* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download OSI vs TCP/IP models
Wireless security wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Distributed firewall wikipedia , lookup
Deep packet inspection wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Computer network wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Network tap wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Airborne Networking wikipedia , lookup
Internet protocol suite wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
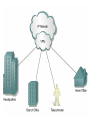
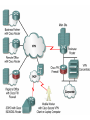
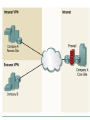
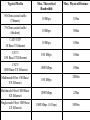
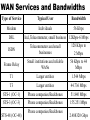
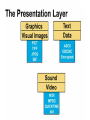
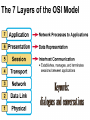
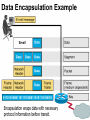
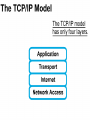
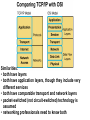
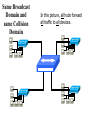
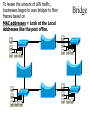
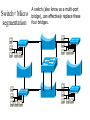
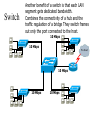
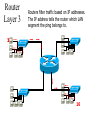
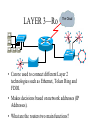
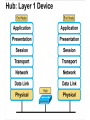
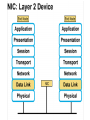
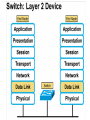
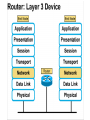
Networking Fundamentals John Bellavance CCNI Data Networks Developed because companies wanted to exchange info over long distances. At first they used sneakernet, but sharing data using floppy disks was not efficient. •The solution was to network the resources (printers,servers) to increase productivity and save money. •Companies in the 80s created a variety of network software and hardware, with their own standards. As a result they were incompatible with each other. Internetworking History One solution was to create LAN (Local Area Network) standards which provided guidelines for creating hardware and software.. ENIAC – the first large scale electronic digital computer, weighed 30 Tons. 1947 – Transistors (tiny ON/OFF switches) were invented at Bell labs. 1976 - APPLE II – Starts the PC Revolution Network Protocols Protocol suites are collections of protocols that enable network communication between hosts. A protocol is a formal description of a set of rules and conventions that govern how devices on a network communicate.Protocols determine the format, timing, sequencing, and error control of data communication. Without protocols the computer cannot create or rebuild the stream of incoming bits from another computer into the original data.These network rules are created and maintained by many different organizations, such as IEEE, ANSI, TIA. LANs – Operate in a limited geographical area. Allow many users to access high-bandwidth media Provide full-time connectivity to local services. Connect physically adjacent devices Ex: Ethernet, Token Ring, FDDI WANs (Wide Area Networks) WANs interconnect LANs. They make it possible for businesses to communicate across great distances. WANs create a new class of workers called Telecommuters – never leave home to go to work. •Operate over large geographically separate areas. Allow users to engage in real-time communication with other users. Provide full-time remote resources connected to local services. Provide e-mail, WWW, file transfer and e-commerce services. •Ex: Modems, ISDN, DSL, Frame Relay, T or E carrier. MANs (Metropolitan-Area Networks) Spans a city and connects LANs, for example a bank with several branches might use a MAN. Rowville SC is a MAN using a wireless link. The MAN interconnects users is a geographic area lager than the LAN. MANs interconnect several LANs by bridging them with backbone lines. Specialized Networks Located within the LAN •Storage-Area Networks (SANs)- is a high performance link between server-to-storage, storage-to-storage, or server-to-server. •SANs offer Performance- allow access to disk or tape arrays by two or more servers at high speed. Availability- disaster tolerant using mirrored disks. Scalability- uses a variety of technologies and allows easy relocation. DATA CENTER – is a globally coordinated network of devices designed to accelerate the delivery of information over the Internet infrastructure. Service providers can use these services and avoid congestion by distributing the load. The Data Center can deliver the download of a movie over the Internet much quicker. The Internet Business Exchange™ Center – Critical Hubs in the Core Infrastructure of the Internet. Our Internet Business Exchange™ (IBX®) centers serve as core hubs for critical IP networks and Internet operations worldwide. With direct access to more than 200 networks, network and Internet operations through direct interconnection to the largest aggregation of networks for unmatched service diversity, flexibility and reliability. At Equinix, customers can directly access the providers that serve over 90% of the world's Internet networks and users. Intranets- Intranet server are different than public web servers, in that the public does not have access to the organizations intranet. Extranets- is and intranet that is partially accessible to authorized outsiders with a password and username. Virtual Private Networks (VPN) – is a private network constructed within a public network infrastructure like the Internet.The the telecommuter can access the company headquarters’ network