* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Document
Survey
Document related concepts
Power over Ethernet wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Computer network wikipedia , lookup
Bus (computing) wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Network tap wikipedia , lookup
Low-voltage differential signaling wikipedia , lookup
MIL-STD-1553 wikipedia , lookup
Transcript
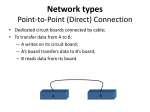
Data Communications & Networking CT101 - Computing Systems Contents • Data Transmission Circuits • Data Communications – Parallel Data Transmission – Serial Data Transmission • Asynchronous Serial Transmission • Synchronous Serial Transmission • Data Multiplexing & Modems • Networks & Topologies (bus, star and ring) • Cabling (coaxial, UTP, fiber optic) • Media Access Methods (CSMA/CD, CSMA/CA, Token Passing) • LAN Architectures (Ethernet, Token Ring) • Networking Devices • OSI Model. OSI layer functions. OSI versus TCP/IP Data Transmission • Data transmission is the transfer of data from point-to-point often represented as an electromagnetic signal over a physical point-to-point or point-to-multipoint communication channel • A communication channel refers to the medium used to convey information from a sender (or transmitter) to a receiver, and it can use fully or partially the medium. • Examples of channels: copper wires, optical fibbers or wireless communication channels. Data Communication Channels • • The following is a discussion on the THREE main types of transmission circuits (channels), simplex, half duplex and full duplex. Simplex – Data in a simplex channel is always one way. Simplex channels are not often used because it is not possible to send back error or control signals to the transmit end. An example of a simplex channel in a computer system is the interface between the keyboard and the computer, in that key codes need only be sent one way from the keyboard to the computer system. • Half Duplex – A half duplex channel can send and receive, but not at the same time. Its like a one-lane bridge where two way traffic must give way in order to cross. Only one end transmits at a time, the other end receives. • Full Duplex – Data can travel in both directions simultaneously. There is no need to switch from transmit to receive mode like in half duplex. Its like a two lane bridge on a two-lane highway. Parallel and Serial Data • Parallel transmission (e.g. 8 bits) – Each bit uses a separate wire – To transfer data on a parallel link, a separate line is used as a clock signal. This serves to inform the receiver when data is available. In addition, another line may be used by the receiver to inform the sender that the data has been used, and its ready for the next data. Parallel and Serial Data • Serial (e.g. 8 bits) – Each bit is sent over a single wire, one after the other – Usually no signal lines are used to convey clock (timing information) – There are two types of serial transmission, essentially having to do with how the clock is embedded into the serial data • Asynchronous serial transmission • Synchronous serial transmission • If no clock information was sent, the receiver would misinterpret the arriving data (due to bits being lost, going too slow). • Parallel transmission is obviously faster, in that all bits are sent at the same time, whereas serial transmission is slower, because only one bit can be sent at a time. Parallel transmission is very costly for anything except short links. • • • • • Asynchronous Serial Transmission (RS232 Example) Because no signal lines are used to convey clock (timing) information, this method groups data together into a sequence of bits (five to eight), then prefixes them with a start bit and a stop bit. This is the method most widely used for PC or simple terminal serial communications. In asynchronous serial communication, the electrical interface is held in the mark position between characters. The start of transmission of a character is signaled by a drop in signal level to the space level. At this point, the receiver starts its clock. After one bit time (the start bit) come 8 bits of true data followed by one or more stop bits at the mark level. The receiver tries to sample the signal in the middle of each bit time. The byte will be read correctly if the line is still in the intended state when the last stop bit is read. Thus the transmitter and receiver only have to have approximately the same clock rate. A little arithmetic will show that for a 10 bit sequence, the last bit will be interpreted correctly even if the sender and receiver clocks differ by as much as 5%. It is relatively simple, and therefore inexpensive. However, it has a high overhead, in that each byte carries at least two extra bits: a 20% loss of line bandwidth. Synchronous Serial Transmission (PS2 Example) • • • The PS/2 mouse and keyboard implement a bidirectional synchronous serial protocol. The bus is "idle" when both lines are high (open-collector). This is the