* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download How to Hack a Telecommunication Company And Stay Alive
Survey
Document related concepts
Computer network wikipedia , lookup
Deep packet inspection wikipedia , lookup
Policies promoting wireless broadband in the United States wikipedia , lookup
Net neutrality law wikipedia , lookup
Network tap wikipedia , lookup
TV Everywhere wikipedia , lookup
Computer security wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Airborne Networking wikipedia , lookup
Distributed firewall wikipedia , lookup
Wireless security wikipedia , lookup
Transcript
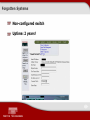
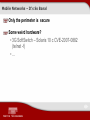
How to Hack a Telecommunication Company And Stay Alive Sergey Gordeychik Positive Technologies CTO Ic Beo Sergey Gordeychik, Positive Technologies, CTO A “script writer” and a “director” of the Positive Hack Days forum Science editor of the SecurityLab.Ru portal Author of the Web Application Security course, and a book titled A Wireless Network Security and a namesake course A participant of WASC, RISSPA http://sgordey.blogspot.com What Is It All About? What is so peculiar about telecoms? Attacks against subscribers/Attacks by subscribers Perimeter… Just a perimeter Partners and contractors Technology networks What’s So Peculiar? Specific Features of Telecommunication Companies Large, large networks Unification of various services (broadband access, Wi-Fi, hosting, mobile communication) Great number of applications and systems on the perimeter Exotics inside and outside Lots of perimeters Most networks belong to third parties Forensics nightmare How many perimeters do telecoms have? Internet Subscribers Partners Office Technology network …and a bit more… Mobile communications Broadband access Technological network Internet TV Hosting Wired broadband access Wireless broadband access VOIP Hosting ... …and a bit more… Vladivostok Moscow Roma Phnom Penh Attack AGAINST Subscribers Why Subscribers? Subscribers’ $ = telecoms’ $ DOS = - $$ - reputation - $$ PWN (100 000 PC) = Botnet Personal data! Broadband Access Huge non-segmented networks Great number of end devices: • Various SOHO devices • Installed and unattended • Standard bugs configurations A manual on insecurity of network appliances SNMP/Telnet/HTTP/UPnP control protocols in the Internet Insecure/empty passwords Web attacks on Client’s side (Pinning, CSRF) Huge number of users • 1 out of1000, for 10 000 000 = 10 000 • Trivial passwords Broadband Access. Attack Collecting information • Network scanning • Access layer error (BRAS) • Collecting information from internal forums and other resources • Self-service platform errors Invalid login or password vs Invalid username Preparing scenarios • Capturing devices • Guessing passwords $profit$ Well…yes, it happens Pick a Task… Examples of Risks Gaining access to a self-service portal • Cashout guessing password or stealing the router cfg files (vpn/pppoe) transferring money from a broadband access to a cell phone (integration!) Cashing out via PRS • It drives me NUTS!!! Guessing password or stealing the router cfg files (vpn/ppoe) Purchasing the available Balance =0 Performing a mass hacking of a router/PC Performing a mass changing of configurations Attacks against Clients of Mobile Networks Faking Caller ID •self-service portal/USSD •voice mailbox •cash-out via PRS •direct money withdrawal Internet SS7 Tech Systems SIP-GW FAKE ID Taget GSM unauthorized access Attacks against Clients of Mobile Networks Malware for mobile devices; Intercepting GSM – Not a ROCKET SCIENCE! • attacking A5/1 • MITM, switch to A5/0 • downgrading UMTS -> GSM Traffic, SMS, one-time passwords... • Self-service portals/USSD • Cash-out via PRS • Voice mailbox Hosting Local network for collocated/dedicated servers • Attacks of a network/data link layer, attacks against network infrastructure • ARP Spoofing, IP Spoofing… old school • Intrasegment IPv6 attacks Attack against infrastructure (DNS…) Shared hosting (once having intruded into one of the sites…) Pentester Tips & Tricks || || Pentester Tips & Tricks We are only searching for vulnerabilities We use only our own resources for demonstration We avoid information protected by the law A fickle client… C: Prove it! Enter the portal! P: No, thank