* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download 05 – Internet Protocol
Piggybacking (Internet access) wikipedia , lookup
Network tap wikipedia , lookup
Distributed firewall wikipedia , lookup
Point-to-Point Protocol over Ethernet wikipedia , lookup
Airborne Networking wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Computer network wikipedia , lookup
Serial digital interface wikipedia , lookup
Internet protocol suite wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
SIP extensions for the IP Multimedia Subsystem wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Deep packet inspection wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
UniPro protocol stack wikipedia , lookup
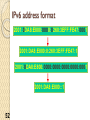
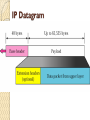
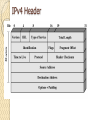
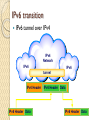
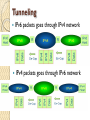
Internet Protocol BS IT 4th Semester By: Muhammad Hanif Goals…. Many people fail in life, not for lack of ability or brains or even courage but simply because they have never organized their energies around a goal. ‐ Elbert Hubbard It's how you deal with failure that determines how you achieve success. ‐ David Feherty Network layer in an internetwork Network Layer Source ◦ Creating a packet from the Segments. The header contains source and destination IP addresses. ◦ Checking the routing table to find the path. ◦ If the packet is larger than MTU, fragment it. Router ◦ Routing the packet by consulting the routing table for each incoming packet and find the path that the packet must be sent to. Destination ◦ Address verification. ◦ Removing the Packets header from the packets and pass it to Transport layer. IPV4 The Internet Protocol version 4 (IPv4) is the delivery mechanism used by the TCP/IP protocols. Position of IPv4 in TCP/IP protocol suite IPv4 datagram format IPv4 Header Variable length: 20-60 byte Contains routing information IPv4 Format Version (4-bit): currently 4. Header length (4-bit): the length of the IP header in 4-byte unit. Type of Services(TOS): ◦ This field was not used earlier because of the lack of standard Total length ◦ to defines the total length of the datagram including the header in bytes. ◦ 16-bit number, the maximum IP size is limited to 216 bytes, or 64 Kbytes. IPv4 Format Identification ◦ A source node gives a unique ID to each packet. Time to Live (TTL) ◦ A packet has a limited lifetime in the network to avoid deadly packets. ◦ Designed to hold a timestamp, and decreased by each router. A packet is discarded by a router if TTL is zero. Protocol ◦ What other protocols are in payload IPv4 Format Header checksum ◦ The checksum is use for error correction. Source IP address and Destination IP address Options ◦ For new protocols Padding ◦ To make the header a multiple of 32-bit words Fragmentation A IP packet can travel through many different networks using different Layer 2 (Data Link layers). The source node has no idea of the path and data link layer its packets will travel. MTU ◦ Each Data Link layer has its own frame format and limitation. ◦ One of such limitation is the maximum size of the frame, which is imposed by software, hardware, performance, and standards. MTUs for some networks Fragmentation of IP The source node usually does not fragment the packet. Instead, Layer 4 will segment the data into a size that can fit into Layer 3 and Layer 2 of the source. But, there is a possibility that a packet travel through a link whose MTU is smaller than one of the source node. ◦ Then, the packet must be fragmented to go forward the next hop. ◦ Each fragment has its own header mostly repeated from the original packet. ◦ A fragmented packet can be further fragmented into even smaller packet. ◦ Fragmented packets will be re-assembled at the final destination. Fields for Fragmentation Identification ◦ The source host generates the unique ID Flags (3-bits) ◦ Unused bit ◦ DF bit (Don’t Fragment) 1 – force the router not to fragment the packet. If the packet length is greater than the MTU, the router will discard the packet and send an error message to the source ◦ MF bit (More Fragment) 1 – tell the destination whether or not more fragments follow Offset ◦ Unit of 8-byte ◦ Allows a receiver to determine the place of a particular fragment in the original IP datagram, measured in units of 8-byte blocks. Header