* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download NAT - Hong Kong University of Science and Technology
Airborne Networking wikipedia , lookup
Remote Desktop Services wikipedia , lookup
Computer network wikipedia , lookup
Wireless security wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Parallel port wikipedia , lookup
Dynamic Host Configuration Protocol wikipedia , lookup
Network tap wikipedia , lookup
Internet protocol suite wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Universal Plug and Play wikipedia , lookup
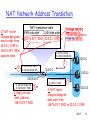
Deep packet inspection wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
SIP extensions for the IP Multimedia Subsystem wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Network Address Translation Dr. Danny Tsang Department of Electronic & Computer Engineering Hong Kong University of Science and Technology NAT 1 Outline Goal Understand how firewall and NAT function Be aware of problems created by Firewall and NAT Master the NAT traversal techniques What are Firewall and NAT? Problems created by Firewall and NAT? Solutions Traversal of NAT/Firewall NAT 2 Firewalls firewall isolates organization’s internal net from open Internet, protect the local network from being accessed by unauthorized sources public Internet administered network firewall NAT 3 Firewalls: Why prevent denial of service attacks: SYN flooding: attacker establishes many bogus TCP connections, no resources left for “real” connections. prevent illegal modification/access of internal data. e.g., attacker replaces CIA’s homepage with something else allow only authorized access to inside network (set of authenticated users/hosts) two types of firewalls: application-level packet-filtering NAT 4 Packet Filtering Should arriving packet be allowed in? Departing packet let out? internal network connected to Internet via router firewall router filters packet-by-packet, decision to forward/drop packet based on: source IP address, destination IP address TCP/UDP source and destination port numbers ICMP message type TCP SYN and ACK bits NAT 5 Packet Filtering Example 1: block incoming and outgoing datagrams with IP protocol field = 17 and with either source or dest port = 23. All incoming and outgoing UDP flows and telnet connections are blocked. Example 2: Block inbound TCP segments with ACK=0. Prevents external clients from making TCP connections with internal clients, but allows internal clients to connect to outside. NAT 6 Application gateways ALG filters packets on host-to-gateway telnet session application messages while firewall filters packets on IP/TCP/UDP fields. Example: allow select internal users to telnet outside. application gateway gateway-to-remote host telnet session router and filter 1. Require all telnet users to telnet through ALG. 2. For authorized users, gateway sets up telnet connection to dest host. Gateway relays data between 2 connections 3. Router blocks all telnet connections not originating from ALG. NAT 7 Default Behavior of Firewall A firewall identifies networks as inside or outside Packets can get from the inside to the outside Packets from the outside that are associated with an inside originated connections are allowed back in Packets originated from the outside are not allowed to the inside NAT 8 Limitations of firewalls and gateways IP spoofing: router can’t know if data “really” comes from claimed source if multiple app’s. need special treatment, each has own app. gateway. client software must know how to contact gateway. filters often use all or nothing policy for UDP. tradeoff: degree of communication with outside world, level of security many highly protected sites still suffer from attacks. e.g., must set IP address of proxy in Web browser NAT 9 NAT: Network Address Translation rest of Internet local network (e.g., home network) 10.0.0/24 10.0.0.4 10.0.0.1 10.0.0.2 138.76.29.7 10.0.0.3 All datagrams leaving local network have same single source NAT IP address: 138.76.29.7, different source port numbers Datagrams with source or destination in this network have 10.0.0/24 address for source, destination (as usual) NAT 10 NAT: Network Address Translation Motivation: local network uses just one IP address as far as outside word is concerned: no need to be allocated range of addresses from ISP: - just one IP address is used for all devices can change addresses of devices in local network without notifying outside world can change ISP without changing addresses of devices in local network devices inside local net not explicitly addressable, visible