* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download network
Survey
Document related concepts
Net neutrality wikipedia , lookup
Net neutrality law wikipedia , lookup
Deep packet inspection wikipedia , lookup
Network tap wikipedia , lookup
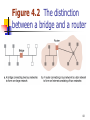
Wake-on-LAN wikipedia , lookup
Airborne Networking wikipedia , lookup
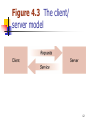
Computer network wikipedia , lookup
Distributed firewall wikipedia , lookup
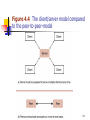
Internet protocol suite wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Transcript
Chapter 4 Networking and the Internet Chapter 4: Networking and the Internet 4.1 4.2 4.3 4.4 4.5 Network Fundamentals The Internet The World Wide Web Network Protocols Security 2 Network classifications Networks--Isolated computers can be connected to work together via networking. Classifications Local area network (LAN) --on a single building or a group of buildings. Such as university campus, a manufacture plant, or the like. Wide area network (WAN)—one LANs can be connected to other LANs over any distance through telephone lines or radio waves. Such as city. 3 Network classifications Closed, or proprietary--held by an individual corporation like Novell networks. Open--networks have the ownership in the public domain like the Internet 4 Network classifications Characteristics of Network Topology—The geometric arrangement. Protocols:The rules and encoding specifications for sending data. Media---Devices are connected by twisted-pair wire, coaxial cables, or fiber optics, or radio waves. 5 Network topologies Ring Bus Star Irregular 6 Figure 4.1 Network topologies 7 Figure 4.1 Network topologies (cont’d) 8 Connecting networks Networked computers can be connected in a hierarchical fashion as an internet. DARPA (Defense Advanced Research Projects Agency) initiated the Internet in 1973. Interconnection of networks are achieved through routers or proprietary gateways(earlier terms for routers). Bridge: connects two compatible networks Router: connects two incompatible networks Resulting “network” is called an internet 9 Figure 4.2 The distinction between a bridge and a router 10 Inter-process communication Clients: a client makes requests to servers. Servers: a server performs the service and sends replies back to the client (s). Ex:A machine with high-capacity disk drive contains all the records of other machine (servers, the others—clients) 11 Figure 4.3 The client/ server model 12 Inter-process communication Inside the same machine, or among the machines over the networks. Client-server One server, many clients Server must execute continuously Client initiates communication Peer-to-peer Two processes communicating as equals 13 Figure 4.4 The client/server model compared to the peer-to-peer-model 14 Distributed systems Systems with parts that run on different computers Multiple independent computers communicating over a network to accomplish a common task Infrastructure usually provided by standardized toolkits Example: Enterprise Java Beans from Sun Microsystems Example: .NET framework from Microsoft 15 1. Which of the following is not a way of classifying networks? A. WAN versus LAN C. Router versus bridge B. Closed versus open D. Star versus bus ANSWER: 2 Which of the following is not a means of performing interprocess communication over a network? A. Client/server B. ICANN C. Peer-to-peer ANSWER: 16 The Internet The Internet: one internet spanning the world Started by DARPA in 1973 Today involves millions of machines 17 Internet Architecture Domain = network or internet controlled by one organization Gateway = router connecting a domain to the cloud cloud = the rest of the internet Domains must be registered by their owners Internet Corporation for Assigned Names & Numbers (ICANN) serves as registrar 18 Figure 4.5 A typical approach to connecting to the Internet 19 Strategies for connecting to the Internet Large organization: buy a direct connection Small organization or individual: link domain to the domain of an ISP ISP = Internet Service Provider Individual: temporarily link computer into ISP’s domain 20 Internet Addressing: IP Addresses IP address = 32 bit identifier for a machine Network identifier = part assigned by ICANN Host address = part assigned by domain owner Dotted decimal notation = standard for displaying IP addresses Example: 192.207.177.133 21 Internet addressing: host names Host name = mnemonic name Example: mymachine.aw.com Domain name = part assigned by a registrar Example: aw.com Top level domain = classification of domain owner By usage – Example: .com = commercial By country – Example: .au = Australia Subdomains and individual machine names Assigned by domain owner Domain owner must run a name server . 22 Connecting networks InterNIC(Internet Network Information Center) regulates the 32-bit address of domains and thus each machine= network identifier (x-bit) + host address (32–x -bit). The network identifier of the mnemonic domain name“nthu.edu.tw” is “140.114” determined globally, while “nyx.cc”is “63.1”assigned locally by the Computer Center of NTHU.⇒ The host machine “nyx.cc.nthu.edu.tw”has an address “140.114.63.1”. 23 Internet applications Electronic main (e-mail) File Transfer Protocol (FTP) Remote login: telnet, etc. World Wide Web 24 Electronic mail Mail server: set up by domain owner Mail sent from domain members goes through mail server Mail sent to domain members is collected by mail server 25 If the network identifier of a domain in the Internet is 115.48, how many unique IP addresses are available for identifying machines within the domain? A. 4096 B. 16,384 C. 32,768 D. 65,536 . Which of the following is not an application of the Internet? A. FTP B. Email C. Telnet D. RING 26 World Wide Web Atop the Internet, the WWW allows the propagation of multimedia documents. --The hypermedia documents consists of hypertexts: texts, audiovisual contents, links. Server disseminates hypertext (or hypermedia) documents Web site = all hypertext documents controlled by one organization or individual Usually all at same internet address HTML = language of hypertext