* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Network Protocols
Parallel port wikipedia , lookup
Point-to-Point Protocol over Ethernet wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Distributed firewall wikipedia , lookup
TCP congestion control wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
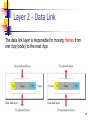
Airborne Networking wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Deep packet inspection wikipedia , lookup
Network tap wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Computer network wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Zero-configuration networking wikipedia , lookup
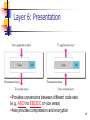
UniPro protocol stack wikipedia , lookup
Internet protocol suite wikipedia , lookup
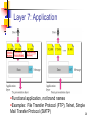
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Introduction and Review – Network Protocols Copyright © Lopamudra Roychoudhuri 1 What’s a Protocol? Human protocols: Network protocols: “What’s the time?” Machines rather than “I have a question” humans Introductions and good- All communication byes activity in Internet governed by protocols … Specific messages sent … Specific actions taken when messages received, or other events 3 What’s a protocol? A human protocol and a computer network protocol: Hi TCP connection request Hi TCP connection response Got the time? Get http://www.awl.com/kurose-ross 2:00 <file> time Q: Other human protocols? 4 Network Protocols A set of agreed-upon rules in which computers exchange information (rules for communication) Define what is communicated; how it is communicated; when it is communicated Key elements of a protocol: Syntax: structure or format of the data Semantics: Meanings of each section of bits Timing/Procedure: when data should be sent and how fast it can be sent. 5 Layered Protocol Architecture Modules arranged in a vertical stack Each layer in stack: Performs related functions (Each layer implements a service) Relies on lower layer for more primitive functions Provides services to next higher layer Communicates with corresponding peer layer of neighboring system using a protocol 6 OSI model International Standards Organization (ISO, est. 1947) A multinational body dedicated to worldwide agreement on international standards Open Systems Interconnection (OSI) model An ISO standard that covers all aspects of network communications First introduced in 1977. 7 OSI Layers 8 Layer 1 - Physical The physical layer is responsible for the movement of individual bits from one hop (node) to the next. 9 Layer 2 - Data Link The data link layer is responsible for moving frames from one hop (node) to the next hop. 10 Layer 3 - Network The network layer is responsible for the delivery of individual packets from the source host to the destination host via hops. 11 Source-to-destination delivery 12 Layer 3-Network cont. Addressing of network nodes Sends data to correct address (possibly across multiple networks) Examples: IP (Internet Protocol), Appletalk, Novell IPX 13 Layer 4 - Transport The transport layer is responsible for the delivery of a whole message (called segment) from one process to another process. 14 Reliable process-to-process delivery of a message 15 Layer 4 – Transport cont. Controls end-to-end error correction and flow control Example: Transmission Control Protocol (TCP) 16 Layer 5 – Session Sets up and manages logical sessions between client programs and servers Synchronization – mechanism for inserting check points Dialog control – half-duplex or fullduplex Example: NetBIOS Extended User Interface (NETBEUI) (Microsoft) 17 Layer 6: Presentation Provides conversions between different code sets (e.g., ASCII to EBCDIC or vice versa) Also provides compression and encryption 18 ASCII Code vs. EBCDIC Code 19 Layer 7: Application (directory Services) (File transfer, Access & mgmt) (msg handling Services) Functional application, not brand names Examples: File Transfer Protocol (FTP), Telnet, Simple Mail Transfer Protocol (SMTP) 20 Summary of OSI Layers e.g. EBCDIC to ASCII Synchronization mechanisms and Dialog control (half-duplex or full-duplex) Messages End-to-end Error and Flow Control Packets Frames Error and Flow Control over a single link Bits 21 OSI Layers cont. Source Destination Hop Hop ‘End-to-end’ protocols ‘Hop-to-Hop’ protocols 22 Internet Protocol Stack Developed by Cerf/Kahn in the early ‘70s (earlier to