you. Here is a password – enter it yourself… Attacks BY Subscribers Why Subscribers? AGAIN? Subscribers are WITHIN one of the perimeters Many attacks are easier if performed on subscriber’s side The number of subscribers of modern telecoms is quite large General Problems Network access control weakness Intrasegment attacks Protection of the end equipment Web applications for subscribers Network Access Control Errors A direct way does not always mean the most interesting one :) C:\>tracert -d www.ru Tracing route to www.ru [194.87.0.50] over a maximum of 30 hops: 1 3 4 * * * Request timed out. 10 ms 13 ms 5 ms 192.168.5.4 7 ms 6 ms 5 ms 192.168.4.6 Per Aspera Ad…level 15 #sh run Using 10994 out of 155640 bytes ! version 12.3 ... ! username test1 password 7 <removed> username antipov password 7 <removed> username gordey password 7 <removed> username anisimov password 7 <removed> username petkov password 7 <removed> username mitnik password 7 <removed> username jeremiah password 7 <removed> Network Access Control Errors GPRS/EDGE/3G, which traditionally stick to NAT Other clients are “invisible” This is not always true… GPRS: payment kiosks, ATMs, and etc., which can have: • A missing firewall; • Missing updates; • misconfigurations. A Joke SNMP ‘private’ on a GGSN A Joke Captive portal “Your balance is low” •Linux •Apache •MySQL •PHP Intrasegment Attacks Subscribers of broadcast access and hosting Web Portals and Services for Subscribers A good few of resources • forums, dating sites, video convertors, online games, statistics, online shopping, photo hosting, file hosting, online radio… A good few of loopholes • Old versions of applications and CMS, SQLi, LFI and so on… Single-Sign-On or the same passwords… Are often placed into the DMZ together with “ordinary” servers Web Portals and Servers for Subscribers Games server* Proxima CMS, path traversal + SQLi + configuration error= root About 20 more sites on the host • Online broadcasting • Branded desktop applications •… Pentester Tips & Tricks Resources on the subscriber networks are often SUBSCRIBER’s resources Getting approvals for every step of your work Many systems operate on a wing and a prayer They collapse all the time, but if you are online anyway… Avoiding (!) information protected by the law A fickle client… Perimeter… Just a Perimeter Perimeter? Large, large networks! •Use clouds Great number of “third-party” resources Get ready for rarities Corporate web applications The Lord of The Net Great Number of Third-Party Resources Quite a large number of perimeter hosts belong to partners/subscribers Quite often these hosts are “mixed” with those of the client Yet, they should not be disregarded • Imagine that you are already a level 15/root/admin on the host and you just entered the segment Great Number of Third-Party Resources SQLi on the mobile content portal (Oracle, sys) private at the VoIP gateway Maintained by partners No hacking Are actually located at a flat DMZ together with client’s servers Enabling the billing Front-End Rarities So many different things can be found on the perimeter • Technology “hardware” • VoIP • Old-school firewalls • Web cameras •Unusual control systems: ELOM, conditioners (!), UPS (!), etc. Keep in mind the momentous attacks (X-mas scan, UNIX RPC, Finger, and etc.) Don’t underrate the rarities Rarities nc –P 20 xxx.xxx.xxx.xxx 8080 Wireless Access Point • Insecure password for web • Enabling Telnet • Compiling tcpdump/nc and others for the platform • Using them for traffic/tunnel interception Web camera • LFI via a web interface • Obtaining configuration files • Gaining an access password for the control system • Gaining access to the control system Journey to Gattaca Watching the Video Cobweb Lots of Web. For real. Enterprise web applications are often accessible • Terminal services (Citrix) • Email systems • Helpdesk systems • Ill-equipped for operating on the “wild web” Support system We found and applied Path Traversal ManageEngine ServiceDesk Plus Gained the “encrypted” password for integration with AD The password fitted for VPN The password fitted for AD (Enterprise Admin) The password fitted for Cisco ACS So we finally got lucky! VPN Lots of VPN, good and not so good Passwords, IPSec Aggressive Mode… The Lords of the Net Administrator, the