by outside world (a security plus). NAT 11 NAT Traversal in VoIP NATs map a private IP address space to externally visible (public) IP addresses Conserve limited public IP addresses Shield internal hosts from outside world Useful for enterprises, cable modem networks, broadband access routers, internet cafes… NATs interfere with peer-to-peer protocols such as SIP SIP clients must identify the IP address and ports they will use to receive media streams (in payload of their signaling messages) But they don’t know their externally visible addresses “One of the SIP community’s biggest problems” NAT 12 NAT: Network Address Translation Implementation: NAT router must: outgoing datagrams: replace (source IP address, port #) of every outgoing datagram to (NAT IP address, new port #) . . . remote clients/servers will respond using (NAT IP address, new port #) as destination addr. remember (in NAT translation table) every (source IP address, port #) to (NAT IP address, new port #) translation pair incoming datagrams: replace (NAT IP address, new port #) in dest fields of every incoming datagram with corresponding (source IP address, port #) stored in NAT table NAT 13 NAT: Network Address Translation 2: NAT router changes datagram source addr from 10.0.0.1, 3345 to 138.76.29.7, 5001, updates table 2 NAT translation table WAN side addr LAN side addr Bindings only 1: host can 10.0.0.1 besends initiated by datagram to outgoing traffic 128.119.40, 80 138.76.29.7, 5001 10.0.0.1, 3345 …… …… S: 10.0.0.1, 3345 D: 128.119.40.186, 80 S: 138.76.29.7, 5001 D: 128.119.40.186, 80 138.76.29.7 S: 128.119.40.186, 80 D: 138.76.29.7, 5001 3: Reply arrives dest. address: 138.76.29.7, 5001 3 1 10.0.0.1 10.0.0.4 S: 128.119.40.186, 80 D: 10.0.0.1, 3345 10.0.0.2 4 10.0.0.3 4: NAT router changes datagram dest addr from 138.76.29.7, 5001 to 10.0.0.1, 3345 NAT 14 NAT: Pros Use of a single registered IP address for an entire network Independence of ISP IP addresses Transparent to end systems in some cases (increased security) Delays need for IPv4 replacement 16-bit port-number field: 60,000 simultaneous connections with a single WAN-side address! Mask the true internal IP addresses of the internal network NAT 15 NAT: Cons Violates end-to-end argument NAT possibility must be taken into account by app designers, e.g, P2P application Increases local support burden and complexity NAT 16 Outline What are Firewall and NAT? Problems created by Firewall and NAT? Solutions Traverse of NAT/Firewall NAT 17 NAT & Firewall Problem NAT & Firewall are employed to prevent hackers or unauthorized persons to access to the internal network Voice and video over IP are not NAT & Firewall friendly Provide secure two-way communication connection cross the NAT & Firewall Firewall Problem NAT Problem NAT 18 Firewall Problem for VoIP A 4.INVITE 1. INVITE 5. Media (A) Internet 3.Media B 2.OK 5.Media (B) 1. User A is able to call User B since the firewall allows inside to outside sessions 2. User B is able to respond back to User A at the VoIP signaling layer 3. PROBLEM: Media traffic sent by User B from outside will be blocked since it uses a different socket than the VoIP signaling 4. PROBLEM: If User B tries to initiate a call to User A, it will be blocked by firewall 5. PROBLEM: If symmetric RTP is not used, the RTP fails to get back inside from B (S-RTP = the UA uses the same socket/port for sending and receiving the RTP)NAT 19 NAT Problem for VoIP 1. INVITE 10.0.0.1 202.123.211.25 Internet ? 2. OK 3. Media 1. User A sends an invite to User B, NAT translate the layer 3 address, but not the layer 5 (SIP,SDP) addresses 2. User B receives the invite and responds back to the NAT address 3. PROBLEM: User B tries to send RTP to User A with IP:Port (c= 10.0.0.1 :m= 8000), but this fails since it can not route to User A Notes: VoIP devices on the Internet •cannot make calls to private address (where to send them?) •do no know the type of NAT being used (cone, symmetric and so on), so they do not know about what kinds of bindings to use •do not know if the bindings are still open NAT 20 Sip trace SIP Signaling SDP Signaling 001 002 003 004 005 006 007 008 009 010 011 012 013 014 015 016 017 018 019 020 Internal IP address INVITE sip:[email protected] SIP/2.0 Via: SIP/2.0/UDP 211.123.66.223:5060;branch=a71b6d57-507c77f2 Via: SIP/2.0/UDP 10.0.0.1:5060;received=202.123.211.25;rport=12345 From: <sip:[email protected]>;tag=108bcd14 To: sip: [email protected] Contact: sip: [email protected] Call-ID: [email protected] CSeq: 703141 INVITE External IP address Content-Length: 138 seen by SIP proxy