OSI model) Application: supporting network applications FTP, SMTP, SSH Transport: host-host data transfer TCP, UDP, SCTP Network: routing of datagrams from source to destination IP, routing protocols Link: data transfer between neighboring network elements PPP, Ethernet Physical: bits “on the wire” 5-layer Application Transport Network Link Physical 23 TCP/IP vs. OSI Model Connection-oriented Connectionless 24 Connectionless vs. Connectionoriented Connectionless Service No connection setup necessary before sending data Data sequencing is not guaranteed Example – UDP, IP •Connection-oriented Service A connection must be established first before data transmission Data sequencing is guaranteed Example - TCP 25 Addresses in TCP/IP •Unique address of Network Interface Card. •Also supports for multicast and broadcast physical addresses. •e.g. Ethernet 48 bit globally unique address •Numerical Address assigned to a device participating in a network •e.g. 32-bit IP address for devices in an IP network •No two computers on the Internet can have the same IP address Address for processes to communicate with each other - e.g. 16-bit TCP/UDP port addresses 26 Relationship of layers and addresses in TCP/IP 27 Physical Addresses Ethernet uses a 6-byte (48 bits, 12 hexadecimal digits) physical address, like 07:01:02:01:2C:4B 28 MAC Addresses Every Ethernet interface (NIC) has a 6-byte physical address, also called MAC address (Media Access Control) or hardware address, which is assigned and burned into hardware when it is manufactured. MAC address of every Ethernet device is guaranteed to be globally unique. Identifies some destination device on the same LAN. Cannot identify destination device across any router. It is a local address. 29 How do you find your MAC address? • • By running “ipconfig /all” in a command window Output from ipconfig /all 30 Is MAC Address all we need? The MAC address provides the physical address for the network interface card, but provides no information about its network location what LAN, which building, city, or even the country in which the network resides IP addressing provides a solution to worldwide addressing. 31 IP addresses An internet address in IPv4 is a 4 byte global address, separated by decimals (dotted decimal notation), such as 132.24.75.9 32 Layer 3 IP Addresses Carried in Internet Protocol header Identifies a particular host (computer), which may be on any subnet or network. It is a global address. 4 bytes, split into IP Network IP Host Stored by operating system. Assigned by: IANA, ARIN and/or ISP (Network part) Local network administrator (Host part) 33 IP Addressing Initially ‘classful’ We will discuss Classless (CIDR) addressing later 34 Dotted Decimal Notation Class A: Large networks Class B: Medium networks Classful IP Addresses Class C: Small networks Hostid with all 0’s or all 1’s are special. 35 00000000. 0 ……0 01111111. 1 ……1 10000000. 0 ……0 10111111. 1 ……1 11000000. 0 ……0 11011111. 1 ……1 36 Figure 5.9 Blocks in Class A Figure 5.10 Blocks in Class B Figure 5.11 Blocks in Class C 37 Figure 5.15 netid Information extraction in classful addressing 000 ... 0 First address 38 How do you find your IP address? • • By running “ipconfig /all” in a command window Output from ipconfig /all 39 Port addresses A port address is represented as a 16-bit integer, such as 80 40 Layer 4 TCP Ports Carried in TCP header Identifies a particular user/server process 2 byte port codes Well-Known Port Numbers assigned by ICANN / IANA and stored in “services” file Examples: HTTP = port 80 File Transfer (FTP) = port 21 E-mail (SMTP) = port 25 Remote login (Telnet) = port 23 41 Example: Web Browsing - I’m running Chrome on my Windows machine - I type http://www.google.com.sa and hit ENTER. WHAT HAPPENS??? 42 Web Browsing Stack My computer is running the following protocols: •- Application Layer = HTTP (Chrome) •- Transport Layer = TCP •- Network Layer = IP •- Data Link Layer = Ethernet •- Physical Layer = Ethernet 43 Relationship of layers and addresses in TCP/IP Example: web browser implementing HTTP Interface. e.g. WINSOCK on PCs Implemented in TCP and UDP software. HTTP uses TCP. e.g. TCP port 80 for web server e.g. 192.168.1.12 (32bit) Implemented in IP software e.g. Ethernet Medium Access Control (MAC) implemented in NIC card (Network Interface Card) and driver software e.g. Ethernet address (48-bit) e.g. Ethernet PHY layer. Implemented in NIC card 44