* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Configuring IP Routing
Survey
Document related concepts
Parallel port wikipedia , lookup
Point-to-Point Protocol over Ethernet wikipedia , lookup
Network tap wikipedia , lookup
Airborne Networking wikipedia , lookup
Computer network wikipedia , lookup
Spanning Tree Protocol wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
Serial digital interface wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Wake-on-LAN wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Virtual LAN wikipedia , lookup
Routing in delay-tolerant networking wikipedia , lookup
Transcript
Part No. 321712-B Rev 03
June 2006
4655 Great America Parkway
Santa Clara, CA 95054
Configuring IP Routing and
Multicast Operations using
Device Manager
Ethernet Routing Switch 1600 Series, Software
Release 2.1
*321712-B* Rev 03
2
Copyright © 2005-2006 Nortel Networks. All rights reserved.
The information in this document is subject to change without notice. The statements, configurations, technical data, and
recommendations in this document are believed to be accurate and reliable, but are presented without express or implied
warranty. Users must take full responsibility for their applications of any products specified in this document. The
information in this document is proprietary to Nortel Networks.
The software described in this document is furnished under a license agreement and may be used only in accordance
with the terms of that license. The software license agreement is included in this document.
Trademarks
*Nortel, Nortel Networks, the Nortel logo, and the Globemark are trademarks of Nortel Networks.
All other products or services may be trademarks, registered trademarks, service marks, or registered service marks of
their respective owners.
The asterisk after a name denotes a trademarked item.
Restricted rights legend
Use, duplication, or disclosure by the United States Government is subject to restrictions as set forth in subparagraph
(c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013.
Notwithstanding any other license agreement that may pertain to, or accompany the delivery of, this computer software,
the rights of the United States Government regarding its use, reproduction, and disclosure are as set forth in the
Commercial Computer Software-Restricted Rights clause at FAR 52.227-19.
Statement of conditions
In the interest of improving internal design, operational function, and/or reliability, Nortel Networks reserves the right to
make changes to the products described in this document without notice.
Nortel Networks does not assume any liability that may occur due to the use or application of the product(s) or circuit
layout(s) described herein.
Portions of the code in this software product may be Copyright © 1988, Regents of the University of California. All
rights reserved. Redistribution and use in source and binary forms of such portions are permitted, provided that the above
copyright notice and this paragraph are duplicated in all such forms and that any documentation, advertising materials,
and other materials related to such distribution and use acknowledge that such portions of the software were developed
by the University of California, Berkeley. The name of the University may not be used to endorse or promote products
derived from such portions of the software without specific prior written permission.
SUCH PORTIONS OF THE SOFTWARE ARE PROVIDED “AS IS” AND WITHOUT ANY EXPRESS OR IMPLIED
WARRANTIES, INCLUDING, WITHOUT LIMITATION, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE.
In addition, the program and information contained herein are licensed only pursuant to a license agreement that contains
restrictions on use and disclosure (that may incorporate by reference certain limitations and notices imposed by third
parties).
Nortel Networks software license agreement
This Software License Agreement (“License Agreement”) is between you, the end-user (“Customer”) and Nortel
Networks Corporation and its subsidiaries and affiliates (“Nortel Networks”). PLEASE READ THE FOLLOWING
321712-B Rev 03
3
CAREFULLY. YOU MUST ACCEPT THESE LICENSE TERMS IN ORDER TO DOWNLOAD AND/OR USE THE
SOFTWARE. USE OF THE SOFTWARE CONSTITUTES YOUR ACCEPTANCE OF THIS LICENSE
AGREEMENT. If you do not accept these terms and conditions, return the Software, unused and in the original shipping
container, within 30 days of purchase to obtain a credit for the full purchase price.
“Software” is owned or licensed by Nortel Networks, its parent or one of its subsidiaries or affiliates, and is copyrighted
and licensed, not sold. Software consists of machine-readable instructions, its components, data, audio-visual content
(such as images, text, recordings or pictures) and related licensed materials including all whole or partial copies. Nortel
Networks grants you a license to use the Software only in the country where you acquired the Software. You obtain no
rights other than those granted to you under this License Agreement. You are responsible for the selection of the
Software and for the installation of, use of, and results obtained from the Software.
1. Licensed Use of Software. Nortel Networks grants Customer a nonexclusive license to use a copy of the Software
on only one machine at any one time or to the extent of the activation or authorized usage level, whichever is applicable.
To the extent Software is furnished for use with designated hardware or Customer furnished equipment (“CFE”),
Customer is granted a nonexclusive license to use Software only on such hardware or CFE, as applicable. Software
contains trade secrets and Customer agrees to treat Software as confidential information using the same care and
discretion Customer uses with its own similar information that it does not wish to disclose, publish or disseminate.
Customer will ensure that anyone who uses the Software does so only in compliance with the terms of this Agreement.
Customer shall not a) use, copy, modify, transfer or distribute the Software except as expressly authorized; b) reverse
assemble, reverse compile, reverse engineer or otherwise translate the Software; c) create derivative works or
modifications unless expressly authorized; or d) sublicense, rent or lease the Software. Licensors of intellectual property
to Nortel Networks are beneficiaries of this provision. Upon termination or breach of the license by Customer or in the
event designated hardware or CFE is no longer in use, Customer will promptly return the Software to Nortel Networks or
certify its destruction. Nortel Networks may audit by remote polling or other reasonable means to determine Customer’s
Software activation or usage levels. If suppliers of third party software included in Software require Nortel Networks to
include additional or different terms, Customer agrees to abide by such terms provided by Nortel Networks with respect
to such third party software.
2. Warranty. Except as may be otherwise expressly agreed to in writing between Nortel Networks and Customer,
Software is provided “AS IS” without any warranties (conditions) of any kind. NORTEL NETWORKS DISCLAIMS
ALL WARRANTIES (CONDITIONS) FOR THE SOFTWARE, EITHER EXPRESS OR IMPLIED, INCLUDING,
BUT NOT LIMITED TO THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE AND ANY WARRANTY OF NON-INFRINGEMENT. Nortel Networks is not obligated to
provide support of any kind for the Software. Some jurisdictions do not allow exclusion of implied warranties, and, in
such event, the above exclusions may not apply.
3. Limitation of Remedies. IN NO EVENT SHALL NORTEL NETWORKS OR ITS AGENTS OR SUPPLIERS BE
LIABLE FOR ANY OF THE FOLLOWING: a) DAMAGES BASED ON ANY THIRD PARTY CLAIM; b) LOSS OF,
OR DAMAGE TO, CUSTOMER’S RECORDS, FILES OR DATA; OR c) DIRECT, INDIRECT, SPECIAL,
INCIDENTAL, PUNITIVE, OR CONSEQUENTIAL DAMAGES (INCLUDING LOST PROFITS OR SAVINGS),
WHETHER IN CONTRACT, TORT OR OTHERWISE (INCLUDING NEGLIGENCE) ARISING OUT OF YOUR
USE OF THE SOFTWARE, EVEN IF NORTEL NETWORKS, ITS AGENTS OR SUPPLIERS HAVE BEEN
ADVISED OF THEIR POSSIBILITY. The foregoing limitations of remedies also apply to any developer and/or supplier
of the Software. Such developer and/or supplier is an intended beneficiary of this Section. Some jurisdictions do not
allow these limitations or exclusions and, in such event, they may not apply.
4.
General
a.
If Customer is the United States Government, the following paragraph shall apply: All Nortel Networks
Software available under this License Agreement is commercial computer software and commercial computer
software documentation and, in the event Software is licensed for or on behalf of the United States
Government, the respective rights to the software and software documentation are governed by Nortel
Networks standard commercial license in accordance with U.S. Federal Regulations at 48 C.F.R. Sections
12.212 (for non-DoD entities) and 48 C.F.R. 227.7202 (for DoD entities).
Configuring IP Routing and Multicast Operations using Device Manager
4
b.
Customer may terminate the license at any time. Nortel Networks may terminate the license if Customer fails
to comply with the terms and conditions of this license. In either event, upon termination, Customer must
either return the Software to Nortel Networks or certify its destruction.
c.
Customer is responsible for payment of any taxes, including personal property taxes, resulting from
Customer’s use of the Software. Customer agrees to comply with all applicable laws including all applicable
export and import laws and regulations.
d.
Neither party may bring an action, regardless of form, more than two years after the cause of the action arose.
e.
The terms and conditions of this License Agreement form the complete and exclusive agreement between
Customer and Nortel Networks.
f.
This License Agreement is governed by the laws of the country in which Customer acquires the Software. If
the Software is acquired in the United States, then this License Agreement is governed by the laws of the state
of New York.
321712-B Rev 03
5
Contents
Preface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
Before You Begin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
Text Conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Related information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Publications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
How to get help . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Finding the latest updates on the Nortel web site . . . . . . . . . . . . . . . . . . . . . . . . . 26
Getting help from the Nortel web site . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Getting help over the phone from a Nortel Solutions Center . . . . . . . . . . . . . . . . . 26
Getting help from a specialist using an Express Routing Code . . . . . . . . . . . . . . . 27
Getting help through a Nortel distributor or reseller . . . . . . . . . . . . . . . . . . . . . . . . 27
Chapter 1: IP routing and multicast concepts. . . . . . . . . . . . . . . . . . . . . . . 29
Overview of IP routing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
IP addressing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Subnet addressing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Supernet addressing and CIDR . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Virtual routing between VLANs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
Static routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
Black hole static routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Alternative routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
IP filtering and route policies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38
Accept policies (in filters) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
Announce policies (out filters) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
Prefix list . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
Per-VLAN routing control . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
BootP/DHCP relay . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Differences between DHCP and BootP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Summary of DHCP relay operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Configuring IP Routing and Multicast Operations using Device Manager
6 Contents
Forwarding DHCP packets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
Multiple BootP/DHCP servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
Address Resolution Protocol (ARP) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
Routing Information Protocol (RIP) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
RIP operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
RIP metrics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
Limitations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
Virtual Router Redundancy Protocol (VRRP) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
VLAN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
Initializing VRRP routers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
Basic VRRP configuration steps . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
Configuring the virtual router master . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
Configuring the virtual router backup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
Enabling the switches . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
Critical IP address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
VRRP and Split-MLT . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
Open Shortest Path First (OSPF) Protocol . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
Benefits . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
OSPF routing algorithm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
Autonomous system and areas . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
Backbone area . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
Stub area . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
Neighbors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
Neighbor adjacencies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
OSPF routers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
Router types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
OSPF interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
OSPF and IP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59
OSPF packets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59
Link state advertisements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 60
AS external routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 61
OSPF virtual links . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 61
Specifying ASBRs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 62
Circuitless IP (CLIP) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63
321712-B Rev 03
Contents
7
UDP forwarding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64
Overview of IP multicast . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 65
Multicast addresses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
IP Multicast address ranges . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
IP to Ethernet multicast MAC mapping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 68
Internet Group Management Protocol (IGMP) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 71
IGMP queries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
IGMP host reports . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
Host leave messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 73
Fast-leave feature . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 73
IGMP Snoop . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 73
Static mrouter port and non-querier . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 74
IGMP proxy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 75
IGMP versions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 75
IGMP RFCs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 77
Protocol Independent Multicast-Sparse Mode (PIM-SM) . . . . . . . . . . . . . . . . . . . . . . . 77
PIM-SM concepts and terminology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 78
Hosts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 78
PIM-SM domain . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 78
Designated router (DR) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
Rendezvous-Point (RP) router . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
Bootstrap router . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
Shared trees and shortest-path trees . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
Shared trees . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
Shortest-path trees . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
Join/prune messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82
Register and register-stop messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82
Receiver joining group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82
Receiver leaving group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
Source sending packets to group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
Required elements for PIM-SM operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84
PIM-SM simplified example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
PIM-SM static source groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Multicast access control feature . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Multicast access control policy types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Configuring IP Routing and Multicast Operations using Device Manager
8 Contents
denyRX . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
denyBoth . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
Specifying host addresses and masks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
Multicast MAC filtering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 90
Chapter 2: Configuring IP Routing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 91
Router Interface Types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 91
Assigning an IP Address to a Virtual Routing Port . . . . . . . . . . . . . . . . . . . . . . . . 92
Globally Enabling IP Routing Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 94
Enabling IP Forwarding Globally . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 94
Enabling Alternative Routes Globally . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
Alternative Routes Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
Globally Enabling Alternative Routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 97
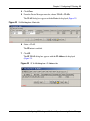
IP Router Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 97
Configuring the Router IP Protocol Stack . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 98
Viewing IP Address Router Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 98
Managing the System Routing Table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 99
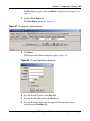
IP Static Route Table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101
Creating IP Static Routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
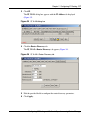
Creating a Static Default Route . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
Creating a Black Hole Static Route . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 106
Deleting a Static Route . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 107
Configuring CLIP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
Creating a CLIP interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
Enabling OSPF on a CLIP interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
Enabling PIM on a CLIP interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 110
Deleting a CLIP Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
Configuring IP Route Preferences . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 112
Configuring ICMP Router Discovery . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
Enabling ICMP Router Discovery Globally . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
Viewing the ICMP Router Discovery Table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
Configuring Router Discovery on a VLAN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
Chapter 3: Configuring ARP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
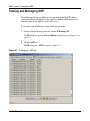
Viewing and Managing ARP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
Static ARP Entries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
321712-B Rev 03
Contents
9
IP, VLAN—ARP tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
Chapter 4: Configuring BootP/DHCP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 125
BootP/DHCP relay . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 125
Configuring BootP/DHCP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 125
Chapter 5: Configuring IP Policies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 129
Configuring the Prefix List . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 130
Creating and Editing a Route Policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 132
Configuring Policy Application . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
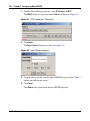
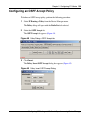
Configuring an OSPF Accept Policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
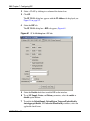
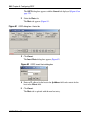
Configuring an OSPF Redistribution Policy
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 140
Configuring Filtering Policies on a RIP Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . 142
Deleting Filtering Policies on a RIP Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 144
Chapter 6: Configuring VRRP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147
Configuration Prerequisites . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 148
Enabling VRRP Globally . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 148
Configuring VRRP for the Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149
Configuring VRRP Secondary Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 152
Configuring VRRP on a VLAN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 154
Viewing VRRP Interface Statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 157
Configuring the Fast Advertisement Interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 159
Configuring the Fast Advertisement Interval on a VLAN . . . . . . . . . . . . . . . . . . . 159
Chapter 7: Configuring RIP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 161
Enabling and Configuring Global RIP Parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
Enabling and Configuring RIP on a VLAN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 165
RIP Supply and Listen Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 170
RIP Versioning Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 170
RIP Send Modes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
RIP Interface Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
Viewing RIP Statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
Chapter 8: Configuring OSPF . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 177
Viewing General OSPF Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 178
Configuring IP Routing and Multicast Operations using Device Manager
10 Contents
Enabling or Disabling OSPF on a Router . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 180
Manually Initiating an SPF Run . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 181
Configuring OSPF Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182
Viewing OSPF Interface Information
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182
Creating an OSPF Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 185
Changing an OSPF Interface Type . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
Configuring OSPF NBMA Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 188
Adding NBMA Neighbors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 189
Viewing OSPF Neighbor Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 190
Managing an OSPF VLAN interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 191
Assigning an IP address to a VLAN Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . 192
Configuring OSPF on a VLAN interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 193
Graphing OSPF Interface Statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 194
Managing OSPF Area Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 197
Viewing OSPF Area Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 199
Creating a Stub Area or NSSAs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 200
Creating a Virtual Link . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 201
Managing an Automatic Virtual Link . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 201
Configuring a Manual Virtual Link . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 202
Viewing Virtual Links on Neighboring Devices . . . . . . . . . . . . . . . . . . . . . . . . . . 204
Configuring Router Hosts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 205
Specifying ASBRs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 207
Configuring Metric Speed . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 208
Configuring Global Default Metric Speed . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 208
Managing Metrics with the Peer Layer Interface . . . . . . . . . . . . . . . . . . . . . . . . . 208
Viewing Stub Area Metrics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 210
Viewing Advertisements in the link state database . . . . . . . . . . . . . . . . . . . . . . . . . . 211
Viewing the External Link State Database . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 212
Inserting OSPF Area Aggregate Ranges . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 213
Configuring an OSPF Redistribution Policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 216
Chapter 9: Configuring UDP Forwarding. . . . . . . . . . . . . . . . . . . . . . . . . . 219
Creating UDP Protocol Entries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 219
Configuring Forwarding Entries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 221
Creating UDP Forwarding Policies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 223
321712-B Rev 03
Contents
11
Applying UDP Forwarding Policies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 225
Chapter 10: Configuring IGMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 227
Configuring IGMP on a VLAN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 227
IGMP Snooping on a VLAN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 230
Enabling IGMP Snooping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 230
Global IGMP Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 231
Viewing IGMP Cache Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 231
IGMP Interface Table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 233
Multicast Router . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 236
Viewing IGMP Snoop Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 238
Viewing IGMP Dynamic Group Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 240
IGMP Static Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 241
Multicast Access Control Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 243
Viewing IGMP Sender Entries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 245
Chapter 11: Configuring Multicast MAC Filtering . . . . . . . . . . . . . . . . . . . 247
Configuring Layer 2 Multicast MAC Filtering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 248
Chapter 12: Configuring PIM-SM . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 251
Configuration Prerequisites . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 252
Enabling PIM-SM Globally . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 252
Enabling PIM on a VLAN Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 255
Viewing and Editing PIM Interface parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 257
Viewing PIM-SM Neighbor Parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 259
Viewing RP Set Parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 260
Configuring a Candidate RP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 261
Viewing the Current Bootstrap Router (BSR) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 263
Chapter 13: Configuring Multicast Routes . . . . . . . . . . . . . . . . . . . . . . . . 265
Viewing Route Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 265
Viewing Next Hop Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 266
Viewing and Editing Interface Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 268
Configuring Static Source Groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 268
Configuration Considerations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 269
Viewing and Editing Static Source Groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 270
Configuring IP Routing and Multicast Operations using Device Manager
12 Contents
Adding a Static Source Group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 271
Deleting a Static Source Group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 271
Troubleshooting Multicast Routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 272
Prunes Dialog . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 273
Sources dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 274
Egress VLANs dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 275
Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 277
321712-B Rev 03
13
Figures
Figure 1
Network and host boundaries in IP address classes . . . . . . . . . . . . . . . . 31
Figure 2
Class C address supernet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Figure 3
IP Routing Between VLANs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
Figure 4
DHCP operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
Figure 5
Forwarding DHCP packets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
Figure 6
Configuring multiple BootP/DHCP servers . . . . . . . . . . . . . . . . . . . . . . . . 42
Figure 7
Hop count or metric in RIP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
Figure 8
VRRP Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
Figure 9
VRRP Configuration with Split-MLT . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
Figure 10
Virtual link between ABRs through a transit area . . . . . . . . . . . . . . . . . . . 61
Figure 11
CLIP (loopback) Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63
Figure 12
Multicast distribution tree . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66
Figure 13
Multicast IP address to MAC address mapping . . . . . . . . . . . . . . . . . . . . 69
Figure 14
Static mrouter port and non-querier . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 74
Figure 15
IGMPv1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 76
Figure 16
IGMPv2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 76
Figure 17
Shared tree and shortest-path tree . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
Figure 18
PIM-SM simplified example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86
Figure 19
Data flow using denyRX policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
Figure 20
Data flow using denyBoth policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
Figure 21
IP dialog box—Globals tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 92
Figure 22
VLAN dialog box—Basic tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
Figure 23
IP, VLAN dialog box—IP Address tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
Figure 24
IP, VLAN, Insert IP Address dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . 94
Figure 25
IP dialog box—Addresses tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 98
Figure 26
IP dialog box—Routes tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
Figure 27
IP dialog box—Static Routes tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
Figure 28
IP, Insert Static Routes dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
Figure 29
IP dialog box—Circuitless IP tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
Configuring IP Routing and Multicast Operations using Device Manager
14 Figures
Figure 30
IP, Insert Circuitless dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
Figure 31
Circuitless OSPF dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 110
Figure 32
Circuitless PIM dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
Figure 33
IP dialog box—Route Preference tab . . . . . . . . . . . . . . . . . . . . . . . . . . . 113
Figure 34
IP dialog box—Router Discovery tab . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
Figure 35
IP, VLAN dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
Figure 36
IP, VLAN—Router Discovery tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
Figure 37
IP dialog box—ARP tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
Figure 38
IP, Insert ARP dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 122
Figure 39
IP, Insert ARP, VLAN port selection dialog box . . . . . . . . . . . . . . . . . . . . 122
Figure 40
IP, VLAN dialog box—ARP tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
Figure 41
DHCP dialog box—Globals tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 126
Figure 42
Insert Globals dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 126
Figure 43
Policy dialog box—Prefix List tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 131
Figure 44
Policy, Insert Prefix List dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 131
Figure 45
Policy dialog box—Route Policy tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . 133
Figure 46
Policy, Insert Route Policy dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
Figure 47
Policy Dialog—Applying Policy tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
Figure 48
Policy Dialog—OSPF Accept tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
Figure 49
Policy, Insert OSPF Accept Dialog . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
Figure 50
Policy Dialog—OSPF Redistribute tab . . . . . . . . . . . . . . . . . . . . . . . . . . 141
Figure 51
Policy, Insert OSPF Redistribute dialog box . . . . . . . . . . . . . . . . . . . . . . 141
Figure 52
Policy dialog box—RIP In/Out Policy tab . . . . . . . . . . . . . . . . . . . . . . . . 143
Figure 53
VRRP dialog box—Globals tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 148
Figure 54
VRRP dialog box—Interface tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149
Figure 55
VRRP dialog box—Secondary Feature tab . . . . . . . . . . . . . . . . . . . . . . 152
Figure 56
VLAN dialog box—Basic tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 154
Figure 57
IP, VLAN dialog box—VRRP tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155
Figure 58
IP, VLAN, Insert VRRP dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155
Figure 59
VRRP Stats dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 158
Figure 60
RIP dialog box—Globals tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
Figure 61
IP, VLAN dialog box—RIP tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 166
Figure 62
RIP dialog box—Interface tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
Figure 63
RIP dialog box—Interface Advance tab . . . . . . . . . . . . . . . . . . . . . . . . . 173
Figure 64
RIP dialog box—Status tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
321712-B Rev 03
Figures
Figure 65
15
OSPF dialog box—General tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 178
Figure 66
Force SPF run dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 181
Figure 67
OSPF dialog box—Interfaces tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 183
Figure 68
OSPF Insert Interfaces dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 186
Figure 69
Neighbors tab—NBMA manually-configured neighbors . . . . . . . . . . . . . 187
Figure 70
OSPF dialog box—Neighbors tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 189
Figure 71
OSPF, Insert Neighbors dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 190
Figure 72
VLAN dialog box—Basic tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 192
Figure 73
VLAN dialog box—IP Address tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 192
Figure 74
VLAN, Insert IP Address dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . . 193
Figure 75
VLAN dialog box—OSPF tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 194
Figure 76
OSPF Stats Default dialog . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 196
Figure 77
OSPF dialog box—Areas tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 199
Figure 78
OSPF dialog box—Virtual If tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 202
Figure 79
OSPF, Insert Virtual If dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 203
Figure 80
OSPF dialog box—Virtual Neighbor tab . . . . . . . . . . . . . . . . . . . . . . . . . 205
Figure 81
OSPF dialog box—Hosts tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 206
Figure 82
OSPF, Insert Hosts dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 206
Figure 83
OSPF dialog box—If Metrics tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 209
Figure 84
OSPF dialog box—Stub Area Metrics tab . . . . . . . . . . . . . . . . . . . . . . . 210
Figure 85
OSPF dialog box—Link State Database tab . . . . . . . . . . . . . . . . . . . . . . 211
Figure 86
OSPF dialog box—Ext. Link State DB tab . . . . . . . . . . . . . . . . . . . . . . . 212
Figure 87
OSPF dialog box—Area Aggregate tab . . . . . . . . . . . . . . . . . . . . . . . . . 214
Figure 88
OSPF, Insert Area Aggregate dialog box . . . . . . . . . . . . . . . . . . . . . . . . 214
Figure 89
Policy dialog box—Redistribute tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . 217
Figure 90
Policy, Insert OSPF Redistribute dialog box . . . . . . . . . . . . . . . . . . . . . . 217
Figure 91
UdpForwarding dialog box—Protocols tab . . . . . . . . . . . . . . . . . . . . . . . 220
Figure 92
UdpForwarding, Insert Protocol dialog box . . . . . . . . . . . . . . . . . . . . . . . 220
Figure 93
UdpForwarding dialog box—Forwardings tab . . . . . . . . . . . . . . . . . . . . . 221
Figure 94
UdpForwarding, Insert Forwardings dialog box . . . . . . . . . . . . . . . . . . . 222
Figure 95
UdpForwarding dialog box—Forwarding Lists tab . . . . . . . . . . . . . . . . . 223
Figure 96
UdpForwarding, Insert Forwarding Lists dialog box . . . . . . . . . . . . . . . . 224
Figure 97
UdpForwarding dialog box—Broadcast Interfaces tab . . . . . . . . . . . . . . 225
Figure 98
UdpForwarding, Insert Broadcast Interfaces dialog box . . . . . . . . . . . . . 225
Figure 99
IP, VLAN dialog box—IGMP tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 228
Configuring IP Routing and Multicast Operations using Device Manager
16 Figures
Figure 100 IGMP dialog box—Global tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 231
Figure 101 IGMP dialog box—Global tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 232
Figure 102 IGMP dialog box—Cache tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 233
Figure 103 IGMP dialog box—Interface tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 234
Figure 104 IGMP dialog box—Multicast Router Discovery tab . . . . . . . . . . . . . . . . . 237
Figure 105 IGMP dialog box—Snoop tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 238
Figure 106 IGMP dialog box—Groups tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 240
Figure 107 IGMP dialog box—Static tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 242
Figure 108 IGMP, Insert Static dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 242
Figure 109 IGMP dialog box—Access tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 244
Figure 110 IGMP, Insert Access dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 244
Figure 111 IGMP dialog box—Sender tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 245
Figure 112 VLAN dialog box—Basic tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 248
Figure 113 Bridge, VLAN dialog box—FDB Aging tab . . . . . . . . . . . . . . . . . . . . . . . 248
Figure 114 Bridge, VLAN dialog box—Multicast tab . . . . . . . . . . . . . . . . . . . . . . . . . 249
Figure 115 Bridge, VLAN, Insert Multicast dialog box . . . . . . . . . . . . . . . . . . . . . . . 249
Figure 116 PIM dialog box—Globals tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 253
Figure 117 IP VLAN dialog box I . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 255
Figure 118 IP VLAN dialog box—PIM tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 256
Figure 119 PIM dialog box—Interfaces tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 257
Figure 120 PIM dialog box—Neighbors tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 259
Figure 121 PIM dialog box—RP Set tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 260
Figure 122 PIM dialog box—Candidate RP tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . 262
Figure 123 PIM dialog box—Insert Candidate RP dialog box . . . . . . . . . . . . . . . . . . 262
Figure 124 PIM dialog box—Current BSR tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 264
Figure 125 Multicast dialog box—Routes tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 265
Figure 126 Multicast dialog box—Next Hops tab . . . . . . . . . . . . . . . . . . . . . . . . . . . 266
Figure 127 Multicast dialog box—Interfaces tab . . . . . . . . . . . . . . . . . . . . . . . . . . . . 268
Figure 128 Multicast dialog box—Static Source Group tab . . . . . . . . . . . . . . . . . . . 270
Figure 129 Multicast, Insert Static Source Group dialog box . . . . . . . . . . . . . . . . . . 271
Figure 130 Multicast dialog box—Mroute-HW tab . . . . . . . . . . . . . . . . . . . . . . . . . . 273
Figure 131 Prunes dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 274
Figure 132 Sources dialog box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 274
Figure 133 Egress VLANs Dialog . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 275
321712-B Rev 03
17
Tables
Table 1
IP addresses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Table 2
Subnet masks for Class B and Class C IP addresses . . . . . . . . . . . . . . . 32
Table 3
Router types in an OSPF network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
Table 4
IP dialog box—Globals tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 95
Table 5
IP dialog box—Addresses tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 99
Table 6
IP dialog box—Routes tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
Table 7
IP dialog box—Static Routes tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . 104
Table 8
IP dialog box—Circuitless IP tab and Insert Circuitless dialog box fields 109
Table 9
Circuitless OSPF dialog box fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 110
Table 10
Circuitless PIM dialog box fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
Table 11
IP dialog box—Route Preference tab fields . . . . . . . . . . . . . . . . . . . . . . 113
Table 12
IP dialog box—Router Discovery tab fields . . . . . . . . . . . . . . . . . . . . . . 115
Table 13
IP, VLAN—Router Discovery tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . 118
Table 14
IP dialog box—ARP tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
Table 15
Globals tab and Insert Globals dialog box fields . . . . . . . . . . . . . . . . . . 127
Table 16
Policy, Insert Prefix List dialog box fields . . . . . . . . . . . . . . . . . . . . . . . . 132
Table 17
Policy, Insert Route Policy dialog box fields . . . . . . . . . . . . . . . . . . . . . . 136
Table 18
Applying Policy tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
Table 19
Policy, Insert OSPF Accept Dialog fields . . . . . . . . . . . . . . . . . . . . . . . . 140
Table 20
Policy, Insert OSPF Redistribute dialog box fields . . . . . . . . . . . . . . . . . 142
Table 21
Policy dialog box—RIP In/Out Policy tab fields . . . . . . . . . . . . . . . . . . . . 144
Table 22
Globals tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149
Table 23
Interface tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 150
Table 24
Secondary Feature tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 153
Table 25
IP, VLAN, Insert VRRP dialog box fields . . . . . . . . . . . . . . . . . . . . . . . . . 156
Table 26
VRRP Stats Dialog Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 158
Table 27
RIP dialog box—Globals tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 164
Table 28
IP, VLAN dialog box—RIP tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
Table 29
RIP supply and listen settings and switch action . . . . . . . . . . . . . . . . . . 170
Configuring IP Routing and Multicast Operations using Device Manager
18 Tables
Table 30
RIP dialog box—Interface tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
Table 31
RIP send modes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
Table 32
RIP dialog box—Interface Advance tab fields . . . . . . . . . . . . . . . . . . . . . 174
Table 33
RIP dialog box—Status tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
Table 34
General tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
Table 35
OSPF dialog box—Interfaces tab fields . . . . . . . . . . . . . . . . . . . . . . . . . 183
Table 36
Neighbors tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 191
Table 37
OSPF Stats Default fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 196
Table 38
Areas tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 199
Table 39
OSPF dialog box—Virtual If tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . 203
Table 40
OSPF dialog box—Virtual Neighbor tab fields . . . . . . . . . . . . . . . . . . . . 205
Table 41
Host tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 207
Table 42
If Metrics tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 209
Table 43
Stub Area Metrics tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 210
Table 44
Link State Database tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 211
Table 45
Ext. Link State DB tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 213
Table 46
Area Aggregate tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 215
Table 47
Policy, Insert OSPF Redistribute dialog box fields . . . . . . . . . . . . . . . . . 218
Table 48
UdpForwarding dialog box—Protocols tab fields . . . . . . . . . . . . . . . . . . 221
Table 49
UdpForwarding dialog box—Forwardings tab fields . . . . . . . . . . . . . . . . 222
Table 50
UdpForwarding dialog box—Forwarding Lists tab fields . . . . . . . . . . . . . 224
Table 51
UdpForwarding dialog box—Broadcast Interfaces tab fields . . . . . . . . . 226
Table 52
IGMP tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 229
Table 53
Cache tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 233
Table 54
IGMP dialog box—Interface tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . 235
Table 55
Multicast Router Discovery fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 237
Table 56
Snoop tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 238
Table 57
Group tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 241
Table 58
IGMP, Insert Static dialog box fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . 243
Table 59
Access tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 245
Table 60
Sender tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 246
Table 61
Bridge, VLAN dialog box—Multicast tab fields . . . . . . . . . . . . . . . . . . . . 250
Table 62
PIM Globals tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 253
Table 63
VLAN PIM tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 256
Table 64
PIM Interfaces tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 257
321712-B Rev 03
Tables
19
Table 65
PIM Neighbors tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 259
Table 66
PIM RP Set tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 261
Table 67
PIM Candidate RP tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 263
Table 68
Current BSR tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 264
Table 69
Routes tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 266
Table 70
Next Hops tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 267
Table 71
Multicast dialog box—Interfaces tab fields . . . . . . . . . . . . . . . . . . . . . . . 268
Table 72
Static Source Group tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 270
Table 73
Mroute-HW tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 273
Table 74
Prunes tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 274
Table 75
Sources tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 275
Table 76
Egress VLANs tab fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 275
Configuring IP Routing and Multicast Operations using Device Manager
20 Tables
321712-B Rev 03
21
Preface
The Ethernet Routing Switch 1600 Series is a fixed port, hardware-based Layer 3
routing switch that is available in three models:
•
•
•
the Ethernet Routing Switch 1612G with 12 Small Form Factor (SFP) GBICs,
which provides small to medium aggregation
the Ethernet Routing Switch 1624G with 24 SFP GBICs, which provides
small to medium aggregation
the Ethernet Routing Switch 1648T with 48 10/100 ports and 4 SFP GBICs,
which provides small edge concentration
The Ethernet Routing Switch 1600 Series Layer 3 routing switch can reside in the
wiring closet (1648T) and in the data center or network core (1612G and 1624G):
•
•
The Ethernet Routing Switch 1648T provides Layer 3 functionality in the
wiring closet.
The Ethernet Routing Switch 1612G and 1624G provide gigabit Ethernet
ports for wiring closet aggregation, as well as high-speed connections for
servers and power users. These aggregation devices typically reside in the
network core or data center, but can be placed anywhere.
This guide provides instructions for the configuration and management of IP
routing and multicast operations using the Java Device Manager (JDM).
Java Device Manager (Device Manager) is a graphical user interface (GUI) used
to configure and manage Ethernet Routing Switches. You install it on a
management station in the network. For instructions about installing and starting
Device Manager on a Windows*, UNIX*, or Linux* platform, refer to Installing
and Using Device Manager (316857-C).
Configuring IP Routing and Multicast Operations using Device Manager
22
Preface
Before You Begin
This guide is intended for network administrators who have the following
background:
•
•
•
•
basic knowledge of networks, Ethernet bridging, and IP routing
familiarity with networking concepts and terminology
basic knowledge of data switch management
basic knowledge of network topologies
Before using this guide, you must complete the following procedures. For a new
switch:
1
Install the switch.
For installation instructions, see Installing the Ethernet Routing Switch 1600
Series Switch (316860-D).
2
Connect the switch to the network.
Ensure that you are running the latest version of Nortel Ethernet Routing Switch
1600 Series software. For information about upgrading the Ethernet Routing
Switch 1600 Series, see Upgrading to Ethernet Routing Switch 1600 Series
Software Release 2.1 (321327-B).
321712-B Rev 03
Preface 23
Text Conventions
This guide uses the following text conventions:
angle brackets (< >)
Enter text based on the description inside the brackets.
Do not type the brackets when entering the command.
Example: If the command syntax is
ping <ip_address>, you enter
ping 192.32.10.12
bold text
Objects such as window names, dialog box names, and
icons, as well as user interface objects such as buttons,
tabs, and menu items.
bold Courier text
Command names, options, and text that you must enter.
Example: Use the dinfo command.
Example: Enter show ip {alerts|routes}.
braces ({})
Required elements in syntax descriptions where there is
more than one option. You must choose only one of the
options. Do not type the braces when entering the
command.
Example: If the command syntax is
show ip {alerts|routes}, you must enter either
show ip alerts or show ip routes, but not both.
brackets ([ ])
Optional elements in syntax descriptions. Do not type
the brackets when entering the command.
Example: If the command syntax is
show ip interfaces [-alerts], you can enter
either show ip interfaces or
show ip interfaces -alerts.
ellipsis points (. . . )
Repeat the last element of the command as needed.
Example: If the command syntax is
ethernet/2/1 [<parameter> <value>]... ,
you enter ethernet/2/1 and as many
parameter-value pairs as needed.
Configuring IP Routing and Multicast Operations using Device Manager
24
Preface
italic text
Variables in command syntax descriptions. Also
indicates new terms and book titles. Where a variable is
two or more words, the words are connected by an
underscore.
Example: If the command syntax is
show at <valid_route>,
valid_route is one variable and you substitute one
value for it.
plain Courier
text
Command syntax and system output, for example,
prompts and system messages.
Example: Set Trap Monitor Filters
separator ( > )
Menu paths.
Example: Protocols > IP identifies the IP command on
the Protocols menu.
vertical line ( | )
Options for command keywords and arguments. Enter
only one of the options. Do not type the vertical line
when entering the command.
Example: If the command syntax is
show ip {alerts|routes}, you enter either
show ip alerts or show ip routes, but not
both.
321712-B Rev 03
Preface 25
Related information
This section lists information sources that relate to this document.
Publications
Refer to the following publications for information about Ethernet Routing
Switch 1600 Series, Software Release 2.1:
•
•
•
•
•
•
•
•
•
•
•
•
•
•
•
•
•
Installing the Ethernet Routing Switch 1600 Series Switch (316860-D)
Upgrading to Ethernet Routing Switch 1600 Series Software Release
2.1 (321327-B)
Quick Start Guide (321819-A)
Getting Started (321821-A)
Installing and Using Device Manager (316857-C)
Configuring IP Routing and Multicast Operations using the CLI (321711-B)
Configuring QOS and Filters using the CLI and Device Manager (321822-A)
Configuring and Managing Security using Device Manager (321713-B)
Configuring and Managing Security using the CLI (321714-B)
Configuring VLANs, Spanning Tree, and Static Link Aggregation using the
CLI (321717-B)
Configuring VLANs, Spanning Tree, and Static Link Aggregation using
Device Manager (321718-B)
CLI Command Line Reference for the Ethernet Routing Switch 1600
Series (316862-D)
Network Design Guidelines (321823-A)
Configuring Network Management using the CLI and Device
Manager (321816-A)
Managing Platform Operations (321817-A)
System Messaging Platform Reference Guide (321820-A)
Release Notes for the Ethernet Routing Switch 1600 Series, Software Release
2.1 (316859-J)
Configuring IP Routing and Multicast Operations using Device Manager
26
Preface
How to get help
This section explains how to get help for Nortel products and services.
Finding the latest updates on the Nortel web site
The content of this documentation was current at the time the product was
released. To check for updates to the latest documentation and software for the
Ethernet Routing Switch 1600 Series, click one of the following links:
Latest Software
Takes you directly to the Nortel page for Ethernet Routing
Switch 1600 Series software
Latest Documentation
Takes you directly to the Nortel page for Ethernet Routing
Switch 1600 Series documentation
Getting help from the Nortel web site
The best way to get technical support for Nortel products is from the Nortel
Technical Support web site:
www.nortel.com/support
This site provides quick access to software, documentation, bulletins, and tools to
address issues with Nortel products. From this site, you can:
•
•
•
•
download software, documentation, and product bulletins
search the Technical Support Web site and the Nortel Knowledge Base for
answers to technical issues
sign up for automatic notification of new software and documentation for
Nortel equipment
open and manage technical support cases
Getting help over the phone from a Nortel Solutions Center
If you do not find the information you require on the Nortel Technical Support
web site, and you have a Nortel support contract, you can also get help over the
phone from a Nortel Solutions Center.
321712-B Rev 03
Preface 27
In North America, call 1-800-4NORTEL (1-800-466-7835).
Outside North America, go to the following web site to obtain the phone number
for your region:
www.nortel.com/callus
Getting help from a specialist using an Express Routing
Code
To access some Nortel Technical Solutions Centers, you can use an Express
Routing Code (ERC) to quickly route your call to a specialist in your Nortel
product or service. To locate the ERC for your product or service, go to:
www.nortel.com/erc
Getting help through a Nortel distributor or reseller
If you purchased a service contract for your Nortel product from a distributor or
authorized reseller, contact the technical support staff for that distributor or
reseller.
