* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Slide 1
Survey
Document related concepts
Policies promoting wireless broadband in the United States wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Net neutrality law wikipedia , lookup
Wireless security wikipedia , lookup
Distributed firewall wikipedia , lookup
Network tap wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Airborne Networking wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Computer network wikipedia , lookup
Internet protocol suite wikipedia , lookup
Deep packet inspection wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Transcript
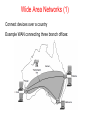
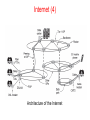
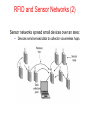
COM320 Computer Networks and Operating Systems Kevin Curran Before we start… Main Books: Tanenbaum, A. (2010) Computer Networks (5th edition), Prentice Hall, ISBN: 978-0132126953 Stallings, W. (2008) Operating Systems, internals and design principles. Upper Saddle River, New Jersey: Pearson/Prentice Hall (6th ed.). Before we start… 2 important Links…… if you missed class, please ask a colleague….. Labs & Notes • Main Page - http://scisweb.ulster.ac.uk/~kevin/com320/index.htm • Notes - http://scisweb.ulster.ac.uk/~kevin/com320/notes.htm • Labs - http://scisweb.ulster.ac.uk/~kevin/com320/labs.htm • Assignments – 2 class tests • Attendance & what not to do when absent • Structure of Labs Introduction Chapter 1 • • • • • • • Uses of Computer Networks Network Hardware Network Software Reference Models Example Networks Network Standardization Metric Units Uses of Computer Networks Computer networks are collections of autonomous computers, e.g., the Internet They have many uses: • Business Applications » • Home Applications » • Mobile Users » These uses raise: • Social Issues » This text covers networks for all of these uses Business Applications Companies use networks and computers for resource sharing with the client-server model: request response Other popular uses are communication, e.g., email, VoIP, and e-commerce Home Applications Homes contain many networked devices, e.g., computers, TVs, connected to the Internet by cable, DSL, wireless, etc. Home users communicate, e.g., social networks, consume content, e.g., video, and transact, e.g., auctions Some application use the peer-to-peer model in which there are no fixed clients and servers: Mobile Users Tablets, laptops, and smart phones are popular devices; WiFi hotspots and 3G cellular provide wireless connectivity. Mobile users communicate, e.g., voice and texts, consume content, e.g., video and Web, and use sensors, e.g., GPS. Wireless and mobile are related but different: Social Issues • • • • • Network neutrality – no network restrictions Content ownership, e.g., DMCA takedowns Anonymity and censorship Privacy, e.g., Web tracking and profiling Theft, e.g., botnets and phishing Network Neutrality Some network operators block content for their own reasons. Opponents of this practice argue that peer-to-peer and other content should be treated in the same way because they are all just bits to the network. This argument for communications that are not differentiated by their content or source or who is providing the content is known as Network Neutrality Network Hardware Networks can be classified by their scale: Scale Type Vicinity PAN (Personal Area Network) » Building LAN (Local Area Network) » City MAN (Metropolitan Area Network) » Country WAN (Wide Area Network) » Planet The Internet (network of all networks) Personal Area Network Connect devices over the range of a person Example of a Bluetooth (wireless) PAN: Local Area Networks Connect devices in a home or office building Called enterprise network in a company Most use Copper Wiring but some use Optical Wireless LAN with 802.11 Wired LAN with switched Ethernet Metropolitan Area Networks Connect devices over a metropolitan area Example MAN based on cable TV: Wide Area Networks (1) Connect devices over a country Example WAN connecting three branch offices: Wide Area Networks (2) An ISP (Internet Service Provider) network is also a WAN. Customers buy connectivity from the ISP to use it. Wide Area Networks (3) A VPN (Virtual Private Network) is a WAN built from virtual links that run on top of the Internet. Network Software • • • • • Protocol layers » Design issues for the layers » Connection-oriented vs. connectionless service » Service primitives » Relationship of services to protocols » Protocol Layers (1) Protocol layering is the main structuring method used to divide up network functionality. • Each protocol instance talks virtually to its peer • Each layer communicates only by using the one below • Lower layer services are accessed by an interface • At bottom, messages are carried by the medium Protocol Layers (2) Example: the philosopher-translator-secretary architecture Each protocol at different layers serves a different purpose Protocol Layers (3) Each lower layer adds its own header (with control information) to the message to transmit and removes it on receive Layers may also split and join messages, etc. Design Issues for the Layers Each layer solves a particular problem but must include mechanisms to address a set of recurring design issues Issue Example mechanisms at different layers Reliability despite failures Codes for error detection/correction (§3.2, 3.3) Routing around failures (§5.2) Network growth and evolution Addressing (§5.6) and naming (§7.1) Protocol layering (§1.3) Allocation of resources like bandwidth Multiple access (§4.2) Congestion control (§5.3, 6.3) Security against various threats Confidentiality of messages (§8.2, 8.6) Authentication of communicating parties (§8.7) Connection-Oriented vs. Connectionless Service provided by a layer may be kinds of either: • Connection-oriented, must be set up for ongoing use (and torn down after use), e.g., phone call • Connectionless, messages are handled separately, e.g., postal delivery Multiplexing Many network designs share network bandwidth dynamically, according to the short-term needs of hosts, rather than by giving each host a fixed fraction of the band-width that it may or may not use. This design is called statistical multiplexing. Statistical TDM Switching Store & Forward Switching - Used on a packet network, when the intermediate nodes receive a message in full before sending it on to the next node, Cut-through switching is a method for packet switching systems, wherein the switch starts forwarding a frame (or packet) before the whole frame has been received, normally as soon as the destination address is processed. Compared to store and forward, this technique reduces latency through the switch, but decreases reliability; corrupted frames are potentially forwarded. Adaptive Switching dynamically selects between cutthrough and store and forward behaviors based on current network conditions. How do loss and delay occur? packets queue in router buffers packet arrival rate to link exceeds output link capacity packets queue, wait for turn packet being transmitted (delay) A B packets queueing (delay) free (available) buffers: arriving packets dropped (loss) if no free buffers Four sources of packet delay transmission A propagation B nodal processing queueing dnodal = dproc + dqueue + dtrans + dprop dproc: nodal processing check bit errors determine output link typically < msec dqueue: queueing delay time waiting at output link for transmission depends on congestion level of router Four sources of packet delay transmission A propagation B nodal processing queueing dnodal = dproc + dqueue + dtrans + dprop dtrans: transmission delay: L: packet length (bits) R: link bandwidth (bps) dtrans = L/R dtrans and dprop very different dprop: propagation delay: d: length of physical link s: propagation speed in medium (~2x108 m/sec) dprop = d/s Caravan analogy 100 km ten-car caravan toll booth cars “propagate” at 100 km/hr toll booth takes 12 sec to service car (transmission time) car~bit; Q: caravan ~ packet How long until caravan is lined up before 2nd toll booth? 100 km toll booth time to “push” entire caravan through toll booth onto highway = 12*10 = 120 sec time for last car to propagate from 1st to 2nd toll both: 100km/(100km/hr)= 1 hr A: 62 minutes Caravan analogy (more) 100 km ten-car caravan cars toll toll booth 100 km toll booth now “propagate” at 1000 km/hr booth now takes 1 min to service a car Q: Will cars arrive to 2nd booth before all cars serviced at 1st booth? A: Yes! After 7 min, 1st car arrives at second booth; three cars still at 1st booth. 1st bit of packet can arrive at 2nd router before packet is fully transmitted at 1st router! (see Ethernet applet at AWL Web site Service Primitives (1) A service is provided to the layer above as primitives Hypothetical example of service primitives that may provide a reliable byte stream (connection-oriented) service: Service Primitives (2) Hypothetical example of how these primitives may be used for a client-server interaction Server Client LISTEN (0) CONNECT (1) Connect request Accept response SEND (3) RECEIVE ACCEPT (2) RECEIVE Request for data SEND (4) Reply DISCONNECT (5) Disconnect DISCONNECT (6) Disconnect Relationship of Services to Protocols Recap: • A layer provides a service to the one above [vertical] • A layer talks to its peer using a protocol [horizontal] Relationship of Services to Protocols Services and protocols are distinct concepts. A service is a set of primitives (operations)that a layer provides to the layer above it. The service defines what operations the layer is prepared to perform on behalf of its users, but it says nothing at