documents Other content can also be disseminated Example: images 27 World Wide Web implementation Web server: provides access to documents on its machine as requested Browser: allows user to access web pages Hypertext Transfer Protocol (HTTP): communication protocol used by browsers and web servers Uniform Resource Locator (URL): unique address of a document on the web 28 Figure 4.6 A typical URL 29 Hypertext document format Entire document is printable characters Contains tags to control display Display appearance Links to other documents and content Dynamic functions 30 Figure 4.7 A simple Web page 31 Figure 4.7 A simple Web page (cont’d) 32 Figure 4.8 An enhanced simple Web page 33 Figure 4.8 An enhanced simple Web page (cont’d) 34 Extensible Markup Language (XML) XML: a language for constructing markup languages similar to HTML A descendant of SGML(Standard Generalized Markup Language) For math, multimedia, music and Web pages 35 Figure 4.9 The first two bars of Beethoven’s Fifth Symphony 36 Dynamic web pages(i.e. search) Client-side(specifies topic of interest) Examples: java applets, java script, Macromedia Flash Server-side(identifying documents) Common Gateway Interface (CGI) Servlets—allow clients to execute programs units in servers PHP(personal home page) 37 Network protocols: transmission control Token ring: one-way communication around ring network Ethernet: Uses carrier sense, multiple access with collision detection (CSMA/CD) Popular for bus networks Like a conversation in small group 38 Figure 4.10 Communication over a ring network 39 Figure 4.11 Communication over a bus network 40 Figure 4.12 Package-shipping example 41 Figure 4.13 The Internet software layers 42 Figure 4.14 Following a message through the Internet 43 Internet software layers Application layer: Example: browser Transport layer: TCP/IP, UDP Network layer: handles routing through the internet Link layer: handles actual transmission of packets Token ring or Ethernet 44 Delivery of messages The transport layer takes the message from the application layer, packages them with additional tags (50+bytes including sequence #, …) into packets of a size compatible with the beneath network layer, and hands over to the network layer. The network layer will properly forward these packets to the very network specified by the application layer. The same prefix of both addresses ⇔on the same network. Different ⇒the network layer appending the address of a router in the current network sends the packets to that router. (maybe, intermediate routers) The link layer does the actual transmission between machines and routers by local addressing system with additional wrapping. ⇒striped off at the message destination. 45 TCP/IP Protocol Suite It is the network layer to determine the destination of the next hop (network). The routing table in the network layer contains the final destination addresses and intermediate addresses. [NAT: IP address vs. Link address] The information in this table routinely exchanges and propagate through the Internet. Packets of the same message may travel along different paths. Once all packets of the message are received (using sequence #), the target transport layer hands it over to its application layer. [complete delivery] The response time of the Internet is rather instant in milliseconds. 46 TCP/IP Protocol Suite The TCP/IP protocol suite defines a collection of protocols beside TCP and IP. IP(Internet Protocol) defines the network layer service. --Hop count, TTL (time to live, 64): decrement per hop forwarding, avoiding circling. TCP(Transmission Control Protocol) defines a reliable transport service. --Two ends first build an acknowledged connection and confirms each subsequent packet delivery in sequence. UDP(User Datagram Protocol) defines a more efficient but less reliable transport service. One end sends the data merely to the destination address regardless of its reception. ISO (International Organization for Standardization) develops the OSI (Open System Interconnection) reference model using 7 layers – Application, Presentation, Session, Transport, Network, Data Link, & Physical. 47 Figure 4.15 Choosing between TCP and UDP 48 Which layer of the TCP/IP hierarchy actually transmits a message? A. Application B. Transport C. Network D. Link Which layer of the TCP/IP hierarchy chops messages into units whose size is compatible with the Internet? A. Application B. Transport C. Network D. Link Which layer of the TCP/IP hierarchy decides the direction in which message segments are transferred across the Internet? A. Application B. Transport C. Network D. Link Which layer of the TCP/IP hierarchy presents incoming messages to the computer user? A. Application B. Transport C. Network D. Link 49 Network security Connecting to the networks, a machine becomes accessible to the general public. Unauthorized access: attack on confidentiality. Protection on personal information Vandalism: malicious acts from hackers, computer viruses, or network worms. Computer Virus—a program segment that attaches itself to other programs in computer systems. Worms—an autonomous program that transfers itself through a network, taking up residence in machines and forwarding copies of itself through network. 50 Network security Privacy of communication Public-key encryption Public key and private key: (asymmetric) A and B each have pairs of public key and private key: PA, pA, and PB, pB. --Private keys are held by individuals, while public keys are known to the party. Authenticated receiver: (only B has pB to decrypt the received data) Authenticated sender: (only A has pA to send that encrypted data) 51 Network security Integrity of machine exposed to internet Attacks: viruses and worms Defense: firewall Firewall software that filters the traffic entering or passing through a machine(network layer to reject traffics from an entire domain or a specific IP) 52 The primary purpose of which of the following is not the enhancement of security? A. ICANN key B. Firewall C. Encryption D. Public Which of the following is not a means of referencing entities on the Internet? A. URL Host address B. IP address C. Anonymous FTP D. 53