Configuring IP Routing and Multicast Operations using Device Manager
28
Preface
321712-B Rev 03
29
Chapter 1
IP routing and multicast concepts
This chapter provides conceptual information for the Ethernet Routing Switch
1600 Series IP routing and multicast features. It includes the following topics:
•
•
•
•
•
•
•
•
•
•
•
•
•
“Overview of IP routing”page 30
“BootP/DHCP relay”page 40
“Address Resolution Protocol (ARP)”page 43
“Routing Information Protocol (RIP)”page 43
“Virtual Router Redundancy Protocol (VRRP)”page 47
“Open Shortest Path First (OSPF) Protocol”page 52
“Circuitless IP (CLIP)”page 63
“UDP forwarding”page 64
“Overview of IP multicast”page 65
“Internet Group Management Protocol (IGMP)”page 71
“Protocol Independent Multicast-Sparse Mode (PIM-SM)”page 77
“Multicast access control feature”page 87
“Multicast MAC filtering”page 90
Configuring IP Routing and Multicast Operations using Device Manager
30
Overview of IP routing
This section provides an overview of IP routing and includes the following topics:
•
•
•
•
•
•
•
“IP addressing” on page 30
“Virtual routing between VLANs” on page 34
“Static routes” on page 35
“Black hole static routes” on page 36
“Alternative routes” on page 37
“IP filtering and route policies” on page 38
“Per-VLAN routing control” on page 39
IP addressing
An IP version 4 address consists of 32 bits expressed in a dotted-decimal
format (x.x.x.x). The IP version 4 address space is divided into classes with
classes A, B, and C reserved for unicast addresses and accounting for 87.5 percent
of the 32-bit IP address space. Class D is reserved for multicast addressing.
Table 1 lists the breakdown of IP address space by address range and mask.
Table 1 IP addresses
Class
Address range
Mask
Number of addresses
A
1.0.0.0 - 126.0.0.0
255.0.0.0
126
B
128.0.0.0 - 191.0.0.0
255.255.0.0
63 * 255
C
192.0.0.0 - 223.0.0.0
255.255.255.0
31 * 255 * 255
D
224.0.0.0 - 239.0.0.0
To express an IP address in dotted-decimal notation, each octet of the IP address
is converted to a decimal number and the numbers are separated by decimal
points. For example, the 32-bit IP address 10000000 00100000 00001010
10100111 is expressed as 128.32.10.167 in dotted-decimal notation.
Each IP address class, when expressed in binary, has a different boundary point
between the network and host portions of the address, as illustrated in Figure 1 on
page 31. The network portion is a network number field from 8 through 24 bits.
The remaining 8 through 24 bits identify a specific host on the network.
321712-B Rev 03
31
Figure 1 Network and host boundaries in IP address classes
Class A
bit #
0
7 8
31
0
Network
portion
Class B
bit #
Host
portion
01
15 16
31
10
Network
portion
Class C
bit #
Host
portion
012
23 24
31
110
Network
portion
Host
portion
9750EA
This section includes the following topics:
•
•
“Subnet addressing”
“Supernet addressing and CIDR” on page 33
Subnet addressing
The concept of subnetworks (or subnets) extends the IP addressing scheme by
allowing an organization to use one IP address range for multiple networks.
Subnets are two or more physical networks that share a common
network-identification field (the network portion of the 32-bit IP address).
A subnet address is created by increasing the network portion to include a subnet
address, thus decreasing the host portion of the IP address. For example, in the
address 128.32.10.0, the network portion is 128.32, while the subnet is found in
the first octet of the host portion (10). A subnet mask is applied to the IP address
and identifies the network and host portions of the address.
Configuring IP Routing and Multicast Operations using Device Manager
32
Table 2 illustrates how subnet masks used with Class B and Class C addresses can
create differing numbers of subnets and hosts. This example includes using the
zero subnet, which is permitted on a 1600 Series switch.
Table 2 Subnet masks for Class B and Class C IP addresses
Number
of bits
Subnet mask
Number of subnets
Number of hosts per subnet
(recommended)
Class B
2
255.255.192.0
2
16 382
3
255.255.224.0
6
8 190
4
255.255.240.0
14
4 094
5
255.255.248.0
30
2 046
6
255.255.252.0
62
1 022
7
255.255.254.0
126
510
8
255.255.255.0
254
254
9
255.255.255.128
510
126
10
255.255.255.192
1 022
62
11
255.255.255.224
2 046
30
12
255.255.255.240
4 094
14
13
255.255.255.248
8 190
6
14
255.255.255.252
16 382
2
Class C
1
255.255.255.128
0
126
2
255.255.255.192
2
62
3
255.255.255.224
6
30
4
255.255.255.240
14
14
5
255.255.255.248
30
6
6
255.255.255.252
62
2
Variable-length subnet masking (VLSM) is the ability to divide your intranet into
pieces that match your requirements. Routing is based on the longest matching
subnet mask/network. Routing Information Protocol (RIPv2) and Open Shortest
Path First (OSPF) are routing protocols that support VLSM.
321712-B Rev 03
33
Supernet addressing and CIDR
A supernet is a group of networks identified by contiguous network addresses.
IP service providers can assign customers blocks of contiguous addresses to
define supernets as needed. Supernetting allows for the addressing of an entire
block of Class C addresses and avoids using large routing tables to track the
addresses.
Each supernet has a unique supernet address that consists of the upper bits shared
by all of the addresses in the contiguous block. For example, consider the Class C
addresses shown in Figure 2. By adding the mask 255.255.128.0 to IP address
192.32.128.0, you aggregate the addresses 192.32.128.0 through 192.32.255.255,
and 128 Class C addresses use a single routing advertisement. In the bottom half
of Figure 2, you use 192.32.0.0/17 to aggregate the 128 addresses (192.32.0.0/24
to 192.32.127.0/24).
Figure 2 Class C address supernet
128
Class C
Networks
192.32.128.0 255.255.128.0
192.32.127.0/24
192.32.126.0/24
192.32.0.0/17
192.32.2.0/24
192.32.1.0/24
192.32.0.0/24
9577EA
Configuring IP Routing and Multicast Operations using Device Manager
34
Another example is the block of addresses 192.32.0.0 to 192.32.7.0. The supernet
address for this block is 11000000 00100000 00000, with the 21 upper bits shared
by the 32-bit addresses.
A complete supernet address consists of an address/mask pair:
•
•
The address is the first 32-bit IP address in the contiguous block. In this
example, the address is 11000000 00100000 00000000 00000000 (192.32.0.0
in dotted-decimal notation).
The mask is a 32-bit string containing a set bit for each bit position in the
supernet part of the address. The mask for the supernet address in this
example is 11111111 11111111 11111000 00000000 (255.255.248.0 in
dotted-decimal notation).
The complete supernet address in this example is 192.32.0.0/21.
The supernet address is also referred to as the classless interdomain routing
(CIDR) address. Although classful routing prohibits using an address mask with
the IP address, CIDR allows you to create networks of various sizes using the
address mask. VLSM also allows for the division of address space, but the
division is not seen outside the network. With CIDR, addresses are used by
routers outside the network.
Virtual routing between VLANs
The Ethernet Routing Switch 1600 Series supports wire-speed IP routing between
VLANs. As shown in Figure 3 on page 35, although VLAN 1 and VLAN 2 are on
the same switch, for traffic to flow from VLAN 1 to VLAN 2, the traffic must be
routed.
When routing is configured on a VLAN, an IP address is assigned to the VLAN
and this acts as a virtual router interface address for the VLAN. It is called a
virtual router interface because it is not associated with any particular port. The
VLAN IP address can be reached through any of the VLAN ports, and frames are
routed from the VLAN through the gateway’s IP address. Routed traffic can be
forwarded to another VLAN within the switch.
321712-B Rev 03
35
Figure 3 IP Routing Between VLANs
When Spanning Tree Protocol is enabled in a VLAN, the spanning tree
convergence must be stable before the routing protocol begins. This requirement
can lead to an additional delay in the forwarding of IP traffic.
Because a given port can belong to multiple VLANs (some of which are
configured for routing on the switch and some of which are not), there is no longer
a one-to-one correspondence between the physical port and the router interface.
As with any IP address, virtual router interface addresses are also used for device
management. For SNMP or Telnet management, any virtual router interface
address can be used to access the switch as long as routing is enabled on the
VLAN. For more information about virtual routing configuration, refer to
“Configuring IP Routing” on page 91.
Static routes
In order for data to traverse from one end of the network to the other, each device
needs a routing table that lists how to get to the various destinations, or routes.
There are two primary ways to generate routes:
•
•
static routes, which are configured by the network administrator
dynamically learned routes, which are produced when a routing protocol is
run on network equipment
Static routes are user-defined routes that specify the path for the router to forward
traffic. Static routes do not update automatically.
Configuring IP Routing and Multicast Operations using Device Manager
36
On the Ethernet Routing Switch 1600 Series, any route can be configured as a
static route. Static routes can also be configured with a next hop that is not directly
connected, but that hop must be reachable. Otherwise, the static route is not
enabled.
A default static route can be used to specify a route to all networks for which there
are no explicit routes in the routing table. This route is, by definition, a route with
the prefix length of zero (see RFC 1812).
Note: To create a default static route, the destination address and subnet
mask must be set to 0.0.0.0.
Static routes are a resource-efficient way to:
•
•
•
help keep data flowing in the network
provide a commonly used method to configure the default route (that is, a
route with network address 0.0.0.0 and network mask 0.0.0.0)
provide an effective way to manually control the routing table, particularly if
the network administrator does not want traffic flowing according to the
dynamic routing protocols
For more information about configuring static routes, refer to “Configuring IP
Routing” on page 91.
Black hole static routes
A black hole static route is a route with an invalid next-hop, such that the data
packets destined to this network are dropped by the switch (see also, “Static
routes” on page 35).
While aggregating or injecting routes to other routers, the router itself may not
have a path to the aggregated destination. In such cases, the result is a “black
hole” and a routing loop. To avoid such loops, a black hole static route can be
configured to the destination it is advertising.
A preference value can be configured for a black hole route. This value must be
configured appropriately so that when the black hole route must be used, it is
elected as the best route.
321712-B Rev 03
37
Before adding a black hole static route, a check is performed to ensure that there is
no other static route to that identical destination in an enabled state. If such a route
exists, the black hole route cannot be added and an error message displays.
If there is a black hole route enabled, another static route to that destination cannot
be added. Delete or disable the black hole route prior to adding a regular static
route to that destination. For more information about configuring black hole static
routes, refer to “Configuring IP Routing” on page 91.
Alternative routes
Routers may have several routes to the same destination network through several
protocols. In the Ethernet Routing Switch 1600 Series software, if the alternative
route feature is enabled, it stores all of these alternative routes sorted in order of
network mask, cost, and route preference. The best, or first one listed, is the best
route and is used by the hardware. The rest of the routes are referred to as
alternative routes.
To avoid traffic interruption, alternative routes can be globally enabled on the
switch. If the best route becomes unavailable, the next best route from the
alternative route list can then replace the best route. In the Ethernet Routing
Switch 1600 Series, both the active routing table and the configured static route
table are maintained.
In the event a route is configured with the same network address, mask, and cost
values from multiple sources, route preferences are taken into consideration to
select the best route added to the forwarding database.
Route preferences can be set for static routes and routing protocols. When
configuring a static route on the Ethernet Routing Switch 1600 Series, a
preference for the route can be specified. To modify the preference for a static
route, disable the route before editing the configuration, and then reenable the
route.
Note: Changing route preferences is a process-oriented operation that
can affect system performance and network reachability while
performing the procedures. Therefore, Nortel recommends that changing
preferences for static routes or routing protocols must only be done when
configuring routes or before enabling routing protocols.
Configuring IP Routing and Multicast Operations using Device Manager
38
On the Ethernet Routing Switch 1600 Series, default preferences are assigned to
all standard routing protocols. The default preference can be modified for a
protocol to make the priority higher or lower than other protocols. When the
preference for a protocol is changed, if all best routes remain best routes, only the
local route tables are changed. However, if changing the protocol preference
causes best routes to no longer be best routes, neighboring route tables may be
affected.
In addition, the preference value can be modified for dynamic routes through
route filtering and IP policies, and the route preference overrides the global
preference for the protocol. With this alternative mechanism, the behavior of
specific routes can have a different preference rather than acquiring the global
protocol preference. For a static route, an individual route preference can be
specified that overrides the global static route preference. The preference value
can be anything between 0 and 255, with 0 reserved for local routes and 255
representing an unreachable route.
For more information about configuring alternative routes, refer to “Configuring
IP Routing” on page 91.
IP filtering and route policies
The Ethernet Routing Switch 1600 Series can apply a number of filters to IP
traffic to manage, accept, and announce policies for routing table information.
The filtering process relies on the IP prefix lists in the common routing table
manager infrastructure.
An IP route policy and its attributes can be defined globally, and then the policy
applied individually to interfaces and protocols.
This section includes the following topics:
•
•
•
321712-B Rev 03
“Accept policies (in filters)” on page 39
“Announce policies (out filters)” on page 39
“Prefix list” on page 39
39
Accept policies (in filters)
The Ethernet Routing Switch 1600 Series applies accept policies (in filters) to
incoming traffic to determine whether or not to add the route to the routing table.
For RIP, accept policies are applied to all incoming route information.
Announce policies (out filters)
The Ethernet Routing Switch 1600 Series applies announce policies (out filters) to
outgoing advertisements to neighbors and peers in the protocol domain. These
polices are used to determine whether or not to announce specific route
information. Out filtering applies to RIP updates.
Prefix list
The prefix list is a list of networks used by route policies to define an action. One
or more IP prefix lists can be created and applied to any IP route policy.
Before the advent of prefix lists, some protocols used two databases for different
types of policies: the address-list database, and the netlist database. A prefix list
combines these two databases:
•
•
A prefix list with a 32-bit mask is equivalent to an address.
A prefix list with a mask less than 32 bits can be used as a network.
For more information about configuring filters and prefix lists, refer to
“Configuring IP Routing” on page 91.
Per-VLAN routing control
Routing capabilities on specified switch ports can be enabled or disabled when the
port is part of a routed VLAN. In the Ethernet Routing Switch 1600 Series, an IP
address is assigned to the port-based or IP protocol-based VLANs.
To enable routing on a VLAN, perform the following steps:
1
Create a VLAN to which you can assign the port.
2
Assign an IP address to the VLAN.
Configuring IP Routing and Multicast Operations using Device Manager
40
For more information about configuring per-port routing, refer to “Configuring IP
Routing” on page 91.
BootP/DHCP relay
The Dynamic Host Configuration Protocol (DHCP) is an extension of the
Bootstrap Protocol (BootP) and provides host configuration information to the
workstations on a dynamic basis. To lower administrative overhead, network
managers prefer to configure a small number of DHCP servers in a central
location. It is necessary for routers to support the BootP/DHCP relay function so
that hosts can access configuration information from servers several router hops
away.
Differences between DHCP and BootP
The following differences between DHCP and BootP are specified in RFC 2131
and include functions that BootP does not address:
•
•
DHCP defines mechanisms through which clients can be assigned a network
address for a finite lease (providing reuse of IP addresses).
DHCP provides the mechanism for clients to acquire all of the IP
configuration parameters needed to operate.
DHCP uses the BootP message format defined in RFC 951. A packet is classified
as DHCP if the first four octets in the options field are 99, 130, 83, 99, and the
fifth octet is 53. The first four octets are referred to as the Magic Cookie, while the
fifth is the DHCP message type code. The remainder of the options field consists
of a list of tagged parameters that are called options (RFC 2131).
Summary of DHCP relay operation
BootP/DHCP clients (workstations) generally use UDP/IP broadcasts to
determine their IP addresses and configuration information. If such a host is on a
network or a subnet segment (or VLAN) that does not include a DHCP server, the
UDP broadcasts are by default not forwarded to the server located on a different
network segment or VLAN. The Ethernet Routing Switch 1600 Series can be
configured to overcome this issue by forwarding the broadcasts to the server
321712-B Rev 03
41
through virtual router interfaces. The router interfaces can be configured to
forward DHCP broadcasts to other locally connected network segments or
directly to the server’s IP address. DHCP must be enabled on a
per-routable-interface basis.
Figure 4 shows an end station connected to subnet 1, corresponding to VLAN 1.
The Ethernet Routing Switch 1600 Series connects two subnets by means of the
virtual routing function. When the end station generates a DHCP request as a
limited UDP broadcast to the IP address of all 1s (that is, 255.255.255.255) with
the DHCP relay function configured, the Ethernet Routing Switch 1600 Series
forwards DHCP requests to subnet 2 or to the host address of the DHCP server,
depending on the configuration.
Figure 4 DHCP operation
Forwarding DHCP packets
In the example shown in Figure 5, the agent address is 10.10.1.254. To configure
the Ethernet Routing Switch 1600 Series to forward DHCP packets from the end
station to the server, use 10.10.2.1 as the server address.
Figure 5 Forwarding DHCP packets
Configuring IP Routing and Multicast Operations using Device Manager
42
All BootP broadcast packets, including DHCP packets that appear on the VLAN 1
router interface (10.10.1.254), are forwarded to the DHCP server. In this case, the
DHCP packets are forwarded as unicast to the DHCP server’s IP address.
To forward BootP/DHCP packets as broadcast packets to VLAN 2, specify the IP
address of the switch VLAN 2 router interface (10.10.2.254) as the server address.
Multiple BootP/DHCP servers
Most enterprise networks use multiple BootP/DHCP servers for fault tolerance.
With the Ethernet Routing Switch 1600 Series, you can configure the switch to
forward BootP/DHCP requests to multiple servers.
If a DHCP client is connected to a routable interface, to configure DHCP requests
to be sent to multiple routable interfaces or multiple server IP addresses, enable
DHCP on the client (agent address) and then enable DHCP from the client to each
of the interfaces or IP addresses (server addresses).
In the example shown in Figure 6, two DHCP servers are located on two different
subnets. To configure the Ethernet Routing Switch 1600 Series to forward the
copies of the BootP/DHCP packets from the end station to both servers, specify
the switch (10.10.1.254) as the agent address. Then, enable DHCP to each of the
DHCP servers by entering 10.10.2.1 and 10.10.3.1 as the server addresses.
Figure 6 Configuring multiple BootP/DHCP servers
321712-B Rev 03
43
Address Resolution Protocol (ARP)
Network stations using the IP protocol need both a physical address and an IP
address to transmit a packet. In situations where the station knows only the
network host’s IP address, the Address Resolution Protocol (ARP) enables the
network station to determine a network host’s physical address by binding a 32-bit
IP address to a 48-bit MAC address. A network station can use ARP across a
single network only, and the network hardware must support physical broadcasts.
If a network station wants to send a packet to a host but knows only the host’s IP
address, the network station uses ARP to determine the host’s physical address, as
follows:
1
The network station broadcasts a special packet, called an ARP request, that
asks the host at the specified IP address to respond with its physical address.
2
All network hosts receive the broadcast request.
3
Only the specified host responds with its hardware address.
4
The network station then maps the host IP address to the host physical address
and saves the results in an address-resolution cache for future use.
5
The network station ARP table displays the associations of the known MAC
address to IP address.
Static ARP entries can be created, and individual ARP entries can be deleted.
Routing Information Protocol (RIP)
Routing Information Protocol (RIP) is a standard, dynamic routing protocol based
on the Bellman-Ford (or distance vector) algorithm. It is used as an Interior
Gateway Protocol (IGP). Using RIP, routers can exchange information to
compute routes through an IPv4-based network.
RIP is defined in RFC 1058 for RIP version 1 and RFC 2453 for RIP version 2.
The most significant difference between the two versions is that RIP version 2
supports subnet masks.
Configuring IP Routing and Multicast Operations using Device Manager
44
RIP operation
RIP uses User Datagram Protocol (UDP) data packets to exchange routing
information. Each router maintains a routing table, which lists the optimal route to
every destination in the system. Each router advertises its routing information by
sending a routing information update at regular intervals. Neighboring routers use
this information to recalculate their routing tables and retransmit the routing
information. For RIP version 1, no mask information is exchanged; the natural
mask is always applied by the router receiving the update. For RIP version 2,
mask information is always included.
If a router does not receive an update from another router within a timeout period,
it deletes the routes served by the nonupdating router from its routing table.
However, it keeps these routes temporarily in a garbage list and continues to
advertise them for a holddown period, so that neighbors know that the routes are
unreachable. If a valid update for a garbage route is received within the holddown
period, the router adds the route back into its routing table. If no update is
received, the router completely deletes all garbage list entries for the nonupdating
router.
To prevent routing loops and to promote fast convergence, RIP uses the
mechanisms of split horizon, with or without poisoned reverse, and triggered
updates. Simple split horizon means that IP routes learned from a neighbor are not
advertised back in updates to that neighbor. Split horizon with poisoned reverse
means that these routes are advertised back to the neighbor, but they are
“poisoned” with a metric of 16, which represents infinite hops in the network. The
receiver neighbor therefore ignores this route. Triggered updates means that a
router is required to send update messages whenever it changes the metric for a
route, even if it is not yet time for a regular update message.
RIP supports the following standard behavior:
•
•
•
•
•
•
•
321712-B Rev 03
periodic RIP updates about effective best routes
garbage collection
split horizon with or without poisoned reverse
triggered update for changed RIP routes
unicast to the specific query requestor
broadcast or multicast of regular and triggered updates
subnet mask (RIP version 2)
45
•
•
•
•
routing table update based on the received RIP message
global update timer
Hold Down Timer and timeout timer per device and per interface
cost per device and per interface
The Ethernet Routing Switch 1600 Series implementation of RIP also supports the
following features:
•
•
in and out routing policies
auto-aggregation (also known as auto-summarization) of groups of adjacent
routes into single entries
Many RIP features are configurable. The actual behavior of the protocol depends
on the feature configurations.
Note: In the Ethernet Routing Switch 1600 Series, RIP is configurable
only for VLANs.
RIP metrics
RIP is known as a distance vector protocol. The vector is the network number
and next hop, and the distance is the cost associated with the network number.
RIP identifies network reachability based on cost, and cost is defined as hop
count. The distance from one router to the next is considered to be one hop. This
cost or hop count is known as the metric (Figure 7 on page 46).
Configuring IP Routing and Multicast Operations using Device Manager
46
Figure 7 Hop count or metric in RIP
A directly connected network has a metric of zero. An unreachable network has
a metric of 16. Therefore, 15 hops or 15 routers is the highest possible metric
between any two networks.
Limitations
RIP has the following limitations:
•
•
•
The protocol is limited to networks whose longest path is 15 hops.
The protocol depends on counting to infinity to resolve certain unusual
situations.
The protocol uses fixed metrics (the hop number) to compare alternative
routes, as opposed to real-time parameters such as measured delay, reliability,
or load.
RIP does not support addressless links.
For more information about configuring RIP, see “Configuring RIP” on page 161.
321712-B Rev 03
47
Virtual Router Redundancy Protocol (VRRP)
Because end stations are often configured with a static default gateway IP address,
a loss of the default gateway router causes a loss of connectivity to the remote
networks.
The Virtual Router Redundancy Protocol (VRRP) is designed to eliminate the
single point of failure that can occur when the single static default gateway router
for an end station is lost. VRRP introduces the concept of a virtual IP address
(transparent to users) shared between two or more routers connecting a common
subnet to the enterprise network. With the virtual IP address as the default
gateway on end hosts, VRRP provides dynamic default gateway redundancy in
the event of failure. (With the Ethernet Routing Switch 8300 Series Switch, only
one IP address can be assigned to any virtual router interface.)
VRRP uses the following terms:
•
•
•
•
•
VRRP router — a router running the VRRP protocol
Virtual router — the abstract object managed by VRRP that is assigned the
virtual IP address and that acts as the default router for a set of IP addresses
across a common LAN. Each virtual router is assigned a virtual router ID.
Virtual router master — the VRRP router that assumes responsibility for
forwarding packets sent to the IP address associated with the virtual router.
The master router also responds to packets sent to the virtual router IP address
and answers ARP requests for this IP address.
Virtual router backup — the router or routers that can serve as the failover
router if the master router becomes unavailable. If the master router fails, an
election process provides a dynamic transition of forwarding responsibility to
a new master router.
Priority — an 8-bit value assigned to all VRRP routers. A higher value
represents a higher priority for election to the master router. You can set the
priority to a value from 1 to 254. When a master router fails, an election
process takes place among the backup routers to dynamically re-assign the
role of the master router.
Configuring IP Routing and Multicast Operations using Device Manager
48
VLAN
With the Ethernet Routing Switch 1600 Series, VRRP can only be configured at
the VLAN level. To configure two or more routers to share a virtual router, the
routers must first belong to the same VLAN.
Initializing VRRP routers
When you initialize a VRRP router, if there are no other VRRP routers enabled in
the VLAN, then the initialized router assumes the role of the master router. When
additional routers are enabled in the VLAN, an election process takes place
among them to elect a master, based on their priority.
The master router functions as the forwarding router for the IP address associated
with the virtual router. It responds to ARP requests for the IP address, forwards
packets with a destination MAC address equal to the virtual router MAC address,
and accepts only packets addressed to the IP address associated with the virtual
router.
In the backup state, a VRRP router monitors the availability and state of the
master router. It does not respond to ARP requests and must discard packets with
a MAC address equal to the virtual router MAC address. It does not accept
packets addressed to IP addresses associated with the virtual router. If a shutdown
occurs, it transitions back to the initialize state.
If the master router fails, the backup router with the highest priority assumes the
role of the master router. It sends the VRRP advertisement and ARP request as
described in the preceding paragraphs and transitions to the controlling state.
Note: Nortel recommends against setting the virtual router IP address to
an IP address that is owned by a local router. If a VRRP router is
initialized and it is the owner of the virtual IP address, its priority is
automatically set to 255, and this value cannot be modified. As a result,
the router transitions to the master router state, and remains in that state
until it fails. As a result, your ability to manually alter the master or
backup router state is restricted.
321712-B Rev 03
49
Basic VRRP configuration steps
If you have a router A that you want to assign as the master router, and a router B
that you want to assign as the backup router, you can configure them for VRRP as
follows:
Configuring the virtual router master
To configure router A as the virtual router master:
1
On router A, create a VLAN, for example, VLAN 10.
2
Assign an IP address to the VLAN for routing.
3
Configure VRRP properties for VLAN 10 on router A:
a
Assign a virtual router ID. For example, VRID 1.
b
Set the virtual router IP address to a previously unassigned IP address.
Note: Nortel recommends against assigning a locally owned IP address as
the virtual router IP address.
c
Set the priority to a value above the priority of the backup router, for
example, 200.
Configuring the virtual router backup
To configure router B as the virtual router backup:
1
On router B, create a matching VLAN; in this case, VLAN 10.
2
Assign a local IP address to the VLAN for routing.
3
Configure VRRP properties for VLAN 10 on router B.
a
Assign the same virtual router ID as on router A. In this case, VRID 1.
b
Set the IP address to match the VRRP IP address configured for router A.
c
Set the priority to a value below the priority of Router A, for example,
100.
Configuring IP Routing and Multicast Operations using Device Manager
50
Enabling the switches
When you enable VRRP on both of these switches, an election process takes
place, and because router A has the higher priority, it is elected the master router.
It then assumes responsibility for the configured virtual router IP address.
Figure 8 shows Virtual router 1 (VRID 1) configured with router A as the master
router and router B as the backup master router. In this configuration, VRRP
provides the end hosts a redundant default gateway to the external networks.
Figure 8 VRRP Configuration
Corporate
network
Critical IP for Router A
Critical IP for Router B
VRID =1
VLAN = 10
Router A
Master router for VRID 1
Router B
Backup router for VRID 1
Default gateway = VRID 1
Legend
Ethernet Routing
Switch 1600
11013fa
Critical IP address
Within a VRRP VLAN, it is possible for one link to go down, while the remaining
links in the VLAN remain operational. Because the VRRP VLAN continues to
function, a virtual router associated with that VLAN does not register a master
router failure.
321712-B Rev 03
51
As a result, if the local router IP interface connecting the virtual router to the
external network fails, this does not automatically trigger a master router failover.
The critical IP address resolves this issue. If the critical IP address fails, it triggers
a failover of the master router.
Therefore, you can specify the local router IP interface uplink from the VRRP
router to the network as the critical IP address. This ensures that, if the local
uplink interface fails, VRRP initiates a master router failover to one of the backup
routers.
In Figure 8, the local network uplink interface on router A is shown as the critical
IP address for router A. As well, the similar network uplink is shown as the
critical IP address for router B. Router B also requires a critical IP address for
cases when it assumes the role of the master router.
With the support of VRRP, and the support of the critical IP interface linked to
VRRP, the Ethernet Routing Switch 1600 Series enables customers to build more
reliable small core networks, providing support for converged applications, like
voice and multimedia.
VRRP and Split-MLT
The standard implementation of VRRP allows only one active master switch per
IP subnet. All other VRRP interfaces in a network are in backup mode.
However, a deficiency occurs when VRRP-enabled switches use Split-MLT. If
VRRP switches are aggregated into two Split-MLT switches, the end host traffic
is load-shared on all uplinks to the aggregation switches (based on the MLT traffic
distribution algorithm).
However, VRRP normally has only one active routing interface enabled. All other
VRRP routers are in backup mode. Therefore, all traffic that reaches the backup
VRRP router is forwarded over the Inter Switch Trunk (IST) link towards the
master VRRP router. In this case, the IST link might not have enough bandwidth
to carry all the aggregated traffic.
You can overcome this issue by assigning the backup router as the master backup
router. The master backup router is a backup router that is permitted to actively
load-share the routing traffic with a master router.
Configuring IP Routing and Multicast Operations using Device Manager
52
When the master backup router is enabled, the incoming host traffic can be
forwarded over the Split-MLT links as normal.
Figure 9 shows a sample VRRP configuration with Split-MLT. As Router B is
configured as the backup master, routing traffic is load-shared between the two
devices.
Figure 9 VRRP Configuration with Split-MLT
Corporate
network
With Router B configured as
the Backup Master,
routing traffic is shared between
the two devices
Critical IP for Router A
Critical IP for Router B
Router A
Router B
IST
Master router for VRID 1
SMLT
SMLT
Backup router, set as the
Backup Master for VRID 1
MLT
Default gateway = VRID 1
Legend
Etthernet Routing
Switch 1600
Open Shortest Path First (OSPF) Protocol
The Open Shortest Path First (OSPF) Protocol is an Interior Gateway Protocol
(IGP) that distributes routing information between routers belonging to a single
autonomous system (AS). Intended for use in large networks, OSPF is a link-state
protocol that supports IP subnetting, IP Type of Service (TOS)-based routing, and
the tagging of externally-derived routing information.
321712-B Rev 03
53
Overview
In an OSPF network, each router maintains a link-state database that describes the
topology of the autonomous system (AS). The database contains the local state
for each router in the AS, including the router’s usable interfaces and reachable
neighbors. Each router periodically checks for changes in its local state and shares
any changes detected by flooding link-state advertisements (LSAs) throughout the
AS. Routers synchronize their topological databases based on the sharing of
information from LSAs.
From the topological database, each router constructs a shortest-path tree, with
itself as the root. The shortest-path tree gives the optimal route to each destination
in the AS. Routing information from outside the AS appears on the tree as leaves.
OSPF routes IP traffic based solely on the destination IP address and subnet mask,
and IP Type of Service (TOS) contained in the IP packet header.
Benefits
In large networks OSPF offers the following benefits:
•
Fast convergence
In the event of topological changes, OSPF recalculates routes quickly.
•
Minimal routing protocol traffic
Unlike distance vector-routing protocols such as RIP, OSPF generates a
minimum of routing protocol traffic.
•
Load sharing
OSPF provides support for equal-cost multipath routing. If several equal-cost
routes to a destination exist, traffic is distributed equally among them.
•
Type of Service
Separate routes can be calculated for each IP Type of Service.
Configuring IP Routing and Multicast Operations using Device Manager
54
OSPF routing algorithm
A separate copy of the OSPF routing algorithm runs in each area. Routers that are
connected to multiple areas run multiple copies of the algorithm. The sequence of
processes governed by the routing algorithm is as follows:
1
When a router starts, it initializes the OSPF data structures and then waits for
indications from lower-level protocols that its interfaces are functional.
2
A router then uses the Hello Protocol to discover neighbors. On point-to-point
and broadcast networks, the router dynamically detects its neighbors by
sending hello packets to the multicast address AllSPFRouters. On
non-broadcast multiaccess networks, some configuration information is
required in order to discover neighbors.
3
On all multiaccess networks (broadcast or non-broadcast), the Hello Protocol
also elects a designated router (DR) for the network.
4
The router attempts to form adjacencies with some of its neighbors. On
multiaccess networks, the DR determines which routers become adjacent.
This behavior does not occur if a router is configured as a passive interface,
because passive interfaces do not form adjacencies.
5
Adjacent neighbors synchronize their topological databases.
6
The router periodically advertises its link-state, and also does so when its
local state changes. LSAs include information about adjacencies enabling
quick detection of dead routers on the network.
7
LSAs are flooded throughout the area, ensuring that all routers in an area have
exactly the same topological database.
8
From this database each router calculates a shortest-path tree, with itself as
root. This shortest-path tree, in turn, yields a routing table for the protocol.
Autonomous system and areas
The AS can be subdivided into areas that group together contiguous networks,
routers connected to these networks, and attached hosts. Each area has its own
topological database that is invisible from outside the area. Routers within an area
know nothing of the detailed topology of other areas. Subdividing the AS into
areas significantly reduces the amount of routing protocol traffic as compared to
treating the entire AS as a single link-state domain.
321712-B Rev 03
55
A router can be attached to more than one area, maintaining a separate topological
database for each area to which it is connected. Two routers within the same area
maintain an identical topological database for that area. Each area is assigned a
unique area ID and the area ID 0.0.0.0 is reserved for the backbone area.
Packets are routed in the AS based on their source and destination addresses. If
the source and destination of a packet reside in the same area, intra-area routing is
used. If the source and destination of a packet reside in different areas inter-area
routing is used. Intra-area routing protects the area from bad routing information
because no routing information obtained from outside the area can be used.
Inter-area routing must pass through the backbone area, which is described in the
following section.
Backbone area
The backbone area consists of the following network types:
•
•
Networks and attached routers that are not contained in any other area
Routers that belong to multiple areas
The backbone is usually contiguous, but it is possible to create a non-contiguous
area by configuring virtual links. Virtual links can be configured between any two
backbone routers that have an interface to a common non-backbone area. Virtual
links belong to the backbone and use intra-area routing only. Virtual links are
described on page 61.
The backbone is responsible for distributing routing information between areas.
The topology of the backbone area is invisible to other areas, while it knows
nothing of the topology of those areas.
In inter-area routing, a packet travels along three contiguous paths in a
point-to-multipoint configuration, as follows:
1
An intra-area path from the source to an area border router (ABR)
2
A backbone path between the source and destination areas
3
Another intra-area path to the destination.
Configuring IP Routing and Multicast Operations using Device Manager
56
The OSPF routing algorithm finds the set of such paths that has the smallest cost.
The topology of the backbone dictates the backbone paths used between areas.
Inter-area paths are selected by examining the routing table summaries for each
connected ABR. The OSPF behavior has been modified according to OSPF
standards so that OSPF routes cannot be learned through an area border router
(ABR) unless it is connected to the backbone or through a virtual link.
Stub area
A stub area is configured at the edge of the OSPF routing domain and has only
one ABR. A stub area does not receive LSAs for routes outside its area, reducing
the size of its link-state database. A packet destined outside the stub area is routed
to the ABR, which examines it before forwarding the packet to its destination. The
network behind a passive interface is treated as a stub area, and does not form
adjacencies. It is advertised into the OSPF area as an internal route.
Neighbors
In an OSPF network, any two routers that have an interface to the same network
are neighbors. Routers use the Hello Protocol to discover their neighbors and
maintain neighbor relationships. On a broadcast or point-to-point network, the
Hello Protocol dynamically discovers neighbors.
The Hello Protocol provides bidirectional communication between neighbors.
Periodically OSPF routers send out hello packets over all interfaces. Included in
these hello packets is the following information:
•
•
•
•
The router priority
The router Hello Timer and Dead Timer values
A list of routers that have sent this router hello packets on this interface
The router choice for designated router (DR) and backup designated router
(BDR)
Bidirectional communication is determined when one router discovers itself listed
in the hello packet of a neighbor.
321712-B Rev 03
57
Neighbor adjacencies
Neighbors may form an adjacency for the purpose of exchanging routing
information. When two routers form an adjacency, they go through a database
exchange process to synchronize their topological databases. When their
databases are synchronized, the routers are said to be fully adjacent. Bandwidth is
conserved because, from this point on, only routing change information is passed
between the adjacent routers.
OSPF routers
To limit the amount of routing protocol traffic, the Hello Protocol elects a
designated router (DR) and a backup designated router (BDR) on each
multiaccess network. Instead of neighboring routers forming adjacencies and
swapping link-state information with each other (which on a large network can
mean a lot of routing protocol traffic), all routers on the network form adjacencies
with the DR and the BDR only and send link-state information to them. The DR
redistributes this information to every other adjacent router.
When operating in backup mode, the BDR receives link-state information from all
routers on the network and listens for acknowledgements. If the DR fails, the
BDR can transition quickly to the role of DR because its routing tables are
up-to-date.
Configuring IP Routing and Multicast Operations using Device Manager
58
Router types
Routers in an OSPF network can take on different roles depending on how they
are configured. Table 3 describes the router types you can configure in an OSPF
network.
Table 3 Router types in an OSPF network
Router Type
Description
AS boundary router
(ASBR)
A router attached at the edge of an OSPF network is called an AS
boundary router (ASBR). An ASBR generally has one or more
interfaces that run an inter-domain routing protocol. In addition,
any router distributing static routes or RIP routes into OSPF is
considered an ASBR. The ASBR forwards external routes into the
OSPF domain. In this way, routers inside the OSPF network learn
about destinations outside their domain.
Area border router
(ABR)
A router attached to two or more areas inside an OSPF network is
considered an area border router (ABR). ABRs play an important
role in OSPF networks by condensing the amount of OSPF
information that is disseminated.
Internal router (IR)
A router that has interfaces only within a single area inside an
OSPF network is considered an internal router (IR). Unlike ABRs,
IRs have topological information only about the area in which they
are contained.
Designated router
(DR)
In a broadcast network a single router is elected to be the
designated router (DR) for that network. A DR assumes the
responsibility of making sure all routers on the network are
synchronized with one another and also advertises that network to
the rest of the AS.
Backup designated
router (BDR)
A backup designated router (BDR) is elected in addition to the
designated router (DR) and, in the event of failure of the DR,
assumes its role quickly.
OSPF interfaces
An OSPF interface, or link, is configured on an IP interface. In the Ethernet
Routing Switch 1600 Series, an IP interface is a logical interface configured on a
VLAN (multiple ports). The state information associated with the interface is
obtained from the underlying lower level protocols and the routing protocol itself.
321712-B Rev 03
59
OSPF and IP
OSPF runs on top of IP, which means that an OSPF packet is sent with an IP data
packet header. The protocol field in the IP header is set to 89, which identifies it as
OSPF, distinguishing it from other packets that use an IP header.
A destination in an OSPF route advertisement is expressed as an IP address and a
variable-length mask. Taken together, the address and the mask indicate the range
of destinations to which the advertisement applies.
The ability to specify a range of networks allows OSPF to send one summary
advertisement that represents multiple destinations. For example, a summary
advertisement for the destination 128.185.0.0 with a mask of 255.255.0.0
describes a single route to destinations 128.185.0.0 to 128.185.255.255.
OSPF packets
All OSPF packets start with a 24-octet header that contain information about the
OSPF version, the packet type and length, the ID of the router transmitting the
packet, and the ID of the OSPF area from which the packet is sent. An OSPF
packet can be one of the following types:
•
Hello packets
Hello packets are transmitted between neighbors and are never forwarded.
The Hello Protocol requires routers to send hello packets to neighbors at
predefined hello intervals. If hello packets are not received by a neighbor
router within the specified dead interval, the neighbor router declares the
other router dead.
•
Database description (DD) packets
DD packets are exchanged when a link is first established between
neighboring routers that synchronize their link state databases.
•
Link state request packets
Link state request packets describe one or more link state advertisements that
a router is requesting from its neighbor. Routers send link state requests if the
information received in DD packets from a neighbor is not consistent with its
own link state database.
•
Link state update packets
Configuring IP Routing and Multicast Operations using Device Manager
60
Link state update packets contain one or more link state advertisements, and
are sent following a change in network conditions.
•
Link state acknowledgement packets
Link state acknowledgement packets are sent to acknowledge receipt of link
state updates, containing the headers of the link state advertisements that were
received.
Link state advertisements
OSPF does not require each router to send its entire routing table to its neighbors.