all about how these operations are implemented. Reference Models Reference models describe the layers in a network architecture • • • • OSI reference model » TCP/IP reference model » Model used for this text » Critique of OSI and TCP/IP » OSI Reference Model A principled, international standard, seven layer model to connect different systems – Provides functions needed by users – Converts different representations – Manages task dialogs – Provides end-to-end delivery – Sends packets over multiple links – Sends frames of information – Sends bits as signals TCP/IP Reference Model A four layer model derived from experimentation; omits some OSI layers and uses the IP as the network layer. IP is the “narrow waist” of the Internet Protocols are shown in their respective layers Model Used in this Book It is based on the TCP/IP model but we call out the physical layer and look beyond Internet protocols. Critique of OSI & TCP/IP OSI: + Very influential model with clear concepts − Models, protocols and adoption all bogged down by politics and complexity TCP/IP: + Very successful protocols that worked well and thrived − Weak model derived after the fact from protocols Model Used in this Book It is based on the TCP/IP model but we call out the physical layer and look beyond Internet protocols. Example Networks • • • • The Internet » 3G mobile phone networks » Wireless LANs » RFID and sensor networks » Internet (1) Before the Internet was the ARPANET, a decentralized, packet-switched network based on Baran’s ideas. Nodes are IMPs, or early routers, linked to hosts 56 kbps links ARPANET topology in Sept 1972. Internet (2) The early Internet used NSFNET (1985-1995) as its backbone; universities connected to get on the Internet T1 links (1.5 Mbps) NSFNET topology in 1988 Internet (3) The modern Internet is more complex: • ISP networks serve as the Internet backbone • ISPs connect or peer to exchange traffic at IXPs • Within each network routers switch packets • Between networks, traffic exchange is set by business agreements • Customers connect at the edge by many means − Cable, DSL, Fiber-to-the-Home, 3G/4G wireless, dialup • • • Data centers concentrate many servers (“the cloud”) Most traffic is content from data centers (esp. video) The architecture continues to evolve Internet (4) Architecture of the Internet Internet (5) Internet Service Provider (ISP) networks may be regional, national, or international in scope. If a packet is destined for a host served directly by the ISP, that packet is routed over the backbone and delivered to the host. Otherwise, it must be handed over to another ISP. ISPs connect their networks to exchange traffic at IXPs(Internet eXchange Points). 3G Mobile Phone Networks (1) 3G network is based on spatial cells; each cell provides wireless service to mobiles within it via a base station 3G Mobile Phone Networks (2) Base stations connect to the core network to find other mobiles and send data to the phone network and Internet 3G Mobile Phone Networks (3) As mobiles move, base stations hand them off from one cell to the next, and the network tracks their location Handover Wireless LANs (1) In 802.11, clients communicate via an AP (Access Point) that is wired to the rest of the network. Wireless LANs (2) Signals in the 2.4GHz ISM band vary in strength due to many effects, such as multipath fading due to reflections − requires complex transmission schemes, e.g., OFDM Wireless LANs (3) Radio broadcasts interfere with each other, and radio ranges may incompletely overlap − CSMA (Carrier Sense Multiple Access) designs are used RFID and Sensor Networks (1) Passive UHF RFID networks everyday objects: − Tags (stickers with not even a battery) are placed on objects − Readers send signals that the tags reflect to communicate RFID and Sensor Networks (2) Sensor networks spread small devices over an area: − Devices send sensed data to collector via wireless hops Peer to Peer A peer-to-peer (abbreviated to P2P) computer network is one in which each computer in the network can act as a client or server for the other computers in the network, allowing shared access to various resources such as files, peripherals, and sensors without the need for a central server. P2P networks can be set up within the home, a business, or over the Internet. Each network type requires all computers in the network to use the same or a compatible program. P2P networks can be used for sharing content such as audio, video, data, or anything in digital format. Many peer-to-peer systems, such as BitTorrent, do not have any central database of content. Instead, each user maintains his own database locally and provides a list of other nearby people who are members of the system. Peer to Peer P2P is a distributed application architecture that partitions tasks or workloads among peers. Peers