* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Network
Multiprotocol Label Switching wikipedia , lookup
Deep packet inspection wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Distributed firewall wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Computer network wikipedia , lookup
Network tap wikipedia , lookup
Internet protocol suite wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Airborne Networking wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Routing in delay-tolerant networking wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Chapter 4
Network Layer
y
All material copyright 1996-2009
J F Kurose and K
J.F
K.W.
W Ross
Ross, All Rights Reserved
Network Layer
4-1
Chapter 4:
4 Network Layer
4. 1 Introduction
4.2 IP: Internet
Protocol
Datagram format
D
f
IPv4 addressing
IPv6
4.3 Routing
g algorithms
g
Link state
Distance Vector
4.4
44R
Routing
ti iin th
the
Internet
RIP
OSPF and BGP
Network Layer
4-2
Network layer
transport segment from
sending to receiving host
on sending
d
side
d
encapsulates segments
into _______________
on rcving side, delivers
segments to _________
network layer protocols
in every _______, ____
router examines header
fields in all IP datagrams
passing through it
application
transport
network
data link
physical
p
y
network
data link
physical
network
data link
physical
network
data link
physical
network
data link
physical
network
data link
physical
network
data link
physical
Network Layer
application
transport
network
data link
physical
4-3
Two K
Key
y Network-Layer
L y Functions
F
___________:: move packets from router
router’ss
input to appropriate router output
____________: determine
d t
i route
t ttaken
k b
by
packets from source to dest.
routing
algorithms
Network Layer
4-4
Interplay between routing and forwarding
0111
1
3 2
Network Layer
4-5
Forwarding
Forward
ng table
D ti ti Address
Destination
Add
R
Range
# possible entries?
Li k Interface
Link
I t f
11001000 00010111 00010000 00000000
through
11001000 00010111 00010111 11111111
0
11001000 00010111 00011000 00000000
through
11001000 00010111 00011000 11111111
1
11001000 00010111 00011001 00000000
through
11001000 00010111 00011111 11111111
2
otherwise
3
Network Layer
4-6
Longest pref
prefix
x match
matching
ng
Prefix
fi Matchh
11001000 00010111 00010
11001000 00010111 00011000
11001000 00010111 00011
otherwise
Link
i k Interface
f
0
1
2
3
Examples
DA: 11001000 00010111 00010110 10100001
DA: 11001000 00010111 00011000 10101010
Which interface?
Which interface?
Network Layer
4-7
Chapter 4:
4 Network Layer
4. 1 Introduction
4.2 IP: Internet
Protocol
Datagram format
D
f
IPv4 addressing
IPv6
4.3 Routing
g algorithms
g
Link state
Distance Vector
4.4
44R
Routing
ti iin th
the
Internet
RIP
OSPF and BGP
Network Layer
4-8
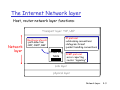
The Internet Network layer
y
Host, router network layer functions:
Transport layer: TCP, UDP
Network
layer
IP p
protocol
•addressing conventions
•datagram format
•packet handling conventions
Routing protocols
•path selection
•RIP, OSPF, BGP
forwarding
f
di
table
ICMP protocol
•error reporting
•router “signaling”
Link layer
physical layer
Network Layer
4-9
IP datagram format
32 bits
how much overhead
with TCP?
20 bytes of TCP
____ bytes of IP
= ___ bytes + app
layer overhead
head. type of
length
ver
len service
fragment
16-bit identifier flgs
offset
upper
time to
header
layer
live
checksum
32 bit source IP address
32 bit destination IP address
Options (if any)
data
( i bl llength,
(variable
n th
typically a TCP
or UDP segment)
Network Layer 4-10
IP F
Fragmentation
gm
& Reassembly
m y
network links have MTU
(max.transfer size) - largest
possible
ibl li
link-level
k l
l frame.
