Čagalj [email protected] FESB Sveučilište u Splitu 2013. Introduction o Computer security is hard o Security of networked computers is much harder o o o o Organizations/companies/universities are connected to the Internet “Outside world” can reach and interact with local network assets Internal networks comprise hundreds of computers running Unix, Win Local computers running different (potentially vulnerable) services • FTP, Telnet, DNS, ARP, rlogin, Skype, POP, IMAP, ICMP… • New Internet vulnerabilities and flaws discovered on a daily basis o How to protect efficiently a large heterogeneous internal network? o Security flaws discovered -> upgrade each potentially affected system • Does this approach scale well? o Better, insert a firewall between the internal network and the Internet • Establish a controlled link between the internal trusted network and the untrusted network (e.g., Internet) 2 What is a Firewall? o Originally, firewall used to define a barrier constructed to prevent the spread of fire from one part of the building to another o Network firewalls are barriers between networks, which prevent or deny unauthorized traffic between the networks o There exists no unified definition, but essentially: A network firewall is a system or a group of systems used to control access to or from a protected (trusted) network, using preconfigured set of rules and filters. Trusted network Untrusted network Firewall o Firewalls can be a single router, multiple routers, a single host system or multiple hosts running firewall software, hardware device or any combination 3 Firewall Characteristics o Main design goals o All traffic from inside to outside, and vice versa, must pass through the firewall o Only authorized traffic (as defined by the local security policy) will be allowed to pass o The firewall is immune to penetration o What firewalls can do – positive effects? o User authentication • Firewalls can be configured to require user authentication • Enforce different access control policies (different users different rights) o Auditing and logging • Useful statistics for updating current security and utilization policies o Security and privacy • Some firewall systems can hide internal (trusted) networks from external (untrasted) networks - Network Address Translator (NAT) • No DNS traffic outside the internal network • Can shield services from unwanted scans 4 Firewall Characteristics contd. o What firewalls can do – negative effects? o Traffic bottlenecks • All the traffic is forced to go through the firewall system (to be inspected) o Single point of failure o Complex management o User frustration • “Arrgh, my Skpye communication doesn’t go through!” • Users may try to go around -> a serious security problem o What firewalls cannot do? o Installed firewall does not imply that the protected network is 100% secure (other security measures necessary) o Firewalls does not protect against inside attacks • Inside traffic is not routed through the firewall o Unwanted and unauthorized backdoors • Modem dial-in access, WiFi access o Firewalls cannot protect against the transfer of viruses or malicious codes • Generally, firewalls do not inspect a packet payload (not practical) 5 Basic Firewall Design Policies o Firewalls generally implement one of two basic design policies: 1. Permit any service unless it is explicitly denied 2. Deny any service unless it is explicitly permitted o 1st policy o Firewall allows all services to pass into the internal network by default o Blocks those services that the service access policy has identified as disallowed o More flexible but less desirable than the 2nd design policy o 2nd policy o o o o Firewall denies all services by default Passes those services that have been identified as allowed Stronger and safer than the 1st policy Legitimate traffic may suffer until the correct rules and filters identified and implemented o Most often recommended 6 Types of Firewalls o Firewall’s basic design policies can be enforced by using different types of packet-screening (inspection) methods o The packet-screening methods are distinguished by how firewalls use pre-configured rules, filters, information gathered from packets and sessions to allow or deny traffic o The three common types of firewalls (screening methods) are: o Packet Filtering firewall o Stateful packet Inspection firewall o Application-level Gateways/proxies Application TCP/UDP IP + hybrid methods Application Gateways Packet Filters Stateful Inspection Data-link layer Physical layer TCP/IP protocol suite 7 Packet Filtering Firewall o The simplest packet screening method – simply filters packets o Each packet is inspected individually, without any regard to other