only state where the keyboard/mouse is allowed begin transmitting data. The host has ultimate control over the bus and may inhibit communication at any time by pulling the Clock line low. The device (slave) always generates the clock signal. If the host wants to send data, it must first inhibit communication from the device by pulling Clock low. The host then pulls Data low and releases Clock. This is the "Request-to-Send" state and signals the device to start generating clock pulses. – Summary: Bus States Data = high, Clock = high: Idle state. Data = high, Clock = low: Communication Inhibited. Data = low, Clock = high: Host Request-to-Send Data is transmited 1 byte at a time: •1 start bit. This is always 0. •8 data bits, least significant bit first. •1 parity bit (odd parity - The number of 1's in the data bits plus the parity bit always add up to an odd number. This is used for error detection.). •1 stop bit. This is always 1. •1 acknowledge bit (host-to-device communication only) Serial Communication Name Sync Type /Async Duplex Max RS-232 async peer RS-422 async multi-drop Max devices speed (Kbps) Max Pin distance count (not including ground) (feet) full 2 115.2 30 2 (or 4 with HW handshake) half 10 10000 4,000 1 (unidirectional only, additional pins for each bidirectional comm.) RS-485 async multi-point half 32 10000 4,000 2 I2C sync multimaster half Limitation based on bus capacitance and bit rate 3400 <10 2 SPI sync multimaster full Limitation based on bus capacitance and bit rate >1000 <10 3+1(Additional pins needed Limitation based on bus capacitance and bit rate >625 Limitation based on bus capacitance and bit rate 16 Microwire sync 1-Wire async master/slave full master/slave half for every slave if slave count is more than one) <10 3+1(Additional pins needed for every slave if slave count is more than one) 1,000 1 Data Communication Terminology • Channel – A channel is a portion of the communications medium allocated to the sender and receiver for conveying information between them. The communications medium is often subdivided into a number of separate paths, each of which is used by a sender and receiver for communication purposes. • Baud Rate – Baud rate is the same as symbol rate and is a measure of the number of line changes which occur every second. Each symbol can represent or convey one (binary encoded signal) or several bits of data. For a binary signal of 20Hz, this is equivalent to 20 baud (there are 20 changes per second). • Bits Per Second – This is an expression of the number of data bits per second. Where a binary signal is being used, this is the same as the baud rate. When the signal is changed to another form, it will not be equal to the baud rate, as each line change can represent more than one bit (either two or four bits). • Bandwidth – Bandwidth is the frequency range of a channel, measured as the difference between the highest and lowest frequencies that the channel supports. The maximum transmission speed is dependant upon the available bandwidth. The larger the bandwidth, the higher the transmission speed. Data Multiplexing • A multiplexer is a device which shares a communication link between a number of devices (users). • Rather than provide a separate circuit for each device, the multiplexer combines each low speed circuit onto a single high speed link. The cost of the single high speed link is less than the required number of low speed links. • It does this by time or frequency division. Time Division Multiplexing • In time division, the communications link is subdivided in terms of time. • Each sub-circuit is given the channel for a limited amount of time, before it is switched over to the next user, and so on • In the picture bellow it can be seen that each sub-channel occupies the entire bandwidth of the channel, but only for a portion of the time Frequency Division Multiplexing • In frequency division multiplexing, each sub-channel is separated by frequency (each sub-channel is allocated part of the bandwidth of the main channel) • The speed or bandwidth of the main link is the sum of the individual sub-channel speeds or bandwidth. Modems • Modems are devices which allow digital data signals to be transmitted across an analogue link. • Modem stands for modulator/demodulator. A modem changes the digital signal to an analogue frequency, and sends this tone across the analogue link. At the other end, another modem receives the signal and converts it back to digital. Modulation Techniques • Modulation techniques are methods used to encode digital information in an analogue world. • There are three basic modulation techniques – AM (amplitude modulation) – FM (frequency modulation) – PM (phase modulation) • All 3 modulation techniques employ a carrier signal. A carrier signal is a single frequency that is used to carry the intelligence (data). – For digital, the intelligence is either a 1 or 0. – When we modulate the carrier , we are changing its characteristics to correspond to either