* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Chapter 05
Survey
Document related concepts
Computer and network surveillance wikipedia , lookup
Wireless security wikipedia , lookup
Airport security wikipedia , lookup
Distributed firewall wikipedia , lookup
Trusted Computing wikipedia , lookup
Access control wikipedia , lookup
Multilevel security wikipedia , lookup
Unix security wikipedia , lookup
Information security wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Mobile security wikipedia , lookup
Cybercrime countermeasures wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Social engineering (security) wikipedia , lookup
Transcript
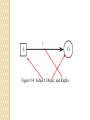
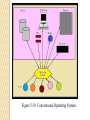
Trusted System? What are the characteristics of a trusted system? What is a security policy and how must it be enforced? Underpinning of a Trusted OS Policy: has requirements. Model: represents the policy. Design: decide how to implement it. Trust ◦ Features: has them to enforce security. ◦ Assurance: provide confidence in the system. Trusted Software Key Characteristics Functionally correct: does what it is suppose to. Enforcement of Integrity: maintain correctness of data. Limited privilege: program access secure data but access is minimized. Appropriate confidence level: program has been evaluated and rated at a degree of trust. ◦ Common Criteria: ICC international standard for security. Figure 5-14 Combined Security Kernel/Operating System. Figure 5-15 Separate Security Kernel. Trusted Computing Base (TCB) Conceptual Construct: not physical. Security-relevant portions of a computer system that enforce a security policy. The level of trust a system provides. Address hardware software and firmware. Trusted Path: communication channel. Trusted Shell: can’t bust out of it. Processes have their own execution domain. Memory and I/O protection. Figure 5-13 TCB and Non-TCB Code. Security Perimeter Everything outside of TCB. Divides trusted from un-trusted. Communication between TCB and components outside the TCB cannot expose the system to security compromises. Figure 5-12 Reference Monitor. Conceptual The most important part of a security kernel. Mediates all access subjects have to objects. •Tamperproof and provide isolation. •Un-bypassable: invoked for every access attempt. •Analyzable: small enough to be tested. There are other security mechanisms helping the system. Security Policy Policy ◦ High-level management directives. ◦ A statement of the security we expect the system to enforce. Policy Components ◦ ◦ ◦ ◦ Purpose: Why. Scope: what is covered. Responsibilities: of teams, staff, management. Compliance: judge effectiveness, consequences Military Security Policy Military Policy. ◦ Protect classified information; ◦ Rank information by sensitivity level. ◦ Need to know rule: only subjects who need to know. ◦ Projects are compartmentalized for protection. Least Sensitive Figure 5-1 Hierarchy of Sensitivities. Compartments Projects are called compartments; ◦ Information can cross compartments and sensitivity levels. ◦ Individuals are assigned to projects. ◦ Compartments enforce need-to-know policy. ◦ Clearances are required to access information. Figure 5-2 Compartments and Sensitivity Levels. Figure 5-3 Association of Information and Compartments. Discussion Question Commercial Security Policies. ◦ Why must companies be concerned about security? Commercial Security Maintain competitive advantage. Industrial espionage. Protect financial information. Categories of information; ◦ Public: less sensitive. ◦ Proprietary: less sensitive than internal. ◦ Internal: sensitive. Figure 5-4 Commercial View of Sensitive Information. Models of Security (Why?) Test a particular policy for completeness and consistency. Document a policy. Help conceptualize and design an implementation. Check whether an implementation meets its requirements. Bell-LaPadula Security Model First mathematical model to of a multi-level security policy. For Department of Defense ◦ Simple security property: no read up. ◦ *Security property: no write down. ◦ Strong Tranquility Property Security labels will not change while system operating. ◦ Weak Tranquility Property Security labels will not change in a way that conflicts with defined security properties. “Keep secrets secret” Figure 5-7 Secure Flow of Information. Bell-La Padula model Simple security property: no read up operations. *security property: no write-down operations. Confidentiality is critical to maintain. Biba (integrity) Mode Businesses are concerned with integrity of information A State Machine model ◦ mathematical model, evaluate every state. Simple integrity axiom: No read down. *Integrity axiom: no write up. Invocation property ◦ Subject cannot request service to subjects of a higher integrity. Opposite of Bell-LaPadula. ◦ Confidentiality at odds with integrity. Clark-Wilson Integrity Model Well formed transactions: ability to enforce control over applications. Users: Active Agents. Transformation Procedures (TPs) abstract operations, read, write and modify. Constrained data items (CDIs): manipulated only by TPs. Unconstrained data items (UDIs): manipulated by users via primitive read and write operations. Integrity verification procedures (IVPs) Check the consistency of CDIs with external reality. Clark Wilson Security Models cont. Information Flow: describe how information can flow. ◦ Bell-LaPadula and Biba use this. Chinese Wall (Brewer-Nash):avoid