* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download IPSec VPN`s
SIP extensions for the IP Multimedia Subsystem wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Extensible Authentication Protocol wikipedia , lookup
Distributed firewall wikipedia , lookup
Wireless security wikipedia , lookup
Internet protocol suite wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Computer security wikipedia , lookup
Deep packet inspection wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
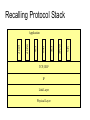
Introduction to IPSec Overview of Presentation • Introduction – – – – The Internet Model and Threats Solutions Possible Security Measures at Various Layers IPsec: security at network layer • How IPsec works – – – – IPsec model Authentication Header Encapsulating Security Payload Internet Key Exchange • Limitations of IPsec • Conclusions Introduction • Original Design Model for Internet – The model of Internet was made for a more benign environment like academia – All data on Internet was free to all and anyone could share or modify the data – Since the some etiquette was being observed by the limited Internet community, security was hardly an issue – Internet has grown beyond academia Introduction (contd.) • In present scenario, Internet enables instant ondemand business by – Establishing communication links with suppliers and business partners – By eliminating the need for costly wide area network dedicated lines – Enabling remote access to corporate networks using many available Internet service providers • One of the main stumbling blocks to achieve these benefits is lack of security (besides, reliability, quality of service among others) Internet Threats • The varied nature of Internet users and networks has brought the security concern • To ratify the fears several threats have surfaced, such as, – – – – – Identity spoofing Denial of service Loss of privacy Loss of data integrity Replay attacks Internet Threats (contd.) • Identity spoofing – Executing transactions by masquerading • Denial of service – Preventing a service provider by flooding with fake requests for service • Loss of privacy – Eavesdropping on conversations, database replies etc • Loss of data integrity – Modifying data in transit to disrupt a valid communication • Replay attacks – Using older legitimate replies to execute new and malicious transactions Solutions to the Problems • Confidentiality – If data is encrypted intruders cannot observe • Integrity – Modification can be detected • Authentication – If devices can identify source of data then it is difficult to impersonate a friendly device – Spoofing , replay attacks and denial of service can be averted • The question is where should such a solution be implemented in the protocol stack? Public-Key Cryptography • A user generates two keys: public-key and private-key pair • Public-key and private-key pairs can be viewed as mutually cancelling – What public-key can encrypt only private-key can decrypt • Public-key is known to everyone – Anyone can send a message to the user using public key • Private-key is secret – Only the user can decrypt with private key • Encryption with private is called digital signature – Can be verified but cannot be forged Message Authentication Codes • A Message Authentication Code algorithm is a family of hash functions hk, parametrized by a secret k, with properties: – Ease of computation: given a key k and input x, it is easy to compute hk(x) – Compression: hk maps an input of arbitrary length to an output of hk(x) of bitlength n – Computation-resistance: given zero or more text-MAC pairs (xi, hk(xi)) it is computationally infeasible to compute any text-MAC pair (x, hk(x)) for any new input x • If two users share a cryptographic key they can use it generate same MAC and hence, validate each other Recalling Protocol Stack Application Physical Layer NFS Link Layer SNMP IP FTP DNS FTP SMTP HTTP TCP, UDP Security Measures at Different Layers Application Layer PGP, Kerberos, SSH, S/MIME Transport Layer SSL/Transport Layer Security (TLS) Network Layer IPsec Data Link Layer Hardware encryption Security (contd.) Measures at Different Layers • Application Layer Security – Implemented as a User Software – No need to modify operating system or underlying network structure – Each application and system requires its own security mechanisms • SSL/TLS (transport layer security) is implement as user-end software, and is protocol specific • Link layer security – Implemented in hardware – Requires encryption decryption between every link – Difficult to implement in Internet like scenario IPsec: Security at IP Layer • IPsec is a framework of open standards developed by IETF (www.ietf.org, rfc’s 4301-4308) • IPsec is below transport layer and is transperant to applications – IPsec provides security to all traffic passing through the IP layer • End users need not be trained on security mechanisms, issued keys or revoked • IPsec has the granularity to provide per-user security if needed IPsec: Security at IP Layer (contd.) • IPsec has additional advantages of protecting routing architecture – IPsec can assure that a router advertisement is from an authorized router – A routing update is not forged – A neighbor advertisement comes from an authorized router IPsec Services • • • • • • Access control Connectionless Integrity Data origin authentication Rejection of replayed packets Confidentiality Limited traffic flow confidentiality IPsec Manifestation IPsec Manifestation • Protects data flow between/among – Pair of hosts: end-to-end protection between two users, independent of applications they are using – Pair of security gateways: A security gateway can be a router, firewall, proxy etc. Secures entire traffic from/to the network – Security gateway and a host: secure remote access to network resources • Granularity in Ipsec – Mode, choice of cryptographic algorithms, protocols – Which subsets of traffic are afforded protection IPsec at a Glance • IPsec uses a combination of the following techniques to provide its services – Diffie-Hellman key exchange to establish keys between peers – Encryption algorithms like DES to provide confidentiality – Keyed hash algorithms like MD5 and SHA-1 to provide