* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download florida institue of technology
Network tap wikipedia , lookup
Distributed firewall wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
SIP extensions for the IP Multimedia Subsystem wikipedia , lookup
Airborne Networking wikipedia , lookup
Computer network wikipedia , lookup
Point-to-Point Protocol over Ethernet wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
TCP congestion control wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Deep packet inspection wikipedia , lookup
Internet protocol suite wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
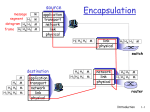
This is a closed book and closed notes exam. Page 1 of 16 FLORIDA INSTITUE OF TECHNOLOGY ELECTRICAL AND COMPUTER ENGINEERING PROGRAMS ECE 5535 COMPUTER NETWORKS 2 CSE 5631 ADVANCED COMPUTER NETWORKS Test #2 26 March 2003 NAME ________________________________Student Number (last 4 digits)_________ 1. Congestion Control. There are two broad classes of type of services that Network Layer provides. When a connection is established from a source to a destination, packets can be sent via a Connection Oriented Service (Virtual-Circuit) or Connectionless Oriented Service (Datagram). A. Which type of connection service allows a simpler Control over Congestion? Explain why. (5 points) B. In Datagram Subnets using Choke Packets is one of the methods that can be applied to Congestion Control. i. Briefly describe this method in the case when destination node D is congested and the sending node is A. Packets are routed from A,B,C to D as presented in the figure bellow: (3 points) A ii. B C D How many hops does it take for the congested node to get relief (i.e., reduced flow) from the source A. (2 points) iii. Is there a way to provide an immediate effect and reduced the flow to the destination node? If yes explain how. (5 points) C. Describe major differences between the WARNING BIT method and the RED (Random Early Detection) method. (5 points) This is a closed book and closed notes exam. Page 2 of 16 ANSWER: A. Connection Oriented Service - Virtual-Circuit. The service can be negotiated during the setup of the Virtual-Circuit. All necessary resources are reserved then and guaranteed for the life of that connection. If a catastrophic failure happens to occur (a router failure along the path) the new Virtual-Circuit can be set up and transmition completed. B. i. D sends a Choke Packet to back to the Source A via Router C. Router C in turn forwards that packet to router B which sends it to A. Source node A reduces the flow to D. ii. 6 – Hops (D to C, C to B, B to A, and A to B, B to C and finally C to D). iii. Yes. The relief can be immediate if the load is distribution across all routers in the path. First router to share the load is B which is the first one to receive the CHOKE packet by reducing the flow to D. As CHOKE packet arrives at node C from B it too reduces the flow to B and finally originating node A does the same think. C. Warning BIT method explicitly sets a BIT that indicates congestion notification to the source; whereas RED implicitly notifies the source by simply dropping one of its packets. This is a closed book and closed notes exam. Page 3 of 16 2. Quality of Service A. Enumerate four parameters/factors that determine quality of service. (4 points) B. Briefly describe each parameter under A, and name at least one application for each parameter that requires High Control to achieve good Quality of Service? (8 points) C. For transmition of Sound data, Jitter Control is very important. Briefly describe one way to lower the jitter? (4 points) This is a closed book and closed notes exam. Page 4 of 16 ANSWER: A. i. Reliability ii. Delay iii. Jitter iv. Bandwidth B. i. Reliability – how often bits gets corrupted. e-mail, File transfer, etc. ii. Delay – how long does it takes to send a packet from source to destination. Telephony Videoconferencing iii. Jitter – how variable the delay is. Audio on Demand Video on Demand iv. Bandwidth – is the frequency range of the signal that is being transmitted. Videoconferencing Video on Demand. C. One can use Buffering to temporarily store incoming packets arriving at varying time intervals. The packets can be released at regular time intervals ensuring minimal jitter. This is a closed book and closed notes exam. Page 5 of 16 3. The main protocol for the integrated services architecture is Resource Reservation Protocol (RSVP). A. What is this protocol used for? (2 points) B. Can congestion