f
different link types,
different MTUs
large IP datagram divided
(“fragmented”) within net
one datagram becomes
several datagrams
“reassembled” only at final
destination
IP header bits used to
identify, order related
fragments
fragmentation:
in: one large datagram
out: 3 smaller datagrams
reassembly
Network Layer
4-11
IP F
Fragmentation
gm
and Reassembly
m y
Example
Ex
mpl
4000 byte
datagram
MTU
MT = 1500 b
bytes
_____ bytes in
data field
offset =
______
length ID fragflag offset
=4000 =x
=0
=0
One large datagram becomes
several smaller datagrams
length ID fragflag offset
=1500 =x
=1
=0
length ID fragflag offset
=1500 =x
=1
=____
length ID fragflag offset
=____ =x
=0
=____
Network Layer 4-12
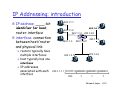
IP Addressing:
g introduction
IP address: ____-bit
identifier for host
host,
router interface
interface: connection
between host/router
and physical link
223.1.1.1
223.1.1.2
223.1.1.4
223.1.1.3
223 1 2 1
223.1.2.1
223.1.2.9
223.1.3.27
223 1 2 2
223.1.2.2
routers typically have
223.1.3.2
223.1.3.1
multiple interfaces
host typically has one
interface
IP addresses
associated with each 223.1.1.1 = 11011111 00000001 00000001 00000001
interface
223
1
1
1
Network Layer 4-13
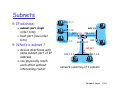
Subnets
IP address:
subnet part (high
order bits)
host part (low order
bits)
What’s a subnet ?
device interfaces with
same subnet part of IP
address
can physically reach
each other without
intervening router
223.1.1.1
223.1.1.2
223.1.1.4
223.1.1.3
223 1 2 1
223.1.2.1
223.1.2.9
223.1.3.27
223 1 2 2
223.1.2.2
subnet
223.1.3.1
223.1.3.2
network consisting of 3 subnets
Network Layer 4-14
Subnets
Recipe
To determine the
subnets, detach each
interface from its
host or router,
creating islands of
i l
isolated
d networks.
k
Each isolated network
is called a subnet.
223.1.1.0/24
223.1.2.0/24
223.1.3.0/24
Subnet mask: /24
Network Layer 4-15
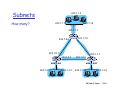
Subnets
223.1.1.2
How many?
223.1.1.1
223.1.1.4
223.1.1.3
223.1.9.2
223.1.7.0
223.1.9.1
223.1.7.1
223.1.8.1
223.1.8.0
223 1 2 6
223.1.2.6
223.1.2.1
223 1 3 27
223.1.3.27
223.1.2.2
223.1.3.1
223.1.3.2
Network Layer 4-16
IP addressing:
address ng CIDR
CIDR: Classless InterDomain Routing
subnet
portion of address of arbitrary length
address format: a.b.c.d/x, where x is # bits in
subnet portion of address
11001000 00010111 00010000 00000000
200.23.16.0/23
Network Layer 4-17
DHCP: Dynamic Host Configuration Protocol
Goal: allow host to dynamically
y
y obtain its IP address from
network server when it joins network
Can renew its lease on address in use
Allows reuse of addresses (only hold address while connected an
“on”)
Support for mobile users who want to join network (more shortly)
DHCP overview:
i
host broadcasts “_________” msg [optional]
DHCP server responds with “__________” msg
[optional]
host requests
q
IP address: “___________” msg
g
DHCP server sends address: “___________” msg
Network Layer 4-18
DHCP client-server scenario
A 223.1.1.1
B
223.1.2.1
223.1.1.2
223.1.1.4
223.1.1.3
223.1.3.1
223.1.2.9
223.1.3.27
223.1.2.2
E
223.1.3.2
Network Layer 4-19
DHCP client-server scenario
DHCP server: 223.1.2.5
DHCP
UDP
IP
Eth
Phy
DHCP discover
src : 0.0.0.0, 68
dest.: 255.255.255.255,67
yiaddr: 0.0.0.0
0000
transaction ID: 654
arriving
client
DHCP offer
src: 223.1.2.5, 67
d t 255.255.255.255,
dest:
255 255 255 255 68
yiaddrr: 223.1.2.4
transaction ID: 654
Lifetime: 3600 secs
DHCP request
time
src: 0.0.0.0, 68
dest:: 255.255.255.255, 67
yiaddrr: 223.1.2.4
transaction ID: 655
Lifetime: 3600 secs
DHCP ACK
src: 223.1.2.5, 67
dest: 255.255.255.255, 68
yiaddrr: 223.1.2.4
t
transaction
ti ID:
ID 655
Lifetime: 3600 secs
Network Layer 4-20
DHCP: more than IP address
DHCP
DHCP can return more than just allocated IP
address on subnet:
address
of first-hop
p router for client
name and IP address of DNS sever
network mask (indicating network versus host
portion
ti of
f address)
dd
)
Network Layer 4-21
IP addresses: how to g
get one?
