* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Document
Wireless security wikipedia , lookup
Airborne Networking wikipedia , lookup
Network tap wikipedia , lookup
Server Message Block wikipedia , lookup
Distributed firewall wikipedia , lookup
Computer network wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Dynamic Host Configuration Protocol wikipedia , lookup
Deep packet inspection wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Remote Desktop Services wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Internet protocol suite wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Chapter 2
Network Models
2.1
Copyright © The McGraw-Hill Companies, Inc. Permission required for reproduction or display.
2-1 LAYERED TASKS
We use the concept of layers in our daily life. As an
example, let us consider two friends who communicate
through postal mail. The process of sending a letter to a
friend would be complex if there were no services
available from the post office.
Topics discussed in this section:
Sender, Receiver, and Carrier
Hierarchy
2.2
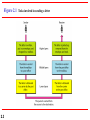
Figure 2.1
2.3
Tasks involved in sending a letter
2-2 THE OSI MODEL
Established in 1947, the International Standards Organization (ISO) is a
multinational body dedicated to worldwide agreement on international
standards. An ISO standard that covers all aspects of network
communications is the Open Systems Interconnection (OSI) model. It was
first introduced in the late 1970s.
an ISO (International Standard Organization) standard that covers all
aspects of network communications
•An open system is a model that allows any two different systems to
communicate regardless of their underlying architecture
•Purpose of OSI model is to open communication between different
systems without requiring changes to the logic of the underlying
hardware and software
•a reference model for understanding and designing a network architecture
that is flexible, robust, interoperable
Layered Architecture
Peer-to-Peer Processes
Encapsulation
2.4
Note
ISO is the organization.
OSI is the model.
2.5
Figure 2.2 Seven layers of the OSI model
•A layered framework
that allows for
communication across all
types of computers
•Consists of seven
separate but related
layers – defining a
segment of process of
moving information
across network
2.6
Each layer defines a family of functions (or
services) distinct from those of the other
layers
2.7
an architecture that is modular,
comprehensive, flexible
The OSI model allows complete
transparency between otherwise
incompatible systems
Figure 2.3 The interaction between layers in the OSI model
2.8
2.9
Each layer communicates with the peer layer by means
of a protocol
an agreed-upon series of rules and conventions
Communication between machines is peer-to-peer
process using protocols at any given layer
Each layer adds information to the data – Headers are
added to the data at layers 6, 5, 4, 3 and 2. Trailers are
usually added at layer 2
Each layer calls upon of the services of the layer below it
by means of an interface
Interface defines what information and services a layer
must provide for the layer above it
As long as a layer provides expected services, specific
functions can be modified and replaced without
requiring changes to other layers
Figure 2.4 An exchange using the OSI model
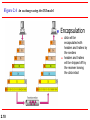
Encapsulation
2.10
data will be
encapsulated with
headers and trailers by
the senders
headers and trailers
will be stripped off by
the receiver leaving
the data intact
2-3 LAYERS IN THE OSI MODEL
In this section we briefly describe the functions of each
layer in the OSI model.
Topics discussed in this section:
Physical Layer
Data Link Layer
Network Layer
Transport Layer
Session Layer
Presentation Layer
Application Layer
2.11
Figure 2.5 Physical layer
Major duties of the physical layer:
• Physical characteristics of interfaces and media.
• Representation of bits 0 – encode into signals (electrical or optical)
and how 0s and 1s are changed into signals.
• Data rate – the transmission rate: the number of bits sent each
second.
• synchronization of bits – sender and receiver must use the same bit
rate (their clock must be synchronized)
2.12
Note
The physical layer is responsible for movements of
individual bits from one hop (node) to the next.
2.13
Figure 2.6 Data link layer
•Framing – divides the stream of bits received from the network layer into
data units called frames.
•Physical addressing – define a sender and receiver.
•Flow control – imposed a mechanism to prevent overwhelming the receiver.
•Error control
•Access control
2.14
Note
The data link layer is responsible for moving
frames from one hop (node) to the next.
2.15
Figure 2.7 Hop-to-hop delivery
2.16
Figure 2.8 Network layer
Responsible for : source-to-destination delivery across multiple networks.
