* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download CSC 335 Data Communications and Networking I
Zero-configuration networking wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Computer network wikipedia , lookup
Remote Desktop Services wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Deep packet inspection wikipedia , lookup
Quality of service wikipedia , lookup
TCP congestion control wikipedia , lookup
Internet protocol suite wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
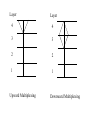
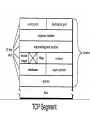
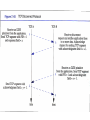
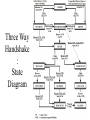
CSC 336 Data Communications and Networking Lecture 10: Transport Layer Dr. Cheer-Sun Yang Spring 2001 TOPICS • OSI Transport Services, design, protocols • Example Protocols: TCP, UDP • Client-Server Model and Socket Programming Comparison with Data Link Layer • Similarity: both layers are focusing on how information is exchanged between two entities • Difference:Data link layer defines communications between stations with a physical connection, whereas transport layer protocols define communications between sites with a logical connection. • Two kinds of transport layer protocols: connection-oriented and connection-less. Transport Layer Characteristics • Reliable: flow control and error recovery are provided • Two kinds: connection-oriented or connection-less • Example: Transmission Control Protocol(TCP), User Datagram Protocol(UDP) • Transport layer is the lowest layer which provides end-to-end services. The lower three protocols defines how network operates. Transport Layer Functions • Logical connection establishment – the transport layer provides the “connection” the user perceives. • A user can log on to computers at remote sites, giving them the impression that they are connected. • But the connection is not a physical one as exists when connecting wires or making phone calls (using circuit switching). Transport Layer Functions(cont’d) • It is similar to a secretary whose function is to place calls in behalf of an executive. The secretary gets the executive’s request, makes the call, and reaches the desired person, thus making the connection. • The executive then proceeds to have the conversation independent of the trouble that the secretary may have had in finding the desired person. Transport Layer Functions(cont’d) • The connection management defines the rules that allow two users to begin talking with one another as if they were connected directly. The function of defining and setting up the connection is referred to as handshaking. Transport Layer Functions(cont’d) • Graceful connection termination • The secretary may have to finish the connection by taking down some important information such as client’s address, checking the executive’s schedule for making a future appointment. • There are other functions. Connection Oriented Transport Protocol Mechanisms • Example: Transmission Control Protocol(TCP) Connection-less Transport Protocol Mechanisms • No connection-establishment • Datagram delivery • User Datagram Protocol(UDP) Motivations • Why do we still need transport layer running on top of network layer? – They have similar connection-oriented and connection-less services. – They both provide addressing and flow-control The answers are… • What happens if the network layer provides connection-oriented but unreliable service? Suppose that it frequently loses packets? What happens if routers crash all the time? • Users have no control over the subnet, so they cannot solve the problem of poor service by using better routers or putting more error handling in the data link layer. • So another layer is added to provide better quality of service(QoS). Error Detection at the Transport Level Transport Layer Functions • Establishment of connectionless or connectionoriented communication • Addressing • Flow Control (transport layer) • Error detection (transport layer) • Interface with upper layers • Multiplexing • Quality of Service (QoS) In general, a transport layer protocol must provide reliable communications between end users. Reliable Sequencing Network Service • Assume arbitrary length message • Assume virtually 100% reliable delivery by network service – e.g. reliable packet switched network using X.25 – e.g. frame relay using LAPF control protocol – e.g. IEEE 802.3 using connection oriented LLC service • Transport service is end to end protocol between two systems on same network Reliable Sequencing Network Service • It is important because IP or other network layer protocols do no guarantee reliable service. Transport protocols must provide acknowledgements and timers to make sure that all of a user’s data are sent and received. TCP is not the OSI Transport Layer Protocol • TCP is designed and developed by the DoD to run on top of IP for providing connection-oriented transport layer services. • OSI transport layer protocol is a generic redesign of transport layer protocol which includes more functions than TCP. OSI vs. TCP • OSI transport services include a more complete set of services • TCP is not identical to OSI transport protocol in terms of the PDU format, and even some terms. For example, TCP calls its PDU a segment; OSI calls its PDU a TPDU; TCP identifies its application using a port number, OSI uses a Transport Service Access Point(TSAP). We will summarize the comparison at the end of this unit of slides. Issues in OSI Transport Protocols • • • • • • • Establishing a Connection Releasing a connection Addressing Quality of Service (QoS) Multiplexing Flow Control and Buffering Crash Recovery Addressing • Target user specified by: – User identification: Transport Service Access Point (TSAP) – Machine identification: Network layer address, such as IP address, identifies a host Finding Addresses • Four methods – Know address ahead of time • e.g. collection of network device stats – Well known addresses – Name server – Sending process request to well known address QoS • Another way to look at the transport service is to regard its primary function as enhancing the QoS provided by the network layer. • If the network layer is impeccable, the transport layer has an easy job. • If