Q: How does network get subnet part of IP
addr?
dd ?
A: gets allocated portion of its provider ISP’s
address space
ISP's block
11001000 00010111 00010000 00000000
200.23.16.0/20
Organization 0
Organization 1
Organization
g
2
...
11001000 00010111 00010000 00000000
11001000 00010111 00010010 00000000
11001000 00010111 00010100 00000000
…..
….
200.23.16.0/23
_________ /23
__________/23
….
Organization ___ 11001000 00010111 00011110 00000000
__________/23
Network Layer 4-22
Hierarchical addressing:
g route aggregation
gg g
Hierarchical addressing allows efficient advertisement of routing
information:
information
Organization 0
200 23 16 0/23
200.23.16.0/23
Organization 1
200.23.18.0/23
Organization 2
200.23.20.0/23
Organization 7
.
.
.
.
.
.
Fly-By-Night-ISP
“Send me anything
with addresses
beginning
_____________”
Internet
200.23.30.0/23
/
ISPs-R-Us
“Send me anything
with addresses
beginning
1
199.31.0.0/16”
1 0 0/16”
Network Layer 4-23
Hierarchical addressing: more specific
routes
ISPs-R-Us
ISPs
R Us has a more specific route to Organization 1
Organization 0
200.23.16.0/23
Organization 2
200 23 20 0/23
200.23.20.0/23
Organization 7
.
.
.
.
.
.
Fly-By-Night-ISP
Fly
By Night ISP
“Send me anything
with addresses
beginning
200.23.16.0/20”
Internet
200.23.30.0/23
ISPs-R-Us
Organization 1
200.23.18.0/23
“Send me anything
with addresses
beginning 199.31.0.0/16
or _______________”
Network Layer 4-24
IP addressing:
g the last word...
Q: How does an ISP get block of addresses?
A: ICANN: Internet Corporation for Assigned
Names and Numbers
allocates addresses
manages DNS
assigns domain names, resolves disputes
Network Layer 4-25
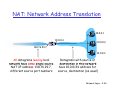
NAT: Network Address Translation
10.0.0.1
10 0 0 4
10.0.0.4
10.0.0.2
138.76.29.7
10.0.0.3
All datagrams leaving local
network have same single source
NAT IP address: 138.76.29.7,
different source port numbers
Datagrams with source or
destination in this network
have 10.0.0/24 address for
source, destination (as usual)
Network Layer 4-26
NAT: Network Address Translation
Motivation: local network uses jjust one IP address as
far as outside world is concerned:
________________________________
________________________________
________________________________
________________________________
Network Layer 4-27
NAT: Network Address Translation
Implementation: NAT router must:
outgoing
datagrams: replace (source IP address, port
#) of every outgoing datagram to (NAT IP address,
new port #)
. . . remote clients/servers
li
/
will
ill respond
d using
i (NAT
IP address, new port #) as destination addr.
remember
b
(i
(in NAT ttranslation
l ti ttable)
bl ) every (source
(
IP address, port #) to (NAT IP address, new port #)
translation pair
incoming
datagrams: replace (NAT IP address, new
port #) in dest fields of every incoming datagram
with corresponding (source IP address
address, port #)
stored in NAT table
Network Layer 4-28
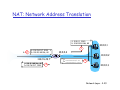
NAT: Network Address Translation
S: 10.0.0.1, 3345
D: 128.119.40.186, 80
2
S: 138.76.29.7, 5001
D: 128.119.40.186, 80
138.76.29.7
S: 128
128.119.40.186,
119 40 186 80
D: 138.76.29.7, 5001
3
1
10 0 0 4
10.0.0.4
S: __________, __
D: _________, ____
10.0.0.1
10.0.0.2
4
10.0.0.3
Network Layer 4-29
NAT: Network Address Translation
_______ port
port-number
number field:
60,000 simultaneous connections with a single
LAN-side address!
