* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download PPP - Ivailo Chakarov
Survey
Document related concepts
Net neutrality law wikipedia , lookup
Distributed firewall wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Deep packet inspection wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Computer network wikipedia , lookup
Network tap wikipedia , lookup
Internet protocol suite wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Transcript
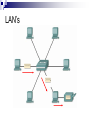
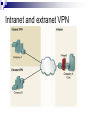
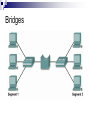
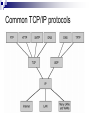
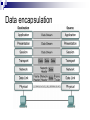
Introduction to IT and Communications Technology Networking Fundamentals CE00378-1 Justin Champion C208 – 3292 Content LANS WANS Technology which keeps them operating Sneakernet Earliest example of networking As more work was done on computers, the need to share this information became greater Multiple people working on the same item for example A need to print a document but there is no printer attached to your network This network was not connected, it involved a person copying the files to a removable medium and physically going to that computer and doing the work Therefore sneakernet Sneakernet LANS Local Area Network (LAN) As computers got more powerful and were relied upon to do more work moving around the office became less desirable Problems were Time involved Limit on the distance that could be travelled Data got corrupted Undue replication of Data Expense in physical media Users wanted all Printers Data files Internet Access functionality at THERE machine LANS Local Area Network (LAN) These were the solution to the problem Locally connecting multiple computers together Allowing sharing of Data files Printers Central storage areas All companies now with more than one machine will use a LAN of some sort to reduce the costs and improve productivity LAN’s LAN WANS Wide Area Network (WAN) With the introduction of LANS in companies there needed to be a method of allowing communications across multiple LANS For example a company who has 4 offices All of these may want to share central data files Backup all of the data on the local LAN to a central location For this a WAN is needed, which uses different technology The WAN will allow communications across a wider distance The Internet is an example of a WAN Companies like Hewlett Packard, will use WANs to connect offices, but smaller companies will also use this technology WAN Other Network Types Metropolitan Area Network (MAN) This is a network which allows resources to be shared across an area larger than a LAN and smaller than a WAN. Services across a town, like Stafford for example Storage Area Network (SAN) This is a high speed network, where a number of servers will be connected These servers will be able to provide a high speed service In the event of more higher speed being needed an additional server can be added to the SAN Metropolitan area network Other Network Types Virtual Private Networks (VPN) These are networks which are usually setup by companies They allow someone who is not connected to a network to be able to use the network as though they were connected Example would be a business person on the road using a Internet connection in Starbucks to connect into the VPN of the company to read emails or replicate a data source These work with a combination of software and hardware VPN connections Other Network Types VPNs Other parts of the same company Can then use the relative cheap access to a network via the Internet Using the VPN removes the worry of people stealing your data or gaining illegal access Other users Can also be used to allow other companies access to your network If you have a company that needs to share some of your data, the VPN can be configured to allow them access This can be restricted so that they can only access the parts of the network you need. i.e. it is highly unlikely that you would a external supplier access to your printers Intranet and extranet VPN History of Networking Networking Technology Did not just happen There were stages which contributed to this development to get where we are now 1890’s Bell invents the telephone 1948 Claude Shannon Publishes “A mathematical theory of communications” 1962 Paul Baran at RAND works on “Packet Switching” 1969 ARPANET is established 1972 Ray Tomlinson creates a email program to send messages 1973 work begins on TCP/IP 1981 The term Internet is first used 1983 TCP/IP becomes the default language for the Internet 1984 Cisco Systems is founded 1990 ARPANET becomes the Internet 1991 World Wide Web is created by Sir Tim Berners-Lee 1993 First Graphical browser Mosaic is created Symbols Throughout this course a number of symbols will be used These are a quick way to recognise different elements of a network Below are the end user symbols Network device icons Symbols Quick overview of the symbols Repeater Switch Based on the IP Address this node will forward the data to the correct host/machine Bridge Based on the Ethernet MAC address this node will forward the data to the correct host/machine Router This receives a signal from the network and then repeats it. After a distance an electrical signal will lose power. This node increases the power of the signal again Connects two segments of a network together. Only allowing data to pass if the destination host/machine is located on the other segment More information will be given on all of these terms during the course Bridges Physical Setup The network has wires, which are used to transfer the information Wireless communications will be covered in other courses These machines can then be wired in different ways depending on The level of reliability needed The network technology being used Money available to invest in the infrastructure Physical topology Bandwidth There are two measures of the amount of data that can be transferred on a network Throughput Bandwidth These are often used interchangeably, but they do indicate different measures Bandwidth This is the amount of data that can be physically supported on your network Throughput This is the amount of data that is actually moved in a period of time This time interval is usually in seconds Why is bandwidth important? For a successful network you must ensure you have enough bandwidth Even for a simple network at home you ensure you have enough If you are downloading multimedia, you would replace your 56 Kbps modem with cable or ADSL You have now increased your available bandwidth Points to remember Bandwidth is limited by the technology used and the physics of the medium used Bandwidth is not free Bandwidth requirements are always growing You can never have enough bandwidth Bandwidth is crucial to the performance of your network Highway analogy Units of bandwidth Max bandwidth and length WAN services and bandwidths Variables effecting throughput So why are bandwidth and throughput different values ? A number of factors may effect the throughput of a device The available speed/power of the requesting machine (Client) The available speed/power of the responding machine (server) Routing delays within the network Design and topology of the networks transferring the data Type of data being transferred Time of day (other users on the network) Email servers are usually slow first thing in the morning as a lot of people are checking them Transfer time calculation Typical S = 20000 Bits (size of the file) P = 5640 Bps (actual throughput at the time) = 3.54 seconds transfer time Network layers Network Flows Data on the network must flow correctly This is from the source to the destination If this happens correct communication can take place This is the same that happens in real-life with other networks i.e. phone call Spoken language is the protocol (the information to be transferred) Flow control takes place with politeness i.e. two people should not speak at the same time. One speaks when the other stops Physical medium for the transfer of information is the telephone and electrical wires. This same set of rules happens within computer networks using software protocols, which both parties agree on before starting Layer based communications Networks use protocols to transfer information The information which is transferred is sent through a number of processes called layers before transmission The destination then reverse the processes to get the information back again OSI Layer based communications All network communications are based on these layers As long as the source and destination use the same layers in the same sequence the information can be transferred successfully The standard for the layers is referred as the OSI model The benefits of using this standard model are Reduces complexity Facilitates modular engineering Standardises interfaces Accelerates evolution Simplifies teaching and learning The OSI model Each of the layers has a specific task to perform The OSI model was developed by the International Standards Organisation (ISO) Peer-to-peer communications In the OSI model The information is passed from layer 7 to 1 at the source Each layer will add some additional information needed for the successful transfer i.e. layer 3 adds the IP address of the destination The destination then receives the data The data is transferred from layer 1 to 7 Each layer removes and process information and passes the remaining data to the layer above Peer-to-peer communications In the OSI model Only the layer which created a piece of information can process it So if Layer 4 (transport) adds some transport information at the source Only layer 4 (transport) can remove this information at the destination TCP/IP The most widely used protocols for the transfer of information is Transport Control Protocol (TCP) / Internet Protocol (IP) TCP/IP does not use all of the OSI layers It combines layers 5,6 and 7 into a single Application layer Layers 1and 2 are combined into Network Access Common TCP/IP protocols Main protocols Data encapsulation Data encapsulation example Conclusion What we have covered today A lot !