* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download here
Survey
Document related concepts
Piggybacking (Internet access) wikipedia , lookup
Remote Desktop Services wikipedia , lookup
TCP congestion control wikipedia , lookup
Deep packet inspection wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Distributed firewall wikipedia , lookup
Internet protocol suite wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Peer-to-peer wikipedia , lookup
Zero-configuration networking wikipedia , lookup
SIP extensions for the IP Multimedia Subsystem wikipedia , lookup
Transcript
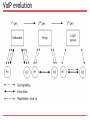
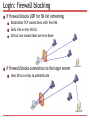
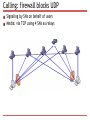
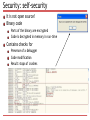
Lecture 10. P2P VoIP D. Moltchanov, TUT, Fall 2014 Outline What is VoIP 2G VoIP system: SIP-based Architecture All-IP calls PSTN-IP-PSTN call Messages and formats 3G VoIP system: P2P Skype Capabilities Login to the network Calling Security features Future VoIP systems: P2P SIP? VoIP basics What is VoIP VoIP definition Specific sets of protocols to carry voice over the IP IP can be private or public Internet Early provided by operators, now by third parties The way VoIP is implemented evolved over time Starting from late 90s End devices Hardware phones Software phones Benefits of using VoIP Operational costs No need for two separate networks (voice and data) Rich set of free features e.g. conference, forwarding… Lower costs since only Internet access is needed Compare pricing scheme: flat for IP vs. per minute Flexibility More than one call over a connection Calls can be encrypted Location independent Integration with other services Computer + phone Note: Internet to Internet calls are free… VoIP evolution 2G VoIP systems: SIP 2G systems: protocols Data transmission: data plane Real-time transport protocol (RTP) Real-time control protocol (RTCP) Signaling: control plane H.323 Session initiation protocol (SIP) Location service: control plane Proxies Finding via DNS SVR PSTN-IP gateways: control plane Media gateway control protocol (MGCP) H.248 (similar to MGCP) Description of codecs used: control plane Session description protocol (SDP) 2G VoIP infrastructure: SIP+RTP SIP+RTP makes a perfect combination DNS is for proxy resolution SIP What it does Setup, control, terminate calls End-to-end signaling Allows for end system and MG control signaling Properties Partially distributed Text based (you may read messages in e.g. Wireshark) Simple (simpler than H.323) Limited but sufficient functionality (i.e. optimized) Functionality Point-to-point and multipoint calls Additional features URL are used for addresses (e.g. sip:[email protected]) Basic call: all-IP Basic call: PSTN-IP-PSTN Reality is a bit more complicated How do we know where to call to? All parties need to be registered with SIP servers Which server to register with? Multicast to all known SIP proxies “sip.mcast.net” (224.0.1.75) How to find the person? SVR (service record) in DNS servers for proxy resolution Specifies the location of proxy server for a specific service That’s why we had DNS servers there What is about type of the media? I use G.711, G.723, G.729, your client may prefer G.729 Use SDP (session description protocol) SIP calling Requesting presence info Alice wants to be informed when Bob is online Registering and notifying Bob goes online, Alice is notified SIP messages: RFC 3261 REGISTER Register and notify proxy about its IP and URLs INVITE Establish a media session between users ACK Confirms reliable message exchanges CANCEL Terminates a pending request BYE Tears down a session between two users in a conference OPTIONS Solicits info about the capabilities SUBSCRIBE Get notifications SDP: RFC 2327 Media streams A session can include multiple streams of differing content. SDP currently: audio, video, data, control, and application Addresses Indicates the destination addresses Ports UDP ports for each stream Payload types Media format for each stream Start and stop times For broadcasting (radio, video) Originator For broadcasting 2G systems: what we see? SIP almost makes a P2P system. Why? Data connection goes directly between parties Control is still performed using servers Similar to “almost P2P” platforms? Music sharing (actually, file sharing) systems of late 90s Napster Audiogalaxy Audiogalaxy example You login using a specific agent Agent imports your song titles to the common DB Once you need something you search through this DB Result is IP of the systems holding this title 3G VoIP systems: P2P Skype What is Skype? A P2P application for Primarily, VoIP Video calls added recently Instant messaging File transfers Proprietary signaling Negotiable voice codecs Proprietary encoders Gateways to/from PSTN/SIP Interesting features Works well in almost all network conditions Works across NATs and firewalls Overlay network Consists of Skype clients (SCs) Supernodes (SNs) Login server HTTP server Client Used to make activities Stores configuration Connected to some SNs Stores few SN addresses Updates them periodically Functionality of elements Supernode A node that can accept incoming TCP connections Preferably has enough CPU, memory, and BW Preferably not behind firewall or NAT There are default supernodes Do signaling directly with other SNs Sometimes perform signaling and data transfer for SCs Login server Ensures that names are unique Authentication point HTTP server Used for updates Skype features Codecs Default: wideband 16KHz sampling, 5Kb per direction 140pcks/s., 67 bytes of payload Ports 80 HTTP, 443 HTTPS TCP Random UDP ports Coding and encryption Everything is encrypted using AES Keys: 256 bits, symmetric RSA for exchanging the symmetric keys Host cache Supernode list (IP, port) to fasten up the process, 200 entries Updated periodically, some SNs are always there Login: joining the overlay Contacting central servers Authentification/authorization Looking for updates at HTTP Joining the overlay Refresh of SN list (shared.xml) List containing SNs Sends UDP packet to a default SN Chooses a certain SN Opens TCP with connection with this SN Connection is maintained throughout a session Exchanges info on on-line nodes Testing for SN capabilities Client sometimes checks whether it could be a new SN Login: firewall blocking If firewall blocks UDP for SN list refreshing Establishes TCP connections with few SNs Gets info on the SN list All but one connections are torn down If firewall blocks connection to the login server Uses SN as a relay to authenticate Calling Signaling Using TCP connection directly Overlay if impossible otherwise Media is carried using UDP Procedure is as follows A queries SNs for the address of B Once obtained signaling is done directly using TCP Then voice is carried using UDP Calling: firewall blocks UDP Signaling by SNs on behalf of users Media: via TCP using 4 SNs as relays Calling: port-restricted NAT Step 1 User A gets address of SN of B Sends UDP query containing its external address SN of B replies with external address of B Step 2 A and B establish UDP flow using hole punching A and B establish TCP connection using 4 SNs as relay Calling: symmetric NAT Step 1 A obtains the address of B Step 2 Trying hole punching It does not work (symmetric NAT) Step 3 They use TCP via 4 SNs as relays Some facts Skype completely fails when firewall blocks UDP and TCP This is exceptionally rare Mechanism 1: hole punching Mechanism 2: tunneling via SN Mechanism 3: use of overlay Trying to use direct connections as much as possible SNs may tear down Nodes may overload overlay Skype is seen as unwanted by enterprises May traverse firewalls, NATs May bring unwanted stuff Security: self-security It is not open source! Binary code Parts of the binary are encrypted Code is decrypted in memory in run-time Contains checks for Presence of a debugger Code modification Result: stops of crushes Security: network security Facts Uses a proprietary protocol Encrypts all the traffic Signaling packets Payload: encrypted using RC4 stream RC4 key can be recovered from the packet VoIP packets Encrypted using AES Only sender and receiver can decrypt Future: P2P SIP? What do we want? A bit more competition + open architecture Goals and motivation Get rid of SIP servers No fixed topology Audio/video/IM all-in-one Interoperability with SIP Possible Join DHT Query position in DHT Update neighbors Repeat periodically More info at: http://www.p2psip.org/