message authentication IPsec: Roadmap • • • • • • • Security Association, Security Policy Database IPsec protocol components IPsec modes Authentication Header Encapsulating Security Payload Internet Key Exchange Commercial Instantiations Security Association • A simplex (one-way) relationship that affords security services to the traffic carried by it • Only one service per SA : AH or ESP • To secure bi-directional traffic 2 SAs are required • Specified by Security parameters index (SPI), destination IP address – Multiple SAs used by same source/receiver – Multiple sources can use same SA Security Association • Security Parameters Index • IP Destination Address • Security Protocol Identifier All three identify the particular SA being used SA Parameters • • • • • • • • Sequence Number Counter Sequence Counter Overflow Anti-Replay Window AH Information ESP Information Lifetime of SA IPSec Protocol mode –Tunnel, Transport Path MTU Security Policy Database • Defines policies for all IP traffic passing through the interface – Each SPD points to one or more corresponding SAs – Processing is done after matching against the corresponding SPD entry by using the relevant SA • Protection offered by IPsec is based on requirements defined by a security policy database, SPD • Packets are selected for one of three processing actions based on IPheader information, matched against entries in SPD – Actions:PROTECT, DISCARD, BYPASS SPD Entries • • • • • • • • • • Destination IP Address Source IP Address UserID Data sensitivity level Transport layer protocol IPSec protocol Source and Destination Ports IPv6 Class IPv6 Flow label IPv4 Type of Service Security Policy Database (contd.) • Logical divisions of SPD: SPD-S, SPD-I, SPD-O – SPD-I (bypassed or discarded), entries that apply to the inbound traffic – SPD-O(bypassed or discarded), entries identifying outbound traffic – SPD-S(secure traffic), entries to lookup SAs, create SAs, IPsec components • IPsec consists of two important protocol components – The first, defines the information that needs to be added to the IP packet to achieve the required services. These are classified further as Authentication Header and Encapsulating Security Protocol – The second, Internet Key Exchange, which negotiates security association between two peers and exchanges keying material Recalling Packet Headers Encapsulation of Data for Network Delivery Application Layer Transport Layer (TCP, UDP) Network Layer (IP) Data Link Header 1 Layer Header 2 Original Message Header 3 Data 3 Data 2 Data 1 IPsec Modes • IPsec can operate in two modes – Transport Mode • Only IP payload is encrypted • IP headers are left in tact • Adds limited overhead to the IP packet – Tunnel • Entire IP packet is encrypted • New IP headers are generated for this packet • Transparent to end-users IPsec modes (contd.) Transport Mode: protect the upper layer protocols Original IP Datagram IP Header TCP Header Transport Mode protected packet IP Header IPSec Header Data TCP Header Data protected Tunnel Mode: protect the entire IP payload Tunnel Mode protected packet New IP Header IPSec Header Original IP Header protected TCP Header Data Authentication Header • This information is added to the header to provide the following services: – Access control, connectionless integrity, data origin authentication, rejection of replayed packets – Information added are: • Sequence number (32-bit) • Integrity check value (variable, multiple of 32-bits) Authentication Header (contd.) • Anti-replay attacks – Range of sequence numbers for session is 232-1 – Sequence numbers are not reused • Integrity Check Value (ICV) – Keyed MAC algorithms used: AES, MD5, SHA-1 – MAC is calculated over immutable fields in transit (source/dest. addr, IP version, header length, packet length) Encapsulating Security Payload • Three types of services – Confidentiality only – Integrity only – Confidentiality and integrity • Others – Anti-replay service – Limited traffic flow confidentiality ESP (contd.) • Header fields – Security parameters index (32-bit) – Sequence number (32-bit) – Encrypted payload (variable)+padding(0-255 bytes) computed over upper layer segment (transport mode) or entire packet (tunnel mode) – TFC padding (optional, variable) – Integrity check value-ICV (variable, optional), computed over ESP header (all above data) ESP (contd.) • Most purposes ESP is sufficient to achieve both confidentiality and integrity. • Some auditable events by IPsec are: – Invalid SA – Processing fragmented packet – Transmitting packet which can cause sequence number overflow – Received packet fails anti-replay – Integrity check fails Internet Key Exchange (IKE) • IKE creates authenticated secure channel between two peers and then, negotiates SA • Phases of IKE – Authentication – Key Exchange – Establishing SA Authentication • Two peers in IPsec need to identify each other. Forms of authentication : – Pre-shared keys: same keys are pre-installed and authentication is done exchanging known data • Decryption requires same key and hence, only valid receivers can recover data – Public key cryptography: Nonces are exchanged using other user’s public-key and replies are checked for verification • Public-key to encrypt, Private-key to decrypt IKE and IPsec Limitations • Security implemented by AH and ESP ultimately depends on their implementation • Operating environment affects the way IPsec security works • Defects in OS security, poor random number generators, misconfiguration of protocols, can all degrade security provided by IPssec. Cryptographic Standards for ESP & IKE • Encapsulating Security Payload – ESP encryption: TripleDES in CBC mode [RFC2451] – ESP integrity : HMAC-SHA1-96 [RFC2404] • IKE and IKEv2 – – – – Encryption : TripleDES in CBC mode [RFC2451] Pseudo-random function: HMAC-SHA1 [RFC2104] Integrity : HMAC-SHA1-96 [RFC2404] Diffie-Hellman group: 1024-bit Modular Exponential [RFC2409] (MODP) Conclusions • IPsec provides a method for creating secure private networks over public networks • Applications, operating systems need not be changed – Implementation can be limited to secure gateways • Several products based on IPsec are commercially deployed • Users can even enable and use IPsec on their machines