through the Internet by building a secure tunnel between and PC and a VPN router in the headquarter. •Access VPNs- provide access to remote user using dial-up, ISDN, DSL. •Intranet VPNs- allow access to employees only. Extranet VPNs- allow access to users outside the organization. Advantaged: Allow privacy and security, encryption for clients(Bank) and allow employees access to the corporate network securely. Digital Bandwidth is the measure of how much information can flow from one place to another in a given amount of time Bandwidth is finite- there are limitation set by the laws of physics, DSL uses the same copper wires for voice but use a frequency range that is wider and therefore DSL ca send more bits per second than modems. Bandwidth is not free- a service provider charges and you need to make the right decisions about services and equipment. Bandwidth is key to analyze network performance and designing networks Demand for bandwidth is ever-increasing- new applications are always created, voice over IP, so we need to anticipate the need for more bandwidth. Pipe Analogy for Bandwidth Highway Analogy for Bandwidth Bandwidth is measured in bit per second. Bandwidth varies depending on the type of medium as well as the LAN and WAN technologies used. The physics of the medium, be it twisted pair copper, coaxial cable or fibre optic cable influences the limitations of the capacity to carry data. Ex; UTP limit is 1 Gbps. Bandwidth determined also by the equipment, the number of users, the amount of broadcasts and so on. Digital Bandwidth Versus Analog bandwidth Until recently, radio and television were sent through the air using analog electromagnetic waves which are measured in Kilohertz and Megahertz. Digital bit streams can carry video, voice and data unlimited amounts of data can be sent over the smallest (lowerbandwidth) digital channel. When digital info arrives at its destination it can be reassembled, viewed and listened to in its original form. Typical Media Max. Theoretical Bandwidth Max. Physical Distance 50-Ohm coaxial cable (Thinnet) 10 Mbps 185m 75-Ohm coaxial cable (thicknet) 10 Mbps 500m CAT5 UTP 10 Base-T Ethernet 10 Mbps 100m CAT 5 100 Base-TX Ethernet 100 Mbps 100m CAT 5 1000 Base-TX Ethernet 1000 Mbps 100m 2000m Multimode Fiber 100 BaseFX Ethernet 100 Mbps Multimode Fiber 1000 BaseSX Ethernet 1000 Mbps 220m Singlemode Fiber 1000 base LX Ethernet 1000 Mbps (1 Gbps) 5000m WAN Services and Bandwidths Type of Service Typical User Bandwidth Modem Individuals 56 Kbps DSL Ind.,Telecommuter, small business 12Kbps-6 Mbps ISDN Telecommuters and small businesses Frame Relay Small institutions and reliable WANs 128 Kbps to 2 Mbps 56 Kbps to 44 Mbps T1 Larger entities 1.544 Mbps T3 Larger entities 44.736 Mbps STS-1 (OC-1) Phone companies/Backbones 51.840 Mbps STS-3 (OC-3) Phone companies/Backbones 155.251 Mbps STS-48 (OC-48) Phone companies/Backbones 2.488320 Gbps Data Throughput Bandwidth is the measure of the amount of info that can move through the network at any given time. Throughput refers to the actual, measured bandwidth at a specific time of day using specific Internet routes while downloading a specific file Throughput is often less than the maximum possible bandwidth. a major factor in analyzing a network’s performance Data Transfer Calculations Divide the file size by the network bandwidth yields an estimate of the fastest time. The result is only an estimate, because the file size does not include any overhead added by the encapsulation process. File: 100 Mbytes * 8 = 800 Mbits / 100 MBitsps = 8 sec. Learning a concept of layers helps us understand how data flows (how data flows, how traffic flows and the rules of flow) and how computers communicate with each other. An example of flow is the Electrical or water networks. Each layer has a specific tasks and uses specific protocols. This layered communication process each layer performs a specific task. We will see how the network communication process is broken into a layered model. We will see how data is sent out over the network to reach its destination and the steps involved. This is helpful when troubleshooting. For computers to send information through a network, communication originates from a source to a destination. Before data can be sent across a network it must first be broken into smaller chunks.(Data Packets, data segments or data frames) before data can be sent in the form of electrical impulses, it must first be broken into manageable chunks. This includes a source and destination address (like a letter) to make communication possible. Computer Protocols • For data packets to travel from source to destination, all devices on the network must speak the same language. • Network protocol: A set of rules that make communication on a network possible and efficient. • Eg: While driving a car, other cars (should!) signal when they wish to make a turn; if they did not, then the roads would be chaos Networking Standards IOS International Organization for Standards. Proprietary systems were created that were privately developed, owned and controlled. This did not work well with other systems. Open means that free usage of the technology is available to the public. To address the problem of different networks systems being incompatible with each other, the International Organization for Standardisation (IOS) researched network schemes to find a set of rules. As a result the