* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download LAN Systems
Distributed firewall wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Computer network wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
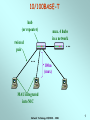
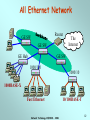
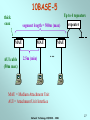
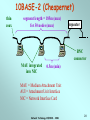
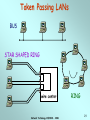
Network Technology CSE3020 Week 8 Network Technology CSE3020 - 2006 1 Local Area Networks (LANs) FDDI Contention Ethernet token passing polling Token ring Wireless LAN MAC protocols Star products topologies ring tree LAN standard bodies bus transmission media IEEE fiber twisted pair coax air (wireless) ISO, ATM Forum Network Technology CSE3020 - 2006 2 Ethernet (CSMA/CD) • Medium Access Control protocol is Carrier Sense Multiple Access with Collision Detection (CSMA/CD). Originally developed by Intel and Xerox as a part of Ethernet LAN. – Later used as a basis for the IEEE 802.3 LAN. • IEEE 802.3 Medium Access Control: – Random Access: • Stations access medium randomly. – Contention • Stations content for time on medium. Network Technology CSE3020 - 2006 3 CSMA/CD Operation • First listen for clear medium (carrier sense). • If the medium is idle, transmit. – If two stations start at the same instant, collision. • If busy, listen for idle, then transmit immediately – Stations continue to listen while transmitting • If a collision is detected, – transmit jamming signal then cease transmission. – after jamming, wait a random amount of time then start again. • Binary exponential back off: the mean value of the random delay is doubled with each repetition (reduce chance of collision). – After 16 unsuccessful attempts, the station gives up, and frame is discarded • Frame should be long enough to allow collision detection before end of transmission. Network Technology CSE3020 - 2006 4 CSMA/CD Operation Network Technology CSE3020 - 2006 5 Collision Detection • For twisted pair (extended star-topology) activity on more than one port of the hub is a collision. – Special collision presence signal is sent out to all stations to inform of collision. Network Technology CSE3020 - 2006 6 IEEE 802.3 Frame Format • Preamble: 7-octet pattern of alternating 0s and 1s for sync. • SFD: Sequence 10101011 to indicate the start of the frame. • DA and SA: Physical source and destination address. • Length/type: Length of LLC data in octets. • LLC PDU: supplied by LLC. • Pad: Added octets to ensure frame length for proper collision detection. • FCS: 32-bit CRC. Network Technology CSE3020 - 2006 7 Ethernet Specification • Concise notation of implementation (not always): < data rate (Mbps) > < Signaling method > < Max segment length (in 100m) > e.g.: 10Base5 & 10Base2 10Base5 10Base2 10/100Base-T 10Base-FP Medium Coaxial Coaxial UTP Fiber Signaling Baseband Baseband Baseband (Manchester) (Manchester) (Manchester) Manchester On/Off Topology Bus Bus Star Star Nodes 100 500 30 185 100 33 500 Max Length (m) Network Technology CSE3020 - 2006 8 10/100BASE-T hub (or repeater) max. 4 hubs in a network … twisted pair … 100m (max) MAU integrated into NIC Network Technology CSE3020 - 2006 9 Fast Ethernet (100Mbps) 100Base-TX Transmission 2 pair STP medium Maximum Segment Length (m) 100 2 pair, Cat. 5 UTP 100 Network Span (m) 200 200 Network Technology CSE3020 - 2006 100Base-FX 2 optical fibers 100 400 10 Gigabit Ethernet (1000 Mbps) 1000BASE-SX: Short wavelength (770nm to 860nm), multimode fiber. 1000BASE-LX: Long wavelength (1270nm to 1355nm), multi or single mode fiber. 1000BASE-CX: Copper jumpers (specialized shielded twisted-pair cable that spans no more than 25 m). 1000BASE-T: 4-pair cat. 5 UTP up to 100 m range. Network Technology CSE3020 - 2006 11 All Ethernet Network Router GE SW GE SW GE Hub The Internet GE SW 1000/100 1000/10 1000BASE-X Fast Ethernet Network Technology CSE3020 - 2006 10/100BASE-T 12 LAN Generations • First Generation: – CSMA/CD and token ring. – Terminal-to-host connectivity and client/server architecture. – Moderate data rates. • Second Generation: – FDDI. – Backbone LANs and high-performance workstations. • Third Generation: – ATM LANs. – Aggregate throughputs and real-time support for multimedia applications. Network Technology CSE3020 - 2006 13 Third Generation LANs • Support for multiple guaranteed classes of service. – Live video may need 2Mbps. – File transfer can use background class of service. • Scalable throughput. – Both aggregate and per host. • Facilitate LAN/WAN internetworking. >> ATM is ideally suited to these requirements. Network Technology CSE3020 - 2006 14 Backbone Networks • The role of a backbone network is to connect individual LANs. This also allows all users to access to a common resource (such as a printer, file server, or the Internet) • Issues to be considered: Unlike a LAN, a backbone network