Instead, each OSPF router floods only link-state change information in the form
of link-state advertisements (LSAs) throughout the area or AS. LSAs in OSPF are
one of the following five types:
•
Router links advertisement
A router links advertisement is flooded only within the area and contains
information about neighbor routers and the LANs to which the router is
attached. A backbone router can flood router link advertisements within the
backbone area.
•
Network links advertisement
A network links advertisement is generated by a DR on a LAN, listing all
routers on that LAN and flooding only within the area. A backbone DR can
flood network links advertisements within the backbone area.
•
Network summary link advertisement
A network summary link advertisement is flooded into an area by an ABR
that describes networks that are reachable outside the area. An ABR attached
to two areas will generate a different network summary link advertisement for
each of these areas. ABRs also generate area summary link advertisements
containing information about destinations within an area, which are flooded to
the backbone area.
•
ASBR summary link advertisement
An ASBR summary link advertisement describes the cost of the path to an
ASBR from the router generating the advertisement.
•
321712-B Rev 03
AS external link advertisement
61
An AS external link advertisement is sent by an ASBR to describe the cost of
the path to a destination outside the AS from the ASBR generating the
advertisement. This information is flooded to all routers in the AS.
AS external routes
OSPF considers the following routes to be AS external (ASE) routes:
•
•
•
•
•
A route to a destination outside the AS
A static route
A default route
A route derived by RIP
A directly connected network not running OSPF
OSPF virtual links
On an OSPF network, an Ethernet Routing Switch 1600 Series that is acting as an
ABR must be connected directly to the backbone. If no physical connection is
available, a virtual link can be established, which you can configure manually.
Figure 10 shows how to configure a virtual link between the ABR in area 2.2.2.2
and the ABR in area 0.0.0.0.
Figure 10 Virtual link between ABRs through a transit area
Configuring IP Routing and Multicast Operations using Device Manager
62
To configure a virtual link between the ABRs in Area 1 and Area 3, define Area 2
as the transit area between the other two areas, and identify switch S2 as the
neighbor router through which switch S2 must send information to reach the
backbone via switch S1.
Specifying ASBRs
ASBRs advertise non-OSPF routes into OSPF domains so that they can be passed
along throughout the OSPF routing domain. A router can function as an ASBR if
one or more of its interfaces is connected to a non-OSPF network (for example,
RIP or EGP).
To conserve resources, you may want to limit the number of ASBRs in your
network or specifically control which routers perform as ASBRs to control traffic
flow.
321712-B Rev 03
63
Circuitless IP (CLIP)
Circuitless IP (CLIP) is a virtual (or loopback) interface that is not associated with
any physical port. The CLIP interface is used to provide uninterrupted
connectivity to the switch as long as there is an actual path to reach the device.
In most environments, the router has multiple alternative paths to peers, but
frequent port up and port down events cause the TCP session to reset. To
minimize communication disruptions, specify a CLIP interface to form the peer
relationship with neighbors.
Figure 11 is an example of a configuration in which router R1 (IP address
195.39.1.1/30) has been configured with a loopback interface (CLIP 1, IP address
195.39.128.1/32) and router R2 (IP address 195.39.1.2/30) has also been
configured with a loopback interface (CLIP 2, IP address 195.39.128.2/32). As
long as there is a physical path from R1 to R2, the virtual link between CLIP 1 and
CLIP 2 is not interrupted.
Figure 11 CLIP (loopback) Configuration
The CLIP interface functions like any other IP interface. The network associated
with the CLIP interface is treated as a local network attached to the device. This
route always exists and the circuit is always up because there is no physical
attachment. The switch advertises this route to other routers in the domain.
Configuring IP Routing and Multicast Operations using Device Manager
64
When a CLIP interface is created, the system software programs a local route with
the CPU as destID. All packets that are destined to the CLIP interface address are
processed by the CPU. Any other packets with destination addresses associated
with this network (but not to the interface address) are treated like packets from
any unknown host.
Almost any routing protocol can be configured on the CLIP interface. However,
the CLIP feature primarily benefits protocols involving session-based
communication.
Note: PIM over CLIP is not supported in this release.
For more information about configuring CLIP, refer to “Configuring IP Routing”
on page 91.
UDP forwarding
Some network applications, such as the NetBIOS name service, rely on a UDP
broadcast to request a service or locate a server for an application. If a host is on a
network, subnet segment, or VLAN that does not include a server for the service,
UDP broadcasts are, by default, not forwarded to the server located on a different
network segment or VLAN. This problem is resolved by forwarding the
broadcasts to the server through physical or virtual router interfaces.
UDP forwarding is a general mechanism for selectively forwarding limited UDP
broadcasts received on an IP interface out to other router IP interfaces as a
rebroadcast or to a configured IP address.
•
•
If the address is that of a server, the packet is sent as a unicast packet to this
address.
If the address is that of an interface on the router, the frame is rebroadcast.
When a UDP broadcast is received on a router interface, it must meet the
following criteria if it is to be considered for forwarding:
•
•
321712-B Rev 03
be a MAC-level broadcast
be an IP limited broadcast
65
•
•
be for the specified UDP protocol
have a TTL value of at least 2
The forwarding policy specifies how to retransmit UDP broadcasts for each
interface and protocol: to a unicast host address, or to a broadcast address.
For more information about using Device Manager to configure UDP forwarding,
refer to “Configuring UDP Forwarding” on page 219.
Overview of IP multicast
This section provides an overview of IP multicast and includes the following
topics:
•
•
•
“Multicast addresses” on page 67
“IP Multicast address ranges” on page 67
“IP to Ethernet multicast MAC mapping” on page 68
IP multicast transmits messages to multiple recipients at the same time. This
one-to-many delivery mechanism is similar to broadcasting, except multicasting
transmits to specific groups and broadcasting transmits to everybody. Since
multicast transmits only one stream of data to the network where it is replicated to
many receivers, multicasting saves a considerable amount of bandwidth.
IP multicast provides services such as the delivery of information to multiple
destinations with a single transmission and the solicitation of servers by clients. IP
multicast services benefit applications such as video conferencing, dissemination
of datagram information, and dissemination of mail or news to a large number of
recipients.
Multicast protocols use different techniques to discover delivery paths.
A Distribution Tree is a set of multicast routers and subnetworks through which
the group members receive traffic from a source. The tree’s source depends on the
algorithm used by the multicast protocol. Figure 12 is an example of a simple
distribution tree, where S is the multicast source and the arrows indicate the
multicast broadcast procedure.
Configuring IP Routing and Multicast Operations using Device Manager
66
Figure 12 Multicast distribution tree
S
9580EA
Reverse path forwarding in multicast is based on the concept that a multicast
distribution tree must be built based on the shortest path from the source to each
network and subnetwork containing active receivers. When a datagram arrives on
an interface, the router determines the reverse path to the source of the datagram
by examining the routing table of known network sources. If the datagram is not
on the optimal path to source, it is discarded.
Multicast host groups and their group members enable the IP multicast router to
transmit just to those groups interested in receiving the traffic. The Ethernet
Routing Switch 1600 Series uses the Internet Group Membership Protocol
(IGMP) to learn the existence of host group members on their directly attached
subnets. A router communicates with the hosts on a local network by sending
IGMP queries. The Ethernet Routing Switch 1600 Series supports IGMP snoop
and can act as a querier if PIM is enabled. For more information, see “IGMP
queries” on page 72 and “Multicast addresses” on page 67. IGMP is described in
more detail in page 71.
Multicast traffic forwarding transmits frames to all interfaces and subnets on
which IGMP reports have been received for the multicast group indicated in the
destination IP address. Multicast packets forwarded within the same VLAN
remain unchanged. Packets are not forwarded to networks with no members of the
multicast group indicated in the destination IP address. The group member is the
VLAN port on which the IGMP receiver exists, so the traffic is forwarded only to
such VLAN ports, and not to all VLAN ports. For more information, see “IGMP
Snoop” on page 73.
321712-B Rev 03
67
Multicast addresses
Each multicast host group is assigned a unique multicast address. To reach all
members of the group, a sender uses the multicast address as the destination
address of the datagram.
An IP version 4 multicast address is a Class D address (the high-order bits are set
to 1110) from 224.0.0.0 to 239.255.255.255. These addresses are assigned
statically for use by permanent groups and dynamically for use by transient
groups.
Note: On the 1600 Series switch, 24-bit subnets, like 224.0.0.0/24 and
224.128.0.0/24 must not be used for multicast data traffic. This
restriction applies to the entire multicast address range from 224.0.0.0/8
to 239.128.0.0/8.
The Ethernet Routing Switch 1600 Series uses multicast MAC addresses to switch
IP multicast data at Layer 2. Thus, several IP multicast addresses can map to the
same multicast MAC address. The subsections that follow explain IP multicast
addressing in more detail.
IP Multicast address ranges
IP multicast utilizes D class addresses, which range from 224.0.0.0 to
239.255.255.255. Although subnet masks are commonly used to configure IP
multicast address ranges, the concept of subnets does not exist for multicast group
addresses. Consequently, the usual unicast conventions where you reserve the all
0s subnets, all 1s subnets, all 0s host addresses, and all 1s host addresses does not
apply when dealing with the IP multicast range of addresses.
Addresses from 224.0.0.0 through 224.0.0.255 are reserved by IANA for
link-local network applications. Packets with an address in this range are not
forwarded by multicast capable routers by design. For example, OSPF uses both
224.0.0.5 and 224.0.0.6 and VRRP uses 224.0.0.18 to communicate across a local
broadcast network segment.
Configuring IP Routing and Multicast Operations using Device Manager
68
IANA has also reserved the range of 224.0.1.0 through 224.0.1.255 for
well-known applications. These addresses are assigned by IANA to specific
network applications. For example, the Network Time Protocol (NTP) uses
224.0.1.1 and Mtrace uses 224.0.1.32. RFC 1700 contains a complete list of these
reserved numbers.
Multicast addresses in the 232.0.0.0/8 (232.0.0.0 to 232.255.255.255) range are
reserved only for source-specific multicast applications, such as one-to-many
applications. While this is the publicly reserved range for SSM applications,
private networks can use other address ranges for SSM.
Finally, addresses in the range 239.0.0.0/8 (239.0.0.0 to 239.255.255.255) are
administratively scoped addresses, meaning they are reserved for use in private
domains and must not be advertised outside that domain. This multicast range is
analogous to the 10.0.0.0/8, 172.16.0.0/20, and 192.168.0.0/16 private address
ranges in the unicast IP space.
Technically, a private network can only assign multicast addresses from 224.0.2.0
through 238.255.255.255 to applications that are publicly accessible on the
Internet. Multicast applications that are not publicly accessible can be assigned
addresses in the 239.0.0.0/8 range.
IP to Ethernet multicast MAC mapping
Like IP, Ethernet has a range of multicast MAC addresses that natively support
Layer 2 multicast capabilities. While IP has a total of 28 addressing bits available
for multicast addresses, Ethernet has only 23 addressing bits assigned to IP
multicast. Ethernet’s multicast MAC address space is much larger than 23 bits,
but only a subrange of that larger space has been allocated to IP multicast by the
IEEE. Because of this difference, 32 IP multicast addresses map to one Ethernet
multicast MAC address.
IP multicast addresses map to Ethernet multicast MAC addresses by placing the
low-order 23 bits of the IP address into the low-order 23 bits of the Ethernet
multicast address 01:00:5E:00:00:00. Thus, more than one multicast address maps
to the same Ethernet address (Figure 13). For example, all 32 addresses 224.1.1.1,
224.129.1.1, 225.1.1.1, 225.129.1.1, 239.1.1.1, 239.129.1.1 map to the same
01:00:5E:01:01:01 multicast MAC address.
321712-B Rev 03
69
Figure 13 Multicast IP address to MAC address mapping
224.0.0.0
224.0.0.1
224.0.0.2
.
.
.
.
.
.
0100.5E00.0000
224.127.255.255
.
.
.
.
.
.
224.128.0.0
28 Bits
224.128.0.1
224.128.0.2
0100.5E00.0001
0100.5E00.0002
23 Bits
0100.5E7F.FFFF
.
.
.
.
.
.
224.255.255.255
225.0.0.0
.
.
.
.
.
.
Most Ethernet switches handle Ethernet multicast by mapping a multicast MAC
address to multiple switch ports in the MAC address table. Therefore, when
designing the group addresses for multicast applications, take care to efficiently
distribute streams only to hosts that are receivers. The Ethernet Routing Switch
1600 Series switches IP multicast data based on the IP multicast address and not
the MAC address and thus, does not have this issue.
As an example, consider two active multicast streams using addresses 239.1.1.1
and 239.129.1.1. Suppose two Ethernet hosts, receiver A and receiver B, are
connected to ports on the same switch and only want the stream addressed to
239.1.1.1. Suppose also that two other Ethernet hosts, receiver C and receiver D,
are also connected to the ports on the same switch as receiver A and B and wish to
receive the stream addressed to 239.129.1.1. If the switch utilizes the Ethernet
multicast MAC address to make forwarding decisions, then all four receivers
receive both streams, even though each host only wants one or the other stream.
This increases the load on both the hosts and the switch. To avoid this extra load,
Nortel recommends that you manage the IP multicast group addresses used on the
network.
Configuring IP Routing and Multicast Operations using Device Manager
70
At the same time, however, it is worth noting that the Ethernet Routing Switch
1600 Series does forward IP multicast packets based on multicast MAC addresses
when bridging VLANs at layer 2. Thus, the Ethernet Routing Switch 1600 Series
does not encounter this problem. Instead, it internally maps IP multicast group
addresses to the ports that contain group members.
When an IP multicast packet is received, the lookup is based on IP group address,
regardless of whether the VLAN is bridged or routed. Be aware that, while the
Ethernet Routing Switch 1600 Series does not suffer from the problem described
in the previous example, other switches in the network might. This is particularly
true of pure Layer 2 switches.
In a network that includes non-Ethernet Routing Switch 1600 Series equipment,
the easiest way to ensure that this issue does not arise is to use only a consecutive
range of IP multicast addresses corresponding to the lower order 23 bits of that
range. For example, use an address range from 239.0.2.0 through
239.127.255.255. A group address range of this size can still easily accommodate
the addressing needs of even the largest private enterprise.
321712-B Rev 03
71
Internet Group Management Protocol (IGMP)
This section provides an overview of Internet Group Management Protocol
(IGMP) and includes the following topics:
•
•
•
•
•
•
•
“IGMP queries” on page 72
“IGMP host reports” on page 72
“Host leave messages” on page 73
“Fast-leave feature” on page 73
“IGMP Snoop” on page 73
“IGMP proxy” on page 75
“IGMP versions” on page 75
IGMP is a protocol used by IP multicast routers to learn the existence of host
group members on their directly attached subnets. With IGMP, hosts can
communicate their desired group memberships to their local querier router, and
receive any datagrams sent to this router and targeted to a group with a specific IP
multicast address.
A router communicates with the hosts on a local network by sending IGMP
queries. Hosts respond by issuing IGMP reports.
IGMP has the following characteristics:
•
•
A host can register group memberships with the local querier router to receive
any datagrams sent to this router and targeted to a group with a specific IP
multicast address.
A router can learn the existence of group members on networks to which it is
directly attached. The router periodically sends a general query message to
each of its local networks. Any host that is a member of any multicasting
group identifies itself by sending a response.
Configuring IP Routing and Multicast Operations using Device Manager
72
IGMP queries
When there are multiple IGMP routers on a network, the router with the lowest IP
address is elected to send queries. This elected querier periodically sends host
membership queries (also known as general queries) to its attached local subnets.
The Ethernet Routing Switch 1600 Series can act as a querier if PIM is enabled.
The Ethernet Routing Switch 1600 supports IGMPv1 and IGMPv2 queries.
IGMP host reports
A host that receives a membership query from a local router can respond with a
host membership report, one report for each joined multicast group. A host that
receives a query delays its reply by a random interval and listens for a reply from
any other host in the same host group. Consider a network that includes two host
members—host A and host B—of the same multicast group. The router sends out
a host membership query on the local network. Both host A and host B receive the
query and listen on the network for a host membership report. Host B’s delay
timer expires first, so it responds to the query with a membership report. Hearing
the response, host A does not send a report of its own for the same group.
Each query from a router to a host includes a Maximum Response Time field.
IGMP inserts a value—n—into this field specifying the maximum time, in tenths
of a second, within which the host must issue a reply. The host uses this value to
calculate a random value between 0 and n tenths of a second for the period that it
waits before sending a response. This is true for IGMP version 2. For IGMP
version 1, this field is set to 0 but defaults to a value of 100, that is, 10 seconds.
If at least one host on the local network specifies that it is a member of a given
group, the router forwards all datagrams bearing the group’s multicast address to
that network.
Upon initialization, the host may immediately issue a report for each of its
supported multicast groups. The router accepts and processes these asynchronous
reports the same way it accepts requested reports.
321712-B Rev 03
73
After hosts and routers are in a steady state, they communicate in a way that
minimizes the exchange of queries and reports. The designated routers set up a
path between the IP Multicast stream source and the end stations and periodically
query the end stations about whether or not to continue participation. As long as
any client continues to participate, all clients, including nonparticipating end
stations on the switch port, receive the IP Multicast stream.
Host leave messages
When an IGMP version 2 host leaves a group and it was the host that issued the
most recent report, it issues a leave group message. The multicast router on the
network issues a group-specific query to determine whether there are other group
members on the network. If no host responds to the query, the router assumes that
no members belonging to that group exist on that interface.
Fast-leave feature
The 1600 Series switches support a fast-leave feature that is useful for
applications such as multicast-based TV distribution. Fast-leave relies on an
alternative leave process in which the switch stops sending traffic for the group
immediately after receiving a leave message, without issuing a query to check if
other group members are present on the network. Fast-leave alleviates the
network from additional bandwidth demand when changing TV channels.
For information about configuring fast leave, refer to “Configuring IGMP” on
page 227.
IGMP Snoop
The Ethernet Routing Switch 1600 Series can provide IP multicast capability as a
Layer 2 switch. When functioning as a Layer 2 switch, it supports IGMPv1 and
IGMPv2 to prune group membership per port within a VLAN. This feature is
called IGMP snoop and you can use it to optimize the multicast data flow for a
group within a VLAN to only those ports that are members of the group.
Configuring IP Routing and Multicast Operations using Device Manager
74
The switch builds a database of group members by listening to IGMP reports from
each port. It suppresses the reports heard by not forwarding them out to ports
other than the one receiving the report, forcing the members to continuously send
their own reports. The switch relays group membership from the hosts to the
multicast routers. It forwards queries from multicast routers to all port members of
the VLAN. Furthermore, it forwards multicast data only to the participating group
members and to the multicast routers within the VLAN.
For IGMP snooping to function properly on a VLAN of Layer 2 switching
devices, the VLAN must be linked to a Layer 3 multicast-enabled device like the
Ethernet Routing Switch 1600 or Ethernet Routing Switch 8600.
Static mrouter port and non-querier
IGMP snoop considers the port on which the IGMP query is received as the active
IGMP multicast router (mrouter) port. An IGMP router acts as non-querier if the
VLAN has another IGMP router with a lower IP address. Non-queriers do not
send an IGMP query. IGMP snoop is not aware of non-querier IGMP routers.
Therefore, configure ports connected to the non-querier as the static mrouter port
for the IGMP snoop interface.
For example, when you enable IGMP snoop on VLAN 10, mrouter1 is the IGMP
querier because it has a lower IP address than the other multicast router in VLAN
10. Mrouter 2 is then considered the non-querier. In Figure 14, VLAN 10 on the
1600 Series switch has port member 1/5, 1/6 connected to IGMP routers. In this
example, IGMP router 1 is the querier because it has a lower IP address than
IGMP router 2.
Figure 14 Static mrouter port and non-querier
IGMP
router 1
IGMP
router 2
192.16.0.2
192.16.0.1
1/5
1/6
Ethernet Routing Switch 1600
321712-B Rev 03
75
For more information about configuring IGMP snoop, refer to “Configuring
IGMP” on page 227.
IGMP proxy
When configured with IGMP proxy function, a 1600 Series switch receives
multiple reports for the same multicast group, but does not transmit each report to
the multicast upstream router. Instead, the switch forwards the first report to the
querier and suppresses the rest. If there is new information that another multicast
group has been added or that a query has been received since the last report was
transmitted upstream, then the report is forwarded to the multicast router ports.
For information about configuring IGMP proxy, see “Configuring IGMP” on
page 227.
IGMP versions
The 1600 Series switches support IGMPv1 and IGMPv2. The versions are
backward compatible and they can all exist together on a multicast network. Both
IGMPv1 and IGMPv2 support multicast with the difference being that IGMPv2
supports an IGMP leave message to allow a quick leave from a multicast group.
With IGMPv1, there is no IGMP leave message.
The following describes the main purpose for each version:
•
IGMPv1 provides the support for IP multicast routing. IGMPv1 specifies the
mechanism for communicating IP multicast group membership requests from
a host to its locally attached routers. Figure 15 shows an example of how
IGMPv1 works.
Configuring IP Routing and Multicast Operations using Device Manager
76
Figure 15 IGMPv1
Querier
General
Query
X
X
Suppressed
Suppressed
REPORT
11040fz
In this example:
•
— the host leaves a group
— the router sends three general queries (60 seconds apart) for IGMP
records
— if no IGMP report is received for the group, the group times out
— in a worst case scenario, a group timeout lasts three minutes
IGMPv2 extends the features in IGMPv1 by quickly reporting group
membership termination to the routing protocol. This feature is important for
multicast groups with highly volatile group membership. Figure 16 on
page 76 shows an example of how IGMPv2 works.
Figure 16 IGMPv2
Querier
Group-specific query
to 239.1.1.1
X
Leave to 224.0.0.2
X
Suppressed
239.1.1.1
11040fy
In this example:
— the host sends a leave message to 224.0.0.2
— the router sends a group-specific query to 239.1.1.1
— no IGMP report is received
321712-B Rev 03
77
— group 239.1.1.1 times out
IGMP RFCs
For additional information about IGMP, see the following RFCs:
•
•
•
•
For IGMPv1, refer to RFC 1112.
For IGMPv2, refer to RFC 2236.
For IGMP MIBs, refer to RFC 2933
For IANA considerations for IPv4, refer to RFC 3328
Protocol Independent Multicast-Sparse Mode (PIM-SM)
Protocol Independent Multicast-Sparse Mode (PIM-SM), as defined in RFC 2362,
was designed to support multicast groups spread out across large areas of a
company or the Internet. Unlike dense mode protocols, such as DVMRP, that
initially flood multicast traffic to all routers over an entire internetwork, PIM-SM
sends multicast traffic only to routers that have specifically joined a multicast
group. This technique reduces traffic flow over WAN links and overhead costs for
processing unwanted multicast packets.
Dense-mode protocols use a “flood-and-prune” technique, which is efficient
where receivers are densely populated. However, for sparsely populated networks,
PIM-SM is more efficient because it sends multicast traffic only to those routers
that belong to a specific multicast group and that choose to receive the traffic.
PIM-SM is independent of any specific unicast routing protocol, but it does
require the presence of a unicast routing protocol, such as RIP or OSPF. PIM-SM
uses the information from the unicast routing table to create and maintain
multicast trees that enables PIM-enabled routers to communicate.
Configuring IP Routing and Multicast Operations using Device Manager
78
PIM-SM concepts and terminology
Typically, a PIM-SM network consists of several multipoint data streams, each
targeted to a small number of LANs in the internetwork. For example, customers
whose networks consist of multiple hosts on different LANs can use PIM-SM to
simultaneously access a video data stream, such as a video teleconference, on a
different subnet.
Note: In some cases, PIM stream initialization can take several seconds.
Hosts
A host can be a source, a receiver, or both.
•
•
A source, also known as a sender, sends multicast data to a multicast group.
A receiver receives multicast data from one or several sources sending data to
a multicast group.
PIM-SM domain
PIM-SM operates in a domain of contiguous routers that have PIM-SM enabled.
Each PIM-SM domain requires the following routers:
•
•
•
Designated router (DR)
Rendezvous-point (RP) router
Bootstrap router (BSR)
Although a PIM-SM domain can have only one active RP router and one active
BSR, you can configure additional routers as candidate RP routers and as
candidate BSRs. Candidate routers provide backup protection in case the primary
RP or BSR router fails.
321712-B Rev 03
79
Designated router (DR)
The designated router (DR) is the router with the highest IP address on a LAN
designated to perform the following tasks:
•
•
•
Sends register messages to the rendezvous-point (RP) router on behalf of
directly connected sources.
Sends join/prune messages to the RP router on behalf of directly connected
receivers.
Maintains information about the status of the active RP router for local
sources in each multicast group.
Note: The DR is not a required configuration and switches act
automatically as such for directly attached sources and receivers.
Rendezvous-Point (RP) router
PIM-SM builds a shared multicast distribution tree within each domain, and the
rendezvous point (RP) is at the root of this shared tree. Although the RP can be
physically located anywhere on the network, it should be as close to the source as
possible. There is only one active RP router for a multicast group.
The RP router is where receivers meet new sources. Sources use the RP to identify
themselves to other routers on the network; receivers use the RP to learn about
new sources.
The RP performs the following tasks:
•
•
•
Registers a source that wants to announce itself and send data to group
members
Joins a receiver that wants to receive data for the group
Forwards data to group
Configuring IP Routing and Multicast Operations using Device Manager
80
Candidate rendezvous-point router
You can configure a set of routers as candidate rendezvous-point (C-RP) routers
that serve as backup to the RP router. If an RP fails, all the routers in the domain
apply the same algorithm to elect a new RP from the group of C-RPs. To make
sure that the routers have a complete list of C-RPs, the C-RP periodically sends
unicast advertisement messages to the bootstrap router (BSR). The most common
implementation is to configure a PIM-SM router as both a candidate RP and a
candidate BSR.
Bootstrap router
The BSR receives RP router advertisement messages from the candidate RPs. The
BSR adds the RP router with its group prefix to the RP set. Only one BSR exists
for each PIM-SM domain.
The BSR periodically sends bootstrap messages containing the complete RP set to
all routers in the domain. The BSR ensures that all PIM-SM routers learn to which
RP router to send join/prune and register packets.
Candidate bootstrap router
Within a PIM-SM domain, you can configure a small set of routers as candidate
BSRs (C-BSRs). The candidate BSR with the highest configured priority becomes
the BSR for the domain. If two candidate BSRs have equal priority, the candidate
with the higher IP address becomes the BSR. If you add a new candidate BSR
with a higher priority to the domain, it automatically becomes the new BSR.
Shared trees and shortest-path trees
In a PIM-SM domain, shared trees and shortest-path trees are used to deliver data
packets to group members. This section describes both trees.
Shared trees
Group members in a PIM-SM domain receive the first packet of data from sources
across a shared tree. A shared tree consists of a set of paths that connect all
members of a multicast group to the RP. PIM creates a shared tree when sources
and receivers send messages toward the RP.
321712-B Rev 03
81
Shortest-path trees
After receiving a certain number of packets from the RP, the DR switches from
a shared tree to a shortest-path tree (SPT). Switching to a shortest-path tree
creates a direct route between the receiver and the source. The 1600 Series
implementation switches to the SPT when it receives the first packet from the RP.
Figure 17 shows a shared tree and a shortest-path tree.
Figure 17 Shared tree and shortest-path tree
Source
S
LAN
DR
Shared-tree
path
Shortest-path
tree (SPT)
R
DR
RP
Receiver
Last-hop
router
Shared-tree path
Key
R
PIM router
RP
Rendezvouspoint router
DR
Designated
router for LAN
Ethernet Routing
Switch 1600
Configuring IP Routing and Multicast Operations using Device Manager
82
Join/prune messages
The DR sends join/prune messages from a receiver toward a group’s RP to either
join the shared tree or remove (prune) a branch from it. A single message contains
both a join and a prune list. This list includes a set of source addresses indicating
the shortest-path trees or the shared trees that the host wants to join. The DR sends
join and prune messages hop by hop to each PIM router on the path to the source
or the RP.
Register and register-stop messages
The DR sends register messages to the RP for a directly connected source. The
register message informs the RP of a new source, causing the RP to send
join/prune messages back toward the source’s DR and forwards the data down the
RP tree after it gets the data natively. When the receiver DR gets the first packet, it
switches to the shortest-path tree (SPT) and continues receiving data through the
SPT path.
The DR stops sending encapsulated packets to the RP after receiving a
register-stop message. This traffic stops without any delay because the RP sends a
register-stop message immediately after receiving the first multicast data packet,
and joins the shortest-path tree.
Receiver joining group
The following steps describe how a receiver joins a multicast group:
1
A receiver multicasts an IGMP host membership message to the group that it
wants to join.
2
When the DR (normally the PIM router with the highest IP address for that
VLAN) receives the IGMP message for a new group, the DR looks up the
associated active RP.
3
After determining the RP router for the group, the DR creates a (*,G) route
entry in the multicast forwarding table and sends a (*,G) join to the RP. When
the DR receives data packets from the RP, the DR switches to shortest path,
creates an (S,G) entry in the multicast forwarding table and sends (S,G) join
to the source.
4
All intermediate routers along the path to the source create the (S,G) entry.
321712-B Rev 03
83
5
The DR receives data from the data source using the SPT.
Receiver leaving group
Before it leaves a multicast group, a receiver sends an IGMP leave message to the
DR. If all directly connected members of a multicast group leave or time out and
no downstream members remain, the DR sends a prune message upstream and
PIM-SM deletes the route entry after that entry times out.
Source sending packets to group
The following steps describe how a source sends multicast packets to a group:
1
A source directly attached to a VLAN bridges the multicast data to the DR.
The DR for the VLAN (the router with the highest IP address) encapsulates
each packet in a register message and sends a unicast message directly to the
RP router to distribute to the multicast group.
2
If a downstream group member chooses to receive multicast traffic, the RP
router sends a join/prune message towards the source DR and forwards the
data down the RP tree after it gets the data natively.
3
When the receiver DR gets the first packet, it switches to the shortest-path tree
(SPT) and continues receiving data through the SPT path.
4
If no downstream members want to receive multicast traffic, the RP router
sends a register-stop message to the DR for the source.
The DR starts the register suppression timer upon receiving the first
register-stop message. During the register suppression timeout period (the
default is 60 seconds), the following events occur:
•
•
The source’s DR sends a probe packet to the RP router before the register
suppression timer expires. The probe packet prompts the RP router to
determine whether any new downstream receivers have joined the group.
If no new receivers have joined the group, the RP router sends another
register-stop message to the source’s DR, and its register suppression
timer restarts.
Configuring IP Routing and Multicast Operations using Device Manager
84
•
When the RP router no longer responds with a register-stop message to
the source DR probe message, the register suppression timer expires and
the DR sends encapsulated multicast packets to the RP router. The RP
router uses this method to tell the DR that new members have joined the
group.
The RP sends a register-stop message to the DR immediately after receiving the
first multicast data packet
Required elements for PIM-SM operation
For PIM-SM to operate, a number of elements must be present in the PIM-SM
domain including the following:
•
•
•
321712-B Rev 03
An underlying unicast routing protocol must be enabled for the switch to
provide routing table information to PIM-SM
In a PIM-SM domain, an active BSR must be in place to send bootstrap
messages to all PIM-V2 configured switches and routers to enable them to
learn group-to-RP mapping. If several BSRs are configured in a network, an
active BSR is elected based on priority and IP address (if priority is equal, the
BSR with the higher IP address is elected).
An RP must be in place in the PIM-SM domain to perform the following
tasks:
— To manage one or several IP Multicast groups
— To become the root for the shared tree to these groups
— To accept join messages from receiver switches for groups that it
manages
85
— If there is more than one RP that have groups in common, the RPs “elect”
an active RP based on priority and IP address (if priority is equal, the RP
with the higher IP address is elected)
Note: If two IGMP routers are active in the same VLAN, the router with
the lowest IP address is elected as the querier. Any Layer 2
snoop-enabled switches exchange IGMP information with this querier.
However, if the same two routers are then enabled with PIM, the router
with the highest IP address is elected as the PIM DR. In this case, the
Layer 2 hosts still attempt to communicate with the lower IP querier, but
the host reports cannot reach the PIM domain. To communicate properly
with the PIM-enabled routers, the Layer 2 switch must send IGMP
reports to the non-querier (the PIM DR).
To work around this issue, enable Multicast Router Discovery on the
switch and routers. With Multicast Router Discovery enabled, the
Layer 2 switch learns all multicast router ports (ports connected to any
Layer 3 multicast routers). Therefore, the switch sends IGMP reports to
all Layer 3 multicast routers (including the PIM DR and non-DR).
PIM-SM simplified example
Figure 18 shows a simplified example of a PIM-SM configuration.
Configuring IP Routing and Multicast Operations using Device Manager
86
Figure 18 PIM-SM simplified example
Source S
Receiver R for G
RP for G
S1
S2
S4
S3
BSR
Legend
Ethernet Routing
Switch 1600
In the sample configuration, the following events occur:
1
The BSR distributes RP information to all switches in the network
2
R sends a report to S4.
3
Acting on this report, S4 sends (*,G) join to RP
4
S starts sending data to G
5
The DR (S1 in this example) encapsulates the data which it unicasts to RP
(S2) in register messages
6
S2 de-capsulates the data which it forwards to S4
7
S4 forwards the data to R
8
S4 joins S1 because it now knows the source
9
S1 starts forwarding to S4. When S4 receives data from S1, it prunes the
stream from the RP.
Note: Figure 18 is a simplified example and is not the best design for a
network if the source and receiver are placed as shown. In general, RPs
are placed as close to sources as possible.
321712-B Rev 03
87
PIM-SM static source groups
Static source groups enable you to configure static source-group entries in the
PIM-SM multicast routing table. PIM-SM cannot prune these entries from the
distribution tree.
Multicast access control feature
Multicast access control operates with standard existing multicast protocols, and
allows for the configuration of an IP multicast-enabled VLAN with an
access-control policy that consists of several IP multicast groups.
This feature is particularly useful when it is necessary to restrict access to certain
multicast streams and protect multicast streams from spoofing (injecting data to
the existing streams). For example, in a television distribution application, a filter
and a multicast access policy must be applied to each channel (multicast group).
If a television channel is to be added or removed from a package, the multicast
access policy for each VLAN is modified. Multicast access policies contain an ID
and a name (for example, PremiumChannels), the IP multicast addresses, and the
subnet mask to be used.
It is important to note that multicast access control is not a regular filtering
configuration and is specifically designed for multicast streams. It relies on
handling multicast control and initial data to prevent hosts from sending or
receiving specified multicast streams and it does not consume any filters. You can
configure and dynamically change multicast access control to support
configuration changes without having to restart any protocol. This allows for
changes to the access capabilities of a given user dynamically.
Note that multicast access control functionality is applicable to any IP multicast
application where controlling user access is required. Thus, it can be used in
financial and other enterprise applications, such as multicast-based
videoconferencing.
Multicast access control policy types
1600 Series switches support two types of multicast access control policies:
Configuring IP Routing and Multicast Operations using Device Manager
88
•
•
denyRX
denyBoth
The rx policy controls the receivers and egress interface for a group.
denyRX
The denyRX access policy is used to prevent a matching group from receiving
IGMP reports from the matching receiver on the interface where the denyRX
access policy is configured.
For example, in Figure 19 on page 88, a denyRX access policy is configured on
VLAN 2, preventing IGMP reports sent by Receiver 1 from being received on
VLAN 2. The denyRX policy denies a multicast group access to a specific VLAN
or receiver.
Figure 19 Data flow using denyRX policy
denyBoth
The denyBoth access policy is used to prevent a matching IP address from both
sending multicast traffic to, and receiving IGMP reports from, a matching receiver
on an interface where the denyBoth policy is configured. This policy can be used
to eliminate all multicast activity for a receiver or source in a specific multicast
group.
For example, in Figure 20, a denyBoth access policy is configured on VLAN 2,
preventing IGMP reports sent by Receiver 2 from being received by VLAN 2, and
preventing multicast traffic sent by Sender 2 from being forwarded from VLAN 2.
The denyBoth policy prevents certain VLANs from participating in any activity
involving the specified multicast groups.
321712-B Rev 03
89
Figure 20 Data flow using denyBoth policy
Specifying host addresses and masks
When configuring multicast access policies, specify the host (IP) address and host
(subnet) mask of the host that is being filtered (that is, the host that is sending
multicast traffic).
The host subnet mask can be used to restrict access to a portion of the host’s
network. For example, when the host subnet mask is configured as
255.255.255.255, the full host address is used. To restrict access to a portion of
the host’s network, use a subnet mask such as 255.255.255.0. Access control is
then applied to the specified subnet only.
Note: For denyboth access control, group addresses must be the same as
host addresses. The denyboth access control type applies to all hosts that
are transmitting and receiving for that group.
For information about configuring multicast access control, refer to “Configuring
IGMP” on page 227.
Configuring IP Routing and Multicast Operations using Device Manager
90
Multicast MAC filtering
Some network applications rely on a Layer 2 multicast MAC mechanism to send a
frame to multiple hosts for processing. Mirroring is one such application. With the
multicast MAC filtering feature, MAC multicast flooding can be directed to a
specific set of ports.
Note: Multicast MAC filtering can be configured only for local
addresses to a switch. This feature cannot be used as a means to route
traffic between switches.
Basically, the multicast MAC is defined as any MAC address in which the least
significant bit of the most significant byte is set to 1. The multicast MAC filtering
feature is available for Layer 2. (This filtering does not apply to BPDUs.)
In Layer 2, a multicast MAC address generally floods to all ports in the VLAN.
With multicast MAC filtering, a separate flooding domain can be defined for a
given multicast MAC address, which is a subset of the ports on a VLAN. The
maximum number of multicast MAC addresses that can be configured is 100.
Depending upon the overall configuration of the switch this may be limited to
fewer addresses.
To perform multicast MAC filtering, create the VLAN normally and then
manually define a flooding domain (that is, MAC address and port list) for a
specific multicast address. When specifying the multicast MAC flooding domain,
indicate which ports or Multilink Trunks (MLTs) to be considered for multicast
traffic. The actual flooding is then based on whether the specified ports are active
members in the VLAN.
For more detailed information, see “Configuring Multicast MAC Filtering” on
page 247.
321712-B Rev 03
91
Chapter 2
Configuring IP Routing
This section describes how to use the JDM to configure and manage basic IP
routing tasks. It discusses the basic IP router interface configuration required
before any routing protocols, such as ARP, can be configured. For conceptual
information about interface configuration and router management, refer to “IP
routing and multicast concepts” on page 29.
This section includes the following topics:
•
•
•
•
•
•
•
“Router Interface Types” on page 91
“Globally Enabling IP Routing Features” on page 94
“IP Router Management” on page 97
“IP Static Route Table” on page 101
“Configuring CLIP” on page 108
“Configuring IP Route Preferences” on page 112
“Configuring ICMP Router Discovery” on page 114
Router Interface Types
The Ethernet Routing Switch 1600 Series supports virtual router interfaces.
Virtual router interfaces correspond to routing on a virtual port that is associated
with a VLAN. With a virtual router interface, the 1600 Series switch can route IP
traffic to, and from, a VLAN. Because a given port can belong to multiple VLANs
(some of which are configured for routing on the switch and some of which are
not), there is no longer a one-to-one correspondence between the physical port
and the router interface.
Configuring IP Routing and Multicast Operations using Device Manager
92 Chapter 2 Configuring IP Routing
For VLAN routing, the router interface for the VLAN is called a virtual router
interface because the IP address is assigned to an interface on the routing entity in
the switch. This initial interface has a one-to-one correspondence with a VLAN on
any given switch.
To continue, refer to:
•
“Assigning an IP Address to a Virtual Routing Port”
Assigning an IP Address to a Virtual Routing Port
To specify an IP address for a virtual routing port:
1
From the Device Manager menu bar, select IP Routing > IP.
The IP dialog box appears with the Globals tab displayed (Figure 21).
Figure 21 IP dialog box—Globals tab
2
Select the forwarding option button from the Forwarding section.
3
Click Apply.
321712-B Rev 03
Chapter 2 Configuring IP Routing 93
4
Click Close.
5
From the Device Manager menu bar, choose VLAN > VLANs.
The VLAN dialog box appears with the Basic tab displayed (Figure 22).
Figure 22 VLAN dialog box—Basic tab
6
Select a VLAN.
The IP button is enabled.
7
Click IP.
The IP, VLAN dialog box appears with the IP Address tab displayed
(Figure 23).
Figure 23 IP, VLAN dialog box—IP Address tab
Configuring IP Routing and Multicast Operations using Device Manager
94 Chapter 2 Configuring IP Routing
8
Click Insert.