the network layer is unreliable, the transport layer has to bridge the gap between what the user wants and the network layer provides. OSI Transport Service Types • TP0: no error control, no resynch, no multiplexing • TP1: no error control, can resynche, no multiplexing • TP2: no error control, multiplexing, no resynch • TP3: no error control, can resynch, multiplexing, flow control • TP4: runs on top of un-reliable network services such as IP; provides error control, resynch, multiplexing, and flow control. OSI TP4 services are similar to TCP services. QoS • What is QoS? It is characterized by a list of QoS parameters which can be negotiated at the connection establishment time. • It is specified by users at the user layer. • It is up to the transport layer to examine them and determine whether or not it can provide the required service. QoS Parameters • • • • • • • • Connection establishment delay Connection establishment failure probability Throughput Transit delay Residual error ratio Protection Priority Resilience QoS Parameters • Connection establishment delay - the amount of time elapsing between a transport connection being requested and the confirmation being provided by the user of the transport services • Connection establishment failure probability - the chance of a connection not being established within the maximum establishment delay time, for example, due to network congestion, lack of table space somewhere, or other internal problems. QoS Parameters • Throughput – measures the number of bytes of user data transferred per second. • Transit delay – measures the time between a message being sent by the transport user on the source and its being received by the transport user on the destination. • Residual error ratio – measures the number of lost or garbled messages as a fraction of the total sent. QoS Parameters • Protection – provides a way for the transport user to specify interest in having the transport layer provide protection against unauthorized third party reading or modifying the transmitted data. • Priority – specifies the priority of a connection. It is used in the event of congestion to make sure that higher priority connections get serviced before the lowerpriority connections. Multiplexing • Multiple users employ same transport protocol • User identified by transport service access point (TSAP) • Multiple transport connections are connected to a single network connection – upward multiplexing – e.g. multiplexing a single virtual X.25 circuit to a number of transport service user • X.25 charges per virtual circuit connection time Multiplexing • Multiplexing can also be useful in the transport layer for another reason. • If the physical connection is a high-speed physical connection and the user layer application also generates data very fast, but the network layer limits the window size to a small constant, several transport layer connection can be established simultaneous. Layer Layer 4 4 3 3 2 2 1 1 Upward Multiplexing Downward Multiplexing Connection Termination • Entity in CLOSE WAIT state sends last data segment, followed by FIN • FIN arrives before last data segment • Receiver accepts FIN – Closes connection – Loses last data segment • Associate sequence number with FIN • Receiver waits for all segments before FIN sequence number • Loss of segments and obsolete segments – Must explicitly ACK FIN Graceful Close • Send FIN i and receive AN i • Receive FIN j and send AN j • Wait twice maximum expected segment lifetime Crash Recovery • After restart all state info is lost • Connection is half open – Side that did not crash still thinks it is connected • Close connection using persistence timer – Wait for ACK for (time out) * (number of retries) – When expired, close connection and inform user • Send RST i in response to any i segment arriving • User must decide whether to reconnect – Problems with lost or duplicate data RFCs regarding TCP & UDP • Transmission Control Protocol – Connection oriented – RFC 793 • User Datagram Protocol (UDP) – Connectionless – RFC 768 TCP Mechanisms (1) • Connection establishment – Three way handshake – Between pairs of ports – One port can connect to multiple destinations TCP Mechanisms (2) • Data transfer – Logical stream of octets – Octets numbered modulo 223 – Flow control by credit allocation of number of octets – Data buffered at transmitter and receiver – Congestion control TCP Mechanisms (3) • Connection termination – Graceful close – TCP users issues CLOSE primitive – Transport entity sets FIN flag on last segment sent – Abrupt termination by ABORT primitive • Entity abandons all attempts to send or receive data • RST segment transmitted TCP Header TCP Services • Reliable communication between pairs of processes • Across variety of reliable and unreliable networks and internets • Two labeling facilities (part of flags) – Data stream push • TCP user can require transmission of all data up to push flag • Receiver will deliver in same manner • Avoids waiting for full buffers – Urgent data signal • Indicates urgent data is upcoming in stream • User decides how to handle it TCP Connection Management • What exactly is a connection? Establishment and Termination • Allow each end to now the other exists • Negotiation of optional parameters • Triggers allocation of transport entity resources • By mutual agreement Connection Establishment • Two way handshake – A send SYN, B replies with SYN – Lost SYN handled by re-transmission • Can lead to duplicate SYNs – Ignore duplicate SYNs once connected • Lost or delayed data segments can cause connection problems – Segment from old connections – Start segment numbers fare removed from previous connection • Use SYN i • Need ACK to include i • Three Way Handshake Two Way Handshake : Obsolete Data Segment Two Way Handshake: Obsolete SYN Segment Three Way Handshake: Examples Three Way Handshake : State Diagram Flow Control • Credit Mechanism • A credit, stored in the segment’s window field, specifies the maximum number of bytes the entity (node) sending this segment can receive and buffer from the other entity (node). See Fig. 7.46. Congestion Control • There are problems that the flow control mechanism cannot solve. • Assume that the previous