conflicts of interest. (consultant control) ◦ Prohibit access to conflict of interest categories. Noninterference: data at different security domains remain separate. Harrison-Ruzzo-Ullman: maps subjects, objects and access rights to a matrix. Zachman Framework: six frameworks for providing information security. Figure 5-5 Chinese Wall Security Policy. Zachman Framework Security Models cont. Take Grant Protection: ◦ rules govern interactions between subjects, and objects and permissions subjects can grant. ◦ Primitive operations: Create Revoke Take Grant Objects are either active or passive. Figure 5-8 Subject, Object, and Rights. Figure 5-9 Creating an Object; Revoking, Granting, and Taking Access Rights. Why Study Models? Models help us to determine what policies a secure system will enforce. Essential to designing a trusted operating system. Determine what is feasible and what is not. Figure 5-10 Overview of an Operating System’s Functions. User authentication, memory protection, file I/O access, access access control, enforce sharing, fair service, inter-process communications and synchronization, protected OS and data. Figure 5-11 Security Functions of a Trusted Operating System. User identification and authentication, mandatory access control, discretionary access control, object reuse protection, complete mediation, trusted path, audit, audit log reduction, intrusion detection. Access Control Mandatory (MAC): decisions made beyond the end user. Discretionary (DAC): end user decides access. Non-Discretionary: Role based access control. Roles define access. Content/Context dependent: check an additional context before allowing access such as time, or if accessing their records. Centralized: all access centralized. ◦ Single Sign On. Provide AAA. Decentralized: allow IT administrators at each location employ different policies and levels of security. Discussion Question Explain the meaning of granularity in respect to access control. Discuss the trade off between granularity and effciency. Granularity vs. Efficiency Granularity: the extend to which a task is broken down into smaller parts. ◦ Maximum granularity control each individual object. ◦ Course granularity Organize information into directories or groups. Then apply access rules. Management efficiency affected by choice. Memory Chip based (RAM), disk based, tape. RAM: CPU may randomly access addresses. ROM: Read Only Memory, survives power loss. Cache Memory: fast memory on system. Memory Protection: protect CIA of process Hardware segmentation: mapping processes to specific memory addresses. Virtual Memory: map between applications and hardware. ◦ More than just paging, shares libraries in memory. Figure 5-16 Conventional Multiuser Operating System Memory. Figure 5-17 Multiple Virtual Addressing Spaces. Typical Computer Application Application Application Application Application Operating System and Drivers CPU(s) Memory Network Storage Peripherals Hardware 5/23/2017 40 Figure 5-18 Conventional Operating System. Virtual Computer Applications Virtual Hardware and Operating System CPU(s) Applications Virtual Hardware and Operating System Memory Applications Virtual Hardware and Operating System Network Storage Applications Virtual Hardware and Operating System Peripherals Hardware 5/23/2017 42 Figure 5-19 Virtual Machine. VM Security Harden base OS: this manages VMs. Set Resource limits: CPU, memory, etc. Firewall host on operating system. Use encrypted protocols. Harden guest operating systems. Keep up with host and guest patches. ◦ Guest operating system may be different. Audit logs and performance. 5/23/2017 45 Figure 5-20 Layered Operating System. Figure 5-21 Modules Operating in Different Layers. International Common Criteria Agreed upon standard for describing and testing the security of IT products. Target of Evaluation ◦ ToE product under evaluation. Security Target (ST) ◦ documentation describing the ToE including security requirements. Protection Profile ◦ Independent set of security requirements for a category of products or systems. Evaluation assurance level ◦ Score of the product. CC Levels of Evaluation 7 Levels building on previous level. EAL1: functionally tested. EAL2: structurally tested. EAL3: methodically tested & checked. EAL4: methodically designed, tested & checked. EAL5: semi-formally designed & tested. EAL6: semi-formally verified, designed & tested. EAL7: formally verified, designed & tested. Discussion Question Why would a company go after Common Criteria Certification for their products? New Business and $$$ Having certified products opens new markets for your business ◦ Government Contracts. ◦ International private businesses requiring high levels of security. It can be an expensive process though. ◦ In 2006 an EAL4 rating takes 2 years and $350,000 for a product. Figure 5-27 Criteria Development Efforts. Payment Card Industry (PCI) Data Security Standard (DSS) Core Principles: ◦ ◦ ◦ ◦ ◦ ◦ Build and maintain a secure network. Protect cardholder data. Maintain a vulnerability management program. Implement strong access control measures. Regularly monitor and test networks. Maintain an information security policy. Certification and Accreditation Certification ◦ System has been certified to meet security requirements of the data owner. Accreditation ◦ The data owner’s acceptance of the certification and the residual risk required before it is put into production. Government busy working on these procedures.