NAT is controversial:
routers should only process up to layer 3
violates end-to-end argument
• NAT possibility must be taken into account by app
designers,
g
, eg,
g, P2P applications
pp
address
IPv6
shortage should instead be solved by
Network Layer 4-30
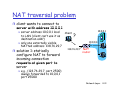
NAT traversal problem
client wants to connect to
server with address 10
10.0.0.1
001
server address 10.0.0.1 local
Client
to LAN (client can’t use it as
st nat on addr)
a r)
destination
only one externally visible
NATted address: 138.76.29.7
solution 1:
1 statically
configure NAT to forward
incoming connection
requests at given port to
server
10.0.0.1
?
138.76.29.7
10.0.0.4
NAT
router
t
e.g., (123.76.29.7, port 2500)
always
a
ways forwarded
forwar
to 10.0.0.1
. . .
port 25000
Network Layer 4-31
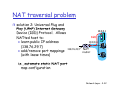
NAT traversal problem
solution 2: Universal Plug and
Play (UPnP) Internet Gateway
Device (IGD) Protocol. Allows
NATted host to:
learn public IP address
(138.76.29.7)
add/remove port mappings
(with lease times)
10.0.0.1
IGD
10.0.0.4
138.76.29.7
NAT
router
t
ii.e.,
e automate static NAT port
map configuration
Network Layer 4-32
NAT traversal problem
solution 3: relaying (used in Skype)
NATed
N T d
client
li
establishes
bli h connection
i to relay
l
External client connects to relay
relay bridges packets between to connections
10.0.0.1
Client
138.76.29.7
NAT
router
Network Layer 4-33
IPv6
Initial motivation: 32-bit address space soon
to be
b completely
l
l allocated.
ll
d
Additional motivation:
header
format helps
l speed processing/forwarding
/
header changes to facilitate QoS
IPv6 datagram format:
fixed-length _______ byte header
no fragmentation allowed
Network Layer 4-34
IPv6 Header (Cont)
Priority: identify priority among datagrams in flow
Flow Label: identify datagrams in same “flow
flow.”
(concept of“flow” not well defined).
Next header: identify upper layer protocol for data
Network Layer 4-35
Other Changes from IPv4
Checksum: removed entirely to reduce
processing time at each hop
Options:
p
allowed,, but outside of
f header,,
indicated by “Next Header” field
Network Layer 4-36
Transition
Trans
t on From IPv4 To IPv6
Not all routers can be upgraded simultaneous
no “flag days”
How will the network operate
p
with mixed IPv4 and
IPv6 routers?
Tunneling: IPv6 carried as payload in IPv4
d
datagram
among IP
IPv4
4 routers
Network Layer 4-37
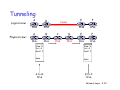
Tunneling
g
Logical view:
Physical view:
E
F
IPv6
IPv6
IPv6
A
B
E
F
IPv6
IPv6
IPv6
P 6
IPv6
A
B
IPv6
tunnel
IPv4
IPv4
Network Layer 4-38
Tunneling
g
Logical view:
Physical view:
A
B
IPv6
IPv6
A
B
C
IPv6
IPv6
IPv4
E
F
IPv6
IPv6
D
E
F
IPv4
IPv6
P 6
IPv6
tunnel
Flow: X
Src: A
Dest: F
Flow: X
Src: A
Dest: F
data
data
A-to-B:
IPv6
E to F
E-to-F:
IPv6
Network Layer 4-39
Chapter 4:
4 Network Layer
4. 1 Introduction
4.2 IP: Internet
Protocol
Datagram format
D
f
IPv4 addressing
IPv6
4.3 Routing
g algorithms
g
Link state
Distance Vector
4.4
44R
Routing
ti iin th
the
Internet
RIP
OSPF and BGP
Network Layer 4-40
Graph abstraction
abstract on
5
2
u
2
1
Graph: G = (N,E)
v
x
3
w
3
1
5
1
y
z
2
N = set off routers = { u, v, w, x, y, z }
E = set of links ={ (u,v), (u,x), (v,x), (v,w), (x,w), (x,y), (w,y), (w,z), (y,z) }
Remark: Graph abstraction is useful in other network contexts
Example: P2P,
P2P where N is set of peers and E is set of TCP connections
Network Layer 4-41
Graph abstraction:
abstract on costs
5
2
u
v
2
1
x
c(x,x’)) = cost of llink
nk (x,x
(x,x’))
• c(x,x
3
w
3
1
5
1
y
2
- e.g., c(w,z) = 5
z
c st could
c uld always
l
s be 1,
1 orr
• cost
inversely related to bandwidth,
or inversely related to
congestion
g
Cost of path (x1, x2, x3,…, xp) = ________________________
Question: What’s the least-cost path between u and z ?