discussion showed that the window sizes (credits) were adjusted based only on what A or B can handle. It didn’t take into account what might be in between. • What happens that A and B both are connected to others with T-1 links but use a link capable to transmit 64 kbps between A and B? Congestion Window • Due to Jacobson [1988]- Jacobson’s algorithm • TCP is enhanced to allow a sending entity to respond to congestion links and to alter the number of segments it can send. Congestion Window • We will focus on the transmission from A to B. • A maintains a congestion window that specifies the number of bytes it thinks it can send without causing or adding to congestion. • If the congestion window’s capacity is larger than A’s credit then A will still not send more than the credit allows. • Otherwise, A uses the congestion window’s value to determine how many segments to send. Congestion Window • How can A determine when congestion exists? – Timeout mechanism • How does A respond to congestion? – reduce the size of the congestion window by half; resend; if timeout occurs again, the window size is reduced by half again. Congestion Window • If the congestion is alleviated, A will increase the congestion window size and recalculate the sending window size. • Consequently, A will reduce the congestion window much more quickly than it will increase it. • A remaining question… Congestion Window • How is the initial congestion window size determined? • It is similar to the recovery procedure after congestion. Initial Value • A will reduce the congestion window much more quickly than it will increase it. • The startup procedure is called a slow start. Window Management • Slow start – Actual window= MIN[credit, congested window] – Start connection with congested window size=1 – Increment congested window(cwnd) at each ACK, to some max • Dynamic windows sizing on congestion – When a timeout occurs – Set slow start threshold to half current congestion window • ssthresh=cwnd/2 – Set cwnd = 1 and slow start until cwnd=ssthresh • Increasing cwnd by 1 for every ACK – For cwnd >=ssthresh, increase cwnd by 1 for each RTT Congestion Control • RFC 1122, Requirements for Internet hosts • Retransmission timer management – To control a lost or discard segment, TCP employs a retransmission timer which handles the retransmission time, the waiting time for an ACK of a segment. – For each connection, TCP maintains a variable, RTT, that is the best estimate of the current round trip time to the destination in question. When a segment is sent, a timer is started. Congestion Control • When a timer is created, two situations can occur: – If an ACK is received for this particular segment before the timer goes off, the timer is destroyed. – If the timer goes off before the ACK is received, the segment is retransmitted and the timer is reset. Calculation of the Retransmission Time • Retransmission = 2 * RTT • RTT: estimated Round-Trip Time Calculation of RTT • RTT = * previous RTT + (1 - ) * current RTT • is usually set to 90%. Karn’s Algorithm • Suppose that a segment is not acknowledged during the retransmission period and it is therefore retransmitted. When the sending TCP receives an ACK for this segment, it does not know if the ACK is for the original segment or for the retransmitted one. The value of the new RTT therefore must be calculated based on the departure of the segment. Karn’s Algorithm • Do not consider the RTT of a retransmitted segment in the calculation of the new RTT. • Do not update the value of the RTT until you send a segment and receive an ACK without the need for retransmission. Karn’s Algorithm • If a segment is re-transmitted, the ACK arriving may be: – For the first copy of the segment • RTT longer than expected – For second copy • • • • No way to tell Do not measure RTT for re-transmitted segments Calculate backoff when re-transmission occurs Use backoff RTO until ACK arrives for segment that has not been re-transmitted Conceptual TCP Primitives • • • • • • Open - request Send - request Deliver - indication Accept - indication Terminate – confirm Etc. Send • If no push or close TCP entity transmits at its own convenience • Data buffered at transmit buffer • May construct segment per data batch • May wait for certain amount of data Deliver • In absence of push, deliver data at own convenience • May deliver as each in order segment received • May buffer data from more than one segment Accept • Segments may arrive out of order • In order – Only accept segments in order – Discard out of order segments • In windows – Accept all segments within receive window Retransmit • TCP maintains queue of segments transmitted but not acknowledged • TCP will retransmit if not ACKed in given time – First only – Batch – Individual Acknowledgement • Immediate • Cumulative UDP • User datagram protocol (UDP) runs on top of IP. • RFC 768 • Connectionless service for application level procedures – Unreliable – Delivery and duplication control not guaranteed • Reduced overhead • There is no formal mechanism for acknowledging errors or a provision for flow control or segment sequencing. UDP Uses • • • • Inward data collection Outward data dissemination Request-Response Real time application UDP Header OSI vs. TCP • • • • • • Segment Types Important Data Graceful Termination Piggyback acknowledgement Sequencing Flow Control Socket Programming • • • • • Sockets Client/Server Model Socket Data Structure Socket Commands Examples: Client Program, Server Program Sockets • A socket is a UNIX construct and is the basis for UNIX networking services. • A socket is similar to an envelop in which information can be stored. Client/Server Model An example of file transfer: • User requests a file. • Client sends request to the server on behalf of the user. • Server receives a request from a client and analyzes it. • Server copies a file from its auxiliary storage. • Server transmits contents of the file back to the client. • Client gets files’s contents from the server and make it accessible to the user. Socket Data Structures Socket Data Structures Socket Data Structures Socket Data Structures Suggested Reading • Shay: Section 7.5, 7.6 • RFC793 (TCP) 768 (UDP) 1112 (Host Extensions for Multicasting)