must deal with a large number of users. Traffic is aggregated from all LANs. Performance is important. Network Technology CSE3020 - 2006 15 Backbone Networks • The 2nd generation LANs (Fast Ethernet, Gigabit Ethernet) have higher data rate and can be used to build the backbone network. • Use asymmetric switches (operate at layer 2) to build extended star topology. Traffic is aggregated from bottom to top. Network Technology CSE3020 - 2006 16 Repeaters • A certain type of cables can only transport signals to a certain distance. Beyond the distance, the signals may be too weak to be decoded accurately. This limits the coverage of a LAN. • Repeaters are used to extend the coverage of a LAN due to its limitation in transmissions. • A repeater is operate at physical layer, it mostly deals with signal regeneration. They do not deal with the MAC frame format. Network Technology CSE3020 - 2006 17 Repeaters B A NET DL PHY PHY PHY NET DL PHY • Repeaters must forward signals to all output ports. Unnecessary signal forwarding may occur. • A certain MAC protocol may limit the number of repeaters used in a LAN (eg. Ethernet allows for only up to 4 repeaters). Network Technology CSE3020 - 2006 18 Bridges A D C Network LLC MAC Physical Relay MAC Physical MAC Physical Network LLC MAC Physical • Unlike repeaters, bridges are operated in Layer-2. They understand MAC frames. • Bridges are capable of: • Frame conversion (from one type to another). • Frame forwarding (to the destination). Network Technology CSE3020 - 2006 19 Multi-site LAN interconnection GW LAN Intersite Communication Facility GW LAN GW LAN • Gateway (GW) router operates at layer 3, can provide DHCP, DNS, Routing and Access control services. • Each LAN is a subnet with Multi-site Network (Intranet) •Inter-site Communication Facility – WAN Services provide by Telecommunications company Network Technology CSE3020 - 2006 20 Multisite LAN interconnection • WAN Services: • ISDN - Used for small enterprise networks (64 kbps) but mediumsized network requires multiple 64 kbps channels. • Frame relay - Multiplexing & routing of frames at link layer. - Supports up to 34 or 45 Mbps. • ATM •High bit rate leased lines -Supports intersite telephony traffic as well. - Either DS1/T1(1.5 Mbps) or E1 (2 Mbps) or higher. Network Technology CSE3020 - 2006 21 Required Reading • W. Stallings, Data and Computer Communications Prentice-Hall. Chapter 14 6E Chapter 16 7E Network Technology CSE3020 - 2006 22 The Following Slides are for Interest Only Network Technology CSE3020 - 2006 23 Precursors: ALOHA • Developed for packet radio networks. • When station has frame, it sends. – Station listens (for max round trip time)plus small increment. – If received ACK, fine. If not, retransmit the frame. – If no ACK after repeated transmissions, give up. • Frames includes frame check sequence (as in HDLC). – If frame OK and address matches receiver, send ACK. – Frame may be damaged by noise or by another station transmitting at the same time (collision) – frame is ignored. • Any overlap of frames causes collision, which increases rapidly with load. • Maximum utilization of the channel is 18%. Network Technology CSE3020 - 2006 24 Precursors: Slotted ALOHA • Time in uniform slots equal to frame transmission time. • Need central clock (or other sync mechanism) for all stations. • Transmission begins at slot boundary. • Frames either miss or overlap totally. • Maximum utilization of the channel is 37%. Network Technology CSE3020 - 2006 25 CSMA • Propagation time is much less than transmission time. – All stations know that a transmission has started almost immediately. • First listen for clear medium (carrier sense). • If the medium is idle, transmit. – If two stations start at the same instant, collision. – Wait reasonable time (round trip plus ACK contention) and if no ACK then retransmit. • Max utilization depends on propagation time (medium length) and frame length. – Longer frame and shorter propagation gives better utilization. • If the medium is busy: – Listen for idle medium then transmit immediately. – If two stations are waiting, a collision will occur. Network Technology CSE3020 - 2006 26 10BASE-5 Up to 4 repeaters thick coax segment length = 500m (max) MAU AUI cable (50m max) MAU 2.5m (min) repeater MAU … MAU = Medium Attachment Unit AUI = Attachment Unit Interface Network Technology CSE3020 - 2006 27 10BASE-2 (Cheapernet) thin coax segment length = 185m (max) for 30 nodes (max) repeater BNC connector MAU integrated into NIC 0.5m (min) MAU = Medium Attachment Unit AUI = Attachment Unit Interface NIC = Network Interface Card Network Technology CSE3020 - 2006 28 Token Passing LANs BUS STAR SHAPED RING wire center Network Technology CSE3020 - 2006 RING 29 Token Ring (802.5) • Most commonly used MAC protocol for ring topology LAN. • Small frame (token) circulates when stations are idle. – Station waits for the