The IP, VLAN, Insert IP Address dialog box appears (Figure 24).
Figure 24 IP, VLAN, Insert IP Address dialog box
9
Enter the IP address and net mask.
Note: Only one IP address can be assigned to any router interface.
Attempting to assign a second IP address returns an invalid IP address
error. The Ethernet Routing Switch 1600 Series can support IP
addresses for up to 512 VLANs.
10 Click Insert.
The new IP address and net mask appears in the IP, VLAN, Insert IP
Address dialog box.
Globally Enabling IP Routing Features
This section describes how to enable IP routing features globally, and contains the
following topics:
•
•
“Enabling IP Forwarding Globally” on page 94
“Enabling Alternative Routes Globally” on page 96
Enabling IP Forwarding Globally
In Device Manager, the IP address of any physical or virtual router interface can
be used for IP-based network management (SNMP, Telnet, and Web).
321712-B Rev 03
Chapter 2 Configuring IP Routing 95
To enable IP forwarding:
1
From the Device Manager menu bar, choose IP Routing > IP.
The IP dialog box appears with the Globals tab displayed (see Figure 21 on
page 92).
2
Select the forwarding option button in the Forwarding section.
3
Click Apply.
Table 4 describes the Globals tab fields.
Table 4 IP dialog box—Globals tab fields
Field
Description
Forwarding
Sets the switch for forwarding (routing) or
not-forwarding. The default is forwarding.
DefaultTTL
Sets the default Time-To-Live (TTL) value for a
routed packet. TTL indicates the maximum number
of seconds elapsed before a packet is discarded.
Enter an integer between 1 and 255. The default
value of 255 is inserted in the TTL field whenever
one is not supplied in the datagram header.
ReasmTimeout
The maximum number of seconds that received
fragments are held while they are waiting for
reassembly at this entity. The default is 30 seconds.
This is a read-only field.
ARPLifeTime
The lifetime of an ARP entry within the system,
global to the switch. The default value is
360 minutes. The range is 1 through 32 767
minutes.
ICMPUnreachableMsgEnable
If checked, enables the generation of ICMP net
unreachable messages if the destination network is
not reachable from this router. These messages
assist in determining if the routing switch is
reachable over the network. The default is disabled
(not checked).
RouteDiscoveryEnable
If checked, enables the ICMP Router Discovery
feature. The default is disabled (not checked).
Configuring IP Routing and Multicast Operations using Device Manager
96 Chapter 2 Configuring IP Routing
Table 4 IP dialog box—Globals tab fields (continued)
Field
Description
AlternativeEnable
Globally enables or disables the alternative-route
feature.
For more information about alternative routes, see
Chapter 1, “IP routing and multicast concepts,” on
page 29.
Note: If the alternative-route parameter is disabled,
all existing alternative routes are removed. When
the parameter is enabled, all alternative routes are
added back.
AllowMoreSpecificNonLocalRoute
Enable
Enables or disables allowing a more specific
non-local route to go into the routing table. The
default is disabled.
UdpCheckSumEnable
Enables or disables the UDP checksum calculation.
The default is enabled.
Enabling Alternative Routes Globally
This section describes how to enable alternative routes globally. The following
topics are included in this section:
•
•
“Alternative Routes Overview” on page 96
“Globally Enabling Alternative Routes” on page 97
Alternative Routes Overview
Routers may have several routes to the same destination network through several
protocols. In the Ethernet Routing Switch 1600 Series software, if the alternative
route feature is enabled, the software stores all of these alternative routes and sorts
them in the following order:
•
•
•
network mask
cost
route preference
The best, or first one listed, is the best route and is used by the hardware. The
remaining routes are referred to as alternative routes.
321712-B Rev 03
Chapter 2 Configuring IP Routing 97
To avoid traffic interruption, alternative routes can be enabled globally on the
switch. If the best route becomes unavailable, the next best route from the
alternative route list can replace the best route. In the Ethernet Routing Switch
1600 Series, both the active routing table and the configured static route table are
maintained. For more information about alternative routes, refer to “IP routing
and multicast concepts” on page 29.
Globally Enabling Alternative Routes
To enable alternative routes globally, follow this procedure:
1
From the Device Manager menu bar, choose IP Routing > IP.
The IP dialog box appears with the Globals tab displayed (see Figure 21 on
page 92).
2
Select the AlternativeEnable check box. If the alternative route parameter is
disabled, all existing alternative routes are removed. When the parameter is
enabled, all alternative routes are re-added.
3
Click Apply.
Table 4 on page 95 describes the Globals tab fields.
IP Router Management
In Device Manager, most of the dialog boxes related to managing the IP router are
found under the IP Routing menu.
This section includes the following topics:
•
•
•
“Configuring the Router IP Protocol Stack”
“Viewing IP Address Router Interfaces” on page 98
“Managing the System Routing Table” on page 99
Configuring IP Routing and Multicast Operations using Device Manager
98 Chapter 2 Configuring IP Routing
Configuring the Router IP Protocol Stack
The IP dialog box contains parameters for configuring the router’s IP protocol
stack. To configure the router’s IP protocol stack, choose IP Routing > IP from
the Device Manager menu bar.
The IP dialog box appears with the Globals tab displayed (see Figure 21 on
page 92).
Table 4 on page 95 describes the Globals tab fields.
Viewing IP Address Router Interfaces
IP addresses and their associated router interfaces can be viewed on the IP dialog
Addresses tab. To view this tab, use this procedure:
1
From the Device Manager menu bar, choose IP Routing > IP.
The IP dialog box appears with the Globals tab displayed (see Figure 21 on
page 92).
2
Click the Addresses tab.
The Addresses tab appears (Figure 25).
Figure 25 IP dialog box—Addresses tab
321712-B Rev 03
Chapter 2 Configuring IP Routing 99
Table 5 describes the Addresses tab fields.
Table 5 IP dialog box—Addresses tab fields
Field
Description
Interface
The IP router interface.
IpAddress
The IP address of the router interface.
Net Mask
The subnet mask of the router interface.
BcastAddrFormat
The IP broadcast address format used on this interface; that is,
whether zero (0) or one (1) is used for the broadcast address. The
Ethernet Routing Switch 1600 Series uses 1.
ReasmMaxSize
The Maximum Transmit Unit (MTU) size of the interface.
VlanId
A value that uniquely identifies the virtual LAN associated with this
entry. This value corresponds to the lower 12 bits in the IEEE 802.1Q
VLAN tag.
BrouterPort
This field always displays as False since brouter ports are not
supported on the Ethernet Routing Switch 1600 Series.
Managing the System Routing Table
The System Routing Table can be managed through the Device Manager. To
manage the System Routing Table, follow this procedure:
1
From the Device Manager menu bar, choose IP Routing > IP.
Note: Exercise caution when managing the System Routing Table as
changes in the table can have effects on other aspects of switch
performance.
The IP dialog box appears with the Globals tab displayed (see Figure 21 on
page 92).
Configuring IP Routing and Multicast Operations using Device Manager
100 Chapter 2 Configuring IP Routing
2
Click the Routes tab.
The Routes tab appears (Figure 26).
Figure 26 IP dialog box—Routes tab
Table 6 describes the Routes tab fields.
Table 6 IP dialog box—Routes tab fields
Field
Description
Dest
The destination IP network of this route. An entry with a value of 0.0.0.0
is considered a default route. Multiple routes to a single destination can
appear in the table, but access to such multiple entries is dependent on
the table access mechanisms defined by the network management
protocol in use.
Mask
Indicates the network mask to be logically ANDed with the destination
address before being compared to the value in the ipRouteDest field.
NextHop
The IP address of the next hop of this route.
AltSequence
The alternative route sequence. The value of 0 denotes the best route.
HopOrMetric
The primary routing metric for this route. The semantics of this metric
are specific to different routing protocols.
Interface
The IP router interface for this route.
Proto
The routing mechanism through which this route was learned:
• local = directly learned
• netmgmt = a static route
Age
The number of seconds since this route was last updated or otherwise
determined to be correct.
321712-B Rev 03
Chapter 2 Configuring IP Routing 101
Table 6 IP dialog box—Routes tab fields (continued)
Field
Description
PathType
The type of route:
• direct
• indirect
• alternative
• best
• unresolved
Note that the values direct and indirect refer to the notion of direct and
indirect routing in the IP architecture.
Pref
The preference value.
IP Static Route Table
The Static Route Table is separate from the System Routing Table that the router
uses to make forwarding decisions. The Static Route Table is used to change static
routes directly.
Although the tables are separate, the Static Route Table Manager entries are
automatically reflected in the System Routing Table if the next hop address in the
static route is reachable, and if the static route is enabled.
The Static Route table is indexed by three attributes:
•
•
•
Destination Network
Destination Mask
Next Hop
The maximum number of entries is 1 000. Static routes are inserted using the
Static Route Table, and deleted by using either the Static Route Table or the
System Routing Table.
Note: Only active static routes with a best route preference are displayed
in the System Routing Table. A static route is active only if the route is
enabled and the next hop address is reachable (for example, if there is a
valid ARP entry for the next hop).
Configuring IP Routing and Multicast Operations using Device Manager
102 Chapter 2 Configuring IP Routing
Multiple routes can be entered (for example, multiple default routes) that have
different costs, and the lowest-cost route that is reachable is used in the routing
table. Note that, if you enter multiple next hops for the same route with the same
cost, the software does not replace the existing route. If identical routes with the
same cost and a different next hop are entered, the first route is used. However, if
that first route becomes unreachable, the second route (with a different next hop)
is activated with no loss of connectivity.
Static routes that are configured for the management port are applied with the
network’s natural mask. Because traffic that originates from the switch refers to
these routes before checking the IP routing table, the switch management traffic
may be incorrectly forwarded out the management port even though a more
specific route exists in the routing table.
For more in-depth information about static routes, refer to “IP routing and
multicast concepts” on page 29.
This section includes the following topics:
•
•
•
•
“Creating IP Static Routes” on page 102
“Creating a Static Default Route” on page 105
“Creating a Black Hole Static Route” on page 106
“Deleting a Static Route” on page 107
Creating IP Static Routes
You can use the IP Static Routing Table Manager feature to directly change static
routes. The Static Route Table is separate from the System Routing Table, which
the router uses to make forwarding decisions. Although the tables are separate,
entries in the Static Routing Table Manager are automatically reflected in the
System Routing Table if the next hop address in the static route is reachable and
the static route is enabled.
Static routes provide a way to route traffic from an Ethernet Routing Switch 1600
Series to other devices in the network, like the Ethernet Routing Switch 8600.
To create a static route, follow this procedure:
1
321712-B Rev 03
From the Device Manager menu bar, choose IP Routing > IP.
Chapter 2 Configuring IP Routing 103
The IP dialog box appears with the Globals tab displayed (see Figure 21 on
page 92).
2
Click the Static Routes tab.
The Static Routes tab appears (Figure 27).
Figure 27 IP dialog box—Static Routes tab
3
Click Insert.
The IP, Insert Static Routes dialog box appears (Figure 28).
Figure 28 IP, Insert Static Routes dialog box
4
Type the desired IP address in the Dest field.
5
Type the desired subnet mask in the Mask field.
6
Type the IP address of the router through which the specified route is
accessible in the NextHop field.
Configuring IP Routing and Multicast Operations using Device Manager
104 Chapter 2 Configuring IP Routing
7
Type the desired metric value in the Metric field.
8
Type the desired route preference value in the Preference field.
9
Enable the static route by selecting the Enable check box.
10 Select the LocalNextHop check box to activate the static route only if the
switch has a local route to the network. If unselected, the static route is
activated if the switch has either a local or dynamic route to the network.
11 Click Insert.
The new route appears in the Static Routes tab.
Table 7 describes the fields in the IP dialog box, Static Routes tab.
Table 7 IP dialog box—Static Routes tab fields
Field
Description
Dest
The static route destination.
Mask
The route mask.
NextHop
The next hop in the static route. The next hop is the IP address of the
router through which the specified route is accessible.
When creating a black hole static route, set this field to
255.255.255.255.
Metric
The primary routing metric for this route. If this metric is not used, set the
value to 1.
IfIndex
The route index of the Next Hop.
Preference
The routing preference used for an alternative-route if one is configured.
Enable
Sets whether the configured static route is available on the port. The
default is enable.
Note: If a static route is disabled, it must be enabled before it can be
added to the system routing table.
Status
Status of the route.
LocalNextHop
True indicates that the static route becomes active only if the switch has
a local route to the network. False indicates that the static route
becomes active if the switch has a local route or a dynamic route to the
network.
321712-B Rev 03
Chapter 2 Configuring IP Routing 105
Creating a Static Default Route
The default route is used to specify a route to all networks for which there are no
explicit routes in either the Forwarding Information Base or the routing table. This
route is a route with a prefix length of zero (refer to RFC 1812 for further
information). The routing switch can be configured with the default route
statically, or it can be learned through a dynamic routing protocol.
Note: When creating a static default route, ensure that the destination
address and subnet mask are set to 0.0.0.0.
Create a static default route by using the following procedure:
1
From the Device Manager menu bar, choose IP Routing > IP.
The IP dialog box appears with the Globals tab displayed (see Figure 21 on
page 92).
2
Click the Static Routes tab.
The Static Routes tab appears (see Figure 27 on page 103).
3
Click Insert.
The IP, Insert Static Routes dialog box appears (see Figure 28 on page 103).
4
Type 0.0.0.0 in the Dest field.
5
Type 0.0.0.0 in the Mask field.
6
Type the IP address of the router through which this route is accessible in the
NextHop field.
7
Type the desired metric value in the Metric field.
8
Click Insert.
The default route record is created in the routing table.
Configuring IP Routing and Multicast Operations using Device Manager
106 Chapter 2 Configuring IP Routing
Creating a Black Hole Static Route
While aggregating or injecting routes to other routers, a router may not have a
route to the aggregated destination, which causes what is known as a black hole.
To avoid routing loops, a black hole static route can be configured to the
destination it advertises. A black hole route is a route with an invalid next hop so
that the data packets destined to this network are dropped by the switch.
Note: To create a black hole static route, the NextHop field must be set
to 255.255.255.255.
To create a black hole static route, do the following:
1
From the Device Manager menu bar, choose IP Routing > IP.
The IP dialog box appears with the Globals tab displayed (see Figure 21 on
page 92).
2
Click the Static Routes tab.
The Static Routes tab appears (see Figure 27 on page 103).
3
Click Insert.
The IP, Insert Static Routes dialog box appears (see Figure 28 on page 103).
4
Type the desired IP address in the Dest field.
5
Type the desired subnet mask in the Mask field.
6
Type 255.255.255.255 in the NextHop field.
7
Type the desired metric value in the Metric field.
8
Type the desired routing preference in the Preference field.
9
Select the Enable check box.
10 Click Insert.
The black hole static route record is created in the routing table.
321712-B Rev 03
Chapter 2 Configuring IP Routing 107
Deleting a Static Route
The Device Manager provides the ability to remove unwanted or unused static
routes. As with all procedures that involve removing configurations from the
switch, ensure that deleting a static route will not adversely affect other aspects of
switch performance.
To delete a static route, follow this procedure:
1
From the Device Manager menu bar, choose IP routing> IP.
The IP dialog box appears with the Globals tab displayed.
2
Click the Static Routes tab.
The Static Routes tab appears (see Figure 27 on page 103).
3
Select the static route to be deleted by clicking in a column in that row.
4
Click Delete.
The static route is removed from the Static Routes tab.
5
Click Close.
Configuring IP Routing and Multicast Operations using Device Manager
108 Chapter 2 Configuring IP Routing
Configuring CLIP
This section describes how to configure the circuitless IP (CLIP) feature. A
maximum of 32 CLIP interfaces can be configured on each device.
This section includes the following topics:
•
•
“Creating a CLIP interface” on page 108
“Deleting a CLIP Interface” on page 111
For conceptual information about the CLIP feature, refer to “IP routing and
multicast concepts” on page 29.
Creating a CLIP interface
To create a CLIP interface, follow this procedure:
1
From the Device Manager menu bar, choose IP routing > IP.
The IP dialog box appears with the Globals tab displayed (see Figure 21 on
page 92).
2
Click the Circuitless IP tab.
The Circuitless IP tab appears (Figure 29).
Figure 29 IP dialog box—Circuitless IP tab
3
Click Insert.
The IP, Insert Circuitless dialog box appears (Figure 30).
321712-B Rev 03
Chapter 2 Configuring IP Routing 109
Figure 30 IP, Insert Circuitless dialog box
4
Specify an integer value to identify the CLIP interface in the Interface field.
5
Enter the IP address of the interface in the IP Address field.
6
Enter the subnet mask of the interface in the Net Mask field.
7
Click Insert.
The new interface is created and appears in the Circuitless IP tab (see
Figure 29 on page 108).
Table 8 describes the fields on the Circuitless IP tab and IP, Insert Circuitless
dialog box.
Table 8 IP dialog box—Circuitless IP tab and Insert Circuitless dialog box fields
Field
Description
Interface
The CLIP identification number you assign to the
interface. The range is 1 to 32.
IP Address
The IP address of the interface you are specifying
as circuitless.
Net Mask
The network mask address of the interface you are
specifying as circuitless.
Enabling OSPF on a CLIP interface
To enable OSPF on a CLIP interface:
1
From the Circuitless IP tab, select the desired interface, and click OSPF.
The Circuitless OSPF dialog box appears.
Configuring IP Routing and Multicast Operations using Device Manager
110 Chapter 2 Configuring IP Routing
Figure 31 Circuitless OSPF dialog box
2
Select the Enable option.
3
In the AreaId field, enter the CLIP IP interface area.
4
Click Apply.
5
Click Close.
Table 9 describes the fields on the Circuitless OSPF dialog box.
Table 9 Circuitless OSPF dialog box fields
Field
Description
Enable
Enables and disables OSPF on the CLIP interface.
AreaId
Specifies the CLIP IP interface area.
Enabling PIM on a CLIP interface
To enable PIM on a CLIP interface:
1
From the Circuitless IP tab, select the desired interface, and click PIM.
The Circuitless PIM dialog box appears.
321712-B Rev 03
Chapter 2 Configuring IP Routing 111
Figure 32 Circuitless PIM dialog box
2
Select the Enable option.
3
Click Apply.
4
Click Close.
Table 10 describes the fields on the Circuitless PIM dialog box.
Table 10 Circuitless PIM dialog box fields
Field
Description
Enable
Enables and disables PIM on the interface.
Mode
Specifies the PIM mode (read-only).
Deleting a CLIP Interface
To delete a CLIP interface, follow this procedure:
1
From the Device Manager menu bar, choose IP routing > IP.
The IP dialog box appears with the Globals tab displayed (see Figure 21 on
page 92).
2
Click the Circuitless IP tab.
The Circuitless IP tab appears (see Figure 29 on page 108).
3
In the Interface column, select the CLIP number of the interface to be
deleted.
Configuring IP Routing and Multicast Operations using Device Manager
112 Chapter 2 Configuring IP Routing
4
Click Delete.
The interface is deleted from the list of interfaces.
Configuring IP Route Preferences
The Route Preference tab displays the protocol and the default and configured IP
global route preference information. The Route Preference tab is used to edit IP
route preference entries. Using this tab, default route preferences can be
overridden and a protocol preference value can be substituted for routes learned
for a specific protocol.
Note: Changing route preferences is a process-oriented operation that
can affect system performance and network reachability while performing
the procedures. Therefore, if you change default preferences for routing
protocols, Nortel recommends that you do so before enabling the
protocols.
To edit an IP route preference, do the following:
1
From the Device Manager menu bar, select IP Routing > IP.
The IP dialog box appears with the Globals tab displayed (see Figure 21 on
page 92).
2
Click the Route Preference tab.
The Route Preference tab appears (Figure 33).
321712-B Rev 03
Chapter 2 Configuring IP Routing 113
Figure 33 IP dialog box—Route Preference tab
3
Double-click the Configured field that corresponds with the desired protocol
and type a new preference value.
4
Click Apply.
Table 11 describes the Route Preference tab dialog box fields.
Table 11 IP dialog box—Route Preference tab fields
Field
Description
Protocol
The Ethernet Routing Switch 1600 Series supports the following
protocols:
• local
• static
• ospfIntra
• ospfInter
• rip
• ospfExternal1
• ospfExternal2
Default
The default preference value for the given protocol.
Configured
Changes the default preference value for the given protocol.
Configuring IP Routing and Multicast Operations using Device Manager
114 Chapter 2 Configuring IP Routing
Configuring ICMP Router Discovery
ICMP router discovery specifies an extension to enable hosts attached to multicast
or broadcast networks to discover the IP addresses of their neighboring routers.
This section includes the following topics:
•
•
•
“Enabling ICMP Router Discovery Globally” on page 114
“Viewing the ICMP Router Discovery Table” on page 114
“Configuring Router Discovery on a VLAN” on page 116
Enabling ICMP Router Discovery Globally
To enable ICMP router discovery globally, follow this procedure:
1
From the Device Manager menu bar, select IP Routing > IP.
The IP dialog box appears with the Globals tab displayed (see Figure 21 on
page 92).
2
Select the RouteDiscoveryEnable check box.
3
Click Apply.
Viewing the ICMP Router Discovery Table
To view the ICMP router discovery table, do the following:
1
From the Device Manager menu bar, select IP Routing > IP.
The IP dialog box appears with the Globals tab displayed (see Figure 21 on
page 92).
321712-B Rev 03
Chapter 2 Configuring IP Routing 115
2
Click the Router Discovery tab.
The Router Discovery tab appears (Figure 34).
Figure 34 IP dialog box—Router Discovery tab
3
Edit the fields provided to configure the router discovery parameters.
4
Click Apply.
Table 12 describes the Router Discovery tab fields.
Table 12 IP dialog box—Router Discovery tab fields
Item
Description
Interface
VLAN ID or the port.
AdvAddress
The IP destination address to be used for broadcast or
multicast router advertisements sent from the interface.
The accepted values are:
• 224.0.0.1 – the all-systems multicast address
• 255.255.255.255 – the limited broadcast address
The default is 255.255.255.255.
AdvFlag
Indicates whether (true) or not (false) the address is to
be advertised on the interface.
The default is true (advertise address).
AdvLifetime
The TTL value (in seconds) of router advertisements
sent from the interface. The range is no less than the
MaxAdvInterval and no greater than 9 000 seconds.
The default is 1 800 seconds.
Configuring IP Routing and Multicast Operations using Device Manager
116 Chapter 2 Configuring IP Routing
Table 12 IP dialog box—Router Discovery tab fields (continued)
Item
Description
MaxAdvInterval
The maximum time (in seconds) between sending
unsolicited broadcast or multicast router
advertisements from the interface. The range is no less
than 4 seconds and no greater than 1 800 seconds.
The default is 600 seconds.
MinAdvInterfal
The minimum time (in seconds) between sending
unsolicited broadcast or multicast router
advertisements from the interface. The range is no less
than 3 seconds and no greater than the
MaxAdvInterval.
The default is 450 seconds.
PreferenceLevel
Specifies the preference assigned to the address as a
default router address, relative to other router
addresses on the same subnet. A higher number
indicates greater preference. The range is
-2 147 483 648 to 2 147 483 647.
The default is 0.
Configuring Router Discovery on a VLAN
To configure router discovery on a VLAN, follow this procedure:
1
From the Device Manager menu bar, choose VLAN > VLANs.
The VLAN dialog box appears with the Basic tab displayed.
2
321712-B Rev 03
Select the VLAN ID to be configured for router discovery. Several buttons on
the bottom of the dialog box become available.
Chapter 2 Configuring IP Routing 117
3
Click IP.
The IP, VLAN dialog box appears with the IP Address tab displayed
(Figure 35).
Figure 35 IP, VLAN dialog box
4
Click the Router Discovery tab.
The IP, VLAN—Router Discovery tab appears (Figure 36).
Figure 36 IP, VLAN—Router Discovery tab
5
Edit the provided fields to configure the router discovery parameters.
6
Click Apply.
Configuring IP Routing and Multicast Operations using Device Manager
118 Chapter 2 Configuring IP Routing
Table 13 describes the IP, VLAN— Router Discovery tab fields.
Table 13 IP, VLAN—Router Discovery tab fields
Field
Description
AdvAddress
The IP destination address to be used for broadcast or
multicast router advertisements sent from the interface.
The accepted values are:
• 224.0.0.1—the all-systems multicast address
• 255.255.255.255—the limited broadcast address
The default is 255.255.255.255.
AdvFlag
Indicates whether (true) or not (false) the address is to be
advertised on the interface.
The default is true (advertise address).
AdvLifetime
The TTL value (in seconds) of router advertisements sent
from the interface. The range is no less than the
MaxAdvInterval and no greater than 9 000 seconds.
The default is 1 800 seconds.
MaxAdvInterval
The maximum time (in seconds) between sending
unsolicited broadcast or multicast router advertisements
from the interface. The range is no less than 4 seconds
and no greater than 1 800 seconds.
The default is 600 seconds.
MinAdvInterval
The minimum time (in seconds) between sending
unsolicited broadcast or multicast router advertisements
from the interface. The range is no less than 3 seconds
and no greater than the MaxAdvInterval.
The default is 450 seconds.
PreferenceLevel
Specifies the preference assigned to the address as a
default router address, relative to other router addresses
on the same subnet. A higher number indicates greater
preference. The range is -2 147 483 648 to 2 147 483 647.
The default is 0.
321712-B Rev 03
119
Chapter 3
Configuring ARP
Network stations using the IP protocol need both a physical address and an IP
address to transmit a packet. In situations where the station knows only the
network host IP address, the Address Resolution Protocol (ARP) enables the
network station to determine the physical address of a network host by binding a
32-bit IP address to a 48-bit MAC address.
A network station can use ARP across a single network only and the network
hardware must support physical broadcasts. If a network station wants to send a
packet to a host but knows only the host IP address, the network station uses ARP
to determine the physical address of the host. For conceptual information about
ARP management, refer to “IP routing and multicast concepts” on page 29.
The following information describes how to configure ARP on your Ethernet
Routing Switch 1600 Series. To configure the Ethernet Routing Switch 1600
Series to communicate with devices that do not respond to ARP requests,
configure a static ARP entry. If an ARP entry is not to be aged out, a static ARP
entry can also be used. A static ARP entry maps the device IP address to the
corresponding MAC address. When configuring a static ARP entry on the
Ethernet Routing Switch 1600 Series, a match between the IP address and MAC
address is assigned to a particular port of a VLAN.
This section contains the following topics:
•
•
•
“Viewing and Managing ARP” on page 120
“Static ARP Entries” on page 121
“IP, VLAN—ARP tab” on page 123
Configuring IP Routing and Multicast Operations using Device Manager
120 Chapter 3 Configuring ARP
Viewing and Managing ARP
Device Manager has the capability to view and manage the MAC/IP address
associations known and learned by the switch. In addition, ARP entries can be
manually added to the ARP list (static ARP entries).
To access the switch ARP entry listing, follow this procedure:
1
From the Device Manager menu bar, choose IP Routing > IP.
The IP dialog box appears with the Globals tab displayed (see Figure 21 on
page 92).
2
Click the ARP tab.
The IP dialog box—ARP tab appears (Figure 37).
Figure 37 IP dialog box—ARP tab
321712-B Rev 03
Chapter 3 Configuring ARP 121
Table 14 describes the IP dialog box—ARP tab fields.
Table 14 IP dialog box—ARP tab fields
Field
Description
Interface
The router interface for this ARP entry.
MacAddress
The media-dependent physical address (that is, the Ethernet address).
IpAddress
The IP address corresponding to the media-dependent physical
address.
Type
Type of ARP entry:
• local—a locally configured ARP entry
• static—a statically configured ARP entry
• dynamic—a learned ARP entry
Static ARP Entries
Static ARP entries are used to manually associate an IP address with a MAC
address. Static ARP entries are used in instances where the dynamic learning of
ARP associations is neither possible (a device does not respond to ARP requests)
or undesirable (an ARP entry must be persistent).
To create static ARP entries, follow this procedure:
1
From the Device Manager menu bar, choose IP Routing > IP.
The IP dialog box appears with the Globals tab displayed (see Figure 21 on
page 92).
2
Click the ARP tab.
The IP dialog box—ARP tab appears (see Figure 37 on page 120).
Configuring IP Routing and Multicast Operations using Device Manager
122 Chapter 3 Configuring ARP
3
Click Insert.
The IP, Insert ARP dialog box appears (Figure 38).
Figure 38 IP, Insert ARP dialog box
4
Select a valid VLAN for the static ARP entry from the Port in VLAN list.
A port selection dialog box appears (Figure 39).
Figure 39 IP, Insert ARP, VLAN port selection dialog box
Select the desired port and click OK.
The VLAN and port information is displayed in the Interface field.
5
Type the device IP address in the IpAddress field.
6
Type the device MAC address in the MacAddress field.
7
Click Insert.
321712-B Rev 03
Chapter 3 Configuring ARP 123
IP, VLAN—ARP tab
The IP, VLAN—ARP tab (Figure 40) is accessible through the IP, VLAN dialog
box (see Figure 23 on page 93). The IP, VLAN—ARP tab is designed for Proxy
ARP configuration. However, as Proxy ARP is not supported in the current
release of Ethernet Routing Switch 1600 Series software, do not attempt to
perform configurations using the IP, VLAN—ARP tab.
Figure 40 IP, VLAN dialog box—ARP tab
Note: Proxy ARP is not supported in the current release of Ethernet
Routing Switch 1600 Series software. Do not attempt any Proxy ARP
configurations using the IP, VLAN—ARP tab.
Configuring IP Routing and Multicast Operations using Device Manager
124 Chapter 3 Configuring ARP
321712-B Rev 03
125
Chapter 4
Configuring BootP/DHCP
This section describes how to use the Device Manager for the configuration and
management of BootP/DHCP relay.
For conceptual information about these topics, refer to “IP routing and multicast
concepts” on page 29.
This section contains the following topics:
•
•
“BootP/DHCP relay”
“Configuring BootP/DHCP” on page 125
BootP/DHCP relay
Dynamic Host Configuration Protocol (DHCP), an extension of the Bootstrap
Protocol (BootP), is used to dynamically provide host configuration information
to network devices. To lower administrative overhead, network managers prefer to
configure a small number of DHCP servers in a central location. Using few DHCP
servers requires the routers connecting to the subnet or bridge (or VLANs)
domains to support the BootP/DHCP relay function so that hosts can get the
configuration information from servers several router hops away.
Configuring BootP/DHCP
Use the DHCP Globals tab when enabling the DHCP behavior globally on an
Ethernet Routing Switch 1600 Series.
To globally enable BOOTP/DHCP, perform the following procedure:
Configuring IP Routing and Multicast Operations using Device Manager
126
Chapter 4 Configuring BootP/DHCP
1
From the Device Manager menu bar, select IP Routing > DHCP.
The DHCP dialog box appears with the Globals tab displayed (Figure 41).
Figure 41 DHCP dialog box—Globals tab
2
Click Insert.
The Insert Globals dialog box is displayed (Figure 42).
Figure 42 Insert Globals dialog box
3
Using the fields provided, enter the global DHCP/Bootp parameters. Table 15
outlines the fields on this screen.
4
Click Insert.
The Globals tab is updated with the new DHCP/Bootp entry.
321712-B Rev 03
Chapter 4 Configuring BootP/DHCP
127
Table 15 outlines the fields on the Insert Globals dialog box and Globals tab.
Table 15 Globals tab and Insert Globals dialog box fields
Field
Description
AgentAddr
IP address of the input interface (agent) on which the
relaying of received BootP/DHCP packets must be
enabled.
ServerAddr
This parameter is either the IP address of the BootP/
DHCP server or the address of another local interface of
the switch.
• If it is the address of the BootP/DHCP server, then the
request is unicast to the server’s address.
• If the address is one of the IP addresses of an interface
on the switch, then the BootP/DHCP requests will be
broadcast out of that local interface.
Enable
Select this check box to enable this DHCP/Bootp entry.
Mode
Select the mode for this entry to use. The choices are:
• bootp
• dhcp
• both
Configuring IP Routing and Multicast Operations using Device Manager
128
Chapter 4 Configuring BootP/DHCP
321712-B Rev 03
129
Chapter 5
Configuring IP Policies
In the Ethernet Routing Switch 1600 Series, there is a single database of route
policies that can be used by protocols such as RIP for any type of filtering
purpose. For conceptual information about route policies, see “IP routing and
multicast concepts” on page 29.
A policy is identified by a name or an ID. Each policy can have several sequence
numbers. The sequence number acts as an implicit preference; a lower sequence
number is preferred.
A policy name can be assigned when the policy is created. When a policy is
created using the CLI, an automated algorithm internally generates the policy
identification number. When the same task is accomplished in the Device
Manager, this value can be manually assigned.
If a field in a policy is not configured, it appears as 0 or any when it is displayed
in Device Manager. This indicates that the switch ignores the field in the match
criteria.
Note: Each policy sequence number contains a set of fields. Only a
subset of those fields is used when the policy is applied in different
contexts. For example, if the set-preference field has been set for a policy,
the field is used only when the policy is applied for accept purposes. This
field is ignored when the policy is applied for announce purposes.
Configuring IP Routing and Multicast Operations using Device Manager
130 Chapter 5 Configuring IP Policies
A policy can be configured so that it applies to one purpose only. For example,
RIP Announce can be configured on a given RIP interface. In this case, all
sequence numbers under the given policy apply to that filter.
Note: Before a route policy can be configured, a prefix list must be
defined. Refer to “Configuring the Prefix List” on page 130 for further
information.
This section includes the following topics:
•
•
•
•
“Configuring the Prefix List” on page 130
“Creating and Editing a Route Policy” on page 132
“Configuring Filtering Policies on a RIP Interface” on page 142
“Deleting Filtering Policies on a RIP Interface” on page 144
Configuring the Prefix List
The prefix list is a list of networks used by route policies to define an action. One
or more IP prefix lists can be created and applied to any IP route policy.
Before the creation of prefix lists, some protocols used two databases for different
types of policies: the address-list database, and the netlist database. A prefix list
combines these two databases with the following outcomes:
•
•
A prefix list with a 32-bit mask is equivalent to an address.
A prefix list with a mask less than 32 bits can be used as a network.
When the MaskLenFrom field is configured to be less than the MaskLenTo
field, it can also be used as a range. These fields are used during prefix list
creation and are found in the Prefix List tab of the Policy dialog (see Figure 43 on
page 131).
For more information about prefix lists, refer to “IP routing and multicast
concepts” on page 29.
321712-B Rev 03
Chapter 5 Configuring IP Policies 131
To set up or edit a route policy prefix list, follow this procedure:
1
From the Device Manager menu bar, choose IP Routing > Policy.
The Policy dialog box appears with the Prefix List tab displayed (Figure 43).
Figure 43 Policy dialog box—Prefix List tab
2
Click Insert.
The Policy, Insert Prefix List dialog box appears (Figure 44).
Figure 44 Policy, Insert Prefix List dialog box
3
Using the provided fields, configure the prefix list.
4
Click Insert.
Configuring IP Routing and Multicast Operations using Device Manager
132 Chapter 5 Configuring IP Policies
Table 16 describes the Policy, Insert Prefix List dialog box fields.
Table 16 Policy, Insert Prefix List dialog box fields
Field
Description
ID
Specifies the list identifier. The range is 1 to 2 147 483 647.
Prefix
Specifies the IP address.
PrefixMaskLen
Specifies the length of the prefix mask.
Note: You must enter the full 32-bit mask in order to exact a full
match of a specific IP address (for example, when creating a policy to
match on next-hop).
Name
Names or renames the specified prefix list. The name length can be
from 1 to 64 characters.
MaskLenFrom
Specifies the lower bound of the mask length. The default is the mask
length.
MaskLenUpto
Specifies the higher bound of the mask length. The default is the
mask length.
Note: Lower bound and higher bound mask lengths together can define a range of
networks.
Creating and Editing a Route Policy
Route policies can be configured for RIP In and Out purposes.
When a route policy is created using Device Manager, the ID of the policy is
manually created. When the same task is performed in the CLI, the policy ID
number is automatically generated.
Note: Changing route preferences is a process-oriented operation that
can affect system performance and network reachability while performing
the procedures. Therefore, if you change a prefix list or routing protocol,
Nortel recommends that you do so before enabling the protocols.
321712-B Rev 03
Chapter 5 Configuring IP Policies 133
To create or edit a route policy, follow this procedure:
1
From the Device Manager menu bar, select IP Routing > Policy.
The Policy dialog box appears with the Prefix List tab displayed (see
Figure 43 on page 131).
2
Click the Route Policy tab.
The Route Policy tab appears (Figure 45). The dialog box is wide. If all fields
do not fully display on your screen, use the scroll bar above the buttons to
scroll across and display all fields on the tab.
Figure 45 Policy dialog box—Route Policy tab
Configuring IP Routing and Multicast Operations using Device Manager
134 Chapter 5 Configuring IP Policies
3
Click Insert.
The Policy, Insert Route Policy dialog box appears (Figure 46).
Figure 46 Policy, Insert Route Policy dialog box
4
Enter a number to identify the policy in the Id field.
5
Enter a number to identify the specific policy within a route policy group in
the SequenceNumber field. The sequence number acts as an implicit
preference; a lower sequence number is preferred.
6
Enter a name for the policy in the Name field.
7
Select the Enable check box to activate the policy.
8
In the Mode section, select the permit option button to allow a route or deny
to ignore the route.
9
Select the desired policy protocols in the MatchProtocol section.
321712-B Rev 03
Chapter 5 Configuring IP Policies 135
10 The MatchNetwork, MatchIpRouteSource, MatchNextHop, and
MatchInterface fields specify the criteria the policy uses to match against the
contents of a prefix list. None of these fields are mandatory for policy
creation. Up to four prefix lists can be selected for each match criterion.
a
To match the destination network, click the ellipse button next to the
MatchNetwork field.
The MatchNetwork list box appears, displaying valid prefix list
selections.
b
In the MatchNetwork list box, select the prefix list used to match the
destination network. To select multiple prefix lists, or to deselect a prefix
list, Ctrl+click the selections.
c
Click Ok.
d
Configure the MatchIPRouteSource, MatchNextHop, and
MatchInterface parameters in the same way.
11 In the MatchMetric field, type the value to match against metric of the
incoming route.
12 In the SetRoutePreference field, type the route preference value to be
assigned to any routes that match this policy.
13 In the SetMetric field, type the metric value to be announced for any routes
that match this policy.
14 To replace the destination network of any routes that match this policy with a
new destination derived from a specified prefix list, do the following:
a
Click the ellipse button next to the SetInjectList field. The
SetInjectNetList list box appears.
b
Select the applicable prefix list.
c
Click Ok.
15 In the SetMask field, type the network mask of the route that matches this
policy.
16 Click Insert.
Configuring IP Routing and Multicast Operations using Device Manager
136 Chapter 5 Configuring IP Policies
Table 17 describes the Policy, Insert Route Policy dialog box fields.
Table 17 Policy, Insert Route Policy dialog box fields
Field
Description
Id
The ID of the policy. The range is 1 to 64.
SequenceNumber
A second index used to identify a specific policy within a route
policy group. The range is 1 to 65 535.
Name
Names or renames a policy. This command changes the
name field for all sequence numbers under the given policy.
Enable
Indicates whether this policy sequence number is enabled or
disabled. If disabled, the policy sequence number is ignored.
Mode
Specifies the action to be taken when a policy is selected for a
specific route. Select permit (allow the route) or deny (ignore
the route).
MatchProtocol
If configured, matches the protocol through which the route is
learned. This field is used only for RIP announce policies. The
options are:
• direct
• static
• RIP
• ospf
• any
MatchNetwork
If configured, the switch matches the destination network
against the contents of the specified prefix list.
Click the ellipse button and choose from the list in the
MatchNetwork dialog box. You can select up to four entries.
To deselect an entry, use the CTRL key.
MatchIpRouteSource
If configured, matches the source IP address for RIP routes
against the contents of the specified prefix list. This option is
ignored for all other route types.
Click the ellipse button and choose from the list in the
MatchIPRouteSource dialog box. You can select up to four
entries. To deselect an entry, use the CTRL key.
MatchNextHop
If configured, matches the next hop IP address of the route
against the contents of the specified prefix list. This field is
used only for RIP routes and ignored for all other types of
route.
Click the ellipse button and choose from the list in the
MatchNextHop dialog box. You can select up to four entries.
To deselect an entry, use the CTRL key.