IOS created the OSI Model Open System Interconnection Reference Model, this allowed network vendors to create networks that would be compatible with other networks. The IEEE sets standards for networking technologies at Data Link and Physical Layers. The Purpose of the OSI Reference Model The primary objective of he OSI model is to accelerate the development of future networking products. The OSI reference model allows you to view the network functions and how information travels through a network and what occur at each layer. Why A Layered Model? • Reduces complexity- Breaks network communication into smaller parts, making it easier to develop. • Standardizes interfaces- facilitates standardization of network components • Facilitates modular engineering- (development can be made in a modular fashion- Changes in one does not effect another Lay). • Ensures interoperable technology- allows different network hardware and software to communicate with each other. • Accelerates evolution • Simplifies teaching & learning- by breaking it up into smaller parts • Easy troubleshooting All People Seem To Need Data Processing The OSI Reference Model Each layer has a unique function. 7 Application 6 Presentation 5 Session 4 Transport 3 Network 2 Data Link 1 Physical User interface Data presentation and encryption Keeping different applications’ data separate End-to-end connections Addresses and best path Access to media Binary transmission Application Layer Application Presentation Session Transport Network Data-Link Physical – Closest to the user and does not provide services to any other layer. – Provides network communication services to applications which allow for the transfer of files(word), Bank transactions. Network redirectors allow applications like Word and Excel to “see” the network. – Responsible for identifying and establishing the availability of communication partners and if there are sufficient resources for communication. Makes sure that appropriate resources are available to initiate a connection with destination host. – Synchronizes and establishes an agreement on procedures for error recovery. – Ex:Email, HTTP, telnet, FTP, SNMP. Presentation Layer – Provides data representation and code formatting. Translates Application between multiple data formats. Presentation – Basically, the presentation layer is Session responsible for representing data so that the source and destination Transport can communicate at the Network application layer. Data-Link – Compression and encryption Physical – Ex: Ascii, Jpeg, Tiff, sound and movie files. Session Layer Application Presentation Session Transport Network Data-Link Physical – Provides inter-host communication by establishing, maintaining, and terminating sessions between applications. – Synchronizes dialogue between 2 hosts presentation layers and manages their data exchange. Session uses dialog control and dialog separation to manage the session parameters and login. – Some Session protocols: • • • • • • NFS (Network File System) Sun/Unix SQL (Structured Query Language) define database info requests RCP (Remote Call Procedure) ASP (AppleTalk Session Protocol) SCP (Session Control Protocol) X-window- Unix Controls sessions, by determining which flows are part of the same sessions and which must be completed before it is considered complete. Transport Layer- boundary between application protocols and data-flow protocols Application Presentation Session Transport Network Data-Link Physical – Connection Oriented -Controls communication between end-to-end hosts using pre-established pathing. – Sets up session establishment and tears down VCs. TCP provides the ability of multiple applications to use a single transport (Multiplexing) – Reliability and Error Recovery- TCP segments and reassembles the data, adding a header with control information for sequencing and acknowledging packets received. – The segment header also includes source and destination ports for upper-layer applications – Flow control using- windowing, buffering and source quench messages (sent by the recipient when the buffers (memory) are nearing capacity) – TCP uses 3 way handshake- synchronizes sequence number between hosts. Transport Layer UDP is connectionless. UDP does not acknowledge the receipt of packets, no sequencing, no virtual circuit creation, no guarantee delivery but less overhead. Provides error detection but not recovery. TCP uses 3 way handshake- synchronizes sequence number between hosts, provides reliability by establishing a communication session before sending data (Virtual Circuit) Provides error detection and recovery. The transport layer attempts to provide a data transport service that shields the upper layers from transport implementation details. Network Layer Application Presentation Session Transport Network Data-Link Physical – Provides connectivity and path selection(path determination and switching). – Connectionless, and Responsible for logically addressing the packet – Addressing is done through routed protocols such as IP, IPX, AppleTalk – Path Selection is done by using routing protocols such as (RIP, IGRP are classfull routing prot. Do not include subnet mask in routing update), EIGRP, OSPF, and BGP. – Routers operate at the Network Layer, ICMP(traceroute and ping), ARP(DHCP), RARP (diskless workstations) operate at this layer. – Fragments data into smaller packets to accommodate smaller MTU size (Maximum Transmission Units) Data-Link Layer Application Presentation Session Transport Network Data-Link Physical – Handles error notification, network topology issues, and physically addressing the frame. – Media Access Control -Provides the transit of data across a physical link. Access to the media using a physical address called a MAC address (48 bits) two part address- 3 bytes OUI, 3 for serial number. – Flow control and error detection. – through either... • • Deterministic—token passing Non-deterministic—broadcast topology (collision domains) – Important concept: CSMA/CD – LLC provides SAPs (service access points) for upper layers, flow control DATA-LINK Prepares data from upper layers to be transmitted over a particular physical medium, the final encapsulation. Convert data into bits, so it can be transmitted by physical layer. Error detection: CRC Cyclical Redundancy Check or FCS Frame check sequence, if an error is detected the frame is discarded. Frame Relay, HDLC, PPP encapsultions. Ethernet , Token Ring 802.5 Physical Layer Application Presentation Session Transport Network Data-Link Physical – Provides electrical, mechanical, procedural and functional means for activating and maintaining links between systems. Like voltage levels, timing, physical data rates (100 Mbps), maximum transmission distances (100 meters). – Standards for sending data over the physical medium through which bits flow. Media types:IEEE • Connectors-Ethernet 802.3 CAT 5 cable, RJ45 jacks. • Coaxial cable • Fiber Optics cable FDDI Fiber Distributed Data Interface • The atmosphere The OSI Reference Model 7 Application 6 Presentation 5 Session 4 3 2 1 The top 3 layers are known as the application layers because they deal with the user interface, data formatting, and the application access. The OSI Reference Model 7 Application 6 Presentation Data Transport 5 Session Layers 1-4 are known as the data flow layers because they control the physical delivery of messages over the network and how data is transferred. 4 Transport 3 Network 2 Data Link 1 Physical For data to travel from source to destination, each layer at the source must communicate with its peer layer at the destination, this is called Peer-To-Peer communication. During this process, the protocols at each layer exchange information, called Protocol data Units (PDU) between each layer.each layer depends on the services of the one below it. If a computer wants to send data to another it must package the data for delivery, this is encapsulation. Encapsulation wraps data with the necessary protocol information before network transit. Encapsulation wraps data with necessary protocol information before transit. How Data is Encapsulated 1. Build the data. 2. Package the data for end-to-end transport. 3. Append (add) the network address to the header 4. Append (add) the Physical address to the data link header. 5. Convert to bits for transmission. De-Encapsulation Headers are looked at at each layer and removed. 1-Read the physical address MAC, strip it off the header and the trailer, creating a packet and passed on to upper-layers. 2- If there are errors, discard the data or ask for retransmission. Each layer depends on the services of the other below it. To provide this service, the lower layers uses encapsulation to put the PDU from the upper layer into its data field; then adds whatever header and trailer is needed. The Importance of TCP/IP The U.S. Department of Defense (DoD) created the TCP/IP reference model. The open standard for the Internet is TCP/IP. Makes communication possible between any computers on earth. The DOD wanted packets to get through every time, under any conditions. The TCP/IP model has only four layers. Common TCP/IP Protocols • Application Layer • Transport Layer • Internet Layer • Network Access Common TCP/IP Protocols • FTP - File Transfer Protocol • HTTP - Hypertext Transfer Protocol • SMTP - Simple Mail Transfer protocol • DNS - Domain Name System • TFTP - Trivial File Transfer Protocol Common TCP/IP Protocols The transport layer involves two protocols transmission control protocol (TCP) and user datagram protocol (UDP). Similarities: • both have layers • both have application layers, though they include very different services • both have comparable transport and network layers • packet-switched (not circuit-switched) technology is assumed • networking professionals need to know both Networking Devices •End User Devices(Hosts) – Include computers, scanners, printers. •Network Devices – Include all devices that allow end user devices to communicate. Hosts devices are physically connected to the network media using a Network Interface Card (NIC) •Install a NIC card in the motherboard expansion slot. On a laptop, the NIC is usually the size of a PCMCIA card NIC Specifics • NICs provide hosts with access to media by using a unique code called a MAC address. This address is used to control data communication on the network. • The NIC controls the hosts access to the media. • MAC stands for Media Access Control • NICs operate at Layer 2 !! • It translates the parallel signal of the PC into a serial format sent over the network cable. • I converts 0s and 1s into an electrical signal, pulses of light or radio waves. LAYER 1—Repeater • Cleans up (regenerates) and retimes the signal at the bit level. • Used when a network’s cabling extends beyond its capability. UTP is 100 meters. NICs, Repeaters, & Hubs Repeaters can be used to increase the distance NIC NIC So what can we use if this distance is greater than 100 meters? What’s the maximum distance for Cat 5 cable? 