* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Security - Ingate Systems
Survey
Document related concepts
Multilevel security wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Airport security wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Unix security wikipedia , lookup
Deep packet inspection wikipedia , lookup
Wireless security wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Mobile security wikipedia , lookup
Computer security wikipedia , lookup
Security-focused operating system wikipedia , lookup
Transcript
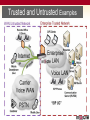
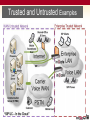
IT Expo SECURITY Scott Beer Director, Product Support Ingate [email protected] +1-613-963-0933 What is Network Security? • Network Security • Consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. • http://en.wikipedia.org/wiki/Network_security • Should Security apply to Voice over IP? • YES! ABSOLUTELY! What is Network Security? • Why should Security apply to VoIP? • VoIP security involves the authorization of access to Voice applications in a network • Authenticating information that allows voice access to Call Control and UC Applications • VoIP Security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. What is Network Security? • Why should Security apply to VoIP? (con’t) • VoIP can be private, such as within a company, and others which might be open to public access. • VoIP security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the Voice Network, as well as protecting and overseeing operations being done. What is Network Security? • Why is VoIP Security Important? • End of Geography • IP Protocol is an OPEN network system, no longer need to be physically present • Any IP Address can connect with any other IP Address. • Prevent Fraudulent Activities • Identify Theft, Toll Fraud, Spoofing, Misuse, SPAM, SPIT, Vishing, Eavesdropping, Data Mining, Reconnaissance • Prevent Disruption of Service • Denial of Service, Fuzzing Trusted and Untrusted • Policies in Defining Network Security Zones • A network zone describes the trust level of a network connection. • Trusted Network Security Zone • Fully trusted connections. All incoming traffic is allowed. • Untrusted Network Security Zone • Fully untrusted connections. No incoming traffic is allowed. Administrator defines the services/policies Trusted and Untrusted Examples Trusted and Untrusted Examples Trusted and Untrusted Examples Comparing SBCs with Firewalls • Summary • VoIP and UC are being deployed at an growing rate • IP networks provide a highly effective means for enterprises and contact centers to communicate • The IP communications network is now a businesscritical resource • IP-based enterprise communications networks, services and applications must be secured. • For successful VoIP/ UC deployments the enterprise must: • Maximize communication service and interoperability • Assure service availability and quality levels • Control costs Comparing SBCs with Firewalls • Firewalls with SIP ALG (Application Layer Gateway) • Ubiquitous in today’s IP networks—protect IP data networks, servers and applications against a variety of threats through stateful inspection and filtering at layers 3 and 4 of the OSI model. • To enable basic VoIP connectivity through the firewall, some firewalls add SIP ALGs that translate embedded SIP addresses • allows the firewall to maintain a single end-toend SIP session between endpoints residing on either side of the firewall. Comparing SBCs with Firewalls • Session Border Controllers (SBC) • SBC’s implement a SIP back-to-back user agent (B2BUA) as defined in IETF RFC 3261. A B2BUA divides each SIP session into two distinct segments. • In doing so, the SBC is able to completely and effectively controls SIP sessions, as well as the associated media flows, in ways that SIP ALGs cannot. This unique capability gives SBCs a clear edge in their ability to securely deliver reliable, highquality IP-based interactive communications. Comparing SBCs with Firewalls • How It Works • Firewall with SIP ALG • Maintains single SIP session through Firewall • Fully state-aware at layer 3 and 4 • Only inspects/modifies SIP, SDP addresses • Unable to terminate, initiate, re-initiate or respond to SIP signaling messages • Only supports static ACLs and policies Comparing SBC with Firewall • How It Works • Session Border Controllers (SBC) • Implements SIP B2BUA for complete control • Fully state-aware at layers 2-7 • Inspects/modifies all SIP, SDP header info • Can terminate, initiate, re-initiate & respond to SIP signaling messages • Supports static and dynamic ACLs and policies Security with SBC • Session Border Controllers uniquely provide all controls required for delivering trusted, reliable and high-quality IP interactive communications: • Security: IP PBX and UC server DoS/DDoS attack protection, SBC self-protection • Communications reach maximization: IP PBX and UC protocol interworking, remote NAT traversal • SLA assurance: IP PBX & UC server session admission and overload control, data center disaster recovery, remote site survivability, Call Admission Control, SBC high-availability operation • Data Firewalls with application layer gateways (FW/ALG) are effective in securing data-oriented application infrastructure (PCs, servers). Successful Delivery of VoIP Requirements for the successful delivery of enterprise and contact center VoIP/UC services and applications SBC/FW DoS/DDoS Self-Protection VoIP Theft of Service IP PBX & UC SIP Protocol Interoperability IP PBX/UC Server Session Admission & Overload Control Remote Site NAT Traversal High Availability VoIP Operations Data Center Disaster Recovery Remote Site Survivability using SBC/FW Call Admission Control Success Combined Completely Ubiquitous Voice & Data Security SIP Security is Better Why is SIP Security Better than PSTN? Encryption Transport Layer Security (TLS) – Encryption of SIP Signaling SIP Security is Better Why is SIP Security Better than PSTN? Encryption Secure RTP (SRTP) – Encryption of Media Common SIP Attacks Intrusion of Services (or Theft of Service) Devices attempting Register with a IP-PBX in an attempt to look like an IP-PBX extension and gain IP-PBX services SPIT (SPAM over Internet Telephony) Toll Fraud A form of an Intrusion of Service, where malicious attempts to send INVITEs to an IP-PBX to gain access to PSTN Gateways and SIP Trunking to call the PSTN Denial of Service INVITE (or any SIP Request) Flood in an attempt to slow services or disrupt services Or any UDP or TCP traffic directed at a SIP Service on SIP Ports Indirect Security Breaches Common SIP Attacks What is Intrusion of Service? A Third Party attempting to defraud either the Enterprise or the Carrier Devices attempting “Spoof” a Client device in an attempt to look like an extension (or enterprise) and gain services directly, including Toll Fraud. Common SIP Attacks What is Denial of Service? A Third Party attack to make a communications resource unavailable to its intended users Generally consists of the concerted efforts to prevent SIP communications service from functioning efficiently or at all, temporarily or indefinitely One common method of attack involves saturating the target (victim) IP-PBX with external communications requests, such that it cannot respond to legitimate traffic, or responds so slowly as to be rendered effectively unavailable Common SIP Attacks Prevention of SIP Attacks Layered Security Do Not to subject “Mission Critical” Voice applications to SIP Attacks The End Scott Beer Director, Product Support Ingate [email protected] +1-613-963-0933