Needs for delivering a packet to different networks with connecting devices
between the networks. (Local delivery Vs global delivery)
Major duties:
•Logical addressing – adds a header to the packet coming from the upper
layer (logical addresses of the sender and receiver)
•Routing – works at the connecting devices (routers)
2.17
Note
The network layer is responsible for the
delivery of individual packets from
the source host to the destination host.
2.18
Figure 2.9 Source-to-destination delivery
2.19
Figure 2.10 Transport layer
Responsible for: process-to-process delivery of the entire message.
•Service point addressing– include a port address in the header (forward the packet to the
correct process).
•Segmentation and reassembly – Sender; message is divided into transmittable segments, each
segment containing a sequence number. Destination; reassemble the message based on seq.
number (identify and replace packet that were lost in transmission).
•Connection control - Connection-oriented or connectionless.
•Flow control – performed end-to-end
•Error control – entire message arrives without error. Error correction achieved through
retransmission.
2.20
Note
The transport layer is responsible for the delivery
of a message from one process to another.
2.21
Figure 2.11 Reliable process-to-process delivery of a message
2.22
Figure 2.12 Session layer
2.23
Session layer is the network dialog controller
Session Layer Responsibilities:
Dialog control – establishes, maintains, terminates dialog
between communicating systems. Communication between
two process can be either half-duplex or full-duplex
Synchronization – allows a process to add checkpoints
(synchronization points) into a stream of data (for efficient
retransmission if necessary).
Note
The session layer is responsible for dialog
control and synchronization.
2.24
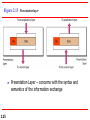
Figure 2.13 Presentation layer
2.25
Presentation Layer – concerns with the syntax and
semantics of the information exchange
The presentation layer is responsible for translation,
compression, and encryption.
Presentation Layer Responsibilities:
2.26
Translation – information in the form of character strings,
numbers, etc need to be encoded to bit streams before being
transmitted; presentation layer is responsible for
interoperability between different encoding systems; possible
different sender-dependent format and receiver-dependent
format need to be encoded and decoded.
Encryption – encryption and decryption may be necessary for
sensitive information.
Compression – compression and decompression if required will
reduce the number of bits transmitted. Important in
transmission of multimedia such as text, audio and video
Figure 2.14 Application layer
provides interfaces and support to various applications, e-mails,
remote file access and transfer, shared data base management, etc.
Example:X.500 (directory services), X.400 (message handling),
FTAM (file transfer access and management)
2.27
The application layer is responsible for
providing services to the user.
Application Layer (cont)
Network virtual terminal –
allows user to log on to a
remote host via terminal emulation software
File transfer, access and management (FTAM)
– allows user to access (read, make changes), retrieve, send, manage
files on a remote computer
Mail services – e-mail forwarding and storage
Directory services – provides distributed database source
and access for global information about various objects and services
2.28
Figure 2.15 Summary of layers
2.29
2-4 TCP/IP PROTOCOL SUITE
The layers in the TCP/IP protocol suite do not exactly match
those in the OSI model. The original TCP/IP protocol suite was
defined as having four layers: host-to-network, internet,
transport, and application.
However, when TCP/IP is compared to OSI, we can say that the
TCP/IP protocol suite is made of five layers: physical, data link,
network, transport, and application
At transport layer, TCP/IP defines two protocol – TCP and UDP.
At network layer, the main protocol defined by TCP/IP is IP.
Topics discussed in this section:
Physical and Data Link Layers
Network Layer
Transport Layer
Application Layer
2.30
Figure 2.16 TCP/IP and OSI model
2.31
2-5 ADDRESSING
Four levels of addresses are used in an internet employing
the TCP/IP protocols: physical, logical, port, and specific.
