* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Week 4: Monetary Transactions in Ecommerce
Remote Desktop Services wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Distributed firewall wikipedia , lookup
Net neutrality law wikipedia , lookup
Airborne Networking wikipedia , lookup
Computer network wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
TCP congestion control wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Deep packet inspection wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Hypertext Transfer Protocol wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Internet protocol suite wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
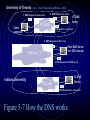
Week 4: Monetary Transactions in Ecommerce Chapter 3 of Amor Text “Selecting the Technology” Virginia F. Kleist, Ph.D. Chapter 3 Chapter 3 is about the hardware and software infrastructure that enables the electronic commerce web application to operate. This chapter covers the basics of the internet communications architecture, IP addresses, software and some middleware applications. This chapter, together with Chpt. 14, covers the fundamentals of the tools that are required to build a viable web presence, infrastructural, software and payments mechanisms. The course has a managerial component, a technology component and a programming component, and these two chapters are related to the technology component. Outline of Chpt. 3 Amor text • • • • • • Internet networking Exploring the IT infrastructure Deciding on the Enterprise Middleware Choosing the Right Enterprise Applications Building the E-Business Applications Speeding up the Internet 3.1 Internet Networking • • • • • • 3.1.1 The internet infrastructure 3.1.2 The Internet architecture 3.1.3 The internet protocol suite 3.1.4 The domain name system 3.1.5 IPv6 3.1.6 ATM Networks Sender Figure 5-1 TCP/IP’s 5-Layer Network Model Application Layer Transport Layer Network Layer Data Link Layer Physical Layer Receiver (note: from Fitzgerald and Dennis, 2002) HTTP Request TCP HTTP Request IP TCP HTTP Ethernet IP Application Layer Transport Layer Request TCP HTTP Request Network Layer Data Link Layer Physical Layer HTTP Request TCP HTTP Request IP TCP HTTP Ethernet IP Request TCP HTTP Request University of Toronto (note: from Fitzgerald and Dennis, 2002) 1. DNS Request to local server 6. DNS Response to client UT DNS Server UT LAN Client computer 2. DNS Request to .edu server 5. DNS Response to UT server Root DNS Server for .EDU domain Internet 3. DNS Request to IU DNS server Indiana University IU DNS Server IU LAN 4. DNS Response to .edu server Figure 5-7 How the DNS works Transmission Control Protocol/Internet Protocol (TCP/IP) (note: from Fitzgerald and Dennis, 2002) • Developed in 1974 by Vint Cerf and Bob Kahn as part of the Arpanet network developed for the US Defense Department. • TCP/IP is the protocol used by the Internet. • Almost 70% of all backbone, metropolitan and wide area networks use TCP/IP. • In 1998, TCP/IP surpassed IPX/SPX to become the most common protocol on local area networks. Introduction: The Network and Transport Layers (note: from Fitzgerald and Dennis, 2002) • The transport layer is responsible for end-to-end delivery of outgoing messages from the application layer. • The transport layer sets up virtual circuits (when needed) and is also responsible for segmentation (breaking the message into several smaller pieces) at the sending end and reassembly (reconstructing the original message into a single whole) at the receiving end. • The network layer is responsible for addressing and routing of the message. • The network and transport layers also perform encapsulation of message segments from the application layer, passing them down to the data link layer on the sending end and passing them up to the application layer on the receiving end (see Figure 5-1). IP Address Ipv4 • Class A networks 16,777,216 IP addresses • Class B networks 65,536 IP addresses • Class C networks 256 IP addresses Types of addresses (note: from Fitzgerald and Dennis, 2002) Address Example Software Application Layer Network Layer Data Link Layer Web browser TCP/IP Ethernet Example Address www.cba.uga.edu 128.192.98.5 00-0C-00-F5-03-5A IPv4 Addresses (note: from Fitzgerald and Dennis, 2002) • IPv4, uses 4 byte (32 bit) addresses which is really a string of 32 binary bits. • To make IP addresses easier to understand for human readers, dotted decimal notation is used. • Dotted decimal notation breaks the address into four bytes and writes each byte values digital equivalent. • An of an IP address in dotted decimal notation would be: 128.192.56.1 Figure 5-12 (note: from Fitzgerald and Dennis, 2002) 3.2 Exploring the IT Infrastructure • 3.2.1 The platform • 3.2.2 Basic internet software 3.3 Deciding on the Enterprise Middleware • • • • • • 3.3.1 3.3.2 3.3.3 3.3.4 3.3.5 3.3.6 Mail and collaboration Network and Systems Management Security software Payment solutions Database Management systems High availability 3.4 Choosing the Right Enterprise Applications • 3.4.1 Software trends • 3.4.2 Imaging technologies • 3.4.3 Content preparation: HTML, web page editors, content management,graphics software, multimedia tools, sound software • 3.4.4 Data warehousing: consolidated views, descriptive terms, preprocessed data, normalization of data • 3.4.5 Enterprise Resource Planning • 3.4.6 Call center solutions 3.5 Building the E-Business Application • 3.5.1 Putting the building blocks together • 3.5.2 Integrating the enterprise • 3.5.4 Solutions to integration: Point to point, database to database, federated databases, brokering, composite application, process automation • 3.5.5 Selecting the right EAI Technology 3.6 Speeding up the Internet • • • • • 3.6.1 3.6.2 3.6.3 3.6.4 3.6.5 Introduction Content delivery management Bandwidth conservation Quality of service Caching