* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Malwares – Types & Defense
Computer security wikipedia , lookup
Net neutrality law wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Wireless security wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
Computer network wikipedia , lookup
Internet protocol suite wikipedia , lookup
Airborne Networking wikipedia , lookup
Network tap wikipedia , lookup
Zero-configuration networking wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Deep packet inspection wikipedia , lookup
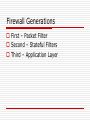
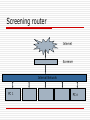
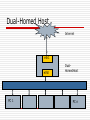
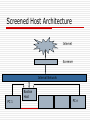
Firewall Raghunathan Srinivasan October 30, 2007 CSE 466/598 Computer Systems Security Before we start Something Interesting I found about XEN And something more: http://kerneltrap.org/OpenBSD/Virtualiz ation_Security A little bit on HW 2, problem 1 & 2 Not discussing problem 3 & 4 as they are fairly simple What are we protecting Data Private Data Secret Integrity Availability Resources Network resources Other computer resources Reputation Your reputation Means for Protection Anti-Virus Why doesn’t it work? Rather why is it ineffective Firewall Does it suffer from same problems as above What is a firewall Is it just a wall that we are burning? No, I guess bad joke Ok, it is a barrier between your computer and the outside world Rather protects the boundary of an intranet against the Internet Computer networks are designed to exchange data So why do we want to restrict data flow? Ideal World Everyone is good No attacker No one can compromise data No one will try to steal data No one will try to install backdoor No one …. (basically a really good world) Unfortunately, this can never exist Working World There are attackers People will try and steal data People will try opening ports on your machine for remote exploitation Individual users are not smart enough to configure network connections So we need some service that can at least differentiate between good & bad connections In practice may not be the case Firewall Your Network Outside Network Tasks of a Firewall Access control based on sender/receiver address or on addressed services Hiding Internal network Logging of traffic Implements Packet Filter & Proxy server 7 Layered OSI Application Layer Supports end – user processes, Telnet, FTP Presentation Layer Session Layer Transport Layer Flow Control Network Layer Switching, routing Data Link Layer Data encoded and coded into bits Physical Layer Packet Filter Analyzes network traffic and filters based on rules in layers 3 & 4 Typically can be Source / Dest Addr If firewall is combined with a router, it is called screening router Simple, Cheap Packet Filter Possible Principles Everything that is not explicitly allowed is denied Everything that is not explicitly denied is allowed Example Lame Example 1: Let your SMTP server be 149.169.0.1, and port be 40 Rule1 From (IP *), (port *) TO (149.169.0.1) (40) : DENY From (149.169.0.1), (40) TO (*) (*): Allow Rules are applied in order listed Proxy Server Controls access to a service Proxy is the only known computer to outside Internet Access control can be done based on user identity, content, used protocol Packet Filter vs Proxy Server PF Simple, Cheap Correctly specifying filters is error prone If you re-order rules, then policy may change Proxy User authentication possible Application Protocol control can be integrated Logging Circuit level proxies/Application level proxies AL proxies more expensive, but versatile Need one ALP for each application Circuit level Proxies hide network info apart from providing packet filter functionalities Firewall Generations First – Packet Filter Second – Stateful Filters Third – Application Layer First generation Just checks for the individual packets Which means most filtering is done based on a strict set of rules Lame example: Drop packets coming from a specific IP address The filter does not care whether the incoming/outgoing packet is part of an existing connection 2nd Gen - Stateful Filters Also called circuit level firewalls Do not examine each packet It maintains records of all connections passing through the firewall Can determine whether a packet is part of an existing connection or a new connection There are static rules that configure firewall behaviour 3rd generation Application layer firewall it can "understand" certain applications and protocols can detect whether an unwanted protocol is being sneaked through on a non-standard port whether a protocol is being abused in a known harmful way. Firewall Architectures Single Box Architecture Screened Host Architecture Screened Subnet Architectures Other Variations Single Box Architecture Screening Router Dual Homed Host Screening router Internet Screener Internal Network PC 1 PC n Features You can configure connections at one place So the firewall is installed in the router Can deny by port numbers/IP addr Not flexible Useful where network inside is considered secure Dual-Homed Host Internet eth1 eth0 DualHomedHost Internal Network PC 1 PC n Features The protected network cannot directly communicate to the Internet Applications should not be real time or business critical Traffic to Internet is small Users do not perform only Internet based jobs Packet filter & Proxy server together Bastion Host special purpose computer on a network specifically designed and configured to withstand attack Contains very few applications proxy server services the requests of its clients by forwarding requests to other servers Why? To reduce threats and vulnerabilities Screened Host Architecture Internet Screener Internal Network Bastion Host PC 1 PC n Features Bastion Host provides proxy Screening router provides packet filtering of incoming traffic Personal Firewall A software installed on a PC Part of OS to protect user machines Learning filter Annoying at times Honeypot Show a machine with weak security to outside world Monitor all the attacks that it experiences NAT - Network address translation Technique for transmitting/receiving network traffic through a router Re-writing of source/destination addresses Re-writing of TCP port number NAT is a popular way of dealing with IPv4 address shortage NAT enables multiple hosts on a private network to use a single public IP address NAT A host typically uses 192.168.x.x 10.x.x.x 172.16-31.x.x The router has a public address Example My router’s add 75-167-48-xxx My PC address 192.168.1.100 NAT When traffic moves from local network to Internet Router performs address change on source IP Router stores data about outgoing connection When reply returns to router, it uses stored data to forward packets to corresponding machine Drawbacks True end to end connectivity not there Cannot participate in some network protocols Services that require initiation from outside network cannot function Benefits NAT helps prevent many malicious attacks External network cannot initiate a connection I wont receive any malicious data unless my machine initiated it Can my machine initiate it? Practical solution to exhaustion of IPv4 address Can a firewall inside a computer be bypassed Yes It is just a service A program can disable it Bagle Bagz So it all boils down to Is my PC secure I believe that this problem is not in P A little refresher Digital signature Challenge Response – midterm The mid term problem 1: