* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Module 8: Examining Active Directory Replication
Survey
Document related concepts
Entity–attribute–value model wikipedia , lookup
Lustre (file system) wikipedia , lookup
Business intelligence wikipedia , lookup
File system wikipedia , lookup
Data vault modeling wikipedia , lookup
Commitment ordering wikipedia , lookup
File locking wikipedia , lookup
File Allocation Table wikipedia , lookup
Design of the FAT file system wikipedia , lookup
Expense and cost recovery system (ECRS) wikipedia , lookup
Computer file wikipedia , lookup
Relational model wikipedia , lookup
Serializability wikipedia , lookup
Versant Object Database wikipedia , lookup
Clusterpoint wikipedia , lookup
Transcript
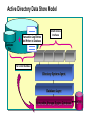
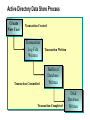
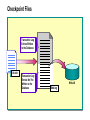
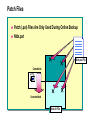
Module 9: Planning for Active Directory Data Recovery and Maintenance Overview Active Directory Data Store Model Active Directory Data Store Process Introduction to Active Directory Data Store Files Maintaining Active Directory Recovering Active Directory Planning for Active Directory Backup Active Directory Data Store Model Database File + Transaction Log Entries Not Written to Database Client Access Interfaces The Current Database Directory System Agent Database Layer Extensible Storage Engine Database NTFS Active Directory Data Store Process Create New User Transaction Created Transaction Log File Written Transaction Committed Transaction Written Buffered Database Written Transaction Completed Disk Database Written Introduction to Active Directory Data Store Files Data Log Files Transaction Logs Database File Checkpoint File Reserved Logs Patch File The Active Directory Database File Contains All Objects in Active Directory Single File for Each Domain Controller Should Be Regularly Backed Up Can Be Included in Routine File Backup Stores Information in Tables The Transaction Log Files Each Previous Log Is Renamed After 10 MB of Data Is Accepted Current Log Previous Logs 1 MB 3 MB Renamed 10 MB Edb.log New Edb.log (10 MB) EdbOOOO1.log EdbOOOO2.log EdbOOOO3.log . . . Logging Can Be Circular or Non-circular Checkpoint Files Transaction Log Entries Written to the Database Edb.chk Transaction Log Entries Not Yet Written to the Database Ntds.dit Edb.log Reserved Log Files Low Disk Space Situations Assumes the Role of a Normal Transaction Log Transaction Logs Res1.log Res2.log Patch Files Patch (.pat) Files Are Only Used During Online Backup Ntds.pat Ntds.pat File Committed Uncommitted Ntds.dit File Maintaining Active Directory Automatic Database Cleanup Manual Database Cleanup Automatic Database Cleanup Garbage Collection Occurs at 12-Hour Intervals Unneeded transaction log files deleted Obsolete objects deleted Online database defragmentation performed Manual Database Cleanup Offline Database Defragmentation Tool Reorders objects Can reduce database size LostAndFound Container Contains misplaced objects Should be examined occasionally Recovering Active Directory Non-Authoritative Restore Authoritative Restore Recovery Without Restore Non-Authoritative Restore Depends on Backup, Replication, and Transaction Logs for Recovery and Includes Placing domain controller in directory safe mode Restoring data Writing flag to registry to trigger a consistency check and re-indexing Replicating bringing the restored server to the current database state Authoritative Restore Authoritative Restore Is a Partial Restore Recovery Without Restore Use Transaction Logging for Recovery No restore needed Circular logging must not be enabled Planning for Active Directory Backup Preferred Disk Configurations Determining Hardware Needs Creating a Backup Strategy Preferred Disk Configurations Enhanced System Performance and Reliability Preferred Configuration Place Windows 2000 system files, and Active Directory database file and transaction log files on separate disks Determining Hardware Needs Predict the Size of Your Active Directory Determine number of objects Take into consideration the addition of attributes Test Your Prediction Double Your Prediction for Actual Production Creating a Backup Strategy Hardware Backup Method Off-Site Storage Test Restores Best Practices Plan for Backup and Recovery Early Keep the Database Files and Transaction Logs on Separate Drives Predict Active Directory Size Develop, Document, and Enforce a Backup Policy Lab A: Active Directory Disaster Recovery Lab B: Active Directory Database Planning Review Active Directory Data Store Model Active Directory Data Store Process Introduction to Active Directory Data Store Files Maintaining Active Directory Recovering Active Directory Planning for Active Directory Backup