packets o Filtering rules are based on information contained in a packet o o o o o Source IP address Destination IP address Protocol type (TCP/UDP/ICMP) Source port Destination port Security perimeter Packet-filtering router (e.g., dual-homed) Internet Private network Application 2 1 TCP/UDP IP 2 Data-link layer Physical layer 8 Packet Filtering Firewall contd. o Operation: o The packet filter is set up as a list of rules based on matches to fields in the IP or TCP headers o If there is a match to one of the rules, the rule is invoked to determine whether to forward or discard the packet o If there is no match to any rule, a default action is take • Discard (2nd firewall design policy) • Forward (1st firewall design policy) Action Ourhost IP Port Theirhost IP Port allow Host A 25 * * “*” is a wildcard designator that matches everything. “SMTP (Simple Mail Transfer Protocol) Port 25” is the port used to send/receive e-mail. 9 Packet Filtering Rules: Examples Action Ourhost IP Port Theirhost IP Port block * * Host A * allow Host B 25 * * Inbound mail is allowed (port 25 is for SMTP incoming), but only to Host B. Packets from an external Host A are blocked because that host does not comply with our email policy. Action Ourhost IP Port Theirhost IP Port block * * * * An explicit statement of the default policy. All rule sets include this rule implicitly as the last rule. Action Ourhost IP Port Theirhost IP Port allow * * * 25 Specifies that any inside host can send mail to the outside. However, this rule also allows to an enemy to access to any internal host and port by originating his call from port 25 on the outside machine! We have to make distinction between incoming and outgoing packets to solve this problem. 10 Packet Filtering Rules: Examples Action Src IP Port Dest IP Port allow {our hosts} * * 25 allow * 25 * * Flag ACK SMTP is based on TCP protocol. A TCP conversation consists of packets flowing in two directions. Even if all of the data is flowing one way, acknowledgment packets and control packets must flow the other way. We want to accomplish that only internal host can make calls to someone’s port 25. We can do this by paying attention to the direction of the packet, and by looking at some of the control fields. In particular, an initial open request packet in TCP does not have the ACK bit set in the header; all other TCP packets do. Thus, packets with ACK set are part of an ongoing conversation; packets without it represent connection establishment messages, which we will permit only from internal hosts. The idea is that an outsider cannot initiate a connection, but can continue one. From: “Firewalls and Internet Security: Repelling the Wily Hacker.” Cheswick and Bellovin, 2003. 11 Packet Filtering: Advantages o Simplicity o Each packet inspected without any regard to other packets from the same connection o Speed o Packet filtering is done at the lower levels of the OSI model, the time it takes to process a packet is much quicker o Transparent to the user o Require no additional configuration for clients o Packet filtering firewalls are typically less expensive o Usually present in standard firewall package o Scale better than other types of firewalls o Lower processing overhead o Packet filtering firewalls are application independent 12 Packet Filtering: Disadvantages o Defining rules can be a very complex task o Packer-filtering firewalls do not support user authentication o Packet filters cannot prevent attacks that employ application specific vulnerabilities o Packet-filter firewalls do not examine upper-layer data o E.g., they cannot block specific application commands o Vulnerable to IP address spoofing attacks o The intruder transmits packets from the outside with a source IP address set to an address of an internal host o Countermeasure: discard any packet with an internal source address if the packet arrives on an external interface o Vulnerable to the packet fragmentation attack o Typically, a packet filter will make a filtering decision based on the first fragment of the packet o The intruder uses the IP fragmentation option to create small fragments such that the TCP header information is forced into a separate fragment 13 Stateful Inspection Firewalls o Uses the same packet-screening technique as packet filtering o In addition, takes into account higher layer(s) context o Inspects the packet from the network layer to the application layer to verify that the packet is part of a legitimate connection o Stateful packet inspection process o Packet header information is examined and stored into a dynamic state table o The packets are first compared to pre-configured rules or filters and allowed to passed or blocked o The state