Topics discussed in this section:
Physical Addresses
Logical Addresses
Port Addresses
Specific Addresses
2.32
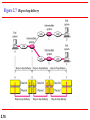
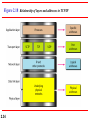
Figure 2.17 Addresses in TCP/IP
Address of node IP Address for
defined by LAN universal
or WAN
communication
s
32 bit IP
address that is
unique
2.33
Labels assign to Examples:
processes
Email
URL
16 bit
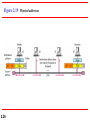
Figure 2.18 Relationship of layers and addresses in TCP/IP
2.34
Example 2.1
In Figure 2.19 a node with physical address 10 sends a
frame to a node with physical address 87. The two nodes
are connected by a link (bus topology LAN). As the
figure shows, the computer with physical address 10 is
the sender, and the computer with physical address 87 is
the receiver.
2.35
Figure 2.19 Physical addresses
2.36
Example 2.2
As we will see in Chapter 13, most local-area networks
use a 48-bit (6-byte) physical address written as 12
hexadecimal digits; every byte (2 hexadecimal digits) is
separated by a colon, as shown below:
07:01:02:01:2C:4B
A 6-byte (12 hexadecimal digits) physical address.
2.37
Example 2.3
Figure 2.20 shows a part of an internet with two routers
connecting three LANs. Each device (computer or
router) has a pair of addresses (logical and physical) for
each connection. In this case, each computer is
connected to only one link and therefore has only one
pair of addresses. Each router, however, is connected to
three networks (only two are shown in the figure). So
each router has three pairs of addresses, one for each
connection.
2.38
Figure 2.20 IP addresses
2.39
Example 2.4
Figure 2.21 shows two computers communicating via the
Internet. The sending computer is running three
processes at this time with port addresses a, b, and c. The
receiving computer is running two processes at this time
with port addresses j and k. Process a in the sending
computer needs to communicate with process j in the
receiving computer. Note that although physical
addresses change from hop to hop, logical and port
addresses remain the same from the source to
destination.
2.40
Figure 2.21 Port addresses
2.41
Note
The physical addresses will change from hop to hop,
but the logical addresses usually remain the same.
2.42
Example 2.5
As we will see in Chapter 23, a port address is a 16-bit
address represented by one decimal number as shown.
753
A 16-bit port address represented
as one single number.
2.43
Note
The physical addresses change from hop to hop,
but the logical and port addresses usually remain the same.
2.44
Extra: The Client-Server Model
Client and server processes are considered to be in
the Application layer.
the device requesting the information is called a client
the device responding to the request is called a server.
Application layer protocols describe the format of the
requests and responses between clients and servers.
One example of a client/server network is a corporate
environment where employees use a company e-mail
server to send, receive and store e-mail.
The e-mail client on an employee computer issues a
request to the e-mail server for any unread mail.
The server responds by sending the requested e-mail to
the client.
Data is typically flowing from the server to the client,
some data always flows from the client to the server.
For example, a client may transfer a file to the server
for storage purposes (upload).
Data from a server to a client as a download.
Extra: Servers
In a general networking context, any device that
responds to requests from client applications is
functioning as a server.
A server is usually a computer that contains
information to be shared with many client systems.
For example, web pages, documents, databases,
pictures, video, and audio files can all be stored on a
server and delivered to requesting clients.
In other cases, such as a network printer, the print
server delivers the client print requests to the specified
printer.
Some servers may require authentication of user
account information to verify if the user has permission
to access the requested data or to use a particular
operation.
if you request to upload data to the FTP server, you may
have permission to write to your individual folder but not
to read other files on the site.
Extra: Servers
In a client/server network, the server runs a
service, or process, sometimes called a server
daemon.
Like most services, daemons typically run in the
background and are not under an end user's
direct control.
Daemons are described as "listening" for a
request from a client, because they are
programmed to respond whenever the server
receives a request for the service provided by the
daemon.
When a daemon "hears" a request from a client,
it exchanges appropriate messages with the
client, as required by its protocol, and proceeds
to send the requested data to the client in the
proper format.
Extra: The Peer-to-Peer Model
In addition to the client/server model for networking, there is
also a peer-to-peer model.
Peer-to-peer networking involves two distinct forms: peer-to-peer
network design and peer-to-peer applications (P2P).
Peer-to-Peer Networks
In a peer-to-peer network, two or more computers are connected
via a network and can share resources (such as printers and files)
without having a dedicated server.