are equally privileged participants in the application. Each computer in the network is referred to as a node. The owner of each computer on a P2P network would set aside a portion of its resources—such as processing power, disk storage, or network bandwidth—to be made directly available to other network participant, without the need for central coordination by servers or stable hosts. With this model, peers are both suppliers and consumers of resources and also it can supplement the user detection and recovery and improve quality assurance activity of the product., in contrast to the traditional client–server model where only the server supply (send), and clients consume (receive). Network Standardization Standards define what is needed for interoperability Some of the many standards bodies: Body Area Examples ITU Telecommunications G.992, ADSL H.264, MPEG4 IEEE Communications 802.3, Ethernet 802.11, WiFi IETF Internet RFC 2616, HTTP/1.1 RFC 1034/1035, DNS W3C Web HTML5 standard CSS standard Security Where do we start? e.g. Phising Phising Messages masquerade as originating from a trustworthy party, for example, your bank, to try to trick you into revealing sensitive information, for example, credit card numbers. …..Hacking tools, DDoS, Passwords, Hashing, PGP, Encryption, Cryptography….all covered later Network Security field of network security: how bad guys can attack computer networks how we can defend networks against attacks how to design architectures that are immune to attacks Internet not originally designed with (much) security in mind original vision: “a group of mutually trusting users attached to a transparent network” Internet protocol designers playing “catch-up” security considerations in all layers! Bad guys: put malware into hosts via Internet malware can get in host from a virus, worm, or Trojan horse. spyware malware can record keystrokes, web sites visited, upload info to collection site. infected host can be enrolled in botnet, used for spam and DDoS attacks. malware often self-replicating: from one infected host, seeks entry into other hosts Bad guys: put malware into hosts via Internet Trojan horse • hidden part of some otherwise useful software • today often in Web page (Active-X, plugin) virus • infection by receiving object (e.g., e-mail attachment), actively executing • self-replicating: propagate itself to other hosts, users worm: infection by passively receiving object that gets itself executed self- replicating: propagates to other hosts, users Sapphire Worm: aggregate scans/sec in first 5 minutes of outbreak (CAIDA, UWisc data) Bad guys: attack server, network infrastructure Denial of Service (DoS): attackers make resources (server, bandwidth) unavailable to legitimate traffic by overwhelming resource with bogus traffic 1. select target 2. break into hosts around the network (see botnet) 3. send packets to target from compromised hosts target The bad guys can sniff packets Packet sniffing: • broadcast media (shared Ethernet, wireless) • promiscuous network interface reads/records all packets (e.g., including passwords!) passing by C A src:B dest:A payload B Wireshark software used for end-of-chapter labs is a (free) packet-sniffer The bad guys can use false source addresses IP spoofing: send packet with false source address C A src:B dest:A payload B The bad guys can record and playback record-and-playback: sniff sensitive info (e.g., password), and use later • password holder is that user from system point of view A C src:B dest:A user: B; password: foo B … lots more on security later in course Metric Units The main prefixes we use: • Prefix Exp. prefix exp. K(ilo) 103 m(illi) 10-3 M(ega) 106 μ(micro) 10-6 G(iga) 109 n(ano) 10-9 Use powers of 10 for rates, powers of 2 for storage − E.g., 1 Mbps = 1,000,000 bps, 1 KB = 1024 bytes • “B” is for bytes, “b” is for bits CN5E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011 Undersea Cables Today’s Lab Protocol Layers - Wireshark Network Packet Sniffing Word version Command Line Tools - Ping, IPconfig, NSlookup and more. Week 1 Supplementary Tutorials Web Page Load Test - Run a diagnostic on www.ulster.ac.uk to see resource loading waterfall charts, Page Speed optimization checks and suggestions for improvements. Web Page Load Comparison - Compare 2 sites such as www.ulster.ac.uk and www.qub.ac.uk to see how optimised they are. Mobile Web Page Load Test - Choose one of the device/location options and hit run. Your page will be loaded on a real mobile device, and you will receive rich detail about how long it took to load, including waterfall charts and video recording of the page load. Week 1 Online Tutorials OSI Layer Names - Arrange the OSI Layers OSI Layer Activity - Arrange the OSI Layers by function Layers video - Short tutorial on network layer communication End Chapter 1