occur when using this protocol? Why? (4 points) C. The network bellow uses RSVP with multicast trees for host 1 and host 2. Suppose that host 3 requires a channel of bandwidth 2 MB/sec for a flow from host 1 and another channel of bandwidth 1 MB/sec for a flow from the host 2. At the same time host 4 requests a channel of bandwidth of 2 MB/sec for a flow from host 1 and host 5 requests a channel of bandwidth of 1 MB/sec for a flow from host 2. How much total bandwidth will be reserved for these requests at routers A, B, C, E, H, J, K, and L? Note: Host 1 and 2 each provide only one type of service. (8 points) This is a closed book and closed notes exam. Page 6 of 16 ANSWER: A. It is used to make reservation of resources when requesting for a particular service. Other protocols are used to transfer data. B. No. All resources needed are reserved with RSVP. If insufficient resources are available then the connection is not established. C. A=2MB/sec, B=0, C=1MB/sec. D=0, E=3MB/sec. F=0, G=0, H=3MB/sec, I=0, J=3MB/sec, K=2MB/sec, L=1MB/sec. This is a closed book and closed notes exam. Page 7 of 16 4. The IP Protocol. Bellow is the figure depicting IPv4 header. A. A router is blasting out IP packets whose total length (data plus header is) is 1024 bytes. Assuming that packets live for 10 sec what is the maximum line speed that router can operate at without danger of cycling through the IP datagram Identification number space? (5 points) B. Suppose that host A is connected to a router R1, R1 is connected to another router, R2, and R2 is connected to host B. Suppose that a TCP message that contains 900 bytes of data and 20 bytes of TCP header is passed to the IP code at host A for delivery to B. Show the Total length, Identification, DF (Don’t Fragment field), MF (More Fragments) and Fragment offset fields of the IP deader in each packet transmitted over the three links. Assume that link A-R1 can support a maximum frame size of 1024 bytes including a 140 byte frame header, link R1-R2 can support a maximum frame size of 512 bytes including a 14-byte frame header, link R1-R2 can support a maximum frame size of 512 bytes, including an 8-byte frame header, and link R2-B can support a maximum frame size of 512 bytes including a 12-byte header. Note that fragments must be a multiple of 8 bytes except the last one. 8 bytes is elementary fragment unit. (12 points) This is a closed book and closed notes exam. Page 8 of 16 ANSWER: A. If the bit rate of the line is b bits/sec, the number of packets/sec that the router can emit is b/(8*1024) = b/8192. The number of seconds it takes to emit a packet is 8192/b. To put 216 = 65536 packets takes 23*210*216/b sec. Equating this equation with packet lifetime of 10 sec, we get: 229/b = 10. Then b is about 53687091 bps = 51.2 Mbps. B. TCP Packet = 900 (data) + 20 (IP header) = 920 Bytes. IP Packet = 920 (data) + 20 (IP header) = 940 Bytes Link A-R1: Can support 1024 bytes including 14-byte frame header (e.g., 1010-byte IP data packet) thus no fragmentation is needed. Length = 940, ID = x, DF = 0, MF = 0, Offset = 0. Link R1-R2: Can support 512 bytes including 8-byte header (e.g., 512-8=504 bytes of IP data packet and 504 – 20 (IP header) = 484). Since IP data in a frame must be multiple of 8 bytes: 8*x ≤ 484 => x ≤ 60.5 bytes. Use x = 60 bytes IP data 1 = 60*8 = 480 Bytes IP packet size 1 = 480 + 20 = 500 Bytes. IP data 2 = 920 – 480 = 440 Bytes IP packet size 2 = 440 + 20 = 460 Bytes. [1] [2] Length = 500, ID = x, DF = 0, MF = 1, Offset = 0. Length = 460, ID = x, DF = 0, MF = 0, Offset = 60. Link R2-B: Can support 512 bytes including 12-byte header (e.g., 512-8=500 bytes of IP data packet and 500 – 20 (IP header) = 480). This implies that no additional fragmentation is needed. Thus [1] [2] Length = 500, ID = x, DF = 0, MF = 1, Offset = 0. Length = 460, ID = x, DF = 0, MF = 0, Offset = 60. This is a closed book and closed notes exam. Page 9 of 16 5. The IP Addresses. Bellow is the figure depicting IPv4 Address Formats. A. Suppose that instead of using 16 bits for the network part of class B address originally, 20 bits had been used. How many class B networks would there have been? (2 points) B. Convert the IP address whose hexadecimal representation is C22F1582 to dotted decimal notation? (2 points) C. A network on the Internet has a subnet mask of 255.255.240.0. What is the maximum number of hosts it can handle? (2 points) D. A large number of consecutive IP addresses are available starting at 198.16.0.0. Suppose that four organizations, A, B, C, and D, request 4000, 