* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Application Control
Zero-configuration networking wikipedia , lookup
Net neutrality law wikipedia , lookup
Remote Desktop Services wikipedia , lookup
TCP congestion control wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Wake-on-LAN wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Internet protocol suite wikipedia , lookup
Quality of service wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Distributed firewall wikipedia , lookup
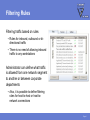
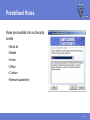
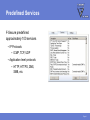
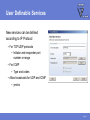
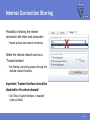
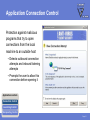
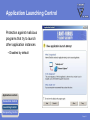
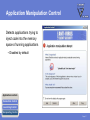
FEATURES & FUNCTIONALITY Agenda Main topics • Packet Filter Firewall • Application Control • Other features Page 2 Requirements Supported platfroms • Windows 2000 Professional (with SP4 or higher) and Windows XP (Professional and Home Edition, with SP1 or higher) • Also installs on Longhorn Beta Minimum requirements • Intel Pentium compatible hardware • 128 MB (Windows 2000), 256 MB (Windows XP) • 256 MB or more recommended (depending on the installed components)! • 50 MB free hard disk space • Internet connection recommended Page 3 PACKET FILTER FIREWALL IP Filtering for Workstations Protects data on mobile workstations and desktops against network worms and cracking Intercepts IP packets at the NDIS (Network Device Interface Specification) layer • Allowed incoming packets are forwarded to the TCP/IP stack • Allowed outgoing packets are sent out through the network interface Application Presentation Session Transport Network DataLink Physical Page 5 Filtering Rules Filtering traffic based on rules • Rules for inbound, outbound or bidirectional traffic • There is no need of allowing inbound traffic to any workstations Administrator can define what traffic is allowed from one network segment to another or between corporate departments • Also, it is possible to define filtering rules for host-to-host or host-tonetwork connections Page 6 Predefined Rules Rules are bundled into six Security Levels • Block all • Mobile • Home • Office • Custom • Network quarantine Page 7 Predefined Services F-Secure predefined approximately 100 services • IP Protocols • ICMP, TCP, UDP • Application level protocols • HTTP, HTTPS, DNS, SMB, etc. Page 8 User Definable Services New services can be defined according to IP Protocol • For TCP/UDP protocols • Initiator and responder port number or range • For ICMP • Type and codes • Allow broadcasts for UDP and ICMP • yes/no Page 9 Security Levels Structure 1 SECURITY LEVEL 2 RULES Allow Web Browsing 3 SERVICES • HTTP / Hyper Text Transfer Protocol • HTTPS (SSL) • FTP / File Transfer Protocol out out out Page 10 Intrusion Detection System (IDS) Analyses the payload and the header information of an IP packet to detect different kind of intrusion attempts • Monitors inbound traffic • Inspects single packets only, not full stream or TCP/IP sequence • System alerts on 31 malicous packets; most common operating system fingerprinting attempts (nmap, CyberCop), port scans and network worms • Database selected carefully to avoid false positives • Patterns are updated when software is updated IDS engine is divided in to generic IP engine (13 packets), UDP protocol engine (5 packets) and TCP protocol engine (13 packets) Page 11 Internet Connection Sharing Possibility of sharing the internet connection with other local computers • Needs at least two network interfaces X Define the internal network card as a ”Trusted interface” • No filtering, everything passes through the defined network interface Important: Trusted interface should be disabled for the whole domain! • Set “Allow Trusted Interface = disabled” (mark as final!) Page 12 APPLICATION CONTROL Application Control Decides what products can and what cannot be used to connect to the internet, manipulate or launch other programs Application controls What is controlled Connection Control External connection attempts Launching Control Application launches Manipulating Control Code injections Page 14 Application Connection Control Protection against malicious programs that try to open connections from the local machine to an outside host • Detects outbound connection attempts and inbound listening attempts • Prompts the user to allow this connection before opening it Application controls Connection Control Launching Control Manipulating Control Page 15 Application Launching Control Protection against malicious programs that try to launch other application instances • Disabled by default Application controls Connection Control Launching Control Manipulating Control Page 16 Application Manipulation Control Detects applications trying to inject code into the memory space of running applications • Disabled by default Application controls Connection Control Launching Control Manipulating Control Page 17 Executable Decisions Permanent Application control decisions regarding a certain program are always tied to the executable • Binary change detection uses a hash function (SHA-1 checksum) • If a program is updated, Internet Shield will prompt for a new decision • Policy Manger is pre-configured with a whitelist of most critical windows and F-Secure services (e.g. allowing AUA connections) Page 18 Dynamic Rules Application connection control creates dynamic rules to the firewall packet filter rulebase • Creates dynamic inbound rules for allowed applications • Checks for existing outbound static rules before opening the connection to prevent timeouts • Tied to the executable Rules visible in the rulebase • Rules only in use when the executable is running • Rules added juts before the last deny rest rule Page 19 Central Administration Policy Manager supports central administration for Application Connection Control • PMC application rules overwrite user defined rules • Applications cannot be added manually (need to be reported by the hosts) • All new application connections can be reported to FSPMC (except system and boot time services) Page 20 OTHER FEATURES Dial-up Control Protection against malicous dialing attempts (monitors dialup processes, e.g. RAS API) • Maintains a list of allowed or denied numbers • Limited central management (user decisions are not reported to the PMC!) Hang-up control • Only allowed applications can close an active connection. Page 22 Alerting Internet Shield alerts are divided into two groups • Packet filter alerts (only create a log entry if so defined in the rule) • Log only (blue alert) • Log and pop-up (red alert) • Intrusion alerts (yellow alert) Page 23 Logging Extended logging capabilities • All firewall actions • All alerts Packet logging • Packet logging will grab all frames from all network devices and store them to a file • Useful for debugging • Needs to be activated with a specific policy! Page 24 Summary Main topics • Packet Filter Firewall • Application Control • Other features Page 25