a 1 or 0. Amplitude Modulation • Modifies the amplitude of the carrier to represent 1s or 0s – a 1 is represented by the presence of the carrier for a predefined period of 3 cycles of carrier. – Absence or no carrier indicates a 0 • Pros – Simple to design and implement • Cons – Noise spikes on transmission medium interfere with the carrier signal. – Loss of connection is read as 0s. Frequency Modulation • Modifies the frequency of the carrier to represent the 1s or 0s. – a 0 is represented by the original carrier frequency – a 1 by a much higher frequency ( the cycles are spaced closer together) • Pros – Immunity to noise on transmission medium. – Always a signal present. Loss of signal easily detected • Cons – Requires 2 frequencies – Detection circuit needs to recognize both frequencies when signal is lost. Phase Modulation • Phase Modulation modifies the phase of the carrier to represent a 1 or 0. – The carrier phase is switched at every occurrence of a 1 bit but remains unaffected for a 0 bit. – The phase of the signal is measured relative to the phase of the preceding bit. The bits are timed to coincide with a specific number of carrier cycles (3 in this example = 1 bit) • Pros – Only 1 frequency used – Easy to detect loss of carrier • Cons – Complex circuitry required to generate and detect phase changes What is a network • A network as a "group of computers and associated devices that are connected by communications facilities." • A network provides two principle benefits: the ability to communicate and the ability to share. – A network supports communication among users in ways that other media cannot. – Sharing involves not only information (database records, e-mail, graphics, etc.), but also resources (applications, printers, modems, disk space, scanners, etc.) Through its ability to share, a network promotes collaboration • A network can consist of two computers connected together on a desk or it can consist of many Local Area Networks (LANs) connected together to form a Wide Area Network (WAN) across a continent. Network Classifications • Scope – Local area network (LAN) – Metropolitan area (MAN) – Wide area network (WAN) • Ownership – Closed versus open • Topology (configuration) – Bus (Ethernet) – Star (Wireless networks with central Access Point) – Ring Network Topologies • A topology refers to the manner in which the cable is run to individual workstations on the network. – the configurations formed by the connections between devices on a local area network (LAN) or between two or more LANs • There are three basic network topologies (not counting variations thereon): the bus, the star, and the ring. • It is important to make a distinction between a topology and an architecture. – A topology is concerned with the physical arrangement of the network components. – In contrast, an architecture addresses the components themselves and how a system is structured (cable access methods, lower level protocols, topology, etc.). An example of an architecture is 10baseT Ethernet which typically uses the star topology. Bus Topology • A bus topology connects each computer (node) to a single segment trunk. – A ‘trunk’ is a communication line, typically coax cable, that is referred to as the ‘bus.’ The signal travels from one end of the bus to the other. – A terminator is required at each end to absorb the signal so it does not reflect back across the bus. • In a bus topology, signals are broadcast to all stations. Each computer checks the address on the signal (data frame) as it passes along the bus. If the signal’s address matches that of the computer, the computer processes the signal. If the address doesn’t match, the computer takes no action and the signal travels on down the bus. • Only one computer can ‘talk’ on a network at a time. A media access method (protocol) called CSMA/CD is used to handle the collisions that occur when two signals are placed on the wire at the same time. • The bus topology is passive. In other words, the computers on the bus simply ‘listen’ for a signal; they are not responsible for moving the signal along. • A bus topology is normally implemented with coaxial cable. Bus Topology • Advantages of bus topology: – – – – Easy to implement and extend Well suited for temporary networks that must be set up in a hurry Typically the cheapest topology to implement Failure of one station does not affect others • Disadvantages of bus topology: – – – – – Difficult to administer/troubleshoot Limited cable length and number of stations A cable break can disable the entire network; no redundancy Maintenance costs may be higher in the long run Performance degrades as additional computers are added Star Topology • All of the stations in a star topology are connected to a central unit called a hub. – The hub offers a common connection for all stations on the network. Each station has its own direct cable connection to the hub. In most cases, this means more cable is required than for a bus topology. However, this