2000, 4000 and 8000 addresses, respectively, and in that order. For each of these, give the first IP address assigned, the last IP address assigned, and the mask in the w.x.y.z/s notation. (8 points) This is a closed book and closed notes exam. Page 10 of 16 ANSWER: A. 2(20-2) = 218. Since all 0’s and 1’s are special there are 218-2 addresses available (262142). B. C2.2F.15.82 = 12*16+2.2*16+15.1*16+5.8*16+2=194.47.21.130 C. The mask is 20 bits long, so the network part is 20 bits. The remaining 12 bits are for the host, so 212 = 4096 host addresses exist. D. All requests are rounded up to a power of 2. Start Address End Address Mask A: 198.16.0.0 - 198.16.15.255 198.16.0.0/20 B: 198.16.16.0 - 198.16.23.255 198.16.16.0/21 C: 198.16.32.0 - 198.16.47.255 198.16.32.0/20 D: 198.16.64.0 - 198.16.95.255 198.16.64.0/19 This is a closed book and closed notes exam. Page 11 of 16 6. Network Address Translation (NAT). Within a LAN NAT is used to convert internal IP addresses to true network addresses as illustrated in the figure bellow: A. What is the major motivation of IP address conversion using NAT and what kind of problem does it solve? (4 points) B. NAT violates a number of fundamental assumptions of Layered Network Architecture by using TCP or UDP fields of transport layer header. Enumerate and very briefly discuss those violations. (8 points) This is a closed book and closed notes exam. Page 12 of 16 ANSWER: A. To enable creation of new LANs in spite of lack of IP addresses. Due to rapid growth of Internet and limitations imposed by the size of address field in IP header there are very few IP addresses available. B. [1] Based on Network Architectural model, IP is supposed to uniquely identify each machine worldwide. NAT violates this model on top of which the whole software structure of the Internet is build. [2] Internet is changed from connectionless-network to a kind of connection oriented network. NAT box must maintain information for each connection passing through it. Having the network maintain connection state is a property of connection-oriented networks. If a NAT box crashes and its mapping table is lost, all its TCP connections are destroyed. In the absence of NAT router crashes have no effect on TCP. [3] NAT violates fundamental rule of protocol layering: layer k may not make any assumptions about what layer k+1 has put into the payload field – keeping the layers independent. NAT uses TCP fields (which are supposed to be known only to Transport layer). If TCP gets upgraded to a new TCP2 protocol NAT will fail. [4] Processes on the Internet are not required to use TCP or UDP. If a process decides to use a protocol other than TCP or UDP, NAT will fail. This is a closed book and closed notes exam. Page 13 of 16 7. IPv6 IPv6 is supposed to alleviate problems of current IPv4. The basic header of the IPv6 is illustrated in the figure bellow: A. If a block of 1 million addresses is allocated every picosecond (10-12 second), how long will the addresses last? (5 points) This is a closed book and closed notes exam. Page 14 of 16 ANSWER: A. With 16 bytes there are 2(16*8) = 2128 ≈ 3.4*1038 addresses. If the rate of allocation is 106/10-12 = 1018 per second they will last 3.4*1038/1018 seconds = 3.4*1020 seconds = 3.4*1020/3.15*107 ≈ 1013 years. This is a closed book and closed notes exam. Page 15 of 16 8. Transport Layer A. Define the task(s) of transport layer. (2 points) B. To allow users to access transport service, the transport layer must provide some operations to application programs (transport service interface offering a number of primitives). Enumerate a minimal set of such primitives that would allow establishment of a connection, data transfer, and release of the connection. Briefly describe function of each primitive. (8 points) C. In order to set up and establish a connection, transfer data, and release connection (that is provide a complete transport service) transport layer uses handshakes. To establish and release a connection transport protocol uses a three-way handshake. Briefly describe three-way handshake concept used for setting up a connection. Also describe reasons why three-way handshake is required. (5 points) This is a closed book and closed notes exam. Page 16 of 16 ANSWER: A. To provide efficient, reliable, and const-effective data transport from source machine to the destination machine. Transport protocols must be able to perform these tasks over unreliable networks. B. C. To prevent effects of lost packets as well as packets appearing at inopportune moments.