Every connected end device (known as a peer) can function as
either a server or a client.
One computer might assume the role of server for one transaction
while simultaneously serving as a client for another.
A simple home network with two computers sharing a printer
is an example of a peer-to-peer network.
Each person can set his or her computer to share files, enable
networked games, or share an Internet connection.
Because peer-to-peer networks usually do not use centralized
user accounts, permissions, or monitors
it is difficult to enforce security
Extra: Peer-to-Peer Applications
Peer-to-Peer (P2P) Applications
A P2P application, allows a device to act as both a client
and a server within the same communication.
However, peer-to-peer applications require that each
end device provide a user interface and run a
background service.
When you launch a specific P2P application it invokes the
required user interface and background services.
Some P2P applications use a hybrid system where
resource sharing is decentralized but the indexes that
point to resource locations are stored in a centralized
directory.
In a hybrid system, each peer accesses an index server
to get the location of a resource stored on another peer.
The index server can also help connect two peers, but
once connected, the communication takes place
between the two peers without additional
communication to the index server.
Peer-to-peer applications can be used on peer-topeer networks, client/server networks, and
across the Internet.
Extra: Application Layer Protocols
The widely-known Application layer protocols
are those that provide the exchange of
information.
Among these TCP/IP protocols are:
Domain Name Service Protocol (DNS) is used to
resolve Internet names to IP addresses.
Hypertext Transfer Protocol (HTTP) is used to
transfer files that make up the Web pages of the
World Wide Web.
Simple Mail Transfer Protocol (SMTP) is used for
the transfer of mail messages and attachments.
Telnet, a terminal emulation protocol, is used to
provide remote access to servers and networking
devices.
File Transfer Protocol (FTP) is used for interactive
file transfer between systems.
The protocols in the TCP/IP suite are generally
defined by Requests for Comments (RFCs).
The Internet Engineering Task Force maintains
the RFCs as the standards for the TCP/IP suite.
Extra: Services and Protocol: Port Number
As we will see later in this course, the Transport
layer uses an addressing scheme called a port
number.
Port numbers identify applications and Application
layer services that are the source and destination of
data.
Server programs generally use predefined port
numbers that are commonly known by clients.
As we examine the different TCP/IP Application layer
protocols and services, we will be referring to the TCP
and UDP port numbers associated with these services.
Some of these services are:
Domain Name System (DNS) - TCP/UDP Port 53
Hypertext Transfer Protocol (HTTP) - TCP Port 80
Simple Mail Transfer Protocol (SMTP) - TCP Port 25
Post Office Protocol (POP) - UDP Port 110
Telnet - TCP Port 23
Dynamic Host Configuration Protocol - UDP Port 67
File Transfer Protocol (FTP) - TCP Ports 20 and 21
Extra: DNS
In data networks, devices are labeled with numeric
IP addresses, so that they can participate in sending
and receiving messages over the network.
However, most people have a hard time remembering
this numeric address.
Hence, domain names were created to convert the
numeric address into a simple, recognizable name.
On the Internet these domain names, such as
www.cisco.com, are much easier for people to
remember than 198.133.219.25, which is the actual
numeric address for this server.
Also, if Cisco decides to change the numeric address, it
is transparent to the user, since the domain name will
remain www.cisco.com.
The new address will simply be linked to the existing
domain name and connectivity is maintained.
The DNS was created for domain name to address
resolution for these networks.
DNS uses a distributed set of servers to resolve the
names associated with these numbered addresses.
Extra: DNS Services and Protocol
DNS is a client/server service;
It differs from the other client/server services that we are
examining.
While other services use a client that is an application
(such as web browser), the DNS client runs as a service
itself.
The DNS client, sometimes called the DNS resolver, supports
name resolution for our other network applications and other
services that need it.
Computer operating systems also have a utility called
nslookup that allows the user to manually query the
name servers to resolve a given host name.
This utility can also be used to troubleshoot name
resolution issues and to verify the current status of the
name servers.
In the first query in the figure, a query is made for
www.cisco.com. The responding name server provides the
address of 198.133.219.25.