makes adding or moving computers a relatively easy task; simply plug them into a cable outlet on the wall. • If a cable is cut, it only affects the computer that was attached to it. This eliminates the single point of failure problem associated with the bus topology. (Unless, of course, the hub itself goes down.) • Star topologies are normally implemented using twisted pair cable, specifically unshielded twisted pair (UTP). The star topology is probably the most common form of network topology currently in use. Star Topology • Advantages of star topology: – Easy to add new stations – Easy to monitor and troubleshoot – Can accommodate different wiring • Disadvantages of star topology: – Failure of hub cripples attached stations – More cable required (more expensive to wire a building for networking) Ring Topology • • • • A ring topology consists of a set of stations connected serially by cable. In other words, it’s a circle or ring of computers. There are no terminated ends to the cable; the signal travels around the circle in a clockwise (or anticlockwise) direction. Note that while this topology functions logically as ring, it is physically wired as a star. The central connector is not called a hub but a Multistation Access Unit or MAU. (Don’t confuse a Token Ring MAU with a ‘Media Adapter Unit’ which is actually a transceiver.) Under the ring concept, a signal is transferred sequentially via a "token" from one station to the next. When a station wants to transmit, it "grabs" the token, attaches data and an address to it, and then sends it around the ring. The token travels along the ring until it reaches the destination address. The receiving computer acknowledges receipt with a return message to the sender. The sender then releases the token for use by another computer. Each station on the ring has equal access but only one station can talk at a time. Ring Topology • In contrast to the ‘passive’ topology of the bus, the ring employs an ‘active’ topology. Each station repeats or ’boosts’ the signal before passing it on to the next station. • Rings are normally implemented using twisted pair or fiber-optic cable • Advantages of ring topology: – Growth of system has minimal impact on performance – All stations have equal access • Disadvantages of ring topology: – Most expensive topology – Failure of one computer may impact others – Complex Choosing a Topology • The following factors should be considered when choosing a topology: – – – – – – Installation Maintenance and troubleshooting Expected growth Distances Infrastructure Existing network • As a general rule, a bus topology is the cheapest to install, but may be more expensive to maintain because it does not provide for redundancy. • Various topologies can be mixed on the same network. • One very common example is a large Ethernet network with multiple hubs. Usually the hubs are located on different floors in a building or perhaps outside in another building. Each hub is wired in the typical star configuration. However, the hubs are connected together along a bus, typically referred to as a ‘backbone.’ • The backbone between hubs might consist of fiber optic cable while the workstations are wired to each individual hub with UTP (unshielded twisted pair) cable. Cabling • Coaxial Cable – Thinnet looks like regular TV cable. It is about 1/4 inch in diameter and is very flexible and easy to work with. – Thicknet is about 1/2 inch in diameter and not very flexible. Thicknet is older and not very common anymore except as a backbone within and between buildings. Coax transmits at 10 Mbps.. • Twisted Pair. Twisted pair looks like telephone wire and consists of insulated strands of copper wire twisted together. There are two versions of twisted pair cable: – Shielded Twisted Pair (STP). STP is commonly used in Token Ring networks – Unshielded Twisted Pair (UTP). UTP is used in Ethernet networks. Transmission rates vary between 10-100-1000-10000 Mbps. • Fiber-Optic Cable. Fiber-optic cable consists of a thin cylinder of glass surrounded by glass cladding, encased in protective outer sheath. Fiber-optic cable is very fast (over 1Gbps). It can transmit over long distances (2 km +) but is expensive. Cabling • Top: Unshielded Twisted Pair and Shielded Twisted Pair Cable • Bottom: Coaxial and Optical Fiber Cable Media Access Methods • A media access method refers to the manner in which a computer gains and controls access to the network’s physical medium (e.g., cable). • Common media access methods include the following: – CSMA/CD – CSMA/CA – Token Passing • One of the primary concerns with media access is how to prevent packets from colliding when two or more computers try to transmit simultaneously. Each of the methods listed above takes a different approach to this problem. • Data transmitted over a network is sent one bit at a time. A bit is either a 1 or a 0 represented by a voltage change (on or off) or a light pulse. If two stations are transmitting at the same time, it is