* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Network Layer - SI-35-02
Multiprotocol Label Switching wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Distributed firewall wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Internet protocol suite wikipedia , lookup
Deep packet inspection wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Computer network wikipedia , lookup
Network tap wikipedia , lookup
Airborne Networking wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
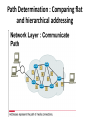
Network Layer Overview • The network layer is responsible for navigating the data through the network. • The function of the network layer is to find the best path through the network. • The network layer's addressing scheme is used by devices to determine the destination of data as it moves through the network. • In this chapter, you will learn about the router’s use and operations in performing the key internetworking function of the Open System Interconnection (OSI) reference model’s network layer, Layer 3. Overview • In addition, you will learn about IP addressing and the three classes of networks in IP addressing schemes. • You also will learn that some IP addresses have been set aside by the American Registry for Internet Numbers (ARIN) and cannot be assigned to any network. • Finally, you will learn about subnetworks and subnet masks and their IP addressing schemes. Importance of a Network Layer : Identifiers • The network layer is responsible for moving data through a set of networks (internetwork). • The network layer's addressing scheme is used by devices to determine the destination of data as it moves through the networks. Importance of a Network Layer : Identifiers • Protocols that have no network layer can only be used on small internal networks. • These protocols usually use only a name (i.e. MAC address) to identify the computer on a network. • The problem with this approach is that, as the network grows in size. • It becomes increasingly difficult to organize all the names, such as making sure that two computers aren't using the same name. Importance of a Network Layer : Identifiers • Protocols that support the network layer use a hierarchical addressing scheme that allows for unique addresses across network boundaries, along with a method for finding a path for data to travel between networks. • While MAC addresses use a flat addressing scheme that makes it difficult to locate devices on other networks. Importance of a Network Layer : Identifiers • Hierarchical addressing schemes enable information to traverse an internetwork, along with a method to find the destination in an efficient fashion. • The telephone network is an example of the use of hierarchical addressing. • The telephone system uses an area code that designates a geographical area for the call's first stop (hop). • The next three digits represent the local exchange (second hop). • The final digits represent the individual destination telephone (which is, or course, the final hop). Importance of a Network Layer : Identifiers • Network devices need an addressing scheme that allows them to forward data packets through the internetwork (a set of networks composed of multiple segments using the same type of addressing). • There are several network layer protocols with different addressing schemes that allow devices to forward data throughout an internetwork. Importance of a Network Layer : Segmentation and autonomous systems • There are two primary reasons why multiple networks are necessary - the growth in size of each network and the growth in the number of networks. • When a LAN, MAN, or WAN grows, it may become necessary or desirable for network traffic control to break it up into smaller pieces called network segments (or just segments). • This results in the network becoming a group of networks, each requiring a separate address. Importance of a Network Layer : Segmentation and autonomous systems • There are already a vast number of networks in existence; separate computer networks are common in offices, schools, companies, businesses, and countries • It is convenient to have these separate networks (or autonomous systems, if each is managed by a single administration) communicate with each other over the Internet. • However, they must do it with sensible addressing schemes and appropriate internetworking devices. • If not, the network traffic flow would become severely clogged, and neither the local networks, nor the Internet, would function. Importance of a Network Layer : Segmentation and autonomous systems • An analogy that might help you understand the need for network segmentation is to imagine a highway system and the number of vehicles that use it. • As the population in the areas surrounding the highways increases, the roads become burdened with too many vehicles. • Networks operate much in the same way. As networks grow, the amount of traffic grows. • One solution might be to increase the bandwidth, much the same as increasing the speed limits of, or adding lanes to, the highways. • Another solution might be to use devices that segment the network and control the flow of traffic, the same way a highway would use devices such as stoplights to control the movement of traffic. Importance of a Network Layer : Segmentation and autonomous systems Importance of a Network Layer : Communication between separate networks • The Internet is a collection of network segments that are tied together to facilitate the sharing of information. • Once again, a good analogy would be the example of the highway system with the large multiple lanes that have been constructed to interconnect many geographical regions. Importance of a Network Layer : Communication between separate networks • Networks operate in much the same manner, with companies known as Internet service providers (ISPs) offering services that tie together multiple network segments. Importance of a Network Layer : Layer 3 network devices • Routers are internetworking devices which operate at OSI layer 3 (the network layer). • They tie together, or interconnect, network segments or entire networks. • They pass data packets between networks based on Layer 3 information Importance of a Network Layer : Layer 3 network devices • Routers make logical decisions regarding the best path for the delivery of data on an internetwork and then direct packets to the appropriate output port and segment. • Routers take packets from LAN devices (e.g. workstations) and, based on Layer 3 information, forward them through the network. • In fact, routing is sometimes referred to as Layer 3 switching Path Determination • Path determination occurs at Layer 3 (network layer). • It enables a router to evaluate the available paths to a destination, and to establish the preferred handling of a packet. • Routing services use network topology information when evaluating network paths. • Path determination is the process that the router uses to choose the next hop in the path for the packet to travel to its destination. • This process is also called routing the packet. Path Determination Path Determination • Path determination for a packet can be compared to a person driving a car from one side of a city to the other. • The driver has a map that shows the streets that he/she needs to take to get to the destination. • The drive from one intersection to another is a hop. Similarly, a router uses a map that shows the available paths to a destination. Path Determination • Routers can also make their decisions based on the traffic density and the speed of the link (bandwidth) • Just as a driver may choose a faster path (a highway) or use less crowded back streets. Path Determination : Network layer addressing • The network address helps the router identify a path within the network cloud. • The router uses the network address to identify the destination network of a packet within an internetwork. Path Determination : Network layer addressing • For some network layer protocols, a network administrator assigns network addresses according to some predetermined internetwork addressing plan. • For other network layer protocols, assigning addresses is partially or completely dynamic/automatic. • In addition to the network address, network protocols use some form of host, or node, address. • The graphic shows three devices in Network 1 (two workstations and a router), each with its own unique host address. • (it also shows that the router is connected to two other networks - Networks 2 & 3). Path Determination : Network layer addressing Path Determination : Network layer addressing • Addressing occurs at the network layer. • Earlier analogies of a network address include the first portions (area code and first three digits) of a telephone number. • The remaining (last four) digits of a phone number tell the phone company equipment which specific phone to ring. • This is similar to the function of the host portion of an address. • The host portion tells the router to which specific device it should deliver a packet. Path Determination : Network layer addressing • Without network layer addressing, routing can not take place. • Routers require network addresses to ensure proper delivery of packets. • Without some hierarchical addressing structure, packets would not be able to travel across an internetwork. • In a similar way, without some hierarchical structure to telephone numbers, postal addresses, or transportation systems, there would not be a smooth delivery of the goods and services. Path Determination : Layer 3 and computer mobility • A MAC address can be compared to your name and the network address to your mailing address. • For example, if you were to move to another town, your name would remain unchanged, but your mailing address would indicate your new location. • Network devices (routers as well as individual computers) have both a MAC address and a protocol (network layer) address. • When you physically move a computer to a different network, the computer maintains the same MAC address, but you must assign it a new network address. Path Determination : Comparing flat and hierarchical addressing • The function of the network layer is to find the best path through the network. • To accomplish this, it uses two addressing methods - flat addressing and hierarchical addressing. • A flat addressing scheme assigns a device the next available address. • There is no thought given to the structure of the addressing scheme. Path Determination : Comparing flat and hierarchical addressing • An example of a flat addressing scheme would be military identification numbering system, or a birth identification numbering system. • MAC addresses function in the same manner. • A vendor is given a block of addresses; the first half of each address is for