Lord of the Net A large network means many administrators Feudalism • Rules are for wimps • Enterprise IT infrastructure VS “my infrastructure” • Remote access systems • Amusing web servers and trail apps “All animals are equal but…” The Lords of the Rings TCP:1337 (SSL) – a web server of the system administration department Radio broadcasting (ShoutCast Server with a default password) Location: an administrator workstation With all the consequences… Pentester Tips & Tricks Try not to miss a thing on the perimeter Keep in mind third-party hosts Get approvals for every step of your work Don’t disregard network rarities. Sometimes a web camera can pave the way to the network core! Pay special attention to Web Remember admins Partners and Contractors Contractors? Requirements for system access (VPN) Standard accounts (in order to remember) No update management Employees Contractors… Contractor in the technology network • Wireless interface on a laptop • Everyone, a shared folder • The folder contains an installer of a control system for xDSL modems/end routers • With an in-built SA password in DBMS • Who also has the same system? Applications for agents, sale and activation of communication services package • Fat-client application • Build-in access password for DBMS • … as SYSDBA There Are Different Contractors... OMG?! HAVE I PWND THAT? Pentester Tips & Tricks Contractors are never to be hacked Get approvals for every step of your work Many scenarios can be efficiently demonstrated by a “white box” method Suppose, I were a contractor But you are not a contractor …A fickle client… Technology Networks Something special? Changes are highly dynamic in the network • New gadgets keep emerging • Contractors keep working • Configuration keeps changing Implemented components and protocols are standard • Threats typical for IP • Configuration errors • Platform vulnerabilities Some errors can cause failures and facilitate frauds Technology Networks Are Networks First of All! Equipment vulnerabilities Test systems, contractors’ systems FORGOTTEN(!) systems Network management systems Forgotten Systems Non-configured switch Uptime: 2 years! Network Management Systems Such treasure •Network topology •Device configuration •Passwords and keys for VPN/Wi-Fi/SNMP/RADIUS/VPN… “They are behind the firewall” + Web password - OS, DBMS, Web updates + Standard passwords for DBMS + File(!) shares That’s Tough! WPA-PSK for AP is found Where are the points located?!! Backup Is Quite a Useful Thing! Especially on the Net! VoIP Is a Honey Pie Call management (fraud) Identity theft Access to the enterprise network VoIP Attack against… infrastructure gateways protocols i[P]Phone Fraud or fraudulent mispresentation Wiretapping And more… VoIP 1. VoIP Wi-Fi access (No WPA, so “slow”) 2. The nearest CISCO Call Manager a) SQLi, CVE-2008-0026 https://www.example.org/ccmuser/personaladdressbookEdit.do?key='+UNION+ALL+SELECT+'','','',user,'',password+from+app licationuser;-- b) Collecting hash runsql select user,password from applicationuser c) Restoring passwords from the hash Компьютер нарушителя 1 3. Level 15 for the whole network WEP ТОП 2 ТОП Вне офиса Компании «А» КЛВС PSTN IP PBX Компания «А» 3 SQL injection CVE-2008-0026 Mobile Networks – It’s So Banal Only the perimeter is secure Some weird hardware? • 3G SoftSwitch – Solaris 10 с CVE-2007-0882 (telnet -f) •… Self-Service Platform WEB/USSD/WAP Interface with payment systems A possibility of money withdrawal No authentication (Caller ID) Weak authentication (PIN-код?) Vulnerable applications (Web, SQL Injection, XSS) VAS platforms Someone’s application on the operator’s network Malicious content, WAP-provisioning Rich access via mobile stations (WAP/HTTP): • Web application vulnerabilities • Platform vulnerabilities Platforms for service development Instead of a Conclusion Forensic Nightmare Large networks make it extremely difficult to investigate incidents Lots of vectors, tons of hardware, a great deal of administrators A couple of hops on the internal network, and no one will make head or tail of it Who is there? Trying To Make Head or Tail… Some Are Concerned… Others Are Happy Thank you for your attention! Sergey Gordeychik [email protected] http://sgordey.blogspot.com http://ptresearch.blogspot.com http://phdays.com