Routing algorithm: algorithm that finds least-cost
least cost path
Network Layer 4-42
Routing
g Algorithm
g
m classification
f
Global or decentralized
information?
Global:
all routers have complete
topology,
l
link
li k cost iinfo
f
“___________” algorithms
Decentralized:
router knows physicallyconnected neighbors, link
costs to neighbors
g
iterative process of
computation, exchange of
info with neighbors
“___________” algorithms
Static or dynamic?
Static:
routes change slowly
over time
Dynamic:
routes change
g more
m
quickly
periodic update
in response to link
cost changes
Network Layer 4-43
AL
Link-State Routing
g Algorithm
g
m
Dijkstra’s
j
algorithm
g
net topology, link costs
known to all nodes
accomplished via “link
link
state broadcast”
all nodes have same info
computes least cost paths
from one node (‘source”) to
all other nodes
gives forwarding table
for that node
iterative: after k
iterations know least cost
iterations,
path to k dest.’s
Notation:
c(x,y): link cost from node
x to y; = ∞ if not direct
neighbors
D(v): current value of cost
of path from source to
dest v
dest.
p(v): predecessor node
along path from source to v
N': set of nodes whose
least cost path definitively
known
Network Layer 4-44
Dijsktra’s
D
j
Algorithm
g
m
1 Initialization:
2 N'
N = {u}
3 for all nodes v
4
if v adjacent to u
5
then D(v) = c(u,v)
c(u v)
6
else D(v) = ∞
7
8 Loop
p
9 find w not in N' such that D(w) is a minimum
10 add w to N'
11 update D(v) for all v adjacent to w and not in N' :
12
D(v) = min( D(v), D(w) + c(w,v) )
13 /* new cost to v is either old cost to v or known
14 shortest path cost to w plus cost from w to v */
15 until
til all
ll nodes
d in
i N'
Network Layer 4-45
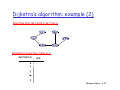
Dijkstra’s
D
j
algorithm:
g
m example
mp
Step
0
1
2
3
4
5
N’
D(v),p(v) D(w),p(w)
D(x),p(x)
D(y),p(y)
D(z),p(z)
5
2
u
v
2
1
x
3
w
3
1
5
1
y
z
2
Network Layer 4-46
Dijkstra’s
D
j
algorithm:
g
m example
mp (2)
( )
Resulting shortest-path tree from u:
v
w
u
z
x
y
R
Resulting
l i f
forwarding
di table
bl iin u:
destination
link
v
x
y
w
z
Network Layer 4-47
Dijkstra’s
D
j
algorithm,
g
m, discussion
Algorithm complexity: n nodes
each iteration: need to check all nodes,
nodes w,
w not in N
_______comparisons: ______
more efficient implementations
p
possible:
p
O(nlogn)
( g )
Oscillations possible:
e.g., link cost = amount of carried traffic
D
1
1
0
A
0 0
C
e
1+e
B
e
initially
1
A
D
A
B
C
… recompute
routing
D
A
B
C
… recompute
D
B
C
… recompute
Network Layer 4-48
Distance
D
stance Vector Algorithm
Algor thm
Bellman Ford Equation (dynamic programming)
Bellman-Ford
Define
dx(y) := cost of least-cost
least cost path from x to y
Then
dx(y) = __________________
Network Layer 4-49
Bellman-Ford
Bellman
Ford example
5
2
u
v
2
1
x
3
w
3
1
Clearly dv(z) = 5
Clearly,
5, dx(z) = 3
3, dw(z) = 3
5
1
y
2
z
B-F equation says:
du(z) =
Node that achieves minimum is next
h p in
hop
i shortest
sh t st path
p th ➜ forwarding
f
di ttable
bl
Network Layer 4-50
Distance
D
stance Vector Algorithm
Algor thm
Dx(y) = estimate of
f least cost f
from x to y
Node x knows cost to each neighbor v: c(x,v)
Node x maintains distance vector Dx = [Dx(y): y є N ]
Node x also maintains its neighbors’ distance vectors