Checksum Used for error checking of the header. At each hop, the checksum of the header is compared to the value of this field. If a header checksum is found to be mismatched, the packet is discarded. IP Addresses: Classful Addressing BS IT 4th Semester By: Muhammad Hanif Remember ….. “The more you understand the less you have to remember.” Craig A. McCraw “Develop a passion for learning. If you do, you’ll never cease to grow.” Anthony J. D’Angelo Addressing IP Addresses: Classful Addressing Lecture overview IPv4 (IP version 4) Addressing For efficient routing, IP addresses are organized in Networks ◦ Classful addressing ◦ Subnetting ◦ Classless addressing IP addressing basics The Internet is used to “move” data from host to host All devices connected to the Internet must have a globally unique IP address ◦ No two devices can have the same public IP address ◦ This address can be permanent or temporary IPv4 addresses are 32 bits (= 4 octets) long ◦ This gives 2^32 ~ 4.29 billion addresses Notation IPv4 addresses can be written using the following notation ◦ Binary ◦ Dotted Decimal ◦ Hexadecimal Binary and Decimal Exercise 120.120.1.98 11111110. 10011010. 00110110. 00000101 Solution 120.120.1.98 11111110. 10011010. 00110110. 00000101 01111000 .01111000 .00000001. 01100010 254.154.54.5 Classful addressing IP addresses were divided into 5 classes: A,B,C,D and E ◦ This is the original scheme known as classful addressing ◦ From mid‐90’s, classless addressing is introduced ◦ However, classful addressing is still used Finding the class in binary notation Exercises 1. Find the class of these IP addresses: ◦ a) 11000001 10000011 00011011 11111111 ◦ b) 10000001 10000011 00011011 11111111 2. How many class B addresses are there altogether? 3. What is the range of class B addresses? Answer this by giving the first and last class B addresses in dotted decimal notation. Solution 1. a) First 3 bits are 110 ‐> Class C. b) First 2 bits are 10 ‐> Class B. 2. Class B addresses: the first two bits are 10 then followed by 30 bits of 1/0 2^30 addresses 3.The first and last class B addresses in binary are: ◦ 10000000 00000000 00000000 00000000 ◦ 10111111 11111111 11111111 11111111 In dotted decimal notation, they are: ◦ 128.0.0.0 and 191.255.255.255 Finding the class in decimal notation NetID and HostID IP addresses in classes A,B and C are divided into Netid and Hostid ◦ Netid: Identifying the network ◦ Hostid: Identifying a host within the network Hosts within a network ◦ Have the same netid ◦ But different hostid NetID and HostID Classes and blocks Classes and blocks Class A is divided into 128 blocks ◦ ◦ ◦ ◦ Each block has a different netid 1st block: 0.0.0.0 to 0.255.255.255 (netid = 0) 2nd block: 1.0.0.0 to 1.255.255.255 (netid = 1) Last block: 127.0.0.0 to 127.255.255.255 (netid = 127) Network address: the first address of the block Blocks in class A Blocks in class B Blocks in class C Use of addresses Classes A, B and C addresses can be assigned to hosts, router ports etc ◦ They are also known as unicast addresses Class D addresses are for multicast ◦ Multicast: One sender, multiple recipients Class E addresses are reserved for special purposes Network addresses The network address is the first address in the block The network address defines the network to the rest of the Internet ◦ Routers route packets based on network address Given the network address, we can find the class of the address and the range of the address in the block IP Version 6 (IPv6) BS IT 4th Semester By: Muhammad Hanif Challenges in Life…. Sharks and Fish The Japanese have always loved fresh fish. But the waters close to Japan have not held many fish for decades. So to feed the Japanese population, Fishing boats got bigger and went farther than ever.The farther the fishermen went, the longer it took to bring in the fish. If the return trip took more than a few days, the fish were not fresh.The Japanese did not like the taste. To solve this problem: ………………….. Challenges in Life… Sharks and Fish……….. To keep the fish tasting fresh, the Japanese fishing companies still put the fish in the tanks. But now they add a small shark to each tank. The shark eats a few fish, but most of the fish arrive in a very lively state. The fish are challenged. Have you realized that some of us are also living in a pond but most of the time tired & dull, So we need a Shark in our life to keep us awake and moving? Basically in our lives Sharks are new challenges to keep us active and lively. Some times blessings come in disguise! Agenda Why IPv6? IPv6 History IPv6 Addressing IPv6 Datagram Transition from IPv4 to IPv6 Motivations for IPv6 IPv4 addresses are running out IPv4 addresses are not enough Encryption and authentication not provided by IPv4 Conception of IPv6 Internet Protocol version 6 (RFC) ◦ Over 200 related RFCs IPv6 -RFC 2460 IPv6 Neighbor Discovery –RFC 2461 IPv6 Auto Configuration –RFC 2462 A new type of IP address A new type of IP packet What Happened to IPv5? 