token. – Changes one bit in token to make it a start-of-frame sequence for data frame. – Appends the rest of the data frame. – Frame makes round trip and is absorbed by transmitting station. – Station then inserts new token when transmission has finished and leading edge of the returning frame arrives. – Once a new token inserted, the next station downstream may transmit. Network Technology CSE3020 - 2006 30 Token Ring (802.5) • Under light loads, some inefficiency: must wait for token. • Under heavy loads, efficient and fair: round robin fashion. • Advantages: flexible and fair control, can provide priority and guaranteed bandwidth services. • Disadvantages: Token maintenance (to prevent loss or duplication of token). Network Technology CSE3020 - 2006 31 Token Ring Operation • A sends a packets to C (1-5). • C then sends packets to A and D (6-9). • In this example, packets are shorter than link length. A new token is released when packet arrives back at the transmitter. Network Technology CSE3020 - 2006 32 Token Ring MAC Frame Network Technology CSE3020 - 2006 33 Priority Scheme Network Technology CSE3020 - 2006 34 Token Ring Extensions • Early Token Release (ETR): – If the bit length of the ring is less than that of a frame: • the transmitter release a token as soon as the frame is sent. – Otherwise: • Must wait for the frame header to return before issuing a token. • Some of the potential capacity is unused. – ETR allows the transmitter to release a token as soon as the frame is sent. – Priority mechanism is partially disabled. Network Technology CSE3020 - 2006 35 Token Ring Extensions • Dedicated Token Ring (DTR): – Token passing algorithm in star topology using a central hub or concentrator. – Central hub functions as a switch so that the connection is full-duplex point-to-point link. – Concentrator acts as frame level relay rather than a bit-level repeater. – Dedicated link with immediate access. – No token passing. Network Technology CSE3020 - 2006 36 IEEE 802.5 Physical Layer Data Rate (Mbps) 4 16 100 Medium UTP, STP, Fiber Differential Manchester UTP, STP, Fiber Differential Manchester UTP, STP, Fiber MLT-3 or 4B5B/NRZI 4550 18,200 18,200 TP or DTR TP or DTR DTR Signaling Max Frame Size (octets) Access Control TP = Token Passing access control: DTR = Dedicated Token Ring Network Technology CSE3020 - 2006 37 Fiber Distributed Data Interface (FDDI) • Token Ring scheme similar to IEEE 802.5 specifications. • Designed for LAN and MAN applications at higher data rate (100Mbps). • Key differences in FDDI MAC protocol from IEEE 802.5 are: – Station seizes token by aborting token transmission. – Once token captured, one or more data frames are transmitted. – New token released as soon as transmission finished (early token release in 802.5). Network Technology CSE3020 - 2006 38 FDDI MAC Frame Format Network Technology CSE3020 - 2006 39 FDDI Operation Network Technology CSE3020 - 2006 40 FDDI Physical Layer Medium Optical Fiber Twisted Pair Data rate 100 Mbps 100 Mbps Signaling 4B/5B/NRZI MLT-3 Max repeaters 100 100 Between repeaters 2km 100m • Two rings run on fibers or twisted pair. - Primary ring - Secondary ring • A station can be configured as a Single Attach Station (SAS) or Dual Attach Station (DAS). Network Technology CSE3020 - 2006 41 FDDI: Topology FDDI SAS primary ring SAS (bypass mode) wiring concentrator DAS (bypass mode) DAS secondary ring primary ring Network Technology CSE3020 - 2006 42 FDDI Fault Tolerance Normal operation: Link failure: Network Technology CSE3020 - 2006 43 ATM LANs • Asynchronous Transfer Mode (ATM) uses virtual paths and virtual channels. • Multiple classes of services are easily accommodated either in preconfigured fashion or switched connections. • Easily scalable by adding more ATM switches or devices. • Seamless integration of LANs and WANs. • Possible types of ATM LANs are: – Gateway to ATM WAN: • ATM switch acts as a router and traffic concentrator. – Backbone ATM switch: • Single ATM switch or local network of ATM switches. – Workgroup ATM. • End systems connected directly to ATM switch. • In practice, mixed system. Network Technology CSE3020 - 2006 44 Example: ATM LAN Network Technology CSE3020 - 2006 45 Example: ATM LAN HUB Network Technology CSE3020 - 2006 46 ATM LAN: Compatibility • Interaction between end system on ATM and end system on legacy LAN. • Interaction between stations on legacy LANs of same type. • Interaction between stations on legacy LANs of different types. Network Technology CSE3020 - 2006 47 Backbone Networks: Shared versus Switched • A shared LAN is usually low in cost, but low in performance. It is suitable for connecting a small number of LANs that do not use the network intensively. • A switch is usually high in cost, but high in performance. It is suitable for building a large backbone dealing with a large number of users. Network Technology CSE3020 - 2006 48