* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download DOS Defenses - Dr. Stephen C. Hayne
Survey
Document related concepts
Transcript
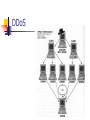
Denial of Service BD 480 This presentation is an amalgam of presentations by Mark Michael, Randy Marchany and Ed Skoudis. I have edited and added material. Dr. Stephen C. Hayne Denial-of-Service Attacks Description Stopping vs. Exhausting Services Local vs. Remote Smurf Attacks DDoS (Distributed Denial-of-Service Attack) DoS Defenses Conclusion Other Resources DoS An explicit attempt to prevent users of a service to use that service. An attacker can attempt to… “flood” a network Disrupt connections between two machines Prevent a particular user from accessing a service Disrupt service to a specific system Stopping vs. Exhausting Resources STOPPING SERVICES • Process Killing LOCALLY ATTACK IS LAUNCHED... REMOTELY (across the network) • System reconfiguring • Process crashing • Malformed packet attacks (e.g., Land, Teardrop, etc.) EXHAUSTING RESOURCES • Forking processes to fill the process table • Filling up the whole file system • Packet floods, (e.g, SYN Flood, Smurf, Distributed Denial of Service Figure 9.1 Denial-of-Service attack categories. Skoudis p. 375 Stopping vs. Exhausting Resources Stopping Crashing a server that a user wants to access Shutting off a server that a user wants to access Exhausting The server itself is still running Attacker consumes computer or network resources Prevents legitimate users from accessing a service Local vs. Remote Stopping Local Resources Using a local account on a machine An attacker with root privileges (UNIX System) can shut down the inetd process Result: Any user cannot access any service started with inetd: Telnet, FTP Three Methods Process Killing Stopping local processes Web or DNS Server Super User Priviledges System Reconfiguration Reconfigure system files to not allow file sharing(FTP) Stop a HTTP daemon from starting Can prevent Web access Process Crashing Input arbitrary large amounts of random data Since return pointer on the stack is pushed on the stack the target process will crash Denying user access Local vs. Remote Exhausting Resources An attacker can run a program that attacks that target machine by grabbing the system resources When all systems are exhausted, the machine may stop Three Methods Filling up the Process Table A program that makes another process run a copy of itself This program will then continue to run another copy of itself Process table will eventually become filled Stop users from running processes Deny users access Three Methods Filling up the File System Continuously write enormous amounts of data to the file system Fill up every available byte on the disk partition Other users can't write files Potentially crash the system Three Methods Sending outbound traffic that fills up the communication link Write a program that sends bogus network traffic Network traffic will consume the processor and the link bandwidth Users will not be able to send or receive network traffic Local vs. Remote Remotely Stopping Resources More prevalent Attacker doesn't need a local account Can be launched from attacker's machine Popular Attacks Malformed Packet attack Attack exploits and error in the TCP/IP stack of target machine Sending one or more malformed packet will crash a target machine Remotely Stopping Resources Famous Exploits Land Latierra Ping of Death Jolt2 Teardrop Winnuke Exploits Land Similar to SYN flooding The attacker floods SYN packets into the network with a spoofed source IP address of the targeted system. Exploits Ping of Death Taking advantage of a known bug in TCP/IP implementation. The attacker uses the ping system utility to make up an IP packet that exceeds the maximum 65,536 bytes of data allowed by the IP specification. Systems may crash or reboot when they received such an oversized packet. Exploits Teardrop Attack exploiting a weakness in the reassembly of IP packet fragments. Attacker creates a sequence of IP fragments with overlapping offset fields. Some systems will crash or reboot when they are trying to reassemble the malformed fragments. Remotely Exhausting Resources SYN Flood Goal is to overwhelm the destination machine with SYN packets Exploits the Three-way handshake Sends a larger number of SYN packets Requires target machine to generate a large number of SYN-ACK responses When the target machine receives more SYN packets than it can handle other legitimate traffic cannot reach the target machine SYN Flood Fill the connection queue with half-open connections while target machine waits for third part of handshake Send more SYN packets Target machine will allocate a small amount of resources to remember each SYN packet as it is transmitted (Two Methods) Filling up the queue with SYN packets will not allow other incoming traffic Best to use a Spoofed IP address that are unresponsive on the Internet SYN Flood (Two Methods) Have a communication link bigger than the target machines communication link SYN flood will just squeeze out other traffic Smurf Attacks a.k.a. Directed Broadcast Attacks Relies on a directed broadcast to create a flood of traffic Sends a common ping Target returns a ICMP echo request Smurf Attacks Smurf Attacks Send a common ping with a spoofed IP address (Target Machine IP address) to a network Network (Smurf Amplifier, misconfigured network) will send a flood of ICMP echo request to target machine Will exhaust target machine DDoS (Distributed Denial-of-Service Attacks) Attacking a large number of hosts at once Harnesses the distributed nature of the Internet Requires a large number of victim machines (Zombies) Client machines will tell all “zombies” to execute a command Victim gets flooded with thousands of packets DDoS DDoS Attacker will scan a large number of networks looking for vulnerable machines Installs zombie software on exploited machine (TFN2K*, Tribe Flood Network…) Achieved with a buffer overflow Evolution as described at TFN3K * CERT Advisory CA-1999-17 Denial-of-Service Tools DoS Defenses Implement router filters Install patches to guard against TCP SYN flooding Disable any unused or unneeded network services Observe your system performance and establish baselines for ordinary activity Routinely examine your physical security with respect to your current needs Zombie Zapper DoS Defenses Invest in and maintain "hot spares" machines that can be placed into service quickly in the event that a similar machine is disabled Invest in redundant and fault-tolerant network configurations Establish and maintain regular backup schedules and policies Establish and maintain appropriate password policies Other Resources Denial-of-Service Attacks CERT® Coordination Center http://www.cert.org/tech_tips/denial_of_service.html Denial-of-Service Tools CERT® Advisory CA-199-17 Denial-of-Service Tools http://www.cert.org/advisories/CA-1999-17.html Types of DoS Attacks University of Texas http://www.cs.utexas.edu/users/chuang/dos.html