0 IP 1 IP 2 IP 3 IP 4 IPv4 5 ST 6 IPv6 7 CATNIP 8 Pip 9 TUBA 10‐15 March 1977 version January 1978 version February 1978 version A February 1978 version B September 1981 version Stream Transport December 1998 version IPng evaluation IPng evaluation IPng evaluation unassigned (deprecated) (deprecated) (deprecated) (deprecated) (current widespread) (not a new IP, little use) (formerly SIP, SIPP) (formerly TP/IX; deprecated) (deprecated) (deprecated) SIP = Simple Internet Protocol SIPP = Simple Internet Protocol Plus CATNIP = Common Address Technology for Next‐Generation IP , TP/IX = RFC 1475 Pip = Paul’s IP? RFC 1621 TUBA = TCP and UDP with Bigger Addresses , RFC 1347 Deprecated = Express strong disapproval What happened to IPv5 Version 5 in IP header was assigned to Streaming Protocol. Experimental non-IP real-time streaming protocol. Never widely used RFC 1819 Features of IPv6 Expanded address space: 128‐bit address (32‐bit for IPv4) Support for ◦ ◦ ◦ ◦ Real‐time service Mobile IP Security Note: Most of these services are added onto IPv4 but IPv6 must support them IPv6 addressing 128 bits means you can have 2^128 addresses, which is 340,282,366,920,938,463,463,374,607, 431,768,211,456 = 340 trillion trillion trillion addresses ◦ This is approximately 3.4 x 10^38 ◦ Compare with 4 x 10^9 IPv4 addresses, IPv6 has 10^29 times more Addresses ◦ 67 billion billion addresses per cm2 of the planet surface IPv6 address format 2001:0DA8:E800:0000:0260:3EFF:FE47:0001 8 groups of 4 hexadecimal digits ◦ Each group represents 16 bits ◦ Separator is “:” 51 IPv6 address format 2001:0DA8:E800:0000:0260:3EFF:FE47:0001 2001:DA8:E800:0:260:3EFF:FE47:1 2001:0DA8:E800:0000:0000:0000:0000:0001 2001:DA8:E800::1 52 IP Datagram IPv4 Header Header: from IPv4 to IPv6 Changed Removed IPv6 Header Format IPv6 header IPv6 header is simpler than IPv4 ◦ IPv4: 14 fields, variable length (20 bytes +) ◦ IPv6: 8 fields, fixed length (40 bytes) Header fields eliminated in IPv6 ◦ ◦ ◦ ◦ ◦ Header Length Identification Flag Fragmentation Offset Checksum Header fields enhanced in IPv6 ◦ Traffic Class ◦ Flow Label IP V6 Header Version –4 bits –Identifies the version of IP protocol 0100 (4) for IPv4 0110 (6) for IPv6 IP V6 Header Traffic Class –8 bits –Allows originating nodes and/or routers to distinguish between different classes or priorities of IPv6 packets QoS is an example implementation IP V6 Header Flow Label –20 bits –Used to “label” a flow of traffic. RFC 1809 “Using the Flow Label Field in IPv6” IP V6 Header Payload Length –16 bits –Length, in octets, of the payload Payload = 65536 bytes IP V6 Header Next Header –8 bits – Identifies the type of header immediately following the IPv6 header; Identifies the “extension” header immediately following Packet may have zero, one, or more extension headers IP V6 Header Hop Limit –8 bits –Maximum number of hops IPv6 packet can be forwarded. ◦ Similar to IPv4 TTL. IP V6 Header Source Address –128-bits ◦ versus IPv4 32-bit Destination Address –128-bits ◦ versus IPv4 32-bit Tunnelling Mechanisms How they work: ◦ Encapsulation of IPv6 packets within IPv4 packets and vice versa ◦ The tunnel's end point performs the necessary operations on the protocol: Reconnection of fragmented packets Packet forwarding in the IPv6 network ◦ Nodes performing the encapsulation and decapsulation operation have to be dual stack Transition Mechanisms Dual Stacks ◦ IPv4/IPv6 coexistence on one device Tunnels ◦ For tunneling IPv6 across IPv4 clouds ◦ Later, for tunneling IPv4 across IPv6 clouds ◦ IPv6 <‐> IPv6 and IPv4 <‐> IPv4 Translators ◦ IPv6 <‐> IPv4 IPv6 transition IPv6 tunnel over IPv4 IPv4 Network IPv6 IPv6 tunnel IPv4 Header IPv6 Header Data IPv6 Header Data IPv6 Header Data Tunneling IPv6 packets goes through IPv4 network IPv4 packets goes through IPv6 network Thank you