possible that the signals may overlap, resulting in garbled data. Such overlapping is referred to as a "collision." CSMA/CD • CSMA/CD stands for Carrier-Sense Multiple Access with Collision Detection. It is a media access method which means it defines how the network places data on the cable and how it takes it off. • CSMA/CD specifies how bus topologies such as Ethernet handle transmission collisions. A collision occurs when two or more computers transmit signals at the same time. – "Carrier Sense" means that each station on the LAN continually listens to (tests) the cable for the presence of a signal prior to transmitting. – "Multiple Access" means that there are many computers attempting to transmit and compete for the opportunity to send data (i.e., they are in contention). – "Collision Detection" means that when a collision is detected, the stations will stop transmitting and wait a random length of time before retransmitting. • CSMA/CD works best in an environment where relatively fewer, longer data frames are transmitted. This is in contrast to token passing which works best with a relatively large amount of short data frames. • Because CSMA/CD works to control or manage collisions rather than prevent them, network performance can be degraded with heavy traffic. The greater the traffic, the greater the number of collisions and retransmissions. • CSMA/CD is used on Ethernet networks. CSMA/CD Operation • In its most simple form it operates as follows: – A station that wishes to transmit on the network checks to see if the cable is free. – If the cable is free, the station starts transmitting. – However, another station may have detected a free cable at the same instant and also start transmitting. The result is a "collision." – Once the collision is detected, all stations immediately stop transmitting. – Stations then wait a random length of time before checking the cable and then retransmit CSMA/CA • CSMA/CA stands for Carrier-Sense Multiple Access with Collision Avoidance and is a media access method very similar to CSMA/CD. • The difference is that the CD (collision detection) is changed to CA (collision avoidance). Instead of detecting and reacting to collisions, CSMA/CA tries to avoid them by having each computer signal its intention to transmit before actually transmitting. In effect, the transmitting computer gives a 'heads up' prior to transmitting. • Although CSMA/CA can prevent collisions, it comes with a cost in the form of the additional overhead incurred by having each workstation broadcast it's intention prior to transmitting. Thus, CSMA/CA is slower than CSMA/CD. • CSMA/CA is used on Apple networks and on WiFi (IEEE 802.11) networks. The hidden terminal problem Token Passing • Token passing is a media access method by which collisions are prevented. • Collisions are eliminated under token passing because only a computer that possesses a free token (a small data frame) is allowed to transmit. The token passing method also allows different priorities to be assigned to different stations on the ring. Transmissions from a stations with higher priority take precedence over stations with lower priority. • Token passing works best in an environment where a relatively large number of shorter data frames are being transmitted. (As opposed to CSMA/CD which works best in an environment where relatively fewer, longer data frames are being transmitted.) • Token passing is used on Token Ring networks Token Passing Operation • In its most simple form it operates as follows: – A station that wishes to transmit on the network waits until it will receive a free token. – The sending station transmits its data with the token. – The data travels to the recipient without stopping at other stations (it is just relayed). – The receiving station receives the data and returns the token to the sender as an acknowledgment. – The sender receives acknowledgment and releases the token to next station. – The token continues being passed along the ring until it is “seized" by the next station that wants to transmit. LAN Architectures • Network architecture refers to the manner in which the hardware and software is structured. The architecture includes the cable access method (transmission), topology, and lower level protocols. • The most common type of LAN architecture is Ethernet. Token Ring was also used in the past. • These architectures are sometimes referred to as "lower-level protocols" because they represent the specifications for the IEEE802 model which encompasses the physical (1st) and data link (2nd) layers of the OSI model (to be discussed latter) Ethernet • Ethernet is a popular, relatively inexpensive, easy-to-install LAN architecture with the following characteristics: – Uses the CSMA/CD media access control. – Data transmission normally occurs at 100 Mbps (10Mbps in the early forms and 10Gbps in the most recent forms). – Typically implemented in a star topology (early versions used bus topology as well). – Ethernet LANs are