Content-Type: application/sdp from outside User-Agent: HearMe SoftPHONE v=0 o=deltathree 0 0 IN IP4 10.0.0.1 s=deltathree c=IN IP4 10.0.0.1 t=0 0 m=audio 8000 RTP/AVP 4 a=ptime:90 a=x-ssrc:00aea3c0 Internal IP address for RTP stream NAT 21 Symmetric RTP Classical RTP is unidirectional (i.e.two RTP sessions, one in each direction) Endpoints use UDP port symmetry to establish bi-directional traffic Sending and receiving ports for the RTP and RTCP traffic should be the same on the endpoint behind the NAT/Firewall Connection oriented Usage require that endpoints use UDP port symmetry to establish bi-directional traffic NAT 22 Solution to NAT Traversal Let clients be aware of their external IP:PORT Ask the NAT Universal Plug and Play (UPnP) Ask someone outside the NAT Simple Traversal of UDP Through NATs (STUN) Traversal Using Relay NAT (TURN) Interactive Connectivity Establishment (ICE) Make NAT & Firewall SIP friendly Application Layer Gateway NAT 23 Universal Plug and Play (UPnP) Proposed by Microsoft Client talks with NAT gateway and ask about IP and ports Will NOT work with cascading NAT NAT 24 Universal Plug and Play (UPnP) 1. What is my IP:Port assigned 40.50.60.70 Source 10.0.0.1:8000 2. 40.50.60.70:9001 Will NOT work with cascading NAT for security issue NAT 25 Solution to NAT/Firewall Traversal Let clients be aware of their external IP:PORT Ask the NAT Universal Plug and Play (UPnP) Ask someone outside the NAT Simple Traversal of UDP Through NATs (STUN) Traversal Using Relay NAT (TURN) Interactive Connectivity Establishment (ICE) Make NAT & Firewall SIP friendly Application Layer Gateway NAT 26 STUN Simple Traversal of UDP Through NATs Types of NATs Full Cone (Address) Restricted Cone Port Restricted Cone Symmetric Increasing security Not suitable for Symmetric NAT NAT 27 Types of NATs: Full Cone NAT translation table LAN side addr WAN side addr Client A 10.0.0.1:8000 10.0.0.1,8000 …… 143.89.47.012:7868 40.50.60.70,9000 …… 40.50.60.70 Client C 166.111.25.36:7865 10.0.0.4 Client B 45.36.245.57:6988 All the incoming traffic can get through from the pinhole to client A if they know the IP : Port mapping Client D NAT 28 Types of NATs: (Address) Restricted Cone NAT translation table LAN side addr WAN side addr 10.0.0.1,8000 …… Client A 10.0.0.1:8000 40.50.60.70,9000 …… Traffic from B with different source ports can get through 40.50.60.70 10.0.0.4 143.89.47.012:7868 Client C 166.111.25.36:7865 166.111.25.36:7865 166.111.25.36:2134 Client B 45.36.245.57:6988 Filter traffic only by IP : block incoming traffic from other IP (client C and D) address. Incoming traffic from same authorized IP but different ports will be accepted Client D NAT 29 Types of NATs: Port Restricted Cone NAT translation table LAN side addr WAN side addr 10.0.0.1, 8000 …… Client A 10.0.0.1:8000 40.50.60.70, 9000 …… 143.89.47.012:7868 Client C 40.50.60.70 166.111.25.36:7865 10.0.0.4 166.111.25.36:2134 166.111.25.36:7865 Client B 45.36.245.57:6988 Filter by both IP and Port: set up one to many mapping Client D NAT 30 Types of NATs: Port Restricted Cone (con’t) Only one entry is set up in the table for 10.0.0.1:8000 to different clients outside Client A 10.0.0.1:8000 NAT translation table LAN side addr WAN side addr 10.0.0.1, 8000 …… 40.50.60.70, 9000 …… 143.89.47.012:7868 Client C 40.50.60.70 166.111.25.36:7865 10.0.0.4 166.111.25.36:2134 166.111.25.36:7865 Client B 45.36.245.57:6988 Filter by both IP and Port: set up only one entry for multiple remote clients Client D NAT 31 Types of NATs: Symmetric NAT translation table LAN side addr WAN side addr 10.0.0.1, 8000 10.0.0.1, 8000 Client A 10.0.0.1:8000 40.50.60.70, 9000 40.50.60.70, 9001 40.50.60.70 10.0.0.4 40.50.60.70:9000 143.89.47.012:7868 Client C 166.111.25.36:7865 40.50.60.70:9001 Filter by both IP and Port, NAT assign a mapping for each source-destination pair Client B 45.36.245.57:6988 Client D NAT 32 STUN External Query Ask a server on the Internet what I “look” like Compared the returned answer (external address) with my own address (local internal address) Put my “real address” in signaling to allow media traffic in This works IF: The client send and receive RTP on the same port (why ?) SIP request must be sent immediately. After a while the mapping might change In the case of Address Restricted Cone or Port Restricted Cone it must send out data to the other end first NAT 33 STUN Solution 3. Incoming media through withIP:Port the informed IP:Port 1. Send query to 2.STUN Put get assigned server IP:Port to ask in SDP assigned by NAT Symmetric NAT case NAT translation table LAN side addr 10.0.0.1, 