table is then used to evaluate subsequent packets to verify that they are part of the same connection o The decision can be made based on the following information o o o o o o Source IP address Destination IP address Protocol type (TCP/UDP/ICMP) Source port Destination port Connection state (derived from information gathered in previous packets) 14 Stateful Inspection Packet Filtering Internet Application Application Application TCP/UDP TCP/UDP TCP/UDP IP IP IP Data layer Data layer Data layer Physical layer Physical layer Physical layer Packet 1 Packet 2 Packet 3 P 4 P 5 Firewall Rule Set P 4 Private network Allow P 5 Discard 15 Stateful Firewall: Connection State Table o Contains an entry for each currently established connection o The packet filter will allow incoming traffic to ports only for those packets that fit the profile of one of the entries Source Address Source Port Destination Address Destination Port Connection State 192.168.1.100 1030 210.9.88.29 80 Established 192.168.1.102 1031 216.32.42.123 80 Established 192.168.1.101 1033 173.66.32.122 80 Established 192.168.1.106 1035 177.231.32.12 80 Established 223.43.21.231 1990 192.168.1.6 80 Established 210.99.212.18 2112 192.168.1.6 80 Established 24.102.32.23 1025 192.168.1.6 80 Established 16 Stateful Inspection: Pros and Cons o Advantages: o Very little impact on network performance (very fast) o Application independent and transparent to users o More secure than basic packet-filtering (determines the connection state between endpoints) o Have logging capabilities o Disadvantages o Rules and filters quite complex to set, test and manage o Allows a direct connection to be made between two endpoints (like basic packet filtering) 17 Application-level Gateway/Proxy o Also called a proxy server, considered the most complex packet screening method o Acts as a relay of application-level traffic o Uses the application layer information to filter packets Outside connection TELNET Inside connection FTP SMTP Outside host HTTP Inside host Application-level gateway o The direct connection is broken into two separate connections o Interfaces on the proxy server do not forward packets -> a proxy service must be implemented for each application protocol 18 Application Gateway/Proxy Operation o Outside connection o A client issues a request to the gateway o A connection is established between the client and the proxy o The proxy determines if the request is valid (by using the filter and rules) and optionally if the user is authorized for the requested service (user’s authentication) o In turn, the proxy sends a new request on behalf of the client to the desired destination o Inside connection o The destination responds to the proxy server o The proxy determines if the response is valid o In turn, the proxy sends back the response from the destination to the client 19 Application Gateway: Pros and Cons o Advantages o Does not allow direct connections between internal and external hosts o Can analyze application commands of data packets o Does not route between an internal and an external networks • Hides the internal network topology (similar to NAT) o Supports user-level authentication o Supports logging at the application level o Perhaps the most secure type of firewall o Disadvantages o o o o Can have a significant impact on network performance Each protocol (HTTP, FTP, SMTP) requires its own proxy application Vulnerable to Denial-of-Service attacks Does not scale well 20 Circuit-level Gateway o o o o Does not examine individual packets Instead, they monitor TCP or UDP sessions Security consist of determining which connections will be allowed Once a session has been established, it leaves the port open to allow all the packets from the same session to pass o In many respects similar to application gateway, with the difference that it operates at the Transport layer Outside connection Outside host Out In Out In Out In Inside connection Circuit-level gateway Inside host 21 Application of a Circuit-level Gateway o A typical use is a situation in which the system administrator trusts the internal users o The gateway can be configured to support application-level service on inbound connections and circuit-level functions for outbound connection o The gateway can incur processing overhead of examining incoming application data o The gateway does not incur that overhead on outgoing data 22 Pseudo Firewalls o Network Address Translation (NAT) o Translates “internal” IP addresses of one network to “external” IP addresses on another network o Static NAT • E.g., 12.1.8.4 <-> 162.145.14.3 o Pooled NAT (dynamical mapping to IP from a given pool of addresses) • E.g., 10.0.0.1-10.0.0.254 <-> 168.13.1.1-168.13.1.254 