normally distinguished by the type of cable they use Twisted Pair (Thinnet or Thicknet were also used in the past). • The Ethernet architecture conforms to most but not all of the IEEE 802.3 specification (the physical layers are identical but the MAC layers are somewhat different). • An Ethernet LAN is often described in terms of three parameters: transmission rate, transmission type, and segment distance or cable type. – "100baseT" means: • 100 - transmission rate or through put of 100Mbps • base - transmission type is baseband rather than broadband network (i.e., the signal is placed directly on the cable, one signal at a time) • T – the cable type (e.g. Twisted pair) • Few types of Ethernet: 10Base2, 10Base5, 10BaseT and 10BaseF, 100BaseT, 100BaseF, etc.. Token Ring • Token ring is a relatively expensive LAN architecture that was strongly influenced by IBM. It is very stable and can be expanded without a significant degradation in network performance. • Token ring uses the token passing media access control. Data transmission normally occurs at 4 or 16 Mbps depending on the cable. • Token ring is normally implemented in a logical ring/physical star topology with a MAU (Multistation Access Unit) as the hub. The maximum number of stations on one ring is 260 for shielded twisted pair and 72 for unshielded twisted pair (UTP). There can be up to 33 MAUs per ring. • Token Ring LANs normally use shielded twisted pair (STP) but may also use unshielded twisted pair (UTP) or fiber-optic cable. The maximum distance to the MAU from the workstation depends on the cable and varies from 45 meters for UTP to 100 meters for STP. • The Token Ring architecture conforms generally to the IEEE’s 802.5 specification Ethernet vs. Token Ring • Ethernet is generally less expensive and easier to install than Token Ring. • Token Ring is generally more secure and more stable than Ethernet, but not used anymore in typical LAN configurations. • It is usually more difficult to add more computers on a Token Ring LAN than it is to an Ethernet LAN. However, as additional computers are added, performance degradation will be less pronounced on the Token Ring LAN than it will be on the Ethernet LAN. • Ethernet uses CSMA/CD media access control and Token Ring uses token passing. This makes Ethernet better suited in a situation where there are a large number of computers sending fewer, larger data frames. Token Ring is better suited for small to medium size LANs sending many, Connecting Networks • Repeater: Extends a network • Bridge: Connects two compatible networks, doesn’t necessarily pass all the messages across the connection • Switch: Connect several compatible networks, allowing it to connect several busses rather than two. 4-42 Building a large bus network from smaller ones Connecting Networks • When networks are connected via repeaters, bridges or switches, the result is a single large network. • The entire system operates in the same way as the original smaller networks • Sometimes the networks to be connected have incompatible characteristics (e.g. WiFi network to be connected with Ethernet network, etc..). • When building networks of networks, the system is known as internet (note the small “i”, term that is distinct from the Internet – which refers to a particular world wide internet). • Router: Connects two incompatible networks resulting in a network of networks - internet Routers connecting two WiFi networks and an Ethernet network to form an internet Routers and internet addressing • Routers purpose is to route (forward messages) in their proper directions. • The forwarding process is based on an internet wide addressing system which all the machines in the internet (including the machines in the original networks as well as the routers) are assigned unique addresses. – Thus each machine in an internet has two addresses: its original local address within its own network and the internet address • A machine wanting to send a message to a machine in a distant network, it will attach the internet address of the destination and will direct the message to its local router. From there it is forwarded to the proper direction (based on a forwarding table maintained by the router). Client and Server • The terms "client" and "server" are used to describe individual computers that are part of a network where computing resources and workload are shared. • A server is a computer that makes its resources available to the network and responds to the commands of a client. The server’s shared resources can be files (a file server); printers (a print server); processing power (an application server); etc… • A client is a computer that uses the resources made available by a server. The client must have sufficient processing power on its own to run applications that interact with the resources on the server. • It is possible, and quite common, for an individual computer to function as both a client and a server. – For example, if Bill queries a SQL Server database