321712-B Rev 03
Chapter 5 Configuring IP Policies 137
Table 17 Policy, Insert Route Policy dialog box fields (continued)
Field
Description
MatchInterface
If configured, the switch matches the IP address of the
received interface against the contents of the specified prefix
list. This field is used only for RIP routes and ignored for all
other types of route.
When the MatchInterface parameter is used in a RIP-In policy,
it is used to match against the interface on which the route is
received. When the parameter is used in a RIP-Out policy, it is
used to match against the next-hop of the route to be
advertised.
Click the ellipse button and choose from the list in the
MatchInterface dialog box. You can select up to four entries.
To deselect an entry, use the CTRL key.
MatchMetric
If configured, the switch matches the metric of the incoming
advertisement or existing route against the specified value.
The range is 0 to 65 535. If the value is 0, then this field is
ignored. The default is 0.
SetRoutePreference
If set to greater than zero, specifies the route preference value
to be assigned to the route that matches this policy. If set to
zero, the global preference value is used. The range is 0 to
255. The default is 0. This field applies only to accept policies.
SetMetric
If configured, the switch sets the metric value for the route
while announcing. The default-import-metric is 0. If the default
is configured, the original cost of the route is advertised into
OSPF; for RIP, the original cost of the route or the default
value is used.
SetInjectNetList
If configured, the switch replaces the destination network of
the route that matches this policy with the contents of the
specified prefix list. Click the ellipse button and choose from
the list in the Set Inject NetList dialog box.
SetMask
If configured, the switch sets the mask of the route that
matches this policy. This field is used only for RIP accept
policies.
Configuring Policy Application
The Applying Policy tab is used to set which type of policies will applied to the
switch. To configure policy application, follow this procedure:
Configuring IP Routing and Multicast Operations using Device Manager
138 Chapter 5 Configuring IP Policies
1
Select IP Routing > Policy from the Device Manager menu.
The Policy dialog box appears with the Prefix List tab selected.
2
Select the Applying Policy tab.
This tab is illustrated in Figure 47.
Figure 47 Policy Dialog—Applying Policy tab
3
Using the check boxes provided, select policy types to be applied to the
switch. Table 18 describes the fields on this tab.
Table 18 Applying Policy tab fields
Field
Description
RoutePolicyApply
When selected, allows the configuration change in a route policy to
take effect. This keeps the switch from attempting to apply the
changes one-by-one after each configuration change.
RedistributeApply
When selected, allows the configuration changes in the policy to
take effect for an OSPF Redistribute context. This keeps the switch
from attempting to apply the changes one-by-one after each
configuration change.
OspfInFilterApply
When selected, allows the configuration change in a route policy or
a prefix list to take effect in an OSPF accept context. This keeps the
switch from attempting to apply the changes one-by-one after each
configuration change.
4
321712-B Rev 03
Click Apply.
Chapter 5 Configuring IP Policies 139
Configuring an OSPF Accept Policy
To define an OSPF Accept policy, perform the following procedure:
1
Select IP Routing > Policy from the Device Manager menu.
The Policy dialog will open with the Prefix List tab selected.
2
Select the OSPF Accept tab.
The OSPF Accept tab appears (Figure 48).
Figure 48 Policy Dialog—OSPF Accept tab
3
Click Insert.
The Policy, Insert OSPF Accept dialog box appears (Figure 49).
Figure 49 Policy, Insert OSPF Accept Dialog
Configuring IP Routing and Multicast Operations using Device Manager
140 Chapter 5 Configuring IP Policies
4
Using the fields provided, enter the information for the OSPF Accept policy.
Table 19 describes the fields on this dialog and the OSPF Accept tab.
Table 19 Policy, Insert OSPF Accept Dialog fields
Field
Description
AdvertisingRtr
The IP address of the advertising router.
Enable
Enables or disables the policy.
MetricType
The metric type for this policy.
PolicyName
The name of the policy.
5
Click Insert.
The OSPF Accept tab is updated with the new policy.
Configuring an OSPF Redistribution Policy
A redistribution entry for OSPF can be configured to announce routes of a certain
source type, for example, static, RIP, or direct. If a route policy field is not
configured for a redistribute entry, then the default action is taken on the basis of
metric, metric-type, and subnet configured. This is called basic redistribution.
Otherwise, use the route policy specified to perform detailed redistribution. If no
redistribution entry is configured, no external LSA is generated for non-OSPF
routes.
Note: Changing OSPF Redistribute contexts is a process-oriented
operation that can affect system performance and network reachability
while performing the procedures. Therefore, Nortel recommends that if
the default preferences are to be changed for an OSPF Redistribute
context, do so before enabling the protocols.
OSPF redistribution policies can be configured in two locations in the Device
Manager:
1
IP Routing > OSPF > Redistribute tab
2
IP Routing > Policy > OSPF Redistribute tab
321712-B Rev 03
Chapter 5 Configuring IP Policies 141
Although the following procedure details using the IP Routing > Policy > OSPF
Redistribute tab, the steps are the same in the IP Routing > OSPF >
Redistribute tab.
To set up or edit an OSPF redistribute policy perform the following tasks:
1
From the Device Manager menu bar select IP Routing >Policy.
The Policy dialog box appears with Prefix List tab selected.
2
Select the OSPF Redistribute tab.
The OSPF Redistribute tab appears (Figure 50).
Figure 50 Policy Dialog—OSPF Redistribute tab
3
Click Insert.
The Policy, Insert OSPF Redistribute dialog box appears (Figure 51).
Figure 51 Policy, Insert OSPF Redistribute dialog box
4
Edit the fields provided.
5
Click Insert.
Configuring IP Routing and Multicast Operations using Device Manager
142 Chapter 5 Configuring IP Policies
Table 20 describes the Policy, Insert OSPF Redistribute dialog box fields.
Table 20 Policy, Insert OSPF Redistribute dialog box fields
Field
Description
RouteSource
Select the route source protocol for the redistribution entry.
Enable
Enables (or disables) an OSPF redistribute entry for a specified
source type.
You can also enable or disable this feature in the OSPF Redistribute
tab of the Policy dialog box by clicking in the field and selecting
enable or disable from the pulldown menu.
Metric
Set the OSPF route redistribution metric for basic redistribution. The
value can be a range between 0 to 65 535. If configured as 0, the
original cost of the route is used.
MetricType
Set the OSPF route redistribution metric type. The default is Type 2.
You can also select your entry in the OSPF Redistribution tab of the
Policy dialog box by clicking in the field and selecting any, type1, or
type2 from the pulldown menu.
Subnets
Allows or suppresses external subnet routes while being
redistributed into an OSPF domain.
You can also select your entry in the OSPF Distribution tab of the
Policy dialog box by clicking in the field and selecting allow or deny
from the pulldown menu.
RoutePolicy
Sets the route policy by name to be used for the detailed
redistribution of external routes from a specified source into an OSPF
domain.
Click the ellipse button and choose from the list in the Route Policy
dialog box (Figure 51 on page 141). To deselect an entry, use the
ALT key.
Configuring Filtering Policies on a RIP Interface
Inbound filtering, or accept policies, can be configured on a RIP interface. The
switch uses the accept policy to determine whether to learn a route on the
interface. The accept policy specifies the parameters of the route when it is added
to the routing table.
321712-B Rev 03
Chapter 5 Configuring IP Policies 143
Outbound filtering, or announce policies, can also be configured on a RIP
interface. The announce policy determines whether to advertise a route from the
routing table on the interface. It also specifies the parameters of the advertisement.
Note: Policies must be created before they can be applied. Refer to
“Creating and Editing a Route Policy” on page 132 for further
information.
To configure inbound or outbound filtering on a RIP interface, follow this
procedure:
1
From the Device Manager menu bar, choose IP Routing > Policy.
The Policy dialog box appears with the Prefix List tab displayed (see
Figure 43 on page 131).
2
Click the RIP In/Out Policy tab.
The RIP In/Out Policy tab appears (Figure 52).
Figure 52 Policy dialog box—RIP In/Out Policy tab
3
Double-click in the InPolicy or OutPolicy field of the interface you wish to
configure.
The InPolicy or OutPolicy list box appears, displaying preconfigured
policies.
4
Select the applicable policy and click Ok.
The policy is added and the Rip In/Out Policy tab is updated.
Configuring IP Routing and Multicast Operations using Device Manager
144 Chapter 5 Configuring IP Policies
5
Click Apply.
Note: RIP In and Out policies can also be configured from the VLAN
configuration menu. Refer to “Enabling and Configuring RIP on a
VLAN” on page 165 for further information.
Table 21 describes the Policy dialog box—RIP In/Out Policy tab fields.
Table 21 Policy dialog box—RIP In/Out Policy tab fields
Field
Description
Address
The IP address of the RIP interface.
Interface
The interface ID.
InPolicy
Double-click in the InPolicy name field and select the policy name to
be applied from the PolicyName dialog box. The policy determines
which routes are learned on this interface. The policy also specifies
the parameters of the route when it is added to the routing table.
Note: You can also configure an interface’s RIP accept policy on the
IP, VLAN dialog box—RIP tab (see “Enabling and Configuring RIP on
a VLAN” on page 165).
OutPolicy
Double-click in the OutPolicy name field and select the policy name
to be applied from the PolicyName dialog box. The policy determines
which routes are advertised from the routing table on the interface.
The policy also specifies the parameters of the advertisement.
Note: You can also configure an interface’s RIP announce policy on
the IP, VLAN dialog box—RIP tab (see “Enabling and Configuring
RIP on a VLAN” on page 165).
Deleting Filtering Policies on a RIP Interface
To delete a RIP In/Out Policy, follow this procedure:
1
From the Device Manager menu bar, select IP Routing > Policy.
The Policy dialog box appears with the Prefix List tab displayed (see
Figure 43 on page 131).
2
Select the RIP In/Out Policy tab.
The RIP In/Out Policy tab appears (see Figure 52 on page 143).
321712-B Rev 03
Chapter 5 Configuring IP Policies 145
3
Double-click in the InPolicy or OutPolicy field of the interface to be
configured.
The InPolicy or OutPolicy list box appears, displaying preconfigured
policies.
4
Press CTRL + the left mouse button on the desired policy to delete.
5
Click Ok.
The policy is removed from that interface and the Rip In/Out Policy tab is
updated.
6
Click Apply.
Configuring IP Routing and Multicast Operations using Device Manager
146 Chapter 5 Configuring IP Policies
321712-B Rev 03
147
Chapter 6
Configuring VRRP
End stations are often configured with a static default gateway IP address. Loss
of the default gateway router can have catastrophic results. Virtual Router
Redundancy Protocol (VRRP), RFC 2338, is designed to eliminate this single
point of failure in a routed environment by introducing the concept of a virtual IP
address (transparent to users) shared between two or more routers connecting
the common subnet to the enterprise network. With the virtual IP address as the
default gateway on end hosts, VRRP provides a dynamic default gateway
redundancy in the event of a failure.
In the current implementation of VRRP, there can be only one active master
switch per IP subnet. All other VRRP interfaces in a network are in backup mode.
If VRRP and other IP routing protocols (for example, OSPF) are configured on
the same IP physical interface, selecting the interface address as the VRRP virtual
IP address (logical IP address) is not supported. Use a separate dedicated IP
address for VRRP.
Use the Hold Down Timer to modify the behavior of the VRRP failover
mechanism so that the router has enough time to detect and update the OSPF or
RIP routes. This timer delays the preemption of the master over the backup, when
the master becomes available.
Note: Nortel recommends that all routers are set to the identical number
of seconds for the Hold Down Timer.
In addition, the preemption of the master over the backup can be manually forced
before the delay timer expires.
This section describes configuring and managing VRRP in Device Manager. For
conceptual information regarding VRRP, refer to “IP routing and multicast
concepts” on page 29.
Configuring IP Routing and Multicast Operations using Device Manager
148 Chapter 6 Configuring VRRP
This section contains the following topics:
•
•
•
•
•
•
“Configuration Prerequisites” on page 148
“Enabling VRRP Globally” on page 148
“Configuring VRRP for the Interface” on page 149
“Configuring VRRP Secondary Features” on page 152
“Configuring VRRP on a VLAN” on page 154
“Configuring the Fast Advertisement Interval” on page 159
Configuration Prerequisites
Before VRRP configurations can take effect, the following steps must be taken:
•
•
Assign an IP address to the interface
Enable VRRP globally
Enabling VRRP Globally
To enable VRRP globally:
1
Select IP Routing > VRRP from the Device Manager menu bar.
The VRRP dialog box appears with the Globals tab displayed (Figure 53).
Figure 53 VRRP dialog box—Globals tab
2
321712-B Rev 03
Select the SendTrap and PingVirtualAddrEnable check boxes as
appropriate.
Chapter 6 Configuring VRRP 149
3
Click Apply.
Table 22 describes the Globals tab fields.
Table 22 Globals tab fields
Field
Description
SendTrap
Indicates whether the VRRP-enabled router generates SNMP
traps for events defined in this MIB:
• Enabled—SNMP traps are sent
• Disabled—no traps are sent
PingVirtualAddrEnable
Used to configure whether this device responds to pings
directed to a virtual router's IP address.
Configuring VRRP for the Interface
VRRP parameters can be configured and managed for the routing interface. To
configure the VRRP interface, follow this procedure:
1
From the Device Manager menu bar, select IP Routing > VRRP.
The VRRP dialog box appears with the Globals tab displayed (Figure 53 on
page 148).
2
Select the Interface tab.
The Interface tab appears (Figure 54). The Interface tab contains a large
number of fields and all fields may not display at once. Use the scroll bars
located above the dialog buttons to view all fields.
Figure 54 VRRP dialog box—Interface tab
3
Edit the desired fields in the appropriate interface.
4
Click Apply.
Configuring IP Routing and Multicast Operations using Device Manager
150 Chapter 6 Configuring VRRP
Table 23 describes the fields in the Interface tab.
Table 23 Interface tab fields
Field
Description
VrId
A number that uniquely identifies a virtual router on a given
VRRP router. The virtual router acts as the default router for
one or more assigned addresses (1 to 255).
Interface
Interface of the VRRP router.
IpAddr
The assigned IP addresses that a virtual router is
responsible for backing up.
VirtualMacAddr
MAC address of the virtual router interface.
State
The state of the virtual router interface:
• initialize—waiting for a startup event
• backup—monitoring availability and state of the master
router
• master—functioning as the forwarding router for the
virtual router IP address
Control
Whether VRRP is enabled or disabled for the VLAN.
Priority
Priority value to be used by this VRRP router. Set a value
from 1 to 255, where 255 is reserved for the router that owns
the IP addresses associated with the virtual router. The
default is 100.
MasterIpAddr
The IP address of the physical interface of the master virtual
router that has the responsibility of forwarding packets sent
to the virtual IP address associated with the virtual router.
FastAdvertisementEnable
Enables or disables the Fast Advertisement Interval.
When disabled, the regular advertisement interval is used.
Default is disable.
AdvertisementInterval
The time interval (in seconds) between sending
advertisement messages. Set from 1 to 255 seconds with a
default of 1 second. Only the master router sends
advertisements.
VirtualRouterUpTime
The time interval (in hundredths of a second) since the virtual
router was initialized.
FastAdvertisementInterval Sets the Fast Advertising Interval, the time interval between
sending VRRP advertisement messages. The interval can be
between 200 and 1 000 milliseconds, and it must be the
same on all participating routers. The default is 200. The
values must be entered in multiples of 200 milliseconds.
VirtualRouterUpTime
321712-B Rev 03
This is the time interval, in hundredths of a second since this
virtual router was initialized.
Chapter 6 Configuring VRRP 151
Table 23 Interface tab fields (continued)
Field
Description
CriticalIpAddrEnable
Sets the IP interface on the local router to enable or disable
the backup.
CriticalIPAddr
An IP interface on the local router configured so that a
change in its state would cause a role switch in the virtual
router (for example, from master to backup) in case the
interface stops responding.
Configuring IP Routing and Multicast Operations using Device Manager
152 Chapter 6 Configuring VRRP
Configuring VRRP Secondary Features
To configure the VRRP secondary features, follow this procedure:
1
From the Device Manager menu bar, select IP Routing > VRRP.
The VRRP dialog box appears with the Globals tab displayed (Figure 53 on
page 148).
2
Select the Secondary Features tab.
The Secondary Features tab appears (Figure 55).
Figure 55 VRRP dialog box—Secondary Feature tab
3
Select the HoldDownTimer field for the desired interface and enter the timer
value in seconds.
Note: The HoldDownState field displays active when the Hold Down
Timer is counting down and preemption will occur; it displays dormant
when preemption is not pending. When the Hold Down Timer is active,
the HoldDownTimeRemaining field displays the seconds remaining
before preemption.
Note: Use the OperAction field to manually override the delay timer
and to force preemption. When this field is clicked, an arrow appears.
Click the field and a list appears. Choose preemption to preempt the
timer, or choose none to allow the timer to keep working.
Note: Use the BackUpMaster field to enable or disable the backup
master feature.
321712-B Rev 03
Chapter 6 Configuring VRRP 153
4
Click Apply.
Table 24 describes the fields in the Secondary Feature tab.
Table 24 Secondary Feature tab fields
Field
Description
VrId
A number that uniquely identifies a virtual router on a given
VRRP router. The virtual router acts as the default router for
one or more assigned addresses (1 to 255).
HoldDownTimer
The time interval (in seconds) a router is delayed for the
following conditions:
• The VRRP Hold Down Timer is executed when the switch
transitions from Init to backup to master. This occurs only
on a switch bootup.
• The VRRP Hold Down Timer is NOT executed under the
following condition: In a non-bootup condition the Backup
switch becomes the master after the Master Downtime
Interval. (3 * hello interval), if the master VR goes down.
• The VRRP Hold Down Timer also applies to the VRRP
BackupMaster feature.
HoldDownState
Status is active when the Hold Down Timer is counting down
and preemption will occur; the text box displays dormant
when preemption is not pending.
HoldDownTimeRemaining The seconds remaining before preemption.
OperAction
Use the action list to manually override the delay timer and
force preemption:
• preemption—preempt the timer
• none—allow the timer to keep working
BackUpMaster
Indicates if the VRRP backup master is enabled or disabled.
This option is not recommended for non Split-MLT ports.
BackUpMastrState
Displays the BackupMaster operational state.
When VRRP is enabled on a switch in a master state, the
BackUpMaster state is DOWN.
When VRRP is enabled on a switch that is in a backup state,
the BackUpMaster state is UP.
States:
• up: in BackupMaster state
• down: original state
Configuring IP Routing and Multicast Operations using Device Manager
154 Chapter 6 Configuring VRRP
Configuring VRRP on a VLAN
Before VRRP can be configured on a VLAN, it must first be enabled globally.
VRRP can only be configured on a VLAN if the VLAN has been assigned an IP
address.
To configure VRRP on a VLAN follow this procedure:
1
From the Device Manager menu bar, select VLAN > VLANs.
The VLAN dialog box appears with the Basic tab displayed (Figure 56).
Figure 56 VLAN dialog box—Basic tab
321712-B Rev 03
Chapter 6 Configuring VRRP 155
2
Select a VLAN by clicking in a column of the appropriate row.
3
Click IP.
The IP, VLAN dialog box appears with the IP Address tab displayed.
4
Select the VRRP tab.
The VRRP tab appears (Figure 57).
Figure 57 IP, VLAN dialog box—VRRP tab
5
Click Insert.
The IP, VLAN, Insert VRRP dialog box appears (Figure 58).
Figure 58 IP, VLAN, Insert VRRP dialog box
6
Using the fields provided, configure VRRP for the VLAN.
7
Click Insert.
Configuring IP Routing and Multicast Operations using Device Manager
156 Chapter 6 Configuring VRRP
Table 25 describes the IP, VLAN, Insert VRRP dialog box fields.
Table 25 IP, VLAN, Insert VRRP dialog box fields
Field
Description
VrId
A number that uniquely identifies a virtual router on a given
VRRP router. The virtual router acts as the default router
for one or more assigned addresses (1 to 255).
IpAddr
IP address of the virtual router interface.
Control
Whether VRRP is enabled or disabled for the VLAN.
Priority
Priority value to be used by this VRRP router. Set a value
from 1 to 255, where 255 is reserved for the router that
owns the IP addresses associated with the virtual router.
The default is 100.
FastAdvertisementEnable
Enables or disables the Fast Advertisement Interval.
When disabled, the regular advertisement interval is used.
Default is disable.
AdvertisementInterval
The time interval (in seconds) between sending
advertisement messages. Set from 1 to 255 seconds with a
default of 1 second. Only the master router sends
advertisements.
FastAdvertisementInterval
Sets the Fast Advertising Interval, the time interval
between sending VRRP advertisement messages. The
interval can be between 200 and 1 000 milliseconds, and it
must be the same on all participating routers. The default is
200. The values must be entered in multiples of 200
milliseconds.
CriticalIpAddrEnable
Sets the IP interface on the local router to enable or disable
the backup.
CriticalIpAddr
Indicates if the user-defined critical IP address is enabled.
There is no effect if a user-defined IP address does not
exist.
• No—use the default IP address (0.0.0.0)
321712-B Rev 03
Chapter 6 Configuring VRRP 157
Table 25 IP, VLAN, Insert VRRP dialog box fields
Field
Description
HoldDownTimer
The time interval (in seconds) a router is delayed for the
following conditions:
• The VRRP Hold Down Timer is executed when the
switch transitions from Init to backup to master. This
occurs only on a switch bootup.
• The VRRP Hold Down Timer is NOT executed under
the following condition: In a non-bootup condition, the
Backup switch becomes master after the Master
Downtime Interval. (3 * hello interval), if the master VR
goes down.
• The VRRP Hold Down Timer also applies to the VRRP
BackupMaster feature.
OperAction
Use the action list to manually override the delay timer and
force preemption:
• preemptHoldDownTimer—preempt the timer
• none—allow the timer to keep working
BackUpMaster
Enables or disables the VRRP backup master switch.
Viewing VRRP Interface Statistics
To view VRRP interface statistics, perform the following procedure:
1
Select VLAN > VLANS from the Device Manager menu.
The VLAN dialog will open with the Basic tab selected.
2
Choose a VLAN by selecting a column in the appropriate row of the Basic
tab.
3
Click IP.
The IP, VLAN dialog will open with the IP Address tab selected.
4
Select the VRRP tab.
5
Choose a VRRP entry by selecting a column in the appropriate row of the
VRRP tab.
6
Click Graph.
Configuring IP Routing and Multicast Operations using Device Manager
158 Chapter 6 Configuring VRRP
The VRRP Stats dialog box appears. This dialog box is illustrated in
Figure 59.
Figure 59 VRRP Stats dialog box
Table 26 describes the fields on this dialog.
Table 26 VRRP Stats Dialog Fields
Fields
Description
BecomeMaster
The total number of times that this virtual router's state
has transitioned from BACKUP to MASTER.
AdvertiseRcvd
The total number of VRRP advertisements received by
this virtual router.
ChecksumErrors
The total number of VRRP packets received with an
invalid checksum value.
VersionErrors
The total number of VRRP packets received with an
invalid version number.
VrIdErrors
The total number of VRRP packets received with an
invalid VRID for this virtual router.
AdvertiseIntervalErrors
The total number of VRRP advertisement packets
received for which the advertisement interval is different
than the one configured for the local virtual router.
321712-B Rev 03
Chapter 6 Configuring VRRP 159
Table 26 VRRP Stats Dialog Fields (continued)
Fields
Description
PasswdSecurityViolations
The total number of VRRP packets received that do not
pass the simple text password authentication check.
HmacSecurityViolations
The total number of VRRP packets received that do not
pass the HMAC-MD5-96 authentication check.
IpTtlErrors
The total number of VRRP packets received by the virtual
router with an IP TTL (Time-To-Live) not equal to 255.
PriorityZeroPktsRcvd
The total number of VRRP packets received by the virtual
router with a priority of 0.
PriorityZeroPktsSent
The total number of VRRP packets sent by the virtual
router with a priority of 0.
InvalidTypePktsRcvd
The number of VRRP packets received by the virtual
router with an invalid value in the type field.
AddressListErrors
The number of packets received where the address list
does not match the locally configured list for the virtual
router.
UnknownAuthType
The number of packets received with an unknown
authentication type.
AuthTypeErrors
The number of packets received with an Auth Type not
equal to the locally configured authentication method.
Configuring the Fast Advertisement Interval
The following sections discuss the configuration of the Fast Advertisement
Interval on a VLAN.
Configuring the Fast Advertisement Interval on a VLAN
To configure the Fast Advertisement Interval on a VLAN, follow this procedure:
1
From the Device Manager menu bar, select VLAN > VLANs.
The VLAN dialog box appears with the Basic tab displayed (Figure 56 on
page 154).
2
Select a VLAN by clicking in a column of the desired row.
3
Click IP.
Configuring IP Routing and Multicast Operations using Device Manager
160 Chapter 6 Configuring VRRP
The IP, VLAN dialog box appears with the IP Address tab displayed.
4
Select the VRRP tab.
5
Click Insert.
The IP, VLAN, Insert VRRP dialog box appears (Figure 58 on page 155).
6
Select the enable option button in the FastAdvertisementEnable area.
7
In the AdvertisementInterval field, enter an interval in seconds.
8
Click Insert.
Refer to Table 25 on page 156 for a description of the VRRP Insert fields.
321712-B Rev 03
161
Chapter 7
Configuring RIP
In a routed environment, routers communicate with one another to keep track of
available routes. Routers can learn about available routes dynamically using the
Routing Information Protocol (RIP). RIP is a standard routing protocol based on
the Bellman-Ford (or distance vector) algorithm. It is used as an Interior Gateway
Protocol (IGP). For conceptual information about RIP, refer to “IP routing and
multicast concepts” on page 29.
The Ethernet Routing Switch 1600 Series supports the use of RIP to exchange
information with other routers to compute routes through an IPv4-based network.
By default, RIP is disabled globally and on every interface. RIP must be
configured globally and on the interface in order for a RIP configuration to take
effect.
Note: In the Ethernet Routing Switch 1600 Series, RIP is configurable
only for VLANs. There is no brouter port on the Ethernet Routing
Switch 1600 Series.
The basic steps for enabling and configuring RIP are:
1
Enable and configure RIP globally. Refer to “Enabling and Configuring
Global RIP Parameters” on page 163 for this procedure.
2
Create and configure the IP interfaces. Refer to “Router Interface Types” on
page 91 for this procedure.
3
Enable and configure RIP on the IP interfaces. Refer to “Enabling and
Configuring RIP on a VLAN” on page 165 for this procedure.
Configuring IP Routing and Multicast Operations using Device Manager
162 Chapter 7 Configuring RIP
4
Configure RIP send and receive versions on the IP interfaces. Refer to “RIP
Versioning Configuration” on page 170 for this procedure.
Note: RIP can be configured on IP interfaces even when it is disabled
globally. This means RIP can be configured on the interfaces before it is
enabled on the switch.
This section includes the following topics:
•
•
•
•
•
321712-B Rev 03
“Enabling and Configuring Global RIP Parameters” on page 163
“Enabling and Configuring RIP on a VLAN” on page 165
“RIP Versioning Configuration” on page 170
“RIP Interface Management” on page 173
“Viewing RIP Statistics” on page 175
Chapter 7 Configuring RIP 163
Enabling and Configuring Global RIP Parameters
In the Ethernet Routing Switch 1600 Series, the global RIP parameters are used
by all router interfaces using RIP.
To enable and configure global RIP parameters, follow this procedure:
1
From the Device Manager menu bar, select IP Routing > RIP.
The RIP dialog box appears with the Globals tab displayed (Figure 60).
Figure 60 RIP dialog box—Globals tab
2
Select enable from the Operation section to globally enable RIP.
3
Enter a value in seconds in the UpdateTime field or accept the default of 30
seconds.
4
Enter a value in seconds in the HoldDownTime field or accept the default of
120 seconds.
5
Enter a value in seconds in the TimeOutInterval field or accept the default
value of 180 seconds.
6
Enter a value in the DefImportMetric field or accept the default value of 8.
Configuring IP Routing and Multicast Operations using Device Manager
164 Chapter 7 Configuring RIP
7
Click Apply.
Note: RIP can be configured on interfaces before it is globally enabled.
This means RIP interfaces can be configured before it is enabled on the
switch.
Table 27 describes the RIP dialog box—Globals tab fields.
Table 27 RIP dialog box—Globals tab fields
Field
Description
Operation
Enables or disables RIP operation on the switch. The default is
disabled.
UpdateTime
Sets the RIPupdate timer. The value of the update timer is the time
interval (in seconds) between regular RIP updates. The range is 1 to
2 147 483 647, and the default is 30 seconds.
The global UpdateTime parameter sets the update timer for the VLAN
interfaces.
The UpdateTime value must be less than the timeout interval.
RouteChanges
Reports the number of route changes made to the IP routing database
by RIP. Refreshing an aged route is not considered a change.
Queries
Reports the number of responses sent to RIP queries from other
systems.
HoldDownTime
Sets the RIP Hold Down Timer. The value of the Hold Down Timer is
the length of time (in seconds) that RIP continues to advertise a
network after determining that it is unreachable. The range is 0 to 360,
and the default is 120 seconds.
The global HoldDownTime parameter sets the default value of the
Hold Down Timer for the VLAN interfaces.
321712-B Rev 03
Chapter 7 Configuring RIP 165
Table 27 RIP dialog box—Globals tab fields (continued)
Field
Description
TimeOutInterval Sets the RIP timeout interval. The range is 15 to 259 200.
The default value is set indirectly by the global UpdateTime parameter.
By default, the timeout timer is set at 6 times the update timer, in
accordance with the RFC specification. With a default global
UpdateTime of 30 seconds, the default TimeOutInterval is 180
seconds.
Configure the TimeOutInterval only if you want to break the
relationship with the update timer. For example, if you have set the
global UpdateTime parameter to a very short interval in order to
minimize the problem of fast convergence, the associated default
TimeOutInterval may be too short. In this case, configure the
TimeOutInterval manually.
The global TimeOutInterval parameter sets the default value of the
timeout timer for the VLAN interfaces.
The timeout interval must be greater than the UpdateTime.
DefImportMetric Sets the value of the default metric to apply to routes imported into the
RIP domain. This is the metric used for routes not learned through RIP
if a route policy does not specify a metric for a particular protocol, such
as OSPF. The range is 0 to 15, and the default is 8.
Use a value of 0 for deconfiguration.
Enabling and Configuring RIP on a VLAN
In the Ethernet Routing Switch 1600 Series, RIP global parameters supply the
defaults used by all other router interfaces. The RIP update timer and
DefImportMetric parameters are global settings that are not configurable per
interface. All other global parameters can be overridden by interface parameter
settings.
In addition to being enabled globally on the switch, RIP must be enabled
separately on each participating interface.
To enable and configure RIP on a VLAN, do the following:
1
From the Device Manager menu bar, choose VLAN > VLANs.
The VLAN dialog box appears with the Basic tab displayed (see Figure 22 on
page 93).
Configuring IP Routing and Multicast Operations using Device Manager
166 Chapter 7 Configuring RIP
2
Select a VLAN by clicking in a column of the desired row.
3
Click IP.
The IP, VLAN dialog box appears with the IP Address tab displayed (see
Figure 23 on page 93).
4
Select the RIP tab.
The IP, VLAN dialog box—RIP tab appears (Figure 61).
Figure 61 IP, VLAN dialog box—RIP tab
5
Select the Enable check box to enable RIP on the interface.
6
To set RIP Supply, Listen, and Poison parameters, select the enable or
disable option buttons.
7
To enable the DefaultSupply, DefaultListen, TriggeredUpdateEnable,
AutoAggregateEnable, and AdvertiseWhenDown parameters, select the
applicable check boxes.
321712-B Rev 03
Chapter 7 Configuring RIP 167
8
To apply a RIP In or Out policy:
a
Click the ellipse button next to the InPolicy or OutPolicy field as
applicable.
The InPolicy or OutPolicy list box appears, displaying preconfigured
policies. Refer to “Configuring Filtering Policies on a RIP Interface” on
page 142 for policy creation procedures.
9
b
Select a policy. Only one policy can be selected. To change which policy
to apply, simply select the new policy. To deselect a policy (so that no
policy is applied), press CTRL + the left mouse button on the selected
policy.
c
Click Ok.
In the Cost field, type the metric for the interface.
10 In the HolddownTime field, enter a value to set the Hold Down Timer.
11 In the TimeoutInterval field, enter a value to set the timeout timer. The
timeout interval must be greater than the global RIP update interval.
12 Click Apply.
Table 28 describes the IP, VLAN dialog box—RIP tab.
Table 28 IP, VLAN dialog box—RIP tab fields
Field
Description
Enable
If selected, enables RIP on the interface. The default is
false (disabled).
Supply
Specifies that the routing switch advertises RIP routes
through the interface. The default is enable.
Listen
Specifies that the routing switch learns RIP routes through
this interface. The default is enable.
Configuring IP Routing and Multicast Operations using Device Manager
168 Chapter 7 Configuring RIP
Table 28 IP, VLAN dialog box—RIP tab fields (continued)
Field
Description
Poison
Specifies whether or not RIP routes on the interface learned
from a neighbor are advertised back to the neighbor.
• If disabled, split horizon is invoked, and IP routes
learned from an immediate neighbor are not advertised
back to the neighbor.
• If enabled, the RIP updates sent to a neighbor from
which a route is learned are “poisoned” with a metric of
16. Therefore, the receiver neighbor ignores this route
because the metric 16 indicates infinite hops in the
network.
The default is disable.
DefaultSupply
Specifies whether or not the interface sends RIP
advertisements for the default route, if one exists in the
routing table. The default is false (disabled).
DefaultListen
Specifies whether or not the interface listens for RIP
updates for the default route learned through RIP. The
default is false (disabled).
TriggeredUpdateEnable
Enables or disables automatic triggered updates for RIP on
this interface. The default is false (disabled).
AutoAggregateEnable
Enables or disables automatic route aggregation on the
interface. When enabled, the router switch automatically
aggregates routes to their natural mask when they are
advertised on an interface in a network of a different class.
Routes with different metrics can be aggregated. RIP uses
the out metric associated with the first route found in the
routing table that is to be aggregated.
Automatic route aggregation can be enabled only in RIP2
mode or RIP1 compatibility mode. The default is false
(disabled).
AdvertiseWhenDown
Specifies whether or not the network on this interface is
advertised as up, even if the port is down. The default is
false (disabled).
Note: When you configure a VLAN without any link and
enable AdvertiseWhenDown, it does not advertise the route
until the port is active. Then the route is advertised even
when the link is down. To disable advertising based on link
states, disable AdvertiseWhenDown.
InPolicy
Click the ellipse button or double-click in the InPolicy name
field and select the policy name to be applied from the
PolicyName dialog box. The policy determines which routes
are learned on this interface. The policy also specifies the
parameters of the route when it is added to the routing
table.
321712-B Rev 03
Chapter 7 Configuring RIP 169
Table 28 IP, VLAN dialog box—RIP tab fields (continued)
Field
Description
OutPolicy
Click the ellipse button or double-click in the OutPolicy
name field and select the policy name to be applied from
the PolicyName dialog box. The policy determines which
routes are advertised from the routing table on the interface.
The policy also specifies the parameters of the
advertisement.
Cost
Indicates the RIP cost (metric) for this interface. Enter an
integer value between 1 and 15. The default is 1.
HolddownTime
Sets the RIP Hold Down Timer for the interface. The value
of the Hold Down Timer is the length of time (in seconds)
that RIP continues to advertise a network after determining
that it is unreachable. Enter an integer value between 0 and
360. The default value is set by the global holddown
parameter, which has a default of 120 seconds. The
interface timer setting overrides the global parameter.
However, if you subsequently reset the global parameter,
the global setting then overrides the interface timer setting.
TimeoutInterval
Sets the RIP timeout interval for the interface. Enter an
integer value between 15 and 259 200.
The default value is set indirectly by the global update time
parameter. By default, the timeout timer is set at 6 times the
update timer, in accordance with the RFC specification.
With a default global update timer setting of 30 seconds, the
default timeout interval is 180 seconds.
Configure the timeout parameter on the interface only if you
want to break the relationship with the update timer. For
example, if you have set the global update parameter to a
very short interval in order to minimize the problem of fast
convergence, the associated default timeout may be too
short. In this case, configure the interface timeout interval
manually.
The interface timer setting overrides the global parameter.
However, if you subsequently reset the global parameter,
the global setting then overrides the interface timer setting.
The TimeoutInterval must be greater than the global
UpdateTime value.
Configuring IP Routing and Multicast Operations using Device Manager
170 Chapter 7 Configuring RIP
RIP Supply and Listen Settings
Table 29 shows the relationship between switch action and the RIP supply and
listen settings.
Table 29 RIP supply and listen settings and switch action
RIP supply settings
RIP listen settings
Listen
Defaultlisten
Switch action
Supply
Default-supply
Disabled
Disabled
Sends no RIP updates.
Enabled
Disabled
Sends RIP updates for all
routes except the default route.
Disabled
Enabled
Sends RIP updates for the
default route only (default route
must exist in the routing table).
Enabled
Enabled
Sends RIP updates including
the default route (if it exists).
Disabled
Disabled
Does not listen for RIP
updates.
Enabled
Disabled
Listens for all RIP updates
except the default route.
Disabled
Enabled
Listens only for RIP updates of
the default route.
Enabled
Enabled
Listens for all RIP updates
including the default route (if it
exists).
RIP Versioning Configuration
Interfaces can be configured to use different RIP versions when sending or
receiving RIP updates.
Note: The AuthType and AuthKey parameters are not supported.
321712-B Rev 03
Chapter 7 Configuring RIP 171
To configure RIP versioning, follow this procedure:
1
From the menu bar, choose IP Routing > RIP.
The RIP dialog box appears with the Globals tab displayed (see Figure 60 on
page 163).
2
Select the Interface tab.
The RIP dialog box—Interface tab appears (Figure 62).
Figure 62 RIP dialog box—Interface tab
3
Set the Send or Receive fields by double-clicking the applicable field and
selecting a value from the provided list.
4
Click Apply.
Table 30 describes the RIP dialog box—Interface tab fields.
Table 30 RIP dialog box—Interface tab fields
Field
Description
Address
The IP address of the router interface.
Domain
The value inserted into the Routing Domain field of all RIP packets sent
on this interface. The default is 0.
AuthType
The type of authentication used on this interface.
AuthKey
The value to be used as the Authentication Key whenever the
corresponding instance of rip2IfConfAuthType has a value other than
noAuthentication.
Configuring IP Routing and Multicast Operations using Device Manager
172 Chapter 7 Configuring RIP
Table 30 RIP dialog box—Interface tab fields (continued)
Field
Description
Send
Indicates which version of RIP updates the router sends on this interface:
• DoNotSend—no RIP updates sent on this interface
• ripVersion1—RIP broadcast updates compliant with RFC 1058
• rip1Compatible—compatible with RIP version 1 (RIP version 2
updates are broadcast using RFC 1058 route subsumption rules)
• ripVersion2—multicast RIP updates compliant with RFC 2453
The default is rip1Compatible.
Refer to “RIP Send Modes” on page 172 for more information.
Receive
Indicates which versions of RIP updates are to be accepted on this
interface:
• rip1 (complies with RFC 1058)
• rip2 (complies with RFC 2453)
• rip1OrRip2 (both versions of RIP)
The default is rip1OrRip2.
Note: rip2 and rip1OrRip2 imply reception of multicast packets.
RIP Send Modes
Table 31 describes the RIP send modes supported on the Ethernet Routing Switch
1600 Series. RIP send modes can be configured on all VLAN interfaces.
Table 31 RIP send modes
Mode
Description
Result
rip1
Broadcasts RIP updates that are
compliant with RFC 1058.
•
•
•
•
rip1comp
Broadcasts RIP-2 updates using
RFC 1058 route subsumption rules.
This is the default mode.
•
•
•
•
321712-B Rev 03
Destination MAC is a broadcast, ff-ff-ff-ff-ff-ff
Destination IP is a broadcast for the network (for
example, 192.1.2.255)
RIP update is formed as a RIP-1 update, no
network mask included
RIP version = 1
Destination MAC is a broadcast, ff-ff-ff-ff-ff-ff
Destination IP is a broadcast for the network (for
example, 192.1.2.255)
RIP update is formed as a RIP-2 update,
including network mask
RIP version = 2
Chapter 7 Configuring RIP 173
Table 31 RIP send modes (continued)
Mode
Description
Result
rip2
RIP-2 updates are multicast.
•
•
•
•
notsend
No RIP updates are sent on the
interface.
Destination MAC is a multicast,
01-00-5e-00-00-09
Destination IP is the RIP-2 multicast address,
224.0.0.9
RIP update is formed as a RIP-2 update,
including network mask
RIP version = 2
None
RIP Interface Management
To view and edit RIP configuration on the interface, follow this procedure:
1
From the Device Manager menu bar, choose IP Routing > RIP.
The RIP dialog box appears with the Globals tab displayed (see Figure 60 on
page 163).
2
Click the Interface Advance tab.
The Interface Advance tab appears (Figure 63). If all fields do not fully
display on the screen, use the scroll bar above the buttons to scroll across and
display all fields on the tab.
Figure 63 RIP dialog box—Interface Advance tab
3
Double-click in any field to display a list or dialog box from which alternative
parameter settings can be selected.
4
Click Apply.
Configuring IP Routing and Multicast Operations using Device Manager
174 Chapter 7 Configuring RIP
Table 32 describes the RIP dialog box—Interface Advance tab fields.
Table 32 RIP dialog box—Interface Advance tab fields
Field
Description
Address
Displays the IP address of the interface.
Interface
Displays the interface identification.
Enable
Displays whether RIP is enabled or disabled on the interface.
Supply
Displays whether the switch is enabled (true) or disabled (false) to
send out RIP updates on this interface.
Listen
Displays whether the switch is enabled (true) or disabled (false) to
learn routes on this interface.
Poison
Displays whether or not RIP routes on the interface learned from a
neighbor are advertised back to the neighbor. If disabled (false),
split horizon is invoked and IP routes learned from an immediate
neighbor are not advertised back to the neighbor. If enabled (true),
the RIP updates sent to a neighbor from which a route is learned
are “poisoned” with a metric of 16. Therefore, the receiver
neighbor ignores this route because the metric 16 indicates infinite
hops in the network.
DefaultSupply
Displays whether advertisement of a default route is enabled (true)
or disabled (false) on this interface. This command takes effect
only if a default route exists in the routing table.
DefaultListen
Displays whether the switch is enabled (true) or disabled (false) to
accept the default route learned through RIP on this interface.
TriggeredUpdate
Displays whether the switch is enabled (true) or disabled (false) to
send out RIP updates on this interface.
AutoAggregate
Displays whether automatic route aggregation is enabled (true) or
disabled (false) on this interface. When enabled, the switch
automatically aggregates routes to their natural mask when they
are advertised on an interface.
InPolicy
Indicates the policy that determines whether to learn a route on
this interface. The policy also specifies the parameters of the route
when it is added to the routing table.
OutPolicy
Indicates the policy that determines whether to advertise a route
from the routing table on this interface. The policy also specifies
the parameters of the advertisement.
Cost
Indicates the RIP cost (metric) for this interface. Enter a value
between1 to 15. The default is 1.
321712-B Rev 03
Chapter 7 Configuring RIP 175
Table 32 RIP dialog box—Interface Advance tab fields (continued)
Field
Description
Holddown Time
Indicates the value of the RIP Hold Down Timer for the interface.
The value of the Hold Down Timer is the length of time (in
seconds) that RIP continues to advertise a network after
determining that it is unreachable. Enter an integer value between
0 and 360. The default value is set by the global holddown
parameter, which has a default of 120 seconds. The interface timer
setting overrides the global parameter and does not change if the
global parameter is changed.
TimeoutInterval
Indicates the RIP timeout interval for the interface. Enter an integer
value between 15 and 259 200.
The default value is set indirectly by the global update time
parameter. By default, the timeout timer is set at 6 times the update
timer, in accordance with the RFC specification. With a default
global update timer setting of 30 seconds, the default timeout
interval is 180 seconds. The default interface timeout setting
changes when the global update time parameter is changed.
Configure the timeout parameter on the interface only if you want
to break the relationship with the update timer. For example, if you
have set the global update parameter to a very short interval in
order to minimize the problem of fast convergence, the associated
default timeout may be too short. In this case, configure the
interface timeout interval manually.
Viewing RIP Statistics
To view the RIP statistics, follow this procedure:
1
From the Device Manager menu bar, choose IP Routing > RIP.
The RIP dialog box appears with the Globals tab displayed (see Figure 60 on
page 163).
2
Select the Status tab.
The Status tab appears (Figure 64).
Configuring IP Routing and Multicast Operations using Device Manager
176 Chapter 7 Configuring RIP
Figure 64 RIP dialog box—Status tab
Table 33 describes the RIP dialog box—Status tab fields.
Table 33 RIP dialog box—Status tab fields
Field
Description
Address
The IP address of the interface.
RcvBadPackets
The number of RIP response packets received by the RIP process
that were subsequently discarded for any reason.
(Example: A version 0 packet or an unknown command type.)
RcvBadRoutes
The number of routes, in valid RIP packets, that were ignored for
any reason.
(Example: Unknown address family or invalid metric.)
SentUpdates
The number of triggered RIP updates actually sent on this interface.
This field explicitly does not include full updates sent containing
new information.
321712-B Rev 03
177
Chapter 8
Configuring OSPF
The Open Shortest Path First (OSPF) protocol is a link-state protocol. The state of
a link, or interface on a router, is a description of that interface and its relationship
to its neighboring routers. The link-state description includes, for example, the IP
address of the interface, the mask, the type of network it is connected to, the
routers connected to that network, and so on. The collection of all these link-states
form the link-state database. OSPF uses this link-state database to build and
calculate the shortest path to all known destinations.
Note: OSPF parameters can only be configured on an interface that has
an IP address assigned to it.
For conceptual information about OSPF management, refer to “IP routing and
multicast concepts” on page 29.
This section contains the following concepts:
•
•
•
•
•
•
•
•
•
•
•
“Viewing General OSPF Information” on page 178
“Enabling or Disabling OSPF on a Router” on page 180
“Manually Initiating an SPF Run” on page 181
“Configuring OSPF Interfaces” on page 182
“Managing an OSPF VLAN interface” on page 191
“Managing OSPF Area Information” on page 197
“Creating a Virtual Link” on page 201
“Specifying ASBRs” on page 207
“Configuring Metric Speed” on page 208
“Viewing Stub Area Metrics” on page 210
“Viewing Advertisements in the link state database” on page 211
Configuring IP Routing and Multicast Operations using Device Manager
178 Chapter 8 Configuring OSPF
•
•
•
“Viewing the External Link State Database” on page 212
“Inserting OSPF Area Aggregate Ranges” on page 213
“Configuring an OSPF Redistribution Policy” on page 216
Viewing General OSPF Information
To view general OSPF information:
1
From the Device Manager menu bar, select IP Routing > OSPF.
The OSPF dialog box appears with the General tab displayed (Figure 65).
Figure 65 OSPF dialog box—General tab
321712-B Rev 03
Chapter 8 Configuring OSPF 179
Table 34 describes the General tab fields.
Table 34 General tab fields
Field
Description
RouterID
The Router ID, which in OSPF has the same format as an
IP address but identifies the router independent of other
routers in the OSPF domain.
AdminStat
The administrative status of OSPF in the router. The value
enabled denotes that the OSPF process is active on at
least one interface; disabled disables it on all
interfaces.The default is disabled.
VersionNumber
Current version number of OSPF.
AreaBdrRtrStatus
A flag to note if this router is an area border router (ABR).
Note: AreaBdrRtrStatus value must be true to create a
virtual router interface.
ASBdrRtrStatus
When the ASBdrRtrStatus option is selected, the router is
configured as an autonomous system boundary router
(ASBR).
ExternLsaCount
The number of external (LS type 5) link state
advertisements in the link state database.
ExternLsaCksumSum
The 32-bit unsigned sum of the LS checksums of the
external link state advertisements contained in the link
state database. This sum is used to determine if there has
been a change in a router’s link state database and to
compare the link state databases of two routers.
OriginateNewLsas
The number of new link state advertisements that have
been originated. This number is incremented each time the
router originates a new LSA.
RxNewLsas
The number of link state advertisements received that are
determined to be new instantiations. This number does not
include newer instantiations of self-originated link state
advertisements.
10MbpsPortDefaultMetric
Indicates the default cost to be applied to the 10 Mb/s
interface (port). The default is 100.
100MbpsPortDefaultMetric
Indicates the default cost to be applied to the 100 Mb/s
interface (port). The default is 10.
1000MbpsPortDefaultMetric Indicates the default cost to be applied to the 1 000 Mb/s
interface (port). The default is 1.
1000MbpsPortDefaultMetric Indicates the default cost to be applied to the 10 000 Mb/s
interface (port). The default is 1.
TrapEnable
Indicates whether or not to enable traps relating to the
OSPF. The default is false.
Configuring IP Routing and Multicast Operations using Device Manager
180 Chapter 8 Configuring OSPF
Table 34 General tab fields (continued)
Field
Description
AutoVirtLinkEnable
Enables or disables automatic creation of virtual links. The
default is false.
SpfHoldDownTime
Changes the OSPF hold-down timer value (3 to 60
seconds). The default is 10 seconds.
OspfAction
Initiates a new SPF run to update the routing table. The
default is none.
LastSpfRun
Used to indicate the time (SysUpTime) since the last SPF
calculated by OSPF.
Enabling or Disabling OSPF on a Router
When configuring an interface for the OSPF protocol, OSPF must first be enabled
globally and the interface assigned an IP address. After these two tasks have been
completed, OSPF can be configured on the interface.
To enable or disable OSPF globally on a router, perform the following task:
1
From the Device Manager menu bar, select IP Routing > OSPF.
The OSPF dialog box appears with the General tab displayed (Figure 65 on
page 178).
2
In the AdminStat area, select the enabled option button to activate OSPF, or
disabled to deactivate OSPF.
3
Click Apply.
The OSPF protocol is enabled (or disabled) on this router.
Table 34 on page 179 describes the General tab fields.
321712-B Rev 03
Chapter 8 Configuring OSPF 181
Manually Initiating an SPF Run
From the OSPF General tab (IP Routing > OSPF) an SPF, or Dijkstra, run can
be manually initiated to immediately update the OSPF link-state database. This is
useful in such instances as:
•
•
A deleted OSPF-learned route needs to be immediately restored.
As a debug mechanism when the routing table’s entries and the link-state
database are out of sync.
To force an SPF run, perform the following procedure:
1
From the Device Manager menu bar, select IP Routing > OSPF.
The OSPF dialog box appears with the General tab displayed (Figure 65 on
page 178).
2
In the OSPF Action area, select the runSpf option button.
3
Click Apply.
Device Manager displays a prompt confirming the SPF run request
(Figure 66).
Figure 66 Force SPF run dialog box
4
Click Yes to confirm the forced SPF run.
The router performs the SPF run and the OSPF link state database is updated.
Table 34 on page 179 describes the General tab fields.
Configuring IP Routing and Multicast Operations using Device Manager
182 Chapter 8 Configuring OSPF
Configuring OSPF Interfaces
An OSPF interface, or link, is configured on an IP interface. In the Ethernet
Routing Switch 1600 Series, an IP interface can be either a single link (brouter
port) or a logical interface configured on a VLAN (multiple ports). The state
information associated with the interface is obtained from the underlying
lower-level protocols and the routing protocol itself.
Before OSPF can be configured on a router interface, it must first be enabled
globally on the router and the interface must be assigned an IP address.
When an OSPF interface is enabled, it is designated as one of the following types:
•
•
•
broadcast (active)
non-broadcast multiaccess (NBMA)
passive
Note: When an OSPF interface is enabled, the interface type cannot be
changed. The interface must first be disabled and then the type can be
changed and re-enabled. If it is an NBMA interface, the manually
configured neighbors must first be deleted.
This section includes the following topics:
•
•
•
•
“Viewing OSPF Interface Information” on page 182
“Creating an OSPF Interface” on page 185
“Changing an OSPF Interface Type” on page 187
“Configuring OSPF NBMA Interfaces” on page 188
Viewing OSPF Interface Information
To view OSPF interface information, follow this procedure:
1
From the Device Manager menu bar, select IP Routing > OSPF.
The OSPF dialog box appears with the General tab displayed (Figure 65 on
page 178).
321712-B Rev 03
Chapter 8 Configuring OSPF 183
2
Select the Interfaces tab.
The OSPF dialog box—Interfaces tab appears (Figure 67). The Interfaces
tab contains a large number of fields and all fields may not be viewable at
once. Use the scroll bars located above the dialog buttons to view all fields.
Figure 67 OSPF dialog box—Interfaces tab
Table 35 describes the OSPF dialog box—Interfaces tab fields.
Table 35 OSPF dialog box—Interfaces tab fields
Field
Description
IpAddress
IP address of the current OSPF interface
AddressLessIf
Designates whether an interface has an IP address.
Interfaces with an IP address = 0
Interfaces without IP address = ifIndex
AreaId
Dotted decimal value to designate the OSPF area name.
For VLANs, keeping the default area setting on the
interface causes the LSDB to be inconsistent.
Note: The area name is not related to an IP address. You
can use any value for the OSPF area name (for example,
1.1.1.1 or 200.200.200.200).
AdminStat
Current administrative state of the OSPF interface (enabled
or disabled).
State
Current DR state of the OSPF interface (DR, BDR,
OtherDR)
Configuring IP Routing and Multicast Operations using Device Manager
184 Chapter 8 Configuring OSPF
Table 35 OSPF dialog box—Interfaces tab fields
Field
Description
Rtrpriority
OSPF priority for the interface during the election process
for the designated router. The interface with the highest
priority number is the designated router. The interface with
the second-highest priority becomes the backup
designated router. If the priority is 0, the interface cannot
become the designated router or the backup. The priority is
used only during election of the designated router and
backup designated router. The range is 0 to 255. The
default is 1.
DesignatedRouter
IP address of the router elected by the Hello Protocol to
send link state advertisements on behalf of the NBMA
network.
BackupDesignatedRouter
IP address of the router elected by the Hello Protocol to
send link state advertisements on behalf of the NBMA
network if the designated router fails.
Type
Type of OSPF interface (broadcast, nbma, or passive)
AuthType
Type of authentication required for the interface.
• none = No authentication required.
• simple password = All OSPF updates received by the
interface must contain the authentication key specified
in the interface AuthKey field.
• MD5 authentication = All OSPF updates received by
the interface must contain the md5 key.
AuthKey
Key (up to 8 characters) required when simple password
authentication is specified in the interface AuthType field.
HelloInterval
Length of time, in seconds, between hello packets. This
value must be the same for all routers attached to a
common network. The default is 10 seconds.
Note: When you change the Hello interval values, you
must save the configuration file and reboot the switch for
the values to be restored and checked for consistency.
TransitDelay
Length of time, in seconds, between 1 and 3 600, required
to transmit an LSA update packet over the interface.
RetransInterval
Length of time, in seconds, between 1 and 3 600, required
between LSA retransmissions.
RtrDeadInterval
Interval used by adjacent routers to determine if the router
has been removed from the network. This interval must be
identical on all routers on the subnet and a minimum of four
times the Hello Interval. To avoid interpretability issues, the
RtrDeadInterval value for the OSPF interface needs to
match with the RtrDeadInterval value for the OSPF virtual
interface.The default is 40 seconds.
321712-B Rev 03
Chapter 8 Configuring OSPF 185
Table 35 OSPF dialog box—Interfaces tab fields
Field
Description
PollInterval
Length of time, in seconds, between hello packets sent to
an inactive OSPF router.
Events
Number of state changes or error events that have
occurred through all interfaces.
Creating an OSPF Interface
To create an OSPF interface, follow this procedure:
1
From the Device Manager menu bar, select IP Routing > OSPF.
The OSPF dialog box appears with the General tab displayed (Figure 65 on
page 178).
2
Select the Interfaces tab.
The Interfaces tab appears (Figure 67 on page 183).
3
Click Insert.
The OSPF, Insert Interfaces dialog box appears (Figure 68 on page 186).
Configuring IP Routing and Multicast Operations using Device Manager
186 Chapter 8 Configuring OSPF
Figure 68 OSPF Insert Interfaces dialog box
4
Select the IP address for the interface from the IP Address list.
5
In the Type area, select the option button that represents the type of OSPF
interface to create (broadcast, NBMA, or passive).
6
Designate a router priority by entering a value in the RtrPriority field.
7
Designate values for the HelloInterval, RtrDeadInterval, or PollInterval by
typing them into the appropriate fields.
8
Define interface authentication by selecting either the none, simplePassword,
or md5 option button in the AuthType area.
If simplePassword is chosen, type a password of up to eight characters in the
AuthKey field.
9
Click Insert.
10 Click Apply.
321712-B Rev 03
Chapter 8 Configuring OSPF 187
Changing an OSPF Interface Type
When an OSPF interface is enabled, the interface type cannot be changed. The
interface must first be disabled, the type changed, and the interface reenabled.
Additionally, if it is an NBMA interface, the manually configured neighbors must
first be deleted.
To change an OSPF interface, type follow this procedure:
1
From the Device Manager menu bar, select IP Routing > OSPF.
The OSPF dialog box appears with the General tab displayed (Figure 65 on
page 178).
2
If the interface is an NBMA interface, the manually configured neighbors
must first be deleted. To delete the manually configured neighbors, do the
following:
a
Select the Neighbors tab (Figure 69).
Figure 69 Neighbors tab—NBMA manually-configured neighbors
b
Select the neighbors with a value of permanent in the
ospfNbmaNbrPermanence column.
c
Click Delete.
The manually-configured neighbors are deleted.
3
Select the Interfaces tab.
The Interfaces tab appears (Figure 67 on page 183).
4
To disable the interface, select the AdminStat field, and select disabled from
the list.
5
Click Apply.
Configuring IP Routing and Multicast Operations using Device Manager
188 Chapter 8 Configuring OSPF
The interface is disabled.
6
To change the interface type, select the Type field, and select the new interface
type (broadcast, passive, or nbma) from the list.
7
Click Apply.
The interface type is changed.
8
To enable the interface, select the AdminStat field, and choose enabled from
the list.
9
Click Apply.
The interface is enabled as the new type.
Configuring OSPF NBMA Interfaces
In contrast to a broadcast network, where some OSPF protocol packets are
multicast (sent to AllSPFRouters and AllDRouters), NBMA packets are replicated
and sent to each neighboring router as unicast. NBMA networks drop all OSPF
packets with destination addresses AllSPFRouters and AllDRouters. Because the
NBMA network does not broadcast, a list of neighbors and their priorities must be
manually configured for all routers in the network that are eligible to become the
DR (those with a positive, non-zero router priority).
Before you begin this configuration, identify the following:
•
•
•
•
•
•
Specific interfaces to be included in the NBMA network
IP address for each interface
Router priority for each interface
HelloInterval for the network
RtrDeadInterval for the network
PollInterval for the network
After this information has been gathered, the interfaces can be configured and
neighbors added for each interface that is eligible to become the DR (those with a
positive, non-zero router priority).
321712-B Rev 03
Chapter 8 Configuring OSPF 189
This section includes the following topics:
•
•
“Adding NBMA Neighbors” on page 189
“Viewing OSPF Neighbor Information” on page 190
Adding NBMA Neighbors
An NBMA interface that has a positive, non-zero router priority is eligible to
become the DR for the NBMA network and is configured with the identification
of all attached routers, their IP addresses, and their router priorities.
To add neighbors for an OSPF NBMA interface, follow this procedure:
1
From the Device Manager menu bar, select IP Routing > OSPF.
The OSPF dialog box appears with the General tab displayed (Figure 65 on
page 178).
2
Select the Interfaces tab.
The Interfaces tab appears (Figure 67 on page 183).
3
Select an NBMA interface with a positive, non-zero router priority.
4
Select the Neighbors tab.
The Neighbors tab appears (Figure 70).
Figure 70 OSPF dialog box—Neighbors tab
5
Click Insert.
The OSPF, Insert Neighbors dialog box appears (Figure 71).
Configuring IP Routing and Multicast Operations using Device Manager
190 Chapter 8 Configuring OSPF
Figure 71 OSPF, Insert Neighbors dialog box
6
Enter the IP address and priority for the neighbor.
7
Click Insert.
The neighbor is added to the Neighbors tab.
8
Repeat step 6 for all neighbors.
9
Click Apply.
The neighbors are configured for this NBMA interface.
10 To configure neighbors for other NBMA interfaces eligible to become DR
(those with a positive, non-zero router priority), repeat Steps 1-8.
The neighbors are configured for the NBMA network.
Viewing OSPF Neighbor Information
Two routers that have interfaces to a common network are called neighbors and
appear on each other’s Neighbors tab. Neighbor relationships are maintained, and
usually dynamically discovered, by OSPF’s Hello Protocol. The exception is that,
in an NBMA network, permanent neighbors are manually configured on each
router eligible to become the DR.
To view the OSPF neighbors, do the following:
1
From the Device Manager menu bar, select IP Routing > OSPF.
The OSPF dialog box appears with the General tab displayed (Figure 65 on
page 178).
2
Select the Neighbors tab.
The Neighbors tab appears (Figure 70 on page 189).
321712-B Rev 03
Chapter 8 Configuring OSPF 191
Table 36 describes the Neighbors tab fields.
Table 36 Neighbors tab fields
Field
Descriptions
IpAddr
The neighbor IP address.
AddressLessIndex
On an interface having an IP address, zero. On addressless
interfaces, the corresponding value of ifIndex in the Internet
standard MIB. On row creation, this value is derived from
the instance.
Rtrld
The router ID of the neighboring router, which in OSPF has
the same format as an IP address but identifies the router
independent of its IP address.
Options
A bit mask corresponding to the neighbor’s options field.
Priority
Assignment of preferential treatment to place the transmitted
packets in queues and possible selection of the priority field
in the data-link header when the packet is forwarded.
State
The OSPF Interface state.
Events
The number of state changes or error events that have
occurred between the OSPF router and the neighbor router.
LSRetransQLen
The number of elapsed seconds between advertising
retransmissions of the same packet to a neighbor.
ospfNbmaNbrPermanence
Indicates whether the neighbor is a manually-configured
NBMA neighbor.
HelloSuppressed
This variable indicates whether Hellos to a neighbor are
being suppressed.
Managing an OSPF VLAN interface
From the VLAN dialog box, an IP address can be assigned to an OSPF port and
specific OSPF interface configurations can be made. When configuring an
interface for the OSPF protocol, first enable OSPF globally on the router and then
assign an IP address. For instructions about globally enabling OSPF, refer to
“Enabling or Disabling OSPF on a Router” on page 180.
This section includes the following topics:
•
•
“Assigning an IP address to a VLAN Interface” on page 192
“Configuring OSPF on a VLAN interface” on page 193
Configuring IP Routing and Multicast Operations using Device Manager
192 Chapter 8 Configuring OSPF
•
“Graphing OSPF Interface Statistics” on page 193
Assigning an IP address to a VLAN Interface
To assign an IP address to a VLAN interface, follow this procedure:
1
From the Device Manager menu bar, select VLAN > VLANs.
The VLAN dialog box appears with the Basic tab displayed (Figure 72).
Figure 72 VLAN dialog box—Basic tab
2
Select a VLAN by clicking in a column of the desired row.
3
Click IP.
The IP VLAN dialog box appears with the IP Address tab displayed
(Figure 73).
Figure 73 VLAN dialog box—IP Address tab
4
Click Insert.
The VLAN, Insert IP Address dialog box appears (Figure 74).
321712-B Rev 03
Chapter 8 Configuring OSPF 193
Figure 74 VLAN, Insert IP Address dialog box
5
In the IpAddress field, type the interface IP Address.
6
Enter the subnet mask in the Net Mask field or press the Tab key to have one
automatically calculated and inserted.
7
Click Insert.
The IP Address is assigned to the selected VLAN interface.
Configuring OSPF on a VLAN interface
To enable and configure OSPF on a VLAN interface, follow these steps:
1
From the Device Manager menu bar, select VLAN > VLANs.
The VLAN dialog box appears with the Basic tab displayed (Figure 72 on
page 192).
2
Select a VLAN by clicking in a column of the appropriate row.
3
Click IP.
The IP, VLAN dialog box appears with the IP Address tab displayed
(Figure 73 on page 192).
4
Select the OSPF tab.
The OSPF tab appears (Figure 75).
Configuring IP Routing and Multicast Operations using Device Manager
194 Chapter 8 Configuring OSPF
Figure 75 VLAN dialog box—OSPF tab
5
In the IfType area, select the option button that corresponds to the type of
interface to create (broadcast, nbma, or passive).
6
Select the Enable check box.
7
Designate a router priority in the DesigRtrPriority field.
8
Designate values for the HelloInterval, RtrDeadInterval, and PollInterval
fields.
9
Enable authentication for the interface by selecting either the
simplePassword or md5 option buttons in the AuthType area. If
simplePassword is chosen, type a password of up to eight characters in
length in the AuthKey field.
10 Click Apply.
OSPF is configured for the VLAN.
Graphing OSPF Interface Statistics
To graph OSPF statistics on a VLAN interface, perform the following procedure:
321712-B Rev 03
Chapter 8 Configuring OSPF 195
1
Select VLAN > VLANS from the Device Manager menu.
The VLAN dialog box appears with the Basic tab selected.
2
Select a VLAN from those listed on the Basic tab by clicking in a column of
the applicable row.
3
Click IP.
The IP, VLAN dialog box appears with the IP Address tab selected.
4
Select the OSPF tab.
5
Click Graph.
Note: OSPF statistics are not available if OSPF is not enabled on the
switch. Access to these statistics are only available after the Enable
check box on the OSPF tab is selected.
The OSPF Stats Default dialog box appears. This tab is illustrated in
Figure 76.
Configuring IP Routing and Multicast Operations using Device Manager
196 Chapter 8 Configuring OSPF
Figure 76 OSPF Stats Default dialog
Table 37 describes the fields on this dialog.
Table 37 OSPF Stats Default fields
Field
Description
VersionMismatches
Indicate the number of version mismatches received by this
interface.
AreaMismatches
Indicates the number of area mismatches received by this
interface.
AuthTypeMismatches
Indicates the number of AuthType mismatches received by
this interface.
AuthFailures
Indicates the number of Authentication failures.
NetMaskMismatches
Indicates the number of NetMask mismatches received by
this interface.
HelloIntervalMismatches
Indicates the number of HelloInterval mismatches received
by this interface.
321712-B Rev 03
Chapter 8 Configuring OSPF 197
Table 37 OSPF Stats Default fields (continued)
Field
Description
DeadIntervalMismatches
Indicates the number of DeadInterval mismatches received
by this interface.
OptionMismatches
Indicates the number of Option mismatches received by this
interface.
RxHellos
Indicates the number of hello packets received by this
interface.
RxDBDescrs
Indicates the number of database descriptor packets
received by this interface.
RxLSUpdates
Indicates the number of link state update packets received by
this interface.
RxLSReqs
Indicates the number of link state request packets received
by this interface.
RxLSAcks
Indicates the number of link state acknowledge packets
received by this interface.
TxHellos
Indicates the number of hello packets transmitted by this
interface.
TxDBDescrs
Indicates the number of database descriptor packets
transmitted by this interface.
TxLSUpdates
Indicates the number of link state update packets transmitted
by this interface.
TxLSReqs
Indicates the number of link state request packets
transmitted by this interface.
TxLSAcks
Indicates the number of link state acknowledge packets
transmitted by this interface.
Managing OSPF Area Information
With OSPF, collections of contiguous networks and hosts can be grouped
together. Such a group, together with the routers having interfaces to any of the
included networks, is called an area. Each area runs a separate copy of the basic
link-state routing algorithm. This means that each area has its own link-state
database.
This section includes the following topics:
•
“Viewing OSPF Area Information” on page 199
Configuring IP Routing and Multicast Operations using Device Manager
198 Chapter 8 Configuring OSPF
•
321712-B Rev 03
“Creating a Stub Area or NSSAs” on page 200
Chapter 8 Configuring OSPF 199
Viewing OSPF Area Information
To view information about OSPF areas, follow this procedure:
1
From the Device Manager menu bar, select IP Routing > OSPF.
The OSPF dialog box appears with the General tab displayed (Figure 65 on
page 178).
2
Select the Areas tab
The Areas tab appears (Figure 77).
Notice that the backbone ID is always displayed as 0.0.0.0.
Figure 77 OSPF dialog box—Areas tab
Table 38 describes the Areas tab fields.
Table 38 Areas tab fields
Field
Description
AreaId
A 32-bit integer uniquely identifying an area. Area ID 0.0.0.0 is
used for the OSPF backbone.
For VLANs, keeping the default area setting on the interface
causes the LSDB to be inconsistent.
ImportAsExtern
The area’s support for importing AS external link state
advertisements. Can be importExternal (default),
importNotExternal, or importNssa (not-so-stubby area).
SpfRuns
Used to indicate the number of SPF calculations performed by
OSPF.
AreaBdrRtrCount
The total number of area border routers reachable within this
area. The value, initially zero, is calculated in each SPF Pass.
Configuring IP Routing and Multicast Operations using Device Manager
200 Chapter 8 Configuring OSPF
Table 38 Areas tab fields (continued)
Field
Description
AsBdrRtrCount
The total number of autonomous system border routers reachable
within this area. The value, initially zero, is calculated in each SPF
Pass.
AreaLsaCount
The total number of link state advertisements in this area’s link
state database, excluding AS External LSAs.
AreaLsaCksumSum
The 32-bit unsigned sum of the link state advertisements. This
sum excludes external (LS type 5) link state advertisements. The
sum is used to determine if there has been a change in a router’s
link state database and to compare the link state database of two
routers.
AreaSummary
The area's support for summary advertisements in a stub area.
In instances where summary advertisements into the stub area
are enabled, the OSPF administrative status must also be toggled
to complete the task.
ActiveifCount
The number of active interfaces in this area.
Creating a Stub Area or NSSAs
A stub area does not receive advertisements for external routes, which reduces
the size of the link state database. A stub area has only one area border router.
Any packets destined outside the area are simply routed to that area border exit
point, examined by the area border router, and forwarded to a destination.
A not-so-stubby area (NSSA) also prevents the flooding of AS-External Link
State advertisements into the area by replacing them with a default route. The
added feature of NSSAs is the ability to import small stub (non-OSPF) routing
domains into OSPF.
To create a stub area or NSSA, follow this procedure:
1
From the Device Manager menu bar, select IP Routing > OSPF.
The OSPF dialog box appears with the General tab displayed (Figure 65 on
page 178).
2
Select the Areas tab.
The Areas tab appears (Figure 77 on page 199).
321712-B Rev 03
Chapter 8 Configuring OSPF 201
3
Click in the ImportAsExtern field and use the list to select either
importExternal, ImportNoExternal, or importNssa.
4
Click Apply.
Table 38 on page 199 describes the Areas tab fields.
Creating a Virtual Link
When using OSPF with the Ethernet Routing Switch 1600 Series, the router needs
to be connected directly to the backbone. If the router is not directly connected, a
virtual link must be created, either manually or automatically.
When automatic virtual linking is enabled, it acts as insurance. A virtual link is
created for vital traffic paths in the OSPF configuration if something goes wrong,
such as when an interface cable providing connection to the backbone (either
directly or indirectly) becomes disconnected from the switch. Specifying
automatic virtual linking ensures that a link is created via another switch. When
automatic virtual linking is enabled, it is always ready to create a virtual link. If
automatic virtual linking uses more network resources than is desired, creating a
manual virtual link may be the better solution. This approach conserves resources
while having specific control of where virtual links are placed in the OSPF
configuration.
OSPF behavior has been modified according to OSPF standards so that OSPF
routes cannot be learned through an area border router (ABR) unless it is
connected to the backbone or through a virtual link.
This section includes the following topics:
•
•
•
•
“Managing an Automatic Virtual Link” on page 201
“Configuring a Manual Virtual Link” on page 202
“Viewing Virtual Links on Neighboring Devices” on page 204
“Configuring Router Hosts” on page 205
Managing an Automatic Virtual Link
To specify that virtual links be created automatically, follow this procedure:
Configuring IP Routing and Multicast Operations using Device Manager
202 Chapter 8 Configuring OSPF
1
Select IP Routing > OSPF from the Device Manager menu bar.
The OSPF dialog box appears with the General tab displayed (Figure 65 on
page 178).
2
Select the AutoVirtLinkEnable check box.
By default, this feature is set to false, and virtual links are not created
automatically.
3
Click Apply.
Configuring a Manual Virtual Link
To manually configure a virtual link, follow this procedure:
1
From the Device Manager menu bar, select IP Routing > OSPF.
The OSPF dialog box appears with the General tab displayed (Figure 65 on
page 178).
2
Select the Virtual If tab.
The Virtual If tab appears (Figure 78).
Figure 78 OSPF dialog box—Virtual If tab
3
Click Insert.
The OSPF, Insert Virtual If dialog box appears (Figure 79).
321712-B Rev 03
Chapter 8 Configuring OSPF 203
Figure 79 OSPF, Insert Virtual If dialog box
4
Specify the area identification of the transit area in the AreaID field.
The transit area is the common area between two ABRs.
5
Specify the neighbor identification in the Neighbor field.
The neighbor identification is the IP router identification of the ABR that the
other ABR needs to go through to get to the backbone.
6
Specify the other field values as appropriate for the virtual link.
7
Click Insert.
To verify that the virtual link is active, refresh the Virtual If tab and check the
State field. If the State field displays point to point, the virtual link is active. If the
State column displays down, the virtual link is configured incorrectly.
Table 40 describes the Virtual If tab fields.
Table 39 OSPF dialog box—Virtual If tab fields
Field
Description
AreaId
The Transit Area Id that the virtual link traverses.
Neighbor
The router ID of the virtual neighbor.
TransitDelay
The estimated number of seconds it takes to transmit a link- state
update packet over this interface.
Configuring IP Routing and Multicast Operations using Device Manager
204 Chapter 8 Configuring OSPF
Table 39 OSPF dialog box—Virtual If tab fields (continued)
Field
Description
Retrans Interval
The number of seconds between link-state advertisements and
retransmissions for adjacencies belonging to this interface. This
value is also used when retransmitting database descriptions and
link-state request packets. Set this value to be well over the expected
round- trip time.
HelloInterval
The length of time, in seconds, between the Hello packets that the
router sends on the interface. This value must be the same for the
virtual neighbor.
RtrDeadInterval
The length of time, in seconds, that must elapse following receipt of
the last Hello packet from this router before a neighbor can declare
this router down. Set this value to some multiple of the Hello interval.
This value must be the same for the virtual neighbor.
State
The OSPF virtual interface states.
Events
The number of state changes or error events on this Virtual Link.
AuthType
The authentication type specified for a virtual interface. Additional
authentication types may be assigned locally.
AuthKey
If Authentication Type is a simple password, the device will left adjust
and zero fill to 8 octets.
Note that unauthenticated interfaces need no authentication key and
simple password authentication cannot use a key of more than 8
octets.
Viewing Virtual Links on Neighboring Devices
Use the Virtual Neighbors tab to view the area and virtual link configuration for
neighboring devices.
To view the virtual neighbor, follow this procedure:
1
From the Device Manager menu bar, select IP Routing > OSPF.
The OSPF dialog box appears with the General tab displayed (Figure 65 on
page 178).
2
Select the Virtual Neighbors tab.
The Virtual Neighbors tab appears (Figure 80).
321712-B Rev 03
Chapter 8 Configuring OSPF 205
Figure 80 OSPF dialog box—Virtual Neighbor tab
Table 40 describes the Virtual Neighbors tab fields.
Table 40 OSPF dialog box—Virtual Neighbor tab fields
Field
Description
Area
The subnetwork in which the virtual neighbor resides.
RtrId
A 32-bit integer (represented as a type IpAddress) uniquely
identifying the neighboring router in the autonomous system.
IpAddr
The IP address of the virtual neighboring router.
Options
A bit mask corresponding to the neighbor’s options field.
State
The OSPF interface state.
Events
The number of state changes or error events that have occurred
between the OSPF router and the neighbor router.
LsRetransQLen
The number of elapsed seconds between advertising
retransmissions of the same packet to a neighbor.
HelloSuppressed
This field indicates whether or not Hellos are being suppressed to the
neighbor.
Configuring Router Hosts
It is possible to specify which hosts are directly attached to the router and the
metrics and types of service that can be advertised for them.
To configure router hosts, follow this procedure:
1
From the Device Manager menu bar, select IP Routing > OSPF.
Configuring IP Routing and Multicast Operations using Device Manager
206 Chapter 8 Configuring OSPF
The OSPF dialog box appears with the General tab displayed (Figure 65 on
page 178).
2
Select the Hosts tab.
The Hosts tab appears (Figure 81).
Figure 81 OSPF dialog box—Hosts tab
3
Click Insert.
The Insert Hosts dialog box appears (Figure 82).
Figure 82 OSPF, Insert Hosts dialog box
4
Enter an IP address for the host in the IpAddress field and a metric for the
host in the Metric field.
5
Click Insert.
The Hosts tab is updated with the new host entry.
321712-B Rev 03
Chapter 8 Configuring OSPF 207
Table 41 describes the Hosts tab fields.
Table 41 Host tab fields
Field
Description
IpAddress
The IP address of the host used to represent a point of
attachment in a TCP/IP internetwork.
TOS
The type of service of the route being configured.
Metric
The metric advertised to other areas. The value indicates
the distance from the OSPF router to any network in the
range.
AreaID
Area where the host is found. By default, the area that is
submitting the OSPF interface is in 0.0.0.0.
Specifying ASBRs
ASBRs advertise non-OSPF routes into OSPF domains so that they can be passed
along throughout the OSPF routing domain. A router can function as an ASBR if
one or more of its interfaces is connected to a non-OSPF network (for example,
RIP, or EGP).
To conserve resources, it may be advisable to limit the number of ASBRs in the
network or to specifically control which routers perform as ASBRs to control
traffic flow.
To specify a router ASBR function, follow this procedure:
1
From the Device Manager menu bar, select IP Routing > OSPF.
The OSPF dialog box appears with the General tab displayed (Figure 65 on
page 178).
2
Select the ASBdrRtrStatus check box to designate the router as an ASBR or
deselect it to remove that status.
3
Click Apply.
Configuring IP Routing and Multicast Operations using Device Manager
208 Chapter 8 Configuring OSPF
Configuring Metric Speed
The metric speed can be configured globally or for specific ports and interfaces
on the network. In addition, redistribution options between non-OSPF interfaces
and OSPF interfaces can be configured.
This section includes the following topics:
•
•
“Configuring Global Default Metric Speed” on page 208
“Managing Metrics with the Peer Layer Interface” on page 208
Configuring Global Default Metric Speed
To change the default metric speed on specific port types:
1
Select IP Routing > OSPF from the Device Manager menu bar.
The OSPF dialog box appears with the General tab displayed (Figure 65 on
page 178).
2
Change the metric value in one or all of the following fields:
•
•
•
•
3
10MbpsPortDefaultMetric (default = 100)
100MbpsPortDefaultMetric (default = 10)
1000MbpsPortDefaultMetric (default = 1)
10000MbpsPortDefaultMetric (default = 1)
Click Apply.
Managing Metrics with the Peer Layer Interface
The If Metrics tab indicates the metrics associated with the peer layer interface.
To specify the metric speed, follow this procedure:
1
From the Device Manager menu bar, select IP Routing > OSPF.
The OSPF dialog box appears with the General tab displayed (Figure 65 on
page 178).
2
321712-B Rev 03
Select the If Metrics tab.
Chapter 8 Configuring OSPF 209
The If Metrics tab appears (Figure 83).
Figure 83 OSPF dialog box—If Metrics tab
3
Specify a new metric speed in the Value field.
4
Click Apply.
Table 42 describes the If Metrics tab fields.
Table 42 If Metrics tab fields
Field
Description
IpAddress
The Internet Protocol address of the device used to represent a
point of attachment in a TCP/IP internetwork.
AddressLessIf
For the purpose of easing the instancing of addressed and
addressless interfaces. This variable takes the value 0 on interfaces
with IP addresses and the corresponding value of ifIndex for
interfaces having no IP address.
TOS
Type of service is a mapping to the IP type of service flags, as
defined in the IP forwarding table MIB.
Value
The value advertised to other areas indicating the distance from the
OSPF router to any network in the range.
Status
Active or not active. Not configurable.
Configuring IP Routing and Multicast Operations using Device Manager
210 Chapter 8 Configuring OSPF
Viewing Stub Area Metrics
The Stub Area Metrics tab contains the set of metrics that are advertised by a
default area border router into a stub area.
To view the set of stub area metrics, follow this procedure:
1
From the Device Manager menu bar, select IP Routing > OSPF.
The OSPF dialog box appears with the General tab displayed (Figure 65 on
page 178).