o Port-level NAT (dynamical mapping) • E.g., 10.0.0.1 <-> 168.13.1.1:1084 10.0.0.2 <-> 168.13.1.1:1085 o Not really a network firewall o Personal Firewalls o Control an access to a single device (not to a trusted network) o “The defense in depth” • Provides an additional level of protection 23 Firewall Architectures o Refers to a collection of firewall system components (hardware and software), connectivity between them and the distribution of functions between them o The very first step in designing a firewall architecture is to identify the boundaries between different security domains (security perimeter) o The most common security perimeter is the boundary between an organization’s LAN and the Internet o To make a network more secure, it is advisable to use different types of firewalls within the same firewall system o The most effective firewall architectures require that all the network traffic passes through them 24 Screening Router (Packet Filtering) Trusted LAN Internet Screening (Filtering) Router 25 Screening Router (Packet Filtering) o The most simple and basic architecture o A host on local network and a host on the Internet can communicate directly o The communication is restricted to the types that are allowed by the router (rules and filters) o Simple filtering based on the IP addresses and protocols o Best suited for small and simple networks o Disadvantages: o No logging capabilities o Packet filtering rules may be complex and hard to test o A single component of protection • If it fails, the security is compromised 26 Screened-host/Bastion-host Firewall System o Single-homed bastion host Trusted LAN Screening Router Internet Single-homed Gateway (Bastion host) 27 Screened-host/Bastion-host Firewall System o Consists of two systems: o A packet-filtering router o Single-homed bastion host • Bastion host servers as a platform for an application- or circuit-level gateway • Critical strong point in the network security o Typically, the router is configured such that o Only IP packets, originating from the Internet, destined to the bastion host are allowed in o Only IP packets from the bastion host are allowed out o A direct connection between an internal host and a host on the Internet is also possible, for certain services (e.g., Web server) o The bastion host performs o Authentication and application proxy functions o The system implements both packet-level and application-level filtering o Two points of defense (generally, an intruder would have to penetrate two separate systems) o Still, if the filtering router is compromised, traffic could flow directly through the router between the Internet and other hosts on the LAN 28 Dual-homed Gateway Architecture Trusted LAN Internet Screening Router Dual-homed Gateway (Bastion host) 29 Dual-homed Gateway Architecture o Consists of two systems: o A packet-filtering router o Dual-homed bastion host (application proxy, packet forwarding disabled) o Compared to the screened-host system, all the network traffic passes through the bastion host o A direct connection between an internal host and a host on the Internet is not possible o The bastion host performs o User authentication and application proxy functions o Two points of defense (an intruder must penetrate two separate systems) o If the filtering router is compromised, traffic cannot flow directly through the router between the Internet and other hosts on the LAN 30 Dual-homed Gateway Architecture contd. Demilitarized Zone (DMZ) Web Server Mail Server Trusted LAN Internet Screening Router Dual-homed Gateway (Bastion host) 31 Tri-homed Gateway Demilitarized Zone (DMZ) Web Server Mail Server Trusted LAN Internet Screening Router Tri-homed Gateway (Bastion host) 32 Screened-subnet Firewall Architecture Web Server Mail Server Trusted LAN DMZ Internet Screening Router Screening Router Single-homed Gateway (Bastion host) 33 Screened-subnet Firewall Architecture o Screened-subnet or DMZ typically created between two packet filtering routers o Creates and isolated subnetwork o The most secure architecture o Three levels of defense o The outside router advertises only the existence of the screened subnetwork to the Internet, the internal network is invisible to the Internet o The inside router advertises only the existence of the screened subnet to the internal network (no direct routes between the internal network and the Internet) 34 Literature o “Firewalls and Internet Security: Repelling the Wily Hacker.” Cheswick and Bellovin, 1994. o http://www.wilyhacker.com/1e o http://www2.rad.com/networks/2001/firewall/index.htm o http://www.more.net/technical/netserv/tcpip/firewalls o Any book on network security o And, of course, Google :) 35