100 meters When the signals leave the host they are strong. The longer the cable length, the weaker and more deteriorated the signal becomes. Repeaters amplify and retime signals at the bit level to allow them to travel longer distances on the media. LAYER 1—Hub (multi-port repeater) The Cloud • Simply a multi-port repeater. Active and passive hubs. • Used to connect multiple devices, the hub acts as the centre of the physical star, yet same contention as a bus. • Token Ring Hub-is called a MAU (Media Attachment Unit) FDDI is a concentrator. Same Broadcast Domain and same Collision Domain In this picture, all hubs forward all traffic to all devices. To lessen the amount of LAN traffic, businesses began to uses bridges to filter frames based on MAC addresses = Look at the Local Addresses like the post office. Bridge LAYER 2—Bridge • Connects two LAN segments and pass frames. • Build tables of all Mac addresses on the network. • Keeps traffic local by filtering traffic based on MAC Addresses contained in the layer 2 Frame. Creates more usable bandwidth.the bridge keeps track of MACs on each side of the bridge and filters traffic based on MAC addresses only. • SEGMENTATION = Creates separate or more collision domains. Switch= Micro segmentation A switch (also know as a multi-port bridge), can effectively replace these four bridges. Switch Another benefit of a switch is that each LAN segment gets dedicated bandwidth. Combines the connectivity of a hub and the traffic regulation of a bridge They switch frames out only the port connected to the host. 10 Mbps 10 Mbps The Cloud 10 Mbps 10 Mbps 10 Mbps Router Layer 3 Routers filter traffic based on IP addresses. The IP address tells the router which LAN segment the ping belongs to. 1 16 The Cloud LAYER 3—Router • Can be used to connect different Layer 2 technologies such as Ethernet, Token Ring and FDDI. • Makes decisions based on network addresses (IP Addresses). • What are the routers two main functions? Router’s Two Main Functions • Path Determination • Packet Switching • Operate at Layers 1, 2 AND 3 Other Devices Gateways – Is an Access Server combining routing, remote access, voice gateway, firewall and a digital modem. DSLAM ( Digital Subscriber Line Access Multiplexer) – Is a DSL box giving you access to the carrier netwok. CMTS ( Cable Modem Termination System) used by cable operators as a concentration point or hub in the cable network to provide highspeed Internet access. This would be used in a hotel or apartment building. Optical Platforms – Used as backbone and WANs for fibber backbone. Firewalls – Is either a firewall running on a router or server or a standalone hardware device on a network. AAA server – is a program that handles user requests for access to network resources. They provide authentication, authorization and accounting (who is doing what) VPN concentrators – offer remote access and site-to-site VPN capabilities. Wireless NICs - Have built in antennas. Wireless Access Points – is a wireless transceiver that acts as a hub. Wireless Bridge – provides high-speed ( 11 Mbps) and long range line of sight wireless connectivity (up to 25 Miles) Network Topologies – are defined how computers, printers and other network devices are connected. It defines the physical layout of wires as well as the paths used for data transmission. Network have both Physical and Logical topologies. The physical refers the the layout of devices and the media (cables). Logical defines how the media is accessed by the hosts fro sending data. Bus Ring Star Mesh • Single backbone Bus Topology • All devices are directly connected to a central cable. • Each end of the bus must be properly terminated to absorb electrical signals, so they don’t bounce around. Star Topology • All nodes connected to a central device • Center of star is usually a hub or a switch • Used for Ethernet technologies. • Each device is connected to a central device with its own cable, so if one device has a problem with a bad cable, only that device will be affected. But if the centre of the star fails the whole network will fail. Extended Star Topology • Connects individual star topologies together. • At the center of the star is a hub or a switch. • Extends the length and size of the network. Ring Topology • No backbone • A host is directly connected to each of its neighbors • Used for token passing logical topologies. Two types of rings exist: Single and Dual ring. In a dual ring the 2 rings allow data to be sent in both directions, this type of setup creates redundancy (fault tolerance). Hierarchical Topology Server • Like the extended star except a computer controls traffic—not a hub or a switch. Mesh Topology like the Internet • Each host has its own connection to every other host for redundancy. • Used in situations where communication must not be interrupted. Usually to connect routers in a WAN. Logical Topologies • Broadcast Topology – Each host on the LAN sends its data (or broadcasts its data) to every other host. – Access to media is based of “first-come, firstserve.” (Ethernet works this way) • Token Passing Topology – Access to media is controlled by an electronic token. – Possession of the token gives the host the right to pass data to its destination.