2
Select the Stub Area Metrics tab.
The Stub Area Metrics tab appears (Figure 84).
Figure 84 OSPF dialog box—Stub Area Metrics tab
Table 43 describes the Stub Area Metrics tab fields.
Table 43 Stub Area Metrics tab fields
Field
Description
AreaID
The 32-bit identifier for the stub area. On creation, it can be
derived from the instance.
TOS
The type of service associated with the metric. On creation,
it can be derived from the instance.
Metric
The metric value applied at the indicated type of service.
By default, it equals the lowest metric value at the type of
service among the interfaces to other areas.
Status
Active or not active. Not configurable.
321712-B Rev 03
Chapter 8 Configuring OSPF 211
Viewing Advertisements in the link state database
To view the advertisements of the areas throughout the link state database, follow
this procedure:
1
From the Device Manager menu bar, select IP Routing > OSPF.
The OSPF dialog box appears with the General tab displayed (Figure 65 on
page 178).
2
Select the Link State Database tab.
The Link State Database tab appears (Figure 85).
Figure 85 OSPF dialog box—Link State Database tab
Table 44 describes the Link State Database tab fields.
Table 44 Link State Database tab fields
Field
Description
AreaId
A 32-bit integer uniquely identifying an area. Area ID 0.0.0.0 is
used for the OSPF backbone.
Type
Displays the type of link advertisement by which the current link
was discovered by the switch:
• Router link (RTRLink)
• Network link (NETLink)
• Summary link (Summary)
• Autonomous System link (ASSummary)
Lsid
The Link State ID is an LS type-specific field containing either a
router ID or an IP address. It identifies the piece of the routing
domain that is being described by the advertisement.
Configuring IP Routing and Multicast Operations using Device Manager
212 Chapter 8 Configuring OSPF
Table 44 Link State Database tab fields (continued)
Field
Description
RouterId
A 32-bit integer uniquely identifying the router in the autonomous
system.
Sequence
The sequence number is a signed 32-bit integer that identifies old
and duplicate link state advertisements.
Age
The age, in seconds, of the link state advertisement.
Checksum
This field is the checksum of the complete contents of the
advertisement, excepting the age field. The age field is excepted
so that an advertisement’s age can be incremented without
updating the checksum. The checksum used is the same that is
used for ISO connectionless datagrams. It is commonly referred to
as the Fletcher checksum.
Viewing the External Link State Database
To view the characteristics of the external link state database, follow this
procedure:
1
From the Device Manager menu bar, select IP Routing > OSPF.
The OSPF dialog box appears with the General tab displayed (Figure 65 on
page 178).
2
Select the Ext. Link State Database tab.
The Ext. Link State Database tab appears (Figure 86).
Figure 86 OSPF dialog box—Ext. Link State DB tab
321712-B Rev 03
Chapter 8 Configuring OSPF 213
Table 45 describes the Ext. Link State Database tab fields.
Table 45 Ext. Link State DB tab fields
Field
Description
Type
Displays the type of link advertisements by which the current link
was discovered by the switch:
• AS External Route (asExternalLink)
Lsid
The Link State ID is an LS type-specific field containing either a
router ID or an IP address. It identifies the piece of the routing
domain that is being described by the advertisement.
RouterId
A 32-bit integer uniquely identifying the router in the
autonomous system.
Sequence
The sequence number is a signed 32-bit integer that identifies
old and duplicate link state advertisements.
Age
The age in seconds of the link state advertisement.
Checksum
This field is the checksum of the complete contents of
the advertisement, excepting the age field. The age field
is excepted so that an advertisement’s age can be incremented
without updating the checksum. The checksum used is the same
that is used for ISO connectionless datagrams. It is commonly
referred to as the Fletcher checksum.
Advertisement
Hex representation of the entire link state advertisement,
including the header.
Inserting OSPF Area Aggregate Ranges
To insert OSPF area aggregate ranges, perform the following procedure:
1
From the Device Manager menu bar, select IP Routing > OSPF.
The OSPF dialog box appears with the General tab displayed (Figure 65 on
page 178).
2
Select the Area Aggregate tab.
The Area Aggregate tab appears (Figure 87).
Configuring IP Routing and Multicast Operations using Device Manager
214 Chapter 8 Configuring OSPF
Figure 87 OSPF dialog box—Area Aggregate tab
3
Click Insert.
The OSPF, Insert Area Aggregate dialog box appears (Figure 88).
Figure 88 OSPF, Insert Area Aggregate dialog box
4
Enter the area identification in the AreaID field.
5
Select either the summaryLink or nssaExternalLink option buttons in the
LsdbType area to determine the link state database type.
6
Select either the advertiseMatching, doNotAdvertiseMatching, or
advertiseDoNotAggregate option buttons in the Effect area.
7
In the AdvertiseMetric field, enter a cost value to advertise for the OSPF area
range.
8
Click Insert.
321712-B Rev 03
Chapter 8 Configuring OSPF 215
Table 46 describes the Area Aggregate tab fields.
Table 46 Area Aggregate tab fields
Field
Description
AreaID
The area in which the address is found.
LsdbType
One of the following:
• summaryLink— aggregated summary link
• nssaExternalLink —not-so-stubby area link
IP Address
The IP Address of the Net or Subnet indicated by the range.
Mask
Network mask for the area range.
Effect
One of the following:
• advertiseMatching—advertise the aggregate summary
LSA with same LSID.
• doNotAdvertiseMatching—suppress all networks that fall
within the entire range.
• advertiseDoNotAggregate—advertise individual networks.
AdvertiseMetric
Changes the advertised metric cost value of the OSPF area
range.
Enter an integer value in the range 0 and 65 535, which
represents the metric cost value for the OSPF area range.
Configuring IP Routing and Multicast Operations using Device Manager
216 Chapter 8 Configuring OSPF
Configuring an OSPF Redistribution Policy
A redistribute entry for OSPF can be configured to announce routes of a certain
source type, for example, static, RIP, or direct. If a route policy field is not
configured for a redistribute entry, then the default action is taken on the basis of
metric, metric-type, and subnet configured. This is called basic redistribution.
Otherwise, use the route policy specified to perform detailed redistribution. If no
redistribution entry is configured, no external LSA is generated for non-OSPF
routes.
Note: Changing OSPF Redistribute contexts is a process-oriented
operation that can affect system performance and network reachability
while performing the procedures. Therefore, Nortel recommends that if
the default preferences are to be changed for an OSPF Redistribute
context, do so before enabling the protocols.
OSPF redistribution policies can be configured in two locations in the Device
Manager:
1
IP Routing > OSPF > Redistribute tab
2
IP Routing > Policy > OSPF Redistribute tab
Although the following procedure details using the IP Routing > OSPF >
Redistribute tab, the steps are the same in the IP Routing > Policy > OSPF
Redistribute tab.
To set up or edit an OSPF redistribute policy, perform the following tasks:
1
From the Device Manager menu bar, select IP Routing > OSPF.
The OSPF dialog box appears with the General tab displayed (Figure 65 on
page 178).
2
Select the Redistribute tab.
The Redistribute tab appears (Figure 89).
321712-B Rev 03
Chapter 8 Configuring OSPF 217
Figure 89 Policy dialog box—Redistribute tab
3
Click Insert.
The Policy, Insert OSPF Redistribute dialog box appears (Figure 90).
Figure 90 Policy, Insert OSPF Redistribute dialog box
4
Edit the fields provided.
5
Click Insert.
Configuring IP Routing and Multicast Operations using Device Manager
218 Chapter 8 Configuring OSPF
Table 47 describes the Policy, Insert OSPF Redistribute dialog box fields.
Table 47 Policy, Insert OSPF Redistribute dialog box fields
Field
Description
RouteSource
Select the route source protocol for the redistribution entry.
Enable
Enables (or disables) an OSPF redistribute entry for a specified
source type.
You can also enable or disable this feature in the OSPF Redistribute
tab of the Policy dialog box by clicking in the field and selecting
enable or disable from the menu.
Metric
Set the OSPF route redistribution metric for basic redistribution. The
value can be a range between 0 to 65 535. If configured as 0, the
original cost of the route is used.
MetricType
Set the OSPF route redistribution metric type. The default is Type 2.
You can also select your entry in the OSPF Redistribution tab of the
Policy dialog box by clicking in the field and selecting any, type1, or
type2 from the pulldown menu.
Subnets
Allows or suppresses external subnet routes while being
redistributed into an OSPF domain.
You can also select your entry in the OSPF Distribution tab of the
Policy dialog box by clicking in the field and selecting allow or deny
from the menu.
RoutePolicy
Sets the route policy by name to be used for the detailed
redistribution of external routes from a specified source into an OSPF
domain.
Click the ellipse button and choose from the list in the Route Policy
dialog box (Figure 90 on page 217). To deselect an entry, use the
ALT key.
321712-B Rev 03
219
Chapter 9
Configuring UDP Forwarding
UDP forwarding is a feature that selectively forwards UDP broadcasts received on
an IP interface to either router IP interfaces (as a rebroadcast) or to a configured IP
address.
Generally speaking, the following steps must be performed to enable UDP
forwarding on an Ethernet Routing Switch 1600 Series:
1
Create UDP protocol entries for each port receiving UDP broadcasts.
2
Create UDP forwarding entries for each protocol by specifying a destination
IP address.
3
Create a UDP forwarding policy, by specifying one or more UDP forwarding
entries.
4
Apply the UDP forwarding policy to a local interface.
For conceptual information about UDP forwarding, refer to “IP routing and
multicast concepts” on page 29.
This section covers the following topics:
•
•
•
•
“Creating UDP Protocol Entries” on page 219
“Configuring Forwarding Entries” on page 221
“Creating UDP Forwarding Policies” on page 223
“Applying UDP Forwarding Policies” on page 225
Creating UDP Protocol Entries
Only ports that have configured UDP protocol entries are eligible for UDP
forwarding. To create UDP protocol entries, follow this procedure:
Configuring IP Routing and Multicast Operations using Device Manager
220 Chapter 9 Configuring UDP Forwarding
1
Select IP Routing > UDP Forwarding from the Device Manager menu bar.
The UdpForwarding dialog box appears with the Protocols tab displayed
(Figure 91).
Figure 91 UdpForwarding dialog box—Protocols tab
2
Click Insert.
The UdpForwarding, Insert Protocols dialog box appears (Figure 92).
Figure 92 UdpForwarding, Insert Protocol dialog box
3
Enter the applicable port in the PortNumber field.
4
Type a name that describes the port function in the Name field.
A unique name must be provided when creating a protocol, and this name
cannot be modified later. To change the name of a UDP protocol, delete the
protocol entry and then recreate it with the new name.
5
321712-B Rev 03
Click Insert.
Chapter 9 Configuring UDP Forwarding 221
Table 48 describes the UdpForwarding dialog box—Protocols tab fields.
Table 48 UdpForwarding dialog box—Protocols tab fields
Field
Description
PortNumber
The port number for the protocol. The range is 1 to 65 535.
Name
A descriptive name for the protocol.
Configuring Forwarding Entries
After you specify a UDP protocol entry, create a forwarding entry to specify the
destination IP address for UDP broadcasts. The system automatically assigns a
unique ID number for each forwarding entry.
To configure forwarding entries, follow this procedure:
1
Select IP Routing > UDP Forwarding from the Device Manager menu bar.
The UdpForwarding dialog box appears with the Protocols tab displayed
(see Figure 91 on page 220).
2
Select the Forwardings tab.
The Forwardings tab appears (Figure 93).
Figure 93 UdpForwarding dialog box—Forwardings tab
3
Click Insert.
The UdpForwarding, Insert Forwardings dialog box appears (Figure 94).
Configuring IP Routing and Multicast Operations using Device Manager
222 Chapter 9 Configuring UDP Forwarding
Figure 94 UdpForwarding, Insert Forwardings dialog box
4
Select the applicable entry in the DestPort field.
5
Enter the destination IP address in the DestAddr field.
6
Click Insert.
Table 49 describes the UdpForwarding dialog box—Forwardings tab fields.
Table 49 UdpForwarding dialog box—Forwardings tab fields
Field
Description
DestPort
The original destination port number. UDP broadcast packets sent to
this port number are automatically forwarded to a new destination IP
address.
The destination port number must exist as a protocol before the
forwarding entry is created.
DestAddr
The forwarding destination IP address for UDP broadcasts.
The IP address is any IP server address or subnet broadcast address.
The process used to forward a UDP broadcast depends on the type of
IP address used.
• If the IP address is a routable interface address on the router, then
the frame is rebroadcast as a limited broadcast.
• If the IP address is a server, then the received broadcast packet is
sent as a unicast packet to this address.
• If the IP address is a subnet broadcast address, then the received
broadcast packet is routed as a subnet broadcast packet.
Id
The unique identification number assigned to each UDP forwarding
entry. The system automatically assigns this number.
NumFwd
Packets
The number of UDP broadcast packets forwarded using this
forwarding entry. This is a read-only parameter.
321712-B Rev 03
Chapter 9 Configuring UDP Forwarding 223
Table 49 UdpForwarding dialog box—Forwardings tab fields (continued)
Field
Description
NumDrop
Packets
TtlExpired
The number of UDP broadcast packets dropped because the TTL
expired. This is a read-only parameter.
NumDrop
Packets
DestUnreach
The number of UDP broadcast packets dropped because the
forwarding IP address specified in the forwarding entry was
unreachable. This is a read-only parameter.
Creating UDP Forwarding Policies
UDP forwarding policies are lists of forwarding entries that are applied to an
interface.
To configure UDP forwarding policies, do the following:
1
Select IP Routing > UDP Forwarding from the Device Manager menu bar.
The UdpForwarding dialog box appears with the Protocols tab displayed
(see Figure 91 on page 220).
2
Select the Forwarding Lists tab.
The Forwarding Lists tab appears (Figure 95).
Figure 95 UdpForwarding dialog box—Forwarding Lists tab
3
Click Insert.
The UdpForwarding, Insert Forwarding Lists dialog box appears
(Figure 96).
Configuring IP Routing and Multicast Operations using Device Manager
224 Chapter 9 Configuring UDP Forwarding
Figure 96 UdpForwarding, Insert Forwarding Lists dialog box
4
Enter a unique number for the UDP forwarding policy in the Id field.
5
Enter a unique name for the UDP forwarding policy in the Name field.
6
List the UDP forwarding entries to include in this list in the FwdIdList field.
There are two ways to add multiple forwarding entries in this policy.
•
•
7
Manually enter multiple forwarding entries by typing each unique ID
separated by commas.
Automatically enter multiple forwarding entries by clicking the ellipse
(...) button to select IDs from a list of existing forwarding entries.
Click Insert.
Table 50 describes the UdpForwarding dialog box—Forwarding Lists tab
fields.
Table 50 UdpForwarding dialog box—Forwarding Lists tab fields
Field
Description
Id
A unique identifier for the UDP forwarding policy. The range is 1 to
1 000.
Name
Identifies the UDP forwarding policy in the table.
FwdIdList
A list of one or more UDP forwarding entry IDs on this list, separated
by commas.
321712-B Rev 03
Chapter 9 Configuring UDP Forwarding 225
Applying UDP Forwarding Policies
To apply UDP forwarding policies to an interface, follow this procedure:
1
Select IP Routing > UDP Forwarding from the Device Manager menu bar.
The UdpForwarding dialog box appears with the Protocols tab displayed
(see Figure 91 on page 220).
2
Select the Broadcast Interfaces tab.
The Broadcast Interfaces tab appears (Figure 97).
Figure 97 UdpForwarding dialog box—Broadcast Interfaces tab
3
Click Insert.
The UdpForwarding, Insert Broadcast Interfaces dialog box appears
(Figure 98).
Figure 98 UdpForwarding, Insert Broadcast Interfaces dialog box
4
Enter the IP address of a local interface in the LocalIfAddr field.
Click the Addr button to select from a list of all existing local interfaces.
Configuring IP Routing and Multicast Operations using Device Manager
226 Chapter 9 Configuring UDP Forwarding
5
Enter the ID of an existing forwarding list to use in the UdpPortFwdListId
field.
Click the IdList button to select from a list of all existing forwarding lists.
6
Enter the maximum TTL value for UDP broadcasts on this interface in the
MaxTtl field.
7
Enter the IP address to use as a broadcast mask for this interface in the
BroadCastMask field.
8
Click Insert.
Table 51 describes the UdpForwarding dialog box—Broadcast Interfaces tab
fields.
Table 51 UdpForwarding dialog box—Broadcast Interfaces tab fields
Field
Description
LocalIfAddr
The IP address of the local interface that can receive UDP/TCP
broadcast packets. This IP address must be a routable interface IP
address.
UdpPortFwd
ListId
The UDP forwarding policy ID applied to the local interface. A UDP
forwarding policy can be used by any number of interfaces. The range
is 1 to 100.
MaxTtl
The maximum TTL value for a forwarded broadcast packet.
This value restricts the number of routers a forwarded broadcast can
traverse before it expires. The acceptable range is 1 to 16. The default
is 4.
NumRxPkts
Number of UDP/TCP broadcasts received.
NumFwdPkts
Number of UDP/TCP broadcasts forwarded.
NumDropPkts
MaxTtlExpired
Number of UDP/TCP broadcasts dropped because the TTL value
expired.
NumDropPkts
DestUnreach
Number of UDP/TCP broadcasts dropped because the destination IP
address was unreachable.
NumDropPkts
UnknownPort
Number of UDP/TCP broadcasts dropped due to unknown UDP
protocol.
BroadCast
Mask
The IP address used for a broadcast mask for this interface.
321712-B Rev 03
227
Chapter 10
Configuring IGMP
Internet Group Management Protocol (IGMP) is used by hosts to report their
multicast group memberships to neighbor multicast routers.
For more information about IGMP concepts and terminology, refer to “IP routing
and multicast concepts” on page 29.
This section includes the following topics:
•
•
•
•
•
•
•
•
•
•
•
“Configuring IGMP on a VLAN” on page 227
“IGMP Snooping on a VLAN” on page 230
“Global IGMP Configuration” on page 231
“Viewing IGMP Cache Information” on page 231
“IGMP Interface Table” on page 233
“Multicast Router” on page 236
“Viewing IGMP Snoop Information” on page 238
“Viewing IGMP Dynamic Group Information” on page 240
“IGMP Static Information” on page 241
“Multicast Access Control Configuration” on page 243
“Viewing IGMP Sender Entries” on page 245
Configuring IGMP on a VLAN
To configure IGMP on a VLAN, follow this procedure:
1
From the Device Manager menu bar, select VLAN > VLANs.
The VLAN dialog box appears with the Basic tab displayed (see Figure 22 on
page 93).
Configuring IP Routing and Multicast Operations using Device Manager
228 Chapter 10 Configuring IGMP
2
Select a VLAN by clicking in a column of the desired row.
3
Click IP.
The IP, VLAN dialog box appears with the IP Address tab displayed (see
Figure 23 on page 93).
4
Select the IGMP tab.
The IGMP tab appears (Figure 99).
Figure 99 IP, VLAN dialog box—IGMP tab
5
Using the fields provided, set the desired IGMP parameters.
6
Click Apply.
321712-B Rev 03
Chapter 10 Configuring IGMP 229
Table 52 describes the fields in the IGMP tab.
Table 52 IGMP tab fields
Field
Description
QueryInterval
The frequency (in seconds) at which IGMP host query
packets are transmitted on the interface. The range is from
1 to 65 535, and the default is 125.
QueryMaxResponseTime
The maximum response time (in 1/10 seconds) advertised
in IGMPv2 general queries on this interface. This field is a
read-only field and is not configurable in the Ethernet
Routing Switch 1600 Series.
Robustness
This parameter allows tuning for the expected packet loss
of a network. This value is equal to the number of expected
query packet losses per serial query interval, plus 1. If a
network is expected to lose query packets, increase the
robustness value.
The range is from 2 to 255, and the default is 2. The default
value of 2 means that one query per query interval may be
dropped without the querier aging out.
SnoopEnable
Enables snoop.
ProxySnoopEnable
Enables proxy snoop.
Version
The version of IGMP (1 or 2) that you want to configure on
this interface. For IGMP to function correctly, all routers on
a LAN must use the same version. The default is version 2.
FastLeaveEnable
Enables fast leave on the interface.
FastLeavePortMembers
The set of ports that are enabled for fast leave.
SnoopMRouterPorts
The set of ports in this interface that statically configures
non-query IGMP router ports. You do not have to configure
this parameter if there is only one multicast router on that
interface (VLAN).
Note: The values for the IGMP parameters, QueryInterval, Robustness, and Version,
must be the same as those configured on the interface (VLAN) of the multicast router.
Configuring IP Routing and Multicast Operations using Device Manager
230 Chapter 10 Configuring IGMP
IGMP Snooping on a VLAN
The Ethernet Routing Switch 1600 Series can provide IP multicast capability as a
Layer 2 switch. Functioning as a Layer 2 switch, it supports IGMPv1 and
IGMPv2 to prune group membership per port within a VLAN. This feature is
called IGMP snoop and it provides optimization of the multicast data flow for a
group within a VLAN to only those ports that are members of the group.
The switch builds a database of group members by listening to IGMP reports from
each port. It suppresses the reports heard by not forwarding them out to ports
other than the one receiving the report, forcing the members to continuously send
their own reports. The switch relays group membership from the hosts to the
multicast routers. It forwards queries from multicast routers to all port members of
the VLAN. Furthermore, it forwards multicast data only to the participating group
members and to the multicast routers within the VLAN.
Enabling IGMP Snooping
To enable IGMP snooping, do the following:
1
From the Device Manager menu bar, select VLAN > VLANs.
The VLAN dialog box appears with the Basic tab displayed (see Figure 22 on
page 93).
2
Select a VLAN by clicking in a column of the desired row.
3
Click IP.
The IP, VLAN dialog box appears with the IP Address tab displayed (see
Figure 23 on page 93).
4
Select the IGMP tab.
The IGMP tab appears (see Figure 99 on page 228).
5
Select the SnoopEnable check box.
6
Select the ProxySnoopEnable check box.
7
Click Apply.
321712-B Rev 03
Chapter 10 Configuring IGMP 231
Global IGMP Configuration
The Global tab is used to access global IGMP configuration parameters. To
configure these parameters, perform the following:
1
Select IP Routing > IGMP from the Device Manager menu.
The IGMP dialog box appears with the Global tab displayed (Figure 100).
Figure 100 IGMP dialog box—Global tab
2
Enable or disable the generation of IGMP traps by selecting either the enable
or disable check box in the GenerateTrap area.
3
Click Apply.
Viewing IGMP Cache Information
To view IGMP cache information, do the following:
1
Select IP Routing > IGMP from the Device Manager menu.
The IGMP dialog box appears with the Globals tab displayed (Figure 101).
Configuring IP Routing and Multicast Operations using Device Manager
232 Chapter 10 Configuring IGMP
Figure 101 IGMP dialog box—Global tab
2
Select the Cache tab.
The Cache tab appears (Figure 102).
321712-B Rev 03
Chapter 10 Configuring IGMP 233
Figure 102 IGMP dialog box—Cache tab
Table 53 describes the Cache tab fields.
Table 53 Cache tab fields
Field
Description
Address
The IP multicast group address for which this entry contains
information.
IfIndex
The interface from which the corresponding multicast group address is
heard.
LastReporter
The IP address of the source of the last membership report received for
this IP multicast group address on this interface. If no membership
report has been received, the object has the value 0.0.0.0.
ExpiryTime
The amount of time (in seconds) remaining before this entry is aged
out.
Version1Host
Timer
The time remaining until the local router assumes that there are no
longer any IGMP version 1 members on the IP subnet attached to the
interface. Upon hearing any IGMPv1 membership report, this value is
reset to the group membership timer. When the time remaining is
nonzero, the local router ignores any IGMPv2 leave messages for this
group that it receives on this interface.
IGMP Interface Table
Use the Interface tab to view or edit the IGMP interface table. When a particular
interface does not have an IP address, that interface entry does not appear in the
IGMP table.
To view or edit the IGMP interface table, do the following:
Configuring IP Routing and Multicast Operations using Device Manager
234 Chapter 10 Configuring IGMP
1
From the Device Manager menu bar, choose IP Routing > IGMP.
The IGMP dialog box appears with the Globals tab displayed (see Figure 101
on page 232).
2
Select the Interface tab.
The Interface tab appears (Figure 103). The Interface tab has a large number
of fields on it. Use the scroll bar located above the dialog buttons to view all
fields.
Figure 103 IGMP dialog box—Interface tab
321712-B Rev 03
Chapter 10 Configuring IGMP 235
Table 54 describes the Interface tab fields.
Table 54 IGMP dialog box—Interface tab fields
Field
Description
IfIndex
The interface on which IGMP is enabled.
QueryInterval
The frequency (in seconds) at which IGMP host query
packets are transmitted on the interface. The range is from
1 to 65 535, and the default is 125.
Status
Indicates whether or not the interface is active. Note that it
becomes active if there are any active (that is, forwarding)
ports on the interface. If the VLAN has no port members or
if all of the port members are disabled, the status is
notInService.
Version
The version of IGMP (1 or 2) that you want to configure on
this interface. For IGMP to function correctly, all routers on
a LAN must use the same version. The default is
version 2.
OperVersion
The version of IGMP currently running on this interface.
Querier
The address of the IGMP querier on the IP subnet to which
this interface is attached.
QueryMaxResponseTime
The maximum response time (in 1/10 seconds) advertised
in IGMPv2 general queries on this interface. This field is a
read-only field and is not configurable in the Ethernet
Routing Switch 1600 Series.
WrongVersionQueries
The number of queries received with an IGMP version that
does not match the interface. IGMP requires that all routers
on a LAN be configured to run the same version of IGMP. If
any queries are received with the wrong version, it indicates
a version mismatch.
Joins
The number of times a group membership has been added
on this interface; that is, the number of times an entry for
this interface has been added to the cache table. This
number gives an indication of the amount of IGMP activity
over time.
Robustness
Tuning for the expected packet loss of a network. This value
is equal to the number of expected query packet losses per
serial query interval, plus 1. If a network is expected to lose
query packets, increase the robustness value.
The range is from 2 to 255, and the default is 2. The default
value of 2 means that one query per query interval may be
dropped without the querier aging out.
Configuring IP Routing and Multicast Operations using Device Manager
236 Chapter 10 Configuring IGMP
Table 54 IGMP dialog box—Interface tab fields (continued)
Field
Description
OtherQuerierPresent
Timeout
The length of time that must pass before a multicast router
decides that there is no other router that can be the querier.
If the local router is the querier, the value is 0.
FlushAction
•
•
•
•
RouterAlertEnable
When enabled, this parameter instructs the router to
process packets not directly addressed to it.
Note: To maximize your network performance, Nortel
recommends that you set this parameter according to the
version of IGMP currently in use.
• IGMPv1—Disable
• IGMPv2—Enable
• IGMPv3—Disable (not supported in the Ethernet
Routing Switch 1600 Series)
none
flushGrpMem
flushMrouter
flushSender
Note: The values for the IGMP parameters, QueryInterval, Robustness, and Version,
must be the same as those configured on the interface (VLAN) of the multicast router.
Multicast Router
To manage and configure multicast router discovery, perform the following
procedure:
1
From the Device Manager menu, select IP Routing > IGMP.
The IGMP dialog box appears with the Globals tab displayed (see Figure 101
on page 232).
2
321712-B Rev 03
Select the Multicast Router Discovery tab (Figure 104).
Chapter 10 Configuring IGMP 237
Figure 104 IGMP dialog box—Multicast Router Discovery tab
3
In the fields provided, make the configuration changes necessary.
4
Click Apply.
Table 55 outlines the fields on this tab.
Table 55 Multicast Router Discovery fields
Field
Description
Interface
The IGMP interface.
MrdiscEnable
Enables or disables multicast router discovery.
DiscoveredRouterPorts
The discovered router ports on this interface.
MaxAdvertiseInterval
The maximum interval (in seconds) between successive
advertisements. This is an integer value between 2 and
180.
MinAdvertiseInterval
The minimum interval (in seconds) between successive
advertisements. This is an integer value between 3 and
180.
MaxInitialAdvertiseInterval
The maximum interval (in seconds) between successive
initial advertisements. This is an integer value between 2
and 180.
MinInitialAdvertiseInterval
The minimum interval (in seconds) between successive
advertisements. This is an integer value between 3 and
180.
NeighborDeadInterval
The interval (in seconds) that can pass before a neighbor is
declared dead. This is an integer value between 2 and 180.
Configuring IP Routing and Multicast Operations using Device Manager
238 Chapter 10 Configuring IGMP
Viewing IGMP Snoop Information
To view information about IGMP snooping:
1
From the Device Manager menu bar, select IP Routing > IGMP.
The IGMP dialog box appears with the Globals tab displayed (see Figure 101
on page 232).
2
Select the Snoop tab.
The Snoop tab appears (Figure 105).
Figure 105 IGMP dialog box—Snoop tab
Table 56 describes the Snoop tab fields.
Table 56 Snoop tab fields
Field
Description
Interface
The VLAN ID for the VLAN.
SnoopEnable
Enables (true) or disables (false) IGMP snooping. IGMP
snooping works only when a multicast router exists in the
VLAN.
ProxySnoopEnable
Indicates whether or not the IGMP report proxy feature is
enabled. When this feature is enabled, reports are
forwarded from hosts to the multicast router once per group
per query interval or when there is new group information.
When this feature is disabled, all reports from different
hosts are forwarded to multicast routers, and more than one
group report may be forwarded for the same multicast
group per query interval. The default is enabled.
FastLeaveEnable
Enable or disable FastLeave for this port.
321712-B Rev 03
Chapter 10 Configuring IGMP 239
Table 56 Snoop tab fields (continued)
Field
Description
FastLeavePortMembers
The set of ports that are enabled for FastLeave.
SnoopMRouterPorts
Ports that have been configured as multicast router ports.
Such ports are directly attached to a multicast router so the
multicast data and group reports are forwarded to the
router.
Caution: Configure this field only when there are multiple
multicast routers that are not directly attached to one
another but are directly attached to the VLAN (technically
an invalid configuration). If multicast routers have a route
between them (the valid configuration) and this field is
configured, a multicast loop forms.
SnoopActiveMRouter Ports Active multicast router ports are ports directly attached to a
multicast router. These ports include the querier port and all
ports in the forwarding state that were configured by the
user as well as those that were dynamically learned via
receiving queries.
SnoopMRouterExpiration
Time remaining before the multicast router is aged out. If
the switch does not receive any queries before this time
expires, it flushes out all group memberships known to the
VLAN. The Query Max Response Interval (obtained from
the queries received) is used as the timer resolution.
Configuring IP Routing and Multicast Operations using Device Manager
240 Chapter 10 Configuring IGMP
Viewing IGMP Dynamic Group Information
To view information about IGMP dynamic groups, perform the following
procedure:
1
From the Device Manager menu bar, select IP Routing > IGMP.
The IGMP dialog box appears with the Globals tab displayed (see Figure 101
on page 232).
2
Select the Groups tab.
The Groups tab appears (Figure 106).
Figure 106 IGMP dialog box—Groups tab
321712-B Rev 03
Chapter 10 Configuring IGMP 241
Table 57 describes the Groups tab fields.
Table 57 Group tab fields
Field
Description
IpAddress
Multicast group address (Class D) that members can join. A group
address can be the same for many incoming ports.
InPort
The member port for the group. This is the port on which group traffic is
forwarded.
Members
Specifies the IP address of the IGMP receiver (host or IGMP reporter).
Expiration
Time left before the group report expires on this port. This variable is
updated upon receiving a group report.
IGMP Static Information
Some sources do not join a multicast group before transmitting a multicast stream.
When this is the case, and if there are no other group members joined in the
VLAN, the data is flooded to all VLAN ports. A static entry can be created to
forward multicast data streams to a particular set of ports within the VLAN.
When the entry is created, multicast data streams are always forwarded to the
multicast router within the VLAN, in addition to the ports configured for this
static entry.
Note: IGMP snoop can guarantee delivery of only local multicast data.
It does not guarantee delivery of remote multicast data. A port cannot be
configured as a static receiver in an IGMP snoop-enabled VLAN that
does not contain at least one dynamic receiver port and have multicast
data forwarded.
To add members to the IGMP snoop group, perform the following procedure:
1
From the Device Manager menu bar, select IP Routing > IGMP.
The IGMP dialog box appears with the Globals tab displayed (see Figure 101
on page 232).
2
Select the Static tab.
Configuring IP Routing and Multicast Operations using Device Manager
242 Chapter 10 Configuring IGMP
The Static tab appears (Figure 107).
Figure 107 IGMP dialog box—Static tab
3
Click Insert.
The IGMP, Insert Static dialog box appears (Figure 108).
Figure 108 IGMP, Insert Static dialog box
4
In the IfIndex field, enter the router interface for the IGMP entry. This can be
done manually or by clicking the VLAN . . . button and selecting a VLAN
from the list.
5
Enter the group address in the GrpAddr field.
6
In the MemberPorts field, click the ellipsis (...) button to display the
IgmpStaticMemberPorts dialog box. Select the member ports by doing the
following:
7
a
Select the desired ports from the provided list.
b
Click OK.
In the NotAllowedToJoin field, click the ellipsis (...) button to display the
IgmpStaticNotAllowedToJoin dialog box. Select those ports not allowed to
join this group by doing the following:
a
321712-B Rev 03
Select the desired ports from the provided list.
Chapter 10 Configuring IGMP 243
b
8
Click OK.
Click Insert.
Table 58 describes the fields in the IGMP, Insert Static dialog box.
Table 58 IGMP, Insert Static dialog box fields
Field
Description
Ifndex
The interface on which the IGMP entry is enabled.
Vlan Id
The VLAN to which you wish to flood multicast data.
GrpAddr
Enter the multicast group address of the multicast stream.
MemberPorts
The ports to which you want to redirect the multicast stream for this
multicast group. The ports must be member ports of the VLAN.
NotAllowedToJoin The ports that do not receive the multicast stream for this multicast
group.
Multicast Access Control Configuration
To configure multicast access control for a selected IGMP interface or VLAN,
perform the following tasks:
1
From the Device Manager menu bar, select IP Routing > IGMP.
The IGMP dialog box appears with the Globals tab displayed (Figure 101 on
page 232).
2
Select the Access tab.
The Access tab appears (Figure 109).
Configuring IP Routing and Multicast Operations using Device Manager
244 Chapter 10 Configuring IGMP
Figure 109 IGMP dialog box—Access tab
3
Click Insert.
The IGMP, Insert Access dialog box appears (Figure 110).
Figure 110 IGMP, Insert Access dialog box
4
Enter the router interface on which the IGMP entry is enabled by manually
entering the interface in the IfIndex field or clicking the VLAN button and
selecting one from the list.
5
Enter the group address in the GrpAddr field.
6
Enter the host network in the HostNetwork field.
7
Enter the host subnet mask in the HostMask field.
8
Select the host mode in the Mode area.
9
Click Insert.
10 Click Close.
321712-B Rev 03
Chapter 10 Configuring IGMP 245
Table 59 describes the Access tab fields
Table 59 Access tab fields
Field
Description
IfIndex
Indicates the interface on which the IGMP entry is enabled.
GrpAddr
Indicates the group address on which multicast access
control is configured.
HostNetwork
Indicates the IP address of a host for which this entry
contains information.
HostMask
Indicates the subnet mask of a host for which this entry
contains information.
Mode
Specifies the action of the access policy. The options are:
• denyRX—denies IP multicast received traffic.
• denyBOTH—denies both IP multicast transmitted and
received traffic.
Viewing IGMP Sender Entries
To view IGMP sender entries, perform the following tasks:
1
From the Device Manager menu bar, select IP Routing > IGMP.
The IGMP dialog box appears with the Globals tab displayed (Figure 101 on
page 232).
2
Select the Sender tab.
The Sender tab appears (Figure 111).
Figure 111 IGMP dialog box—Sender tab
Configuring IP Routing and Multicast Operations using Device Manager
246 Chapter 10 Configuring IGMP
Table 60 describes the Sender tab fields.
Table 60 Sender tab fields
Field
Description
GrpAddr
The IP multicast group address.
IfIndex
The VLAN interface index.
MemberAddr
The source IP address of the group traffic sender.
Action
Used to flush an entry or a group.
TPort
The port on which traffic is received.
State
The state, either filtered on non-filtered. Filtered implies the
traffic is blocked, probably due to an access control policy.
321712-B Rev 03
247
Chapter 11
Configuring Multicast MAC Filtering
With Multicast Media Access Control (MAC) filtering, you can create a smaller
flooding domain inside a VLAN. For a particular VLAN, you specify a multicast
MAC address and a subset of ports. When clients send data to that designated
MAC address, only that subset of ports receive the traffic.
The Ethernet Routing Switch 1600 Series uses MAC address information to
switch Layer 2 IP multicast traffic. Mapping of IP to MAC addresses is not a
one-to-one mapping; hence, several IP addresses can be mapped to the same MAC
address. Take this fact into consideration when configuring Multicast Access
control policies applicable to specific IP addresses, since the policy is applied on
the mapped MAC address, which also covers other IP multicast addresses.
This section describes how to configure Layer 2 multicast MAC filtering. For
more information about Multicast MAC filtering concepts, refer to “IP routing
and multicast concepts” on page 29.
Configuring IP Routing and Multicast Operations using Device Manager
248 Chapter 11 Configuring Multicast MAC Filtering
Configuring Layer 2 Multicast MAC Filtering
To configure the MAC address for Layer 2 multicast flooding:
1
From the Device Manager menu bar, select VLAN > VLANs.
The VLAN dialog box appears with the Basic tab displayed (Figure 112). The
Basic tab displays all defined VLANs, their configurations, and their current
status.
Figure 112 VLAN dialog box—Basic tab
2
Select a VLAN by clicking in a column in the desired row.
3
Click Bridge.
The Bridge dialog box appears with the FDB Aging tab displayed
(Figure 113).
Figure 113 Bridge, VLAN dialog box—FDB Aging tab
321712-B Rev 03
Chapter 11 Configuring Multicast MAC Filtering 249
4
Select the Multicast tab.
The Multicast tab appears (Figure 114).
Figure 114 Bridge, VLAN dialog box—Multicast tab
5
Click Insert.
The Bridge, VLAN, Insert Multicast dialog box appears (Figure 115).
Figure 115 Bridge, VLAN, Insert Multicast dialog box
6
In the Address field, type the MAC address for the multicast flooding
domain.
7
Click the ellipsis (...) button next to the ForwardingPorts field and choose
from the list of ports in the BridgeStaticMulticastForwardingPorts dialog
box.
8
Click the ellipsis (...) next to the MltIds field and choose from the list that
appears in the MltIds dialog box.
9
Click Insert.
Configuring IP Routing and Multicast Operations using Device Manager
250 Chapter 11 Configuring Multicast MAC Filtering
Table 61 describes the Bridge, VLAN, Insert Multicast fields.
Table 61 Bridge, VLAN dialog box—Multicast tab fields
Item
Description
MacAddress
The MAC address for the multicast-flooding domain.*
VlanId
The VLAN identifier.
ForwardingPorts
The ports to be included in the multicast-flooding domain.
MltIds
The MLTs to be included in the multicast-flooding domain.
NumMltIds
The number of MLTs included in the multicast-flooding domain.
* WARNING: When you enter a multicast MAC address that falls in the IP multicast range,
the following message appears:
This MAC address falls in the reserved range for IP multicast.
Problems may occur if you have IP multicast configured on this interface.
Do not use any MAC addresses 01:00:5e:00:00:XX corresponding to the 224.0.0.x
reserved IP address range.
321712-B Rev 03
251
Chapter 12
Configuring PIM-SM
The Ethernet Routing Switch 1600 Series supports the sparse mode of Protocol
Independent Multicast (PIM-SM). PIM-SM supports multicast groups spread out
across large areas of a company or the Internet.
PIM-SM does not maintain its own, or depend upon, a specific multicast protocol
to maintain unicast routing tables. PIM-SM uses the routing table information
from any underlying unicast routing protocol, such as RIP or OSPF. PIM-SM
sends one stream of data to the network where it is replicated to all interested
receivers.
Instead of using a push model, PIM-SM uses a pull model, in which receivers pull
down multicast traffic. For sparsely populated networks, PIM-SM is more
efficient than dense-mode protocols because it sends multicast traffic only to
those routers that belong to a specific multicast group and that choose to receive
the traffic.
The Ethernet Routing Switch 1600 Series supports the following for PIM-SM:
•
•
RP functionality
BSR functionality
For more information about PIM-SM concepts and terminology, refer to “IP
routing and multicast concepts” on page 29.