8000 10.0.0.1, 8000 WAN side addr 40.50.60.70, 9000 40.50.60.70, 9001 Useless for symmetric NAT since holes punctured by STUN can not be used by others Assigned for STUN by NAT Assigned for RTP by NAT, RTP is only authorized to get through using 9001 but not 9000 due to the NAT/Firewall combination NAT 34 STUN (Cont’) With the information sent by STUN, client can determine If it is on the open Internet If it is behind a firewall that blocks UDP If it is behind a NAT and what type of NAT it is behind Will NOT work for symmetric NAT Typical in Large Enterprise NAT 35 TURN Solve ‘Symmetric’ NAT case by allowing Media Flows Through TURN Server directly Not the case with STUN servers Increase voice latency Increase probability of packet loss Few SIP clients support TURN today (complex and not-yet a standard) No free TURN server available (only commercial) Skype seems to support TURN NAT 36 TURN Solution Media makes use of the hole punctured by TURN directly NAT translation table LAN side addr WAN side addr 10.0.0.1, 8000 40.50.60.70, 9000 … … Assigned for both TURN and SIP by NAT NAT 37 Interactive Connectivity Establishment Learns about the network topology in which the clients exist and the various sets of network addresses by which these devices can communicate Framework to unify the various NAT traversal techniques STUN, TURN and Realm Specific IP (RSIP) Benefits from the collective functionality of each while avoiding any one protocol's drawback NAT 38 Initiator TURN,STUN Servers Client A 1. Gather address The more The happier 2. Initiate Messages Responder Client B (INVITE) 3. Gather address (200 OK) 4. Accept Messages 5. Address-fixing 6. Address-fixing 7. Media Highest Preference Address Is Used 8. Media NAT 39 ICE ICE Properties Always will find a means for communicating if one physically exists Always finds the communications path with fewest relays Always finds the communication path cheapest for the service provider Does not require any knowledge of topology, NAT types, or anything Can guarantee that the phone won’t ring unless audio works when you pickup NAT 40 Solution to NAT Traversal Let clients be aware of their external IP:PORT Ask the NAT Universal Plug and Play (UPnP) Ask someone outside the NAT Simple Traversal of UDP Through NATs (STUN) Traversal Using Relay NAT (TURN) Interactive Connectivity Establishment (ICE) Make NAT & Firewall SIP aware Application Layer Gateway NAT 41 Application Layer Gateway Make Firewall/NAT SIP aware Analyze the address information inside the packet payload and dynamically open or close holes for media communications Needed to be updated for each new application which restricts it for large corporate networks No commercial SIP ALGs today NAT 42 Application Layer Gateway Solution Understanding the signaling messages and their relationship with resulting media flows ---- Media Friendly NAT 43 Solution to NAT Traversal Let clients be aware of their external IP:PORT Ask the NAT Universal Plug and Play (UPnP) Ask someone outside the NAT Simple Traversal of UDP Through NATs (STUN) Traversal Using Relay NAT (TURN) Interactive Connectivity Establishment (ICE) Make NAT & Firewall SIP aware Application Layer Gateway NAT 44 Summary Problem address Provide “secure” “two-way” communication connection cross the NAT & Firewall Traverse techniques mainly used Universal Plug and Play (UPnP) Simple Traversal of UDP Through NATs (STUN) Traversal Using Relay NAT (TURN) Interactive Connectivity Establishment (ICE) Application Layer Gateway NAT 45 Reference T. Dierks and C. Allen, “The TLS protocol version 1.0,” , United States, 1999. S. Blake-Wilson, M. Nystrom, D. Hopwood, J. Mikkelsen, and T. Wright, “Transport layer security (TLS) extensions,” , United States, 2003. J. Rosenberg, J. Weinberger, C. Huitema, and R. Mahy, “STUN: Simple traversal of user datagram protocol (UDP) through network address translators (NATs),” , United States, 2003. J. Rosenberg, R. Mahy, and C. Huitema, “TURN: traversal using relay NAT,” July 2004, Internet draft, Work in progress, Internet Engineering Task Force. J. Rosenberg, “Interactive connectivity establishment (ICE): A methodology for network address translator (NAT) traversal for multimedia session establishment protocols,” 2005, work in Progress RFC draft. [Online]. Available: http://ietfreport.isoc.org/ids/draft-ietf-mmusic-ice-05.txt Cisco white paper: VoIP Traversal of NAT and Firewall T. Chapuran, “Voice over IP: Architectures, applications and challenges,” 2002, telcordia Technologies. [Online]. Available: http://www.umiacs.umd.edu/docs/voip tc.ppt NAT 46