Extra: WWW Service and HTTP
When a web address (or URL) is typed into a web
browser, the web browser establishes a connection
to the web service running on the server using the
HTTP protocol.
The http://www.cisco.com/index.html example
http (the protocol or scheme)
www.cisco.com (the server name)
A web page named index.html on a server.
The browser then checks with a name server to
convert www.cisco.com into a numeric address,
which it uses to connect to the server.
Using the HTTP protocol, the browser sends a GET
request to the server asks for file index.html.
The server in turn sends the HTML code for this web
page to the browser.
Finally, the browser deciphers the HTML code and
formats the page for the browser window.
Other types of data, may require another service or
program, typically referred to as plug-ins
Extra: WWW Service and HTTP
HTTP is not a secure protocol.
The POST messages upload information to the
server in plain text that can be intercepted and
read.
Similarly, the server responses, typically HTML
pages, are also unencrypted.
For secure communication across the Internet,
the HTTP Secure (HTTPS) protocol is used
for accessing or posting web server
information.
HTTPS can use authentication and encryption
to secure data as it travels between the client
and server.
HTTPS specifies additional rules for passing
data between the Application layer and the
Transport Layer.
Extra: E-mail Services and SMTP/POP3
User composes an e-mail using an application called a mail user
agent (MUA) or e-mail client
Client sends e-mails to a server using Simple Mail Transfer Protocol
(SMTP) and receives e-mails using Post Office Protocol version 3
(POP3)
• SMTP uses TCP port 25
• POP uses UDP port 110
Extra: File Transfer Protocol (FTP)
The FTP is a Application layer protocol.
FTP was developed to allow for file transfers
between a client and a server.
An FTP client is an application that runs on a
computer that is used to push and pull files from
a FTP server.
The client can download (pull) file from server
or, the client can upload (push) file to server.
To transfer files, FTP requires two connections
between client and server:
The client establishes the first connection to the
server on TCP port 21.
It consists of client commands and server
replies.
The client establishes the second connection to
the server over TCP port 20.
This connection is for the actual file transfer
and is created every time there is a file
transferred.
Extra: Dynamic Host Configuration Protocol (DHCP)
The DHCP service enables devices on a
network to obtain IP addresses and other
information from a DHCP server.
This service automates the assignment of IP
addresses, subnet masks, gateway and other IP
networking parameters.
When the DHCP server is contacted and an
address requested.
The DHCP server chooses an address from a
configured range of addresses called a pool and
assigns ("leases") it to the host for a set period.
If the host is powered down or taken off the
network, the address is returned to the pool for
reuse.
This is especially helpful with mobile users that
come and go on a network.
Extra: P2P Service and Gnutella Protocol
Sharing files over the Internet has become
extremely popular. With P2P applications based
on the Gnutella protocol, people can make files
on their hard disks available to others for
downloading.
pronounced /nʊˈtɛlə/ with a
silent g,
Gnutella-compatible client software allows users to
connect to Gnutella services over the Internet and
to locate and access resources shared by other
Gnutella peers.
Many client applications are available for
accessing the Gnutella network, including:
BearShare, Gnucleus, LimeWire, Morpheus, WinMX
and XoloX (see a screen capture of LimeWire in the
figure).
Extra: P2P Service and Gnutella Protocol
Many P2P applications do not use a central database to
record all the files available on the peers.
Instead, the devices on the network each tell the other what
files are available when queried and use the Gnutella protocol
and services to support locating resources.
When a user is connected to a Gnutella service, the client
applications will search for other Gnutella nodes to
connect to.
These nodes handle queries for resource locations and
replies to those requests.
They also govern control messages, which help the service
discover other nodes.
The actual file transfers usually rely on HTTP services.
The Gnutella protocol defines five different packet types:
ping - for device discovery
pong - as a reply to a ping
query - for file location
query hit - as a reply to a query
push - as a download request
Extra: Telnet
Telnet uses TCP port 23
Provides a method of emulating text-based terminals over the
network
allows a local device to access a remote device as if the keyboard and
monitor are connected to the remote device directly
A connection using Telnet is called a virtual terminal (VTY) session
• The Telnet server runs a
service called the Telnet
daemon
Ch 3 - 61