from his workstation for the data he needs to create an Excel spreadsheet, then his workstation is functioning as a client. However, if Sue then connects to Bill’s workstation from her computer and copies the spreadsheet, then Bill’s workstation is functioning as a server. ISO/OSI Model • The International Standards Organization (ISO) Open Systems Interconnect (OSI) is a standard set of rules describing the transfer of data between each layer in a network operating system. Each layer has a specific function (i.e. the physical layer deals with the electrical and cable specifications) • The OSI Model clearly defines the interfaces between each layer. This allows different network operating systems and protocols to work together by having each manufacturer adhere to the standard interfaces. The application of the ISO OSI model has allowed the modern networks that exist today. There are seven layers in the OSI model. OSI Model • The Physical Layer – Establishes the physical characteristics of the network (e.g., the type of cable, connectors, length of cable, etc.) – Defines the electrical characteristics of the signals used to transmit the data (e.g. signal voltage swing, duration of voltages, etc.) – Transmits the binary data (bits) as electrical or optical signals depending on the medium. • The Data Link Layer – Defines how the signal will be placed on or taken off the NIC. The data frames are broken down into individual bits that can be translated into electric signals and sent over the network. On the receiving side, the bits are reassembled into frames for processing by upper levels. – Error detection and correction is also performed at the data link layer. If an acknowledgement is expected and not received, the frame will be resent. Corrupt data is also identified at the data link layer. – Because the Data-Link Layer is very complex, it is sometimes divided into sublayers (as defined by the IEEE 802 model). The lower sublayer provides network access. The upper sublayer is concerned with sending and receiving packets and error checking. OSI Model • The Network Layer – Primarily concerned with addressing and routing. Logical addresses (e.g., an IP address) are translated into physical addresses (i.e., the MAC address) for transmission at the network layer. On the receiving side, the translation process is reversed. – It is at the network layer where the route from the source to destination computer is determined. Routes are determined based on packet addresses and network conditions. Traffic control measures are also implemented at the network layer. • The Transport Layer – On the sending side, messages are packaged for efficient transmission and assigned a tracking number so they can be reassembled in proper order. On the receiving side, the packets are reassembled, checked for errors and acknowledged. – Performs error handling in that it ensures all data is received in the proper sequence and without errors. If there are errors, the data is retransmitted. OSI Model • The Session Layer – Is responsible for establishing, maintaining, and terminating a connection called a 'session'. – A session is an exchange of messages between computers (a dialog). Managing the session involves synchronization of user tasks and dialog control (e.g., who transmits and for how long). Synchronization involves the use of checkpoints in the data stream. In the event of a failure, only the data from the last checkpoint has to be resent. – Logon, name recognition and security functions take place at the Session Layer. • The Presentation Layer – It is responsible for data translation (formatting), compression, and encryption. – The Presentation Layer is primarily concerned with translation; interpreting and converting the data from various formats. For example, EBCIDIC characters might be converted into ASCII. It is also where data is compressed for transmission and uncompressed on receipt. Encryption techniques are implemented at the Presentation Layer. – The redirector operates at the presentation layer by redirecting I/O operations across the network. • The Application Layer – Provides the operating system with direct access to network services. – It serves as the interface between the user and the network by providing services that directly support user applications. OSI Model OSI Model • Each layer may add a Header and a Trailer to its Data (which consists of the next higher layer's Header, Trailer and Data as it moves through the layers). The Headers contain information that specifically addresses layer-to-layer communication. For example, the Transport Header (TH) contains information that only the Transport layer sees. All other layers below the Transport layer pass the Transport Header as part of their Data. OSI vs. TCP/IP References • Andrew S. Tanenbaum – Computer Networks, ISBN: 0-13066102-3 • J Glenn Brookshear “Computer Science – An Overview”, ISBN: 0-321-54428-5 • Eugene Blanchard “Introduction to Networking and Data Communications”