the vendor's code, the rest of the MAC address is a number that has been sequentially assigned. Path Determination : Comparing flat and hierarchical addressing • The postal system ZIP codes are a good example of hierarchical addressing. • In the ZIP code system the address is determined by the location of the building, not by a randomly assigned number. • The addressing scheme that you will use throughout this course is Internet Protocol (IP) addressing. • IP addresses have a specific structure and are not randomly assigned. Path Determination : Comparing flat and hierarchical addressing IP Addresses within the IP Header : Network layer datagrams • The Internet Protocol (IP) is the most popular implementation of a hierarchical network addressing scheme. • IP is the network protocol the Internet uses. • As information flows down the layers of the OSI model, the data is encapsulated at each layer. • At the network layer, the data is encapsulated within packets (also known as datagrams). IP Addresses within the IP Header : Network layer datagrams • IP determines the form of the IP packet header (which includes addressing and other control information), but does not concern itself with the actual data -- it accepts whatever is passed down from the higher layers. IP Addresses within the IP Header : Network layer datagrams IP Addresses within the IP Header : Network Layer Fields IP Addresses within the IP Header : Network Layer Fields • The Layer 3 packet/datagram becomes the Layer 2 data, which is then encapsulated into frames (as previously discussed). • Similarly, the IP packet consists of the data from upper layers plus an IP header, which consists of: – version - indicates the version of IP currently used (4 bits) – IP header length (HLEN) - indicates the datagram header length in 32 bit words (4 bits) IP Addresses within the IP Header : Network Layer Fields – type-of-service - specifies the level of importance that has been assigned by a particular upper-layer protocol (8 bits) – total length - specifies the length of the entire IP packet, including data and header, in bytes (16 bits) – identification - contains an integer that identifies the current datagram (16 bits) – flags - a 3-bit field in which the 2 low-order bits control fragmentation – one bit specifying whether the packet can be fragmented, and the second whether the packet is the last fragment in a series of fragmented packets (3 bits) IP Addresses within the IP Header : Network Layer Fields – fragment offset - the field that is used to help piece together datagram fragments (16 bits) – time-to-live - maintains a counter that gradually decreases, by increments, to zero, at which point the datagram is discarded, keeping the packets from looping endlessly (8 bits) – protocol - indicates which upper-layer protocol receives incoming packets after IP processing has been completed (8 bits) – header checksum - helps ensure IP header integrity (16 bits) IP Addresses within the IP Header : Network Layer Fields – source address - specifies the sending node (32 bits) – destination address - specifies the receiving node (32 bits) options - allows IP to support various options, such as security (variable length) – data - contains upper-layer information (variable length, maximum 64 Kb) – padding - extra zeros are added to this field to ensure that the IP header is always a multiple of 32 bits IP Addresses within the IP Header: IP header source and destination fields • The IP address contains the information that is necessary to route a packet through the network. • Each source and destination address field contains a 32 bit address. • The source address field contains the IP address of the device that sends the packet. • The destination field contains the IP address of the device that receives the packet. IP Addresses within the IP Header: IP header source and destination fields IP Addresses within the IP Header : IP address as a 32-bit binary number • An IP address is represented by a 32 bit binary number. • As a quick review, remember that each binary digit can be only 0 or 1. • In a binary number, the value of the right-most bit (also called the least significant bit) is either 0 or 1. • The corresponding decimal value of each bit doubles as you move left in the binary number. • So the decimal value of the 2nd bit from the right is either 0 or 2. The third bit is either 0 or 4, the fourth bit 0 or 8, etc ... IP Addresses within the IP Header : IP address as a 32-bit binary number IP Addresses within the IP Header : IP address as a 32-bit binary number • IP addresses are expressed as dotted-decimal numbers - we break up the 32 bits of the address into four octets (an octet is a group of 8 bits). • The maximum decimal value of each octet is 255. • The largest 8 bit binary number is 11111111. • Those bits, from left to right, have decimal values of 128, 64, 32, 16, 8, 4, 2, and 1. Added together, they total 255. IP Addresses within the IP Header: IP address component fields • The network number of an IP address identifies the network to which a device is attached. • The host portion of an IP address identifies the specific device on that network. • Because IP addresses consist of four octets separated by dots, one, two, or three of these octets may be used to identify the network number. • Similarly, up to three of these octets may be used to identify the host portion of an IP address.