For each neighbor v, x maintains
Dv = [Dv(y): y є N ]
Network Layer 4-51
Distance
D
stance vector algorithm
algor thm (4)
Basic idea:
From time-to-time, each node sends its own
distance vector estimate to neighbors
Asynchronous
When a node x receives new DV estimate from
neighbor, it updates its own DV using B-F equation:
Dx(y) ← minv{c(x,v) + Dv(y)}
for each node y ∊ N
Under minor
minor, natural conditions
conditions, the estimate
Dx(y) converge to the actual least cost dx(y)
Network Layer 4-52
Distance Vector Algorithm
g
(5)
( )
Iterative, asynchronous:
each local iteration caused by:
local link cost change
DV update message from
neighbor
Each node:
wait for (change in local link
cost or msg from neighbor)
Distributed:
each node notifies neighbors
g
only when its DV changes
neighbors then notify their
neighbors if necessary
recompute estimates
if DV to any
y dest has
changed, notify neighbors
Network Layer 4-53
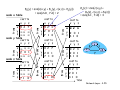
node x table
cost to
x y z
from
m
from
m
x 0 2 7
y ∞∞ ∞
z ∞∞ ∞
node y table
costt tto
x y z
cost to
x y z
x
y
z
x ∞ ∞ ∞
y 2 0 1
z ∞∞ ∞
node z table
cost to
x y z
from
from
m
x
x ∞∞ ∞
y ∞∞ ∞
z 71 0
time
2
y
7
1
z
Network Layer 4-54
Dx(y) = min{c(x,y) + Dy(y), c(x,z) + Dz(y)}
= min{2+0 , 7+1} = 2
node x table
cost to
x y z
x ∞∞ ∞
y ∞∞ ∞
z 71 0
from
from
m
from
fro
om
x 0 2 7
y 2 0 1
z 7 1 0
cost to
x y z
x 0 2 7
y 2 0 1
z 3 1 0
x 0 2 3
y 2 0 1
z 3 1 0
costt tto
x y z
x 0 2 3
y 2 0 1
z 3 1 0
x
2
y
7
1
z
cost to
x y z
from
f
frrom
from
x ∞ ∞ ∞
y 2 0 1
z ∞∞ ∞
node z table
cost to
x y z
x 0 2 3
y 2 0 1
z 7 1 0
cost to
x y z
cost to
x y z
from
f
from
m
x 0 2 7
y ∞∞ ∞
z ∞∞ ∞
node y table
cost to
x y z
cost to
x y z
Dx(z) = min{c(x,y) +
Dy(z), c(x,z) + Dz(z)}
= min{2+1 , 7+0} = 3
x 0 2 3
y 2 0 1
z 3 1 0
time
Network Layer 4-55
Distance Vector: link cost changes
g
Link cost changes:
node
d d
detects
t t llocall li
link
k costt change
h
updates routing info, recalculates
distance vector
if DV changes, notify neighbors
“good
news
travels
fast”
1
x
4
y
50
1
z
At time t0, y detects the link-cost change, updates its DV,
and informs its neighbors
neighbors.
At time t1, z receives the update from y and updates its table.
It computes a new least cost to x and sends its neighbors its DV.
At time t2, y receives z’s update and updates its distance table.
y’s least costs do not change and hence y does not send any
message to z.
Network Layer 4-56
Distance Vector: link cost changes
g
Link cost changes:
good news travels fast
bad news travels slow -
“count to infinity” problem!
44 it
iterations
ti
b
before
f
algorithm stabilizes: see
text
60
x
4
y
50
1
z
P i
Poisoned
d reverse:
If Z routes through Y to
get to X :
Z tells Y its (Z’s) distance
to X is infinite (so Y won’t
route to X via Z)
will
ill this
hi completely
l
l solve
l
count to infinity problem?
Network Layer 4-57
Comparison
p
of LS and DV algorithms
g
Message complexity
LS: with n nodes
nodes, E links
links,
O(nE) msgs sent
DV: exchange between
neighbors only
convergence time varies
Speed
p
of Convergence
g
LS: O(n2) algorithm requires
O(nE) msgs
may have oscillations
DV: convergence time varies
may be routing loops
count-to-infinity
t t i fi it problem
bl
Robustness: what happens
if router malfunctions?
LS:
node can advertise
i
incorrect
li k cost
link
each node computes only
its own table
DV:
DV node can advertise
incorrect path cost
each node’s table used by
others
• error propagate thru
network
Network Layer 4-58
Chapter 4:
4 Network Layer
4. 1 Introduction
4.2 IP: Internet
Protocol
Datagram format
D
f
IPv4 addressing
IPv6
4.3 Routing
g algorithms
g
Link state
Distance Vector
4.4
44R
Routing
ti iin th
the
Internet
RIP
OSPF and BGP
Network Layer 4-59
Intra-AS Routing
g
also known as Interior Gateway
y Protocols (IGP)
(
)
most common Intra-AS (autonomous systems)
routing protocols:
RIP:
Routing Information Protocol
OSPF:
Open Shortest Path First
IGRP:
Interior Gateway Routing Protocol (Cisco
proprietary)
Network Layer 4-60
RIP ( Routing
g Information
f m
Protocol))
distance vector algorithm
g
included in BSD-UNIX Distribution in 1982
distance metric: # of hops (max = 15 hops)
From router A to subnets:
u
v
A
z
C
B
D
w
x
y
destination hops
u
1
v
2
w
2
x
3
y
3
z
2
Network Layer 4-61
RIP advert
advertisements
sements
distance vectors: exchanged among
neighbors every 30 sec via Response
Message (also called advertisement)
each advertisement: list of up to 25
destination subnets within AS
Network Layer 4-62
RIP: Example
z
w
A
x
D
B
y
C
Destination Network
w
y
z
x
….
Next Router
Num. of hops
p to dest.
….
....
A
B
B
--
2
2
7
1
Routing/Forwarding table in D
Network Layer 4-63
RIP: Example
Dest
w
x
z
….
Next
C
…
w
hops
1
1
4
...
A
Advertisement
from A to D
z
x
Destination Network
w
y
z
x
….
D
B
C
Next Router
A
B
y
Num. of hops to dest.
--
….
Routing/Forwarding table in D
2
2
1
....
Network Layer 4-64
RIP: L
RIP
Link
nk Fa
Failure
lure and Recovery
If no advertisement heard after 180 sec -->
neighbor/link declared dead
routes via neighbor invalidated
new advertisements sent to neighbors
neighbors in turn send out new advertisements (if
tables changed)
link failure info quickly (?) propagates to entire net
poison reverse used to prevent ping-pong loops
(infinite distance = 16 hops)
Network Layer 4-65
RIP Table processing
p
g
RIP routing
g tables managed
g by
y application-level
pp
process called route-d (daemon)
advertisements sent in UDP packets, periodically
repeated
t d
routed
routed
Transprt
(UDP)
network
n
t
k
(IP)
link
physical
h i l
Transprt
(UDP)
f
forwarding
din
table
forwarding
f
di
table
network
t
k
(IP)
link
physical
h
l
Network Layer 4-66
OSPF
F (Open
( p Shortest Path First)
F
)
“open”: publicly available
uses Link State algorithm
LS packet dissemination
topology map at each node
route computation using Dijkstra’s algorithm
OSPF advertisement
d
ti
t carries
i one entry
t per neighbor
i hb
router
advertisements disseminated to entire AS (via
flooding)
carried in OSPF messages directly over IP (rather than TCP
or UDP)
Network Layer 4-67
OSPF “advanced” features ((not in RIP))
security: all OSPF messages authenticated (to
prevent malicious intrusion)
multiple same-cost paths allowed (only one path in
RIP)
For each link, multiple cost metrics (e.g., satellite link
cost set “low”
low for best effort; high for real time)
integrated uni- and multicast support:
Multicast OSPF ((MOSPF)) uses same topology
p gy data
base as OSPF
hierarchical OSPF in large domains.
Network Layer 4-68
Internet inter-AS routing:
g BGP
BGP ((Border Gateway
y Protocol):
) the de
facto standard
BGP provides each AS a means to:
1.
2
2.
3.
Obtain subnet reachability information from
neighboring ASs.
Propagate reachability information to all AS
ASinternal routers.
Determine “good” routes to subnets based on
reachability information and policy
policy.
allows subnet to advertise its existence to
rest of Internet: “I am here”
Network Layer 4-69