This section contains the following topics:
•
•
•
•
“Configuration Prerequisites” on page 252
“Enabling PIM-SM Globally” on page 252
“Enabling PIM on a VLAN Interface” on page 255
“Viewing and Editing PIM Interface parameters” on page 257
Configuring IP Routing and Multicast Operations using Device Manager
252 Chapter 12 Configuring PIM-SM
•
•
•
•
“Viewing PIM-SM Neighbor Parameters” on page 259
“Viewing RP Set Parameters” on page 260
“Configuring a Candidate RP” on page 261
“Viewing the Current Bootstrap Router (BSR)” on page 263
Configuration Prerequisites
Before configuring PIM-SM, prepare the router as follows:
1
Configure an IP interface.
2
Configure a unicast protocol (RIP or OSPF) globally and on the interfaces on
which PIM-SM is to be configured.
PIM-SM requires a unicast protocol to use in order to multicast traffic within
the network when performing the Reverse Path Forwarding (RFP) check.
PIM-SM uses the information from the unicast routing table to create and
maintain the shared and shortest multicast tree that enables PIM-enabled
routers to communicate. The unicast routing table must contain a route to
every multicast source in the network as well as routes to PIM entities like the
RPs and BSR.
3
To configure PIM-SM on an Ethernet Routing Switch 1600 Series switch, the
following configurations are required:
— Enable PIM-SM globally.
— Enable PIM-SM on individual interfaces.
— Configure one or several RPs for the groups that will be used by a
multicast application in the network.
— Configure one or several BSRs to propagate RP information to all
switches in the network.
Enabling PIM-SM Globally
IGMP is required for PIM-SM. When PIM-SM is enabled globally and on a
particular interface, the IGMP parameters take effect.
321712-B Rev 03
Chapter 12 Configuring PIM-SM 253
To enable PIM-SM globally, follow this procedure:
1
From the Device Manager menu bar, select IP Routing > PIM.
The PIM dialog box appears with the Globals tab displayed (Figure 116).
Figure 116 PIM dialog box—Globals tab
2
Select the Enable check box.
3
Click Apply.
Table 62 describes the Globals tab fields.
Table 62 PIM Globals tab fields
Field
Description
Mode
Configures the mode on the routing switch: the only valid
value is sm (sparse mode).
Enable
Enables or disables PIM.
JoinPruneInterval
Specifies how long to wait (in seconds) before the PIM router
sends out the next join/prune message to its upstream
neighbors.
The range is from 1 to 18 724, and the default is 60 seconds.
Configuring IP Routing and Multicast Operations using Device Manager
254 Chapter 12 Configuring PIM-SM
Table 62 PIM Globals tab fields (continued)
Field
Description
RegisterSuppTimer
Specifies how long (in seconds) the DR suppresses sending
registers to the RP. The timer starts when the DR receives a
Register Stop message from the RP.
The range is from 5 to 65 535, and the default is 60 seconds.
UniRouteChgTimeOut
Specifies how often (in seconds) the switch polls the routing
table manager (RTM) for unicast routing information updates
to be used by PIM.
The range is from 2 to 65 535, and the default is 5 seconds.
Note: Lowering this value increases how often the switch polls
the RTM. This may affect the switch’s performance, especially
when there is a lot of traffic flowing through the switch.
DiscardDataTimeOut
Specifies how long (in seconds) to discard data until the join
message is received from the RP. An ipmc discard record is
created after a register packet is sent until the timer expires or
when a join message is received.
The range is from 5 to 65 535, and the default is 60 seconds.
CRPADVTimeOut
Specifies how often (in seconds) that routers configured as
candidate RPs send C-RP advertisement messages. When
this timer expires, the C-RP sends an advertisement message
to the elected BSR.
The range is from 5 to 26 214, and the default is 60 seconds.
BootStrapPeriod
Specifies the interval (in seconds) that the elected BSR waits
between originating bootstrap messages.
The range is from 5 to 32 757, and the default is 60 seconds.
321712-B Rev 03
Chapter 12 Configuring PIM-SM 255
Enabling PIM on a VLAN Interface
Before enabling PIM on a VLAN, it must first be enabled globally. Refer to
“Enabling PIM-SM Globally” on page 252 for further information.
To enable PIM on a VLAN, perform the following procedure:
1
From the Device Manager menu bar, select VLAN > VLANs.
The VLAN dialog box appears with the Basic tab displayed.
2
Select a VLAN by clicking in a column of the appropriate row.
3
Click IP.
The IP, VLAN dialog box appears with the IP Address tab displayed
(Figure 117).
Figure 117 IP VLAN dialog box I
4
Select the PIM tab.
The PIM tab appears (Figure 118).
Configuring IP Routing and Multicast Operations using Device Manager
256 Chapter 12 Configuring PIM-SM
Figure 118 IP VLAN dialog box—PIM tab
5
Select the Enable check box.
6
Click Apply.
Table 63 describes the PIM tab fields.
Table 63 VLAN PIM tab fields
Field
Description
Enable
Enables (true) or disables (false) PIM.
Mode
Displays the mode currently running on the routing switch.
The only valid mode is Sparse. This is a read-only field.
HelloInterval
Specifies how long to wait (in seconds) before the PIM router
sends out the next hello message to neighboring routers. The
default is 30 seconds.
JoinPruneInterval
Specifies how long to wait (in seconds) before the PIM router
sends out the next join/prune message to its upstream
neighbors. The default is 60 seconds.
CBSRPreference
Sets your preference for this local interface to become a
Candidate BSR. The Candidate BSR with the highest
BSR-priority and address is referred to as the preferred BSR.
The default is -1, which indicates that the current interface is
not a Candidate BSR.
321712-B Rev 03
Chapter 12 Configuring PIM-SM 257
Viewing and Editing PIM Interface parameters
To view or edit PIM parameters for a port, perform the following procedure:
1
From the Device Manager menu bar, select IP Routing > PIM.
The PIM dialog box appears with the Globals tab displayed.
2
Select the Interfaces tab.
The PIM dialog box, Interfaces tab appears (Figure 119).
Figure 119 PIM dialog box—Interfaces tab
3
Edit any fields, if applicable.
4
Click Apply.
Table 64 describes the Interfaces tab fields.
Table 64 PIM Interfaces tab fields
Field
Description
IfIndex
Interface Index.
Address
The IP address of the PIM interface.
NetMask
The network mask for the IP address of the PIM interface.
Mode
The configured mode of this interface. The only valid mode is
Sparse. This is a read-only field.
DR
The router with the highest IP address on a LAN designated to
perform these tasks.
Configuring IP Routing and Multicast Operations using Device Manager
258 Chapter 12 Configuring PIM-SM
Table 64 PIM Interfaces tab fields (continued)
Field
Description
HelloInterval
Specifies how long to wait (in seconds) before the PIM switch
sends out the next hello message to neighboring switches.
The default is 30 seconds.
JoinPruneInterval
Specifies how long to wait (in seconds) before the PIM switch
sends out the next join/prune message to its upstream
neighbors. The default is 60 seconds.
CBSRPreference
Sets your preference for this local interface to become a
Candidate BSR. The Candidate BSR with the highest
BSR-priority and address is referred to as the preferred BSR.
The default is -1, which indicates that the current interface is
not a Candidate BSR.
OperState
Indicates the status of PIM on this interface: enabled or
disabled.
321712-B Rev 03
Chapter 12 Configuring PIM-SM 259
Viewing PIM-SM Neighbor Parameters
To view PIM-SM neighbor parameters, do the following:
1
From the Device Manager menu bar, select IP Routing > PIM.
The PIM dialog box appears with the Globals tab displayed (Figure 116 on
page 253).
2
Select the Neighbors tab.
The Neighbors tab appears (Figure 120).
Figure 120 PIM dialog box—Neighbors tab
Table 65 describes the Neighbors tab fields.
Table 65 PIM Neighbors tab fields
Field
Description
Address
The IP address of the PIM neighbor for which this entry
contains information.
IfIndex
The slot/port number or VLAN ID of the interface used to
reach this PIM neighbor.
UpTime
The elapsed time since this PIM neighbor last became a
neighbor of the local router.
ExpiryTime
The time remaining before this PIM neighbor times out.
Configuring IP Routing and Multicast Operations using Device Manager
260 Chapter 12 Configuring PIM-SM
Viewing RP Set Parameters
RP Set is a list of rendezvous point addresses. The bootstrap router (BSR)
constructs this list from C-RP advertisements and then distributes it to all PIM
routers in the BSR PIM domain.
To view the RP Set parameters, use this procedure:
1
From the Device Manager menu bar, select IP Routing > PIM.
The PIM dialog box appears with the Globals tab displayed (Figure 116 on
page 253).
2
Select the RP Set tab.
The RP Set tab appears (Figure 121).
Figure 121 PIM dialog box—RP Set tab
321712-B Rev 03
Chapter 12 Configuring PIM-SM 261
Table 66 describes the RP Set tab fields.
Table 66 PIM RP Set tab fields
Field
Description
GroupAddress
The IP address of the multicast group. When combined with
the group mask, it identifies the prefix that the local router
uses to advertise itself as a C-RP.
GroupMask
The address mask of the multicast group. When combined
with the group address, it identifies the prefix that the local
router uses to advertise itself as a C-RP.
Address
The IP address of the C-RP.
HoldTime
The time specified in a C-RP advertisement that the BSR uses
to time out the RP. When the BSR receives an advertisement
for the RP, it restarts the timer. If no advertisement arrives
before the timer expires, the BSR removes that RP from the
RP set.
ExpiryTime
The time remaining before this C-RP times out.
Configuring a Candidate RP
The following procedure describes how to add a candidate rendezvous point
(C-RP) to the RP Set.
To configure a C-RP, do the following:
1
From the Device Manager menu bar, select IP Routing > PIM.
The PIM dialog box appears with the Globals tab displayed (Figure 116).
2
Select the Candidate RP tab.
The Candidate RP tab appears (Figure 122).
Configuring IP Routing and Multicast Operations using Device Manager
262 Chapter 12 Configuring PIM-SM
Figure 122 PIM dialog box—Candidate RP tab
3
Click Insert.
The PIM, Insert Candidate dialog box appears (Figure 123).
Figure 123 PIM dialog box—Insert Candidate RP dialog box
4
Enter values for the GroupAddress, GroupMask, and InterfaceAddress
fields.
5
Click Insert.
321712-B Rev 03
Chapter 12 Configuring PIM-SM 263
Table 67 describes the Candidate RP tab fields.
Table 67 PIM Candidate RP tab fields
Field
Description
GroupAddress
The IP address of the multicast group. When combined with
the group mask, it identifies the prefix that the local router
uses to advertise itself as a C-RP.
GroupMask
The address mask of the multicast group. When combined
with the group address, it identifies the prefix that the local
router uses to advertise itself as a C-RP.
Address
The IP address of the C-RP. This address has to be one of the
local PIM-SM enabled interfaces.
You can use the GroupMask value to configure a Candidate RP for several
groups in one configuration. For example, in a Candidate RP configuration with a
GroupAddress value of 224.0.0.0 and a GroupMask of 240.0.0.0, you can
configure the Candidate RP for a multicast range from 224.0.0.0 to
239.255.255.255.
Viewing the Current Bootstrap Router (BSR)
PIM-SM cannot run without a bootstrap router (BSR). Although a PIM-SM
domain can have only one active BSR, additional routers can be configured as
candidate BSRs (C-BSRs). A C-BSR provides backup protection in case the
primary BSR fails.
To display information about the current bootstrap router, do the following:
1
From the Device Manager menu bar, select IP Routing > PIM.
The PIM dialog box appears with the Globals tab displayed (Figure 116 on
page 253).
2
Select the Current BSR tab.
The Current BSR tab appears (Figure 124).
Configuring IP Routing and Multicast Operations using Device Manager
264 Chapter 12 Configuring PIM-SM
Figure 124 PIM dialog box—Current BSR tab
Table 68 describes the Current BSR tab fields.
Table 68 Current BSR tab fields
Field
Description
Address
The IP address of the current BSR for the local PIM domain.
FragmentTag
A randomly generated number that distinguishes fragments
belonging to different Bootstrap messages. Fragments belonging to
the same Bootstrap message carry the same Fragment Tag.
HashMask
The mask used in the hash function to map a group to one of the
C-RPs from the RP-Set. The hash-mask allows a small number of
consecutive groups (e.g., 4) to always hash to the same RP.
Priority
The priority of the current BSR. The Candidate BSR (C-BSR) with
the highest BSR-priority and address (referred to as the preferred
BSR) is elected as the BSR for the domain.
Bootstrap Timer
When the Bootstrap Timer expires, the BSR sends out Bootstrap
messages.
321712-B Rev 03
265
Chapter 13
Configuring Multicast Routes
This section describes the configuration and management of Layer 3 IP Multicast
protocol interfaces. This section contains the following topics:
•
•
•
•
•
•
“Viewing Route Information” on page 265
“Viewing Next Hop Information” on page 266
“Viewing and Editing Interface Information” on page 268
“Configuring Static Source Groups” on page 268
“Troubleshooting Multicast Routes” on page 272
“Viewing and Editing Static Source Groups” on page 270
Viewing Route Information
To view multicast route information, select IP Routing > Multicast from the
Device Manager menu. The Multicast dialog box appears with the Routes tab
selected (Figure 125).
Figure 125 Multicast dialog box—Routes tab
Configuring IP Routing and Multicast Operations using Device Manager
266
Chapter 13 Configuring Multicast Routes
Table 125 describes the fields on this tab.
Table 69 Routes tab fields
Field
Description
Group
The IP multicast group address for which this entry contains
multicast routing information.
Source
The network address which, when combined with the
corresponding route SourceMask value, identifies the sources for
which this entry contains multicast routing information.
SourceMask
The network mask which, when combined with the corresponding
route Source value, identifies the sources for which this entry
contains multicast routing information.
UpstreamNeighbor
The address of the upstream neighbor (for example, RPF
neighbor) from which IP datagrams from these sources to this
multicast address are received or 0.0.0.0 if the network is local.
Interface
The port number or VLAN ID on which IP datagrams sent by these
sources to this multicast address are received.
ExpiryTime
The amount of time remaining before this entry is aged out. The
value 0 indicates that the entry is not subject to aging.
Protocol
The routing protocol through which this route was learned.
Viewing Next Hop Information
To view Next Hop information, select IP Routing > Multicast from the Device
Manager menu and select the Next Hops tab from the Multicast dialog box
(Figure 126).
Figure 126 Multicast dialog box—Next Hops tab
321712-B Rev 03
Chapter 13 Configuring Multicast Routes
267
Table 70 describes the fields on this tab.
Table 70 Next Hops tab fields
Field
Description
Group
The IP multicast group for which this entry specifies a next hop
on an outgoing interface.
Source
The network address which, when combined with the
corresponding next hop SourceMask value, identifies the source
for which this entry specifies a next hop on an outgoing
interface.
SourceMask
The network mask which, when combined with the
corresponding next hop Source value, identifies the source for
which this entry specifies a next hop on an outgoing interface.
OutInterface
The port number or VLAN ID for the outgoing interface for this
next hop.
Address
The address of the next hop specific to this entry. For most
interfaces, it is identical to the next hop group. NBMA interfaces,
however, may have multiple next hop addresses out a single
outgoing interface.
State
An indication of whether or not the outgoing interface and next
hop represented by this entry is currently being used to forward
IP datagrams. A value of forwarding indicates it is currently
being used; pruned indicates it is not being used.
ExpiryTime
The minimum amount of time remaining before this entry is aged
out. The value 0 indicates that the entry is not subject to aging.
ClosestMemberHops
The minimum number of hops between this router and any
member of this IP Multicast group reached via this next hop on
this outgoing interface. Any IP Multicast datagrams for the group
that have a TTL less than this number of hops are not forwarded
to this next hop.
Protocol
The routing protocol through which this next hop was learned.
Configuring IP Routing and Multicast Operations using Device Manager
268
Chapter 13 Configuring Multicast Routes
Viewing and Editing Interface Information
To view and edit multicast interface information, select IP Routing > Multicast
from the Device Manager menu and select the Interfaces tab from the Multicast
dialog box (Figure 127).
Figure 127 Multicast dialog box—Interfaces tab
Table 71 describes the fields on this tab.
Table 71 Multicast dialog box—Interfaces tab fields
Field
Description
Interface
The slot/port number or VLAN ID for which this entry contains
information.
Ttl
The datagram time to live (TTL) threshold for the interface. Any IP
multicast datagrams with a TTL less than this threshold are not
forwarded out the interface. The default value of 1 means that all
multicast packets are forwarded out the interface.
Protocol
The routing protocol running on this interface.
Configuring Static Source Groups
Static source groups enable the configuration of static source group entries in the
PIM multicast routing table. PIM cannot prune these entries from the distribution
tree. In other words, even if there are no receivers in the group, the multicast
stream for a static source-group entry stays active.
321712-B Rev 03
Chapter 13 Configuring Multicast Routes
269
Configuration Considerations
The Ethernet Routing Switch 1600 Series supports static source groups using
PIM-SM. For conceptual information about PIM and static source groups, refer to
“IP routing and multicast concepts” on page 29.
Note: Before configuring a static source group, PIM must first be
globally enabled. Refer to “Enabling PIM-SM Globally” on page 255 for
further information.
After configuring static source groups, keep the following points in mind:
•
•
•
The maximum number of static source groups cannot exceed 1 024.
Disabling PIM causes the switch to deactivate all of the static source groups.
These groups are reenabled when PIM is reenabled.
In PIM-SM configurations, the static source group feature works for both
specific source addresses and subnet addresses. When the network mask is
configured as 255.255.255.255, the full source address is used to match the
(S,G), which is the specific source case. When the network mask field is
configured as a subnet mask for the source, only the source subnet is used to
match (S,G)s.
Configuring IP Routing and Multicast Operations using Device Manager
270
Chapter 13 Configuring Multicast Routes
Viewing and Editing Static Source Groups
To view and edit static source groups, select IP Routing > Multicast from the
Device Manager menu and select the Static Source Group tab on the Multicast
dialog box (Figure 128).
Figure 128 Multicast dialog box—Static Source Group tab
Table 72 describes the fields on this tab.
Table 72 Static Source Group tab fields
Field
Description
GroupAddress
The multicast group IP address for this static source-group entry.
SourceSubnet
The multicast source address for this static source-group entry.
SrcSubnetMask
The source subnet mask for this static source-group entry.
321712-B Rev 03
Chapter 13 Configuring Multicast Routes
271
Adding a Static Source Group
Use the following procedure to add a new static source group. Attempting to
create a duplicate of an existing source group entry will result in an error.
Perform the following procedure to create a new static source group:
1
From the Device Manager menu, select IP Routing > Multicast.
The Multicast dialog box appears with the Routes tab displayed.
2
Select the Static Source Group tab.
3
Click Insert.
The Multicast, Insert Static Source Group dialog box appears (Figure 129).
Figure 129 Multicast, Insert Static Source Group dialog box
4
Enter the group address, source subnet, and source subnet mask in the
provided fields. An explanation of these values can be found in Table 72 on
page 270.
5
Click Insert.
Deleting a Static Source Group
To delete a static source group, perform the following procedure:
1
From the Device Manager menu, select IP Routing > Multicast.
The Multicast dialog box appears with the Routes tab displayed.
2
Select the Static Source Group tab.
3
Select the desired group address value.
Configuring IP Routing and Multicast Operations using Device Manager
272
Chapter 13 Configuring Multicast Routes
4
Click Delete.
Troubleshooting Multicast Routes
The Mroute-HW tab provides an exact hardware view of existing IP multicast
records and information about sender and receiver ports for every stream. In
addition to this information, data is also provided on prunes, sources, and egress
VLANs in dialog boxes accessible from this tab. This section describes the
procedure necessary to perform multicast route troubleshooting.
To perform multicast route troubleshooting, follow these steps:
1
From the Device Manager menu, select IP Routing > Multicast.
The Multicast dialog box appears with the Routes tab displayed.
2
Select the Mroute-HW tab.
This tab is illustrated in Figure 130 on page 273.
3
To view information about prunes, sources, or egress VLANs, do the
following:
a
Select a row by clicking in it.
b
The Prunes, Sources, and Egress VLANs buttons are enabled.
c
Click the desired button.
Refer to the following topics for further information about prunes, sources, or
Egress VLANs:
•
•
•
321712-B Rev 03
“Prunes Dialog” on page 273
“Sources dialog box” on page 274
“Egress VLANs dialog box” on page 275
Chapter 13 Configuring Multicast Routes
273
Figure 130 Multicast dialog box—Mroute-HW tab
Table 73 describes the fields on this tab.
Table 73 Mroute-HW tab fields
Field
Description
GroupAddress
The IP multicast group address for the multicast stream.
Subnet
The network address of the source subnet that has sources
sending IP multicast traffic to the GroupAddress.
Note: There can be several sources sending to that Group.
You can use the Source tab to view these sources.
Invlan
The ingress VLAN ID where the traffic emanates for the
multicast stream.
Pruned
True indicates that the multicast stream has been pruned
back. False indicates it has not.
Prunes Dialog
The Prunes dialog displays all of the prunes received for the group address in the
multicast stream selected from the Mroute-HW table. Refer to “Troubleshooting
Multicast Routes” on page 272 for the procedure to access this dialog box. This
dialog box is illustrated in Figure 131.
Configuring IP Routing and Multicast Operations using Device Manager
274
Chapter 13 Configuring Multicast Routes
Figure 131 Prunes dialog box
Table 74 describes the fields in this dialog box.
Table 74 Prunes tab fields
Field
Description
Neighbor
The IP address of the downstream neighbor from whom the
prune has been received.
Prune Timer
The time left for the neighboring downstream router to send
the graft message.
Sources dialog box
The Sources dialog box displays all the sources on the subnet that are sending to
the particular group selected in the Mroute-HW table. Refer to “Troubleshooting
Multicast Routes” on page 272 for the procedure to access this dialog box. This
dialog box is illustrated in Figure 132.
Figure 132 Sources dialog box
321712-B Rev 03
Chapter 13 Configuring Multicast Routes
275
Table 75 describes the fields in this dialog box.
Table 75 Sources tab fields
Field
Description
Source Address
The IP addresses of the sources on this particular subnet
sending traffic to the multicast group for the selected entry in
the Mroute-HW table.
Ingress Port
The corresponding ingress port in the multicast stream
selected from the Mroute-HW table.
Egress VLANs dialog box
The Egress VLANs dialog box displays the egress VLANs for the streams
corresponding to the selected entry in the Mroute-Hw entry. Refer to
“Troubleshooting Multicast Routes” on page 272 for the procedure to access this
dialog box. This dialog box is illustrated in Figure 133.
Figure 133 Egress VLANs Dialog
Table 76 describes the fields in this dialog box.
Table 76 Egress VLANs tab fields
Field
Description
Egress Vlan
All the egress VLANs for the particular multicast stream
selected from the Mroute-HW table.
Egress Vlan Ports
The corresponding ports for the particular multicast stream
selected from the Mroute-HW table.
Configuring IP Routing and Multicast Operations using Device Manager
276
Chapter 13 Configuring Multicast Routes
321712-B Rev 03
277
Index
Numbers
10000MbpsPortDefaultMetric field
OSPF General tab 179
1000MbpsPortDefaultMetric field
OSPF General tab 179
100MbpsPortDefaultMetric field
OSPF General tab 179
10MbpsPortDefaultMetric field
OSPF General tab 179
Interface tab 150
IP, VLAN, Insert VRRP dialog box 156
Age field
Ext. Link State DB tab 213
Link State Database tab 212
Routes tab 100
alternative routes, enabling 96
AltSequence field
Routes tab 100
announce policies 39
Area field 205
A
accept policies 39
AreaBdrRtrCount field
OSPF Areas tab 199
ActiveCount field
OSPF Areas tab 200
AreaBdrRtrStatus field
OSPF General tab 179
Addr field
Addresses tab 99
AreaID field 203
Area Aggregate tab 215
Host tab 207
Address Resolution Protocol
See ARP.
Addresses tab
accessing 98
fields 99
AreaId field
Link State Database tab 211
OSPF Interfaces tab 183
Stub Area Metrics tab 210
AddressLessIf field 209
OSPF Interfaces tab 183
AreaLSACksumSum field
OSPF Areas tab 200
AddressLessIndex field
OSPF Neighbors tab 191
AreaSummary field
OSPF Areas tab 200
AdminStat field
OSPF General tab 179
OSPF Interfaces tab 183
ARP
address-resolution cache 43
IP address 43
MAC address 43
managing 120
request 43
static entries 43
Advertise Metric field 215
Advertisement field 213
AdvertisementInterval field
Configuring IP Routing and Multicast Operations using Device Manager
278
Index
table 43
viewing 120
ARP tab
accessing 120
fields 121
C
candidate bootstrap router 80
candidate RP router 80
ASBdrRtCount field
OSPF Areas tab 200
Checksum field
Ext. Link State DB tab 213
Link State Database fields 212
ASBdrRtrStatus checkbox
OSPF General tab 179
Circuitless IP tab
fields 109
ASBR, specifying 207
CLIP interface
configuring 108
AuthKey field
OSPF Interfaces tab 184
AuthType field
OSPF Interfaces tab 184
automatic route aggregation 174
automatic virtual link 201
AutoVirtLinkEnable checkbox
OSPF General tab 180
configuration
Vrrp on a VLAN 148, 154
configuring
route preferences 112
router discovery 114
configuring multicast MAC filtering
using the DM 247
AutoVirtLinkEnable field 202
Control field
Interface tab 150
IP, VLAN, Insert VRRP dialog box 156
B
conventions, text 23
BackupDesignatedRouter
OSPF Interfaces tab 184
CriticalIPAddr field
Interface tab 151
BackUpMaster field 153
IP,VLAN, Insert VRRP dialog box 157
CriticalIpAddr field
IP, VLAN, Insert VRRP dialog box 156
BackUpMastrState field 153
CriticalIpAddrEnable field 156
Interface tab 151
BcastAddr field 99
black hole routes 106
black hole static routes 36
BootP
broadcast packets 42
message format 40
BootP/DHCP relay
overview 125
C-RP
configuring 261
D
DefImportMetric field
RIP Globals tab 165
deleting, L2/L2 static routes 107
Bootstrap Protocol. See BootP
designated router
OSPF 56
bootstrap router 80
designated router. See DR
BSR, viewing 263
DesignatedRouter field
Bootstrap Protocol. See BootP
321712-B Rev 03
Index 279
RoutePref tab 113
OSPF Interfaces tab 184
Dest field
IP, Insert Static Routes dialog box 104
Routes tab 100
Static Routes tab 104
DHCP
assigning network addresses 40
IP address 42
message type 40
multiple servers 42
packet forwarding 41
relay operation 40
servers 40
UDP/IP broadcasts 40
virtual router interface 41
distribution tree 65
DR
(designated router), describing 79
Dynamic Host Configuration Protocol. See DHCP
filtering 38
deleting 144
inbound/outbound traffic on a RIP
interface 142
G
Globals tab
accessing 94, 148
fields 95, 97, 98, 149
H
Hello Protocol 56
Hello Suppressed
OSPF Neighbors tab 191
HelloInterval field
OSPF Interfaces tab 184
Virtual Neighbor tab 204
HelloSuppressed field 205
E
HoldDownState field 153
Effect field 215
Enable field
IP, Insert Static Routes dialog box 104
Static Routes tab 104
Events field 204
OSPF Interfaces tab 185
OSPF Neighbors tab 191
Virtual Neighbor tab 205
ExternalSACksumSum field
OSPF General tab 179
HoldDownTime field
RIP Globals tab 164
HoldDownTimer field
IP, VLAN, Insert VRRP dialog box 157
Secondary Feature tab 153
HoldDownTimeRemaining field 153
HopOrMetric field 100
host addresses and masks, specifying 89
I
ExternLsaCount field
OSPF General tab 179
F
FastAdvertisementEnable field 150
IP, VLAN, Insert VRRP dialog box 156
FastAdvertisementInterval field 150
IP, VLAN, Insert VRRP dialog box 156
ICMP router discovery
configuring 114
configuring on a VLAN 116
enabling 114
viewing the router discovery table 114
Id field
OSPF Areas tab 199
IfIndex field
fields
Configuring IP Routing and Multicast Operations using Device Manager
280
Index
IP, Insert Static Routes dialog box 104
Static Routes tab 104
IGMP
cache information 231
description 71, 75
elected querier 72
fast leave feature 73
host leave message 73
host reports 72
interface table 233
maximum response time 72
proxy 75
queries 72
snoop 73
snooping 230
static entry 241
versions 75
IGMP Device Manager commands
FastLeaveEnable 229
FastLeavePortMembers 229
FlushAction 236
Join messages 235
LastReporter 233
NotAllowedToJoin 243
OtherQuerierPresentTimeout 236
ProxySnoopEnable 229
QueryInterval 229
QueryMaxResponseTime 229
Robustness 229
RouterAlertEnable 236
SnoopEnable 229
SnoopMRouterPorts 229
Version 229
Version1Host Timer 233
WrongVersionQueries 235
IGMPv1
host reports 72
Interface field
ARP tab 121
Interface tab 150
Routes tab 100
Interface tab
accessing 149
fields 150
Interior Gateway Protocol (IGP) 52
IP address
assigning to a VLAN 92
IP configuration dialog box, accessing 98
IP forwarding, enabling 94
IP router, managing 97
IP routes 99
IP routing
address classes 30
address, in dotted-decimal notation 30
BootP/DHCP relay 40
CIDR (classless interdomain routing)
address 34
connectivity protocols 43
multicast addresses 30
OSPF benefits 53
OSPF description 52
unicast addresses 30
IP static routes, creating 102
IP, Insert Circuitless dialog box
fields 109
IP, Insert Static Route dialog box
accessing 103
IP, Insert Static Routes dialog box
fields 104
IP, VLAN RIP tab
fields 167
Insert ARP dialog box 122
IpAddr field
Interface tab 150
IP, VLAN Insert VRRP dialog box 156
OSPF Neighbors tab 191
Virtual Neighbor tab 205
Insert ARP port selection dialog box 122
IpAddress field
IGMPv2
host reports 72
in filters 39
321712-B Rev 03
Index 281
Metrics tab 209
Static Routes tab 104
Stub Area Metrics tab 210
ARP tab 121
Host tab 207
If Metrics tab 209
OSPF Interfaces tab 183
metric speed, OSPF 208
Metric Type field 210
L
MetricType field 142, 218
LastSpfRun field
OSPF General tab 180
Mroute-HW tab 272
LocalNextHop field
IP, Insert Static Routes dialog box 104
Static Routes tab 104
LSACount field
OSPF Areas tab 200
LsdbType field 215
LSID field
Ext. Link State DB tab 213
Link State Database tab 211
LSRetransQLen field 205
OSPF Neighbors tab 191
M
MAC filtering
configuring Layer 2 multicast 248
MAC filtering Device Manager commands
Address 250
ForwardingPorts 250
MltIds 250
VlanId 250
MacAddress field
ARP tab 121
manual virtual link 61
Mask field
Area Aggregate tab 215
IP, Insert Static Routes dialog box 104
Routes tab 100
Static Routes tab 104
MasterIpAddr field 150
Metric field 142, 218
Host tab 207
IP, Insert Static Routes tab 104
multicast
address range 67
class D address 67
distribution tree 65
interfaces 268
next hops 266
PIM-SM 77
PIM-SM domain 78
PIM-SM hosts 78
reverse path 66
routes 265
static source group 268
stream 241
multicast access control
configuring 243
overview of 87
policy types
denyBOTH 88
denyRX 88
tab fields 245
Multicast Device Manager commands
ClosestMemberHops 267
ExpiryTime 266
Group 266
Interface 266
Protocol 266
Source 266
SourceMask 266
static source group 268
UpstreamNeighbor 266
Multicast dialog box- Mroute-HW tab 273
Multicast dialog box- Mroute-HW tab- Egress
VLANs tab 275
Configuring IP Routing and Multicast Operations using Device Manager
282
Index
Multicast dialog box- Mroute-HW tab- Prunes
tab 274
Multicast dialog box- Mroute-HW tab- Sources
tab 274
multicast MAC filtering. See MAC filtering
Multicast Router Discovery Protocol 90
N
Neighbor field
Virtual Neighbor tab 203
NetMask field
Addresses tab 99
NextHop field
IP, Insert Static Route dialog box 104
Routes tab 100
Static Routes tab 104
O
Open Shortest Path First (OSPF) Protocol. See
OSPF
Open Shortest Path First. See OSPF
OperAction field 157
Secondary Feature tab 153
Operation field
RIP Globals tab 164
Options field
OSPF Neighbors tab 191
VIrtual Neighbor tab 205
OriginateNewLSas field
OSPF General tab 179
OSPF 177
adjacent routers 57
area border router (ABR) 58
areas 54
AS boundary router (ASBR) 58, 62
AS external link advertisement 60
AS external routes 61
ASBR summary link advertisement 60
autonomous system external (ASE) routes 61
backbone area 55
321712-B Rev 03
backup designated router (BDR) 56, 58
benefits 53
database description (DD) packets 59
definition 177
description 52
designated router (DR) 56, 58
hello packets 59
Hello Protocol 56
implementation
ASBR 207
creating a virtual link 201
stub area 200
interfaces description 58
internal router (IR) 58
IP 59
link state acknowledgements 60
link state advertisements 60
link state request packets 59
link state update packets 59
link-state database 53
link-state information 57
neighbor adjacencies 57
neighbors 56
network links advertisement 60
network summary link advertisement 60
packets 59
route advertisement 59
router links advertisement 60
router types 58
routing algorithm 54
specifying ASBRs 62
stub area 56
variable-length mask 59
virtual link 61
virtual links 61
OSPF Accept policy 141, 216
OSPF Area dialog box 199
OSPF Neighbors dialog box 190
OspfAction field
OSPF General tab 180
ospfImportASExtern field
OSPF Areas tab 199
Index 283
ospfNbmaNbrPermanence field
OSPF Neighbors tab 191
out filters 39
P
Path Type field
Routes tab 101
PIM
C-RP
configuring 261
DR
showing 257
enabling on a VLAN using Device
Manager 255
neighbor parameters 259
viewing and editing interface parameters using
Device Manager 257
viewing current BSR 263
viewing RP Set parameters 260
PIM Device Manager commands
DR
showing 257
ExpiryTime 259
HoldTime 261
UpTime 259
PIM-SM
BSR
(bootstrap router), description 80
C-BSR
(candidate bootstrap router), description 80
configuration prerequisites 252
C-RP
(candidate RP), description 80
description 77
domain 78
DR
(designated router), description 79
enabling globally 252
hosts 78
IGMP, configuring with 252
join/prune messages 82
OSPF, configuring with 252
receiver join process 82
receiver leave process 83
register messages 82
register-stop messages 82
required elements 84
Reverse Path Forwarding 252
RIP, configuring with 252
RP
(rendezvous-point), description 79
shared tree 80
shortest-path tree 81
source sending packets to group 83
PingVirtualAddress field 149
poisoned reverse, RIP 44
policies
OSPF Accept 141, 216
Policy, Insert Prefix List dialog box
fields 132
Policy, Insert Route Policy dialog box
fields 136
PollInterval field
OSPF Interfaces tab 185
port selection dialog box, Insert ARP 122
Preference field
IP, Insert Static Routes dialog box 104
Static Routes tab 104
prefix list, configuring 130
priority
OSPF 184
Priority field
Interface tab 150
IP, VLAN, Insert VRRP dialog box 156
OSPF Neighbors tab 191
Proto field 100
Protocol Independent Multicast-Sparse Mode. See
PIM-SM
Q
Queries field
RIP Globals tab 164
Configuring IP Routing and Multicast Operations using Device Manager
284
Index
R
RcvBadPackets field 176
RcvBadRoutes field 176
ReasmMaxSize field
Addresses tab 99
rendezvous-point router 79
Retrans Interval field
VIrtual Neighbor tab 204
RetransInterval field
OSPF Interfaces tab 184
Reverse Path Forwarding 252
reverse path multicast 66
UDP 44
RIP Globals tab
fields 164
RIP In/Out Policy tab
accessing 143
fields 144
RIP Interface Advance tab
accessing 173
fields 174
RIP interface status 175
RIP Interface tab
accessing 170
fields 171
RIP
changing interface configuration 173
configuring version 170
deleting inbound/outbound filtering
policies 144
enabling 163
enabling on an interface 165
filtering inbound/outbound traffic 142
interface configuration 165
managing 170
managing global settings 163
RcvBadPackets counter 176
RcvBadRoutes counter 176
send modes 172
supply and listen settings 170
triggered updates counter 176
viewing 163
RIP status
RcvBadPackets field 176
RcvBadRoutes 176
SentUpdates 176
RIP (Routing Information Protocol)
about 43
advertisements 44
distance vector protocol 45
garbage list 44
holddown 44
hop count 45
metric 45
poisoned reverse 44
routing table 44
split horizon 44
triggered updates 44
RoutePolicy field 142, 218
321712-B Rev 03
RIP Status tab
fields 176
RIP tab
accessing 163, 170
route policies
creating 132
editing 132
overview 129
route preferences
configuring 112
RouteChanges field
RIP Globals tab 164
RoutePref tab
fields 113
router interfaces 91
RouterID field
Ext. Link State DB tab 213
Link State Database tab 212
OSPF General tab 179
routes
alternative 96
black hole 106
Index 285
Virtual Neighbor tab 205
Routes tab
accessing 99
fields 100
static ARP entries 121
static default routes, definition 105
RouteSource field 142, 218
Routing Information Protocol. See RIP 43
routing policies
accept 39
announce 39
Static Route tab
fields 104
static routes 35
black hole static routes 36
deleting 107
overview 101
routing tables
IP 99
Static Routes tab
accessing 102
RP Set parameters 260
static routes, creating 102
RtrDeadInterval field
OSPF Interfaces tab 184
Virtual Neighbor tab 204
RtrId field
OSPF Neighbors tab 191
Virtual Neighbor tab 205
static source group
adding a new group 271
configuration considerations 269
definition 268
deleting a group 271
Status field
If Metrics tab 209
IP, Insert Static Routes dialog box 104
Static Routes tab 104
Rtrpriority field
OSPF Interfaces tab 184
RxNewLSas field
OSPF General tab 179
STP
spanning tree convergence 35
S
stub area, creating 200
Secondary Features tab
accessing 152
send modes, RIP 172
subnet
mask 31
variable-length 32
SendTrap field 149
Subnets field 142, 218
SentUpdates 176
supernet
address/mask pair 34
classless interdomain routing (CIDR)
address 34
contiguous network addresses 33
Sequence field
Ext. Link State DB tab 213
Link State Database tab 212
SpfHoldDownTime checkbox
OSPF General tab 180
SpfRuns field
OSPF Areas tab 199
supply and listen settings, RIP 170
T
split horizon, RIP 44
State field 150, 204
OSPF Interfaces tab 183
OSPF Neighbors tab 191
text conventions 23
time to live, setting 95
TimeOutInterval field
Configuring IP Routing and Multicast Operations using Device Manager
286
Index
fields 221
RIP Globals tab 165
TOS field
Host tab 207
IF Metrics tab 209
Stub Area Metrics tab 210
TransitDelay field
OSPF Interfaces tab 184
Virtual Neighbor tab 203
UpdateTime field
RIP Globals tab 164
V
VersionNumber field
OSPF General tab 179
TrapEnable checkbox
OSPF General tab 179
VirtIf 202
triggered updates
RIP 44
virtual router interfaces 91
Type field
ARP tab 121
Ext. Link State DB tab 213
Link State Database tab 211
OSPF Interfaces tab 184
VirtualMacAddr field 150
U
VLANs
VRRP 148, 154
UDP
RIP 44
UDP Forwarding 64
UDP forwarding
accessing Forwarding Lists tab 223
applying policies 225
creating UDP protocols 219
forwarding entries 221
policies 223
UDP protocols
creating 219
UdpForwarding Broadcast Interfaces tab
accessing 225
fields 226
UdpForwarding dialog box
accessing 219
UdpForwarding Forwarding Lists tab
fields 224
UdpForwarding Forwardings tab
fields 222
UdpForwarding Protocols tab
321712-B Rev 03
virtual link, creating 201
Virtual Router Redundancy Protocol. See VRRP
VirtualRouter UpTime field 150
VirtualRouterUpTime field 150
VLAN RIP tab
accessing 165
VrId field 150